Stored XSS
Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted websites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user. Stored attacks are those where the injected script is permanently stored on the target servers, such as in a database, in a message forum, visitor log, comment field, etc. The victim then retrieves the malicious script from the server when it requests the stored information
Exploitation
The webapp takes in user’s input and saves it in a table. Let’s enter a text and submit it.
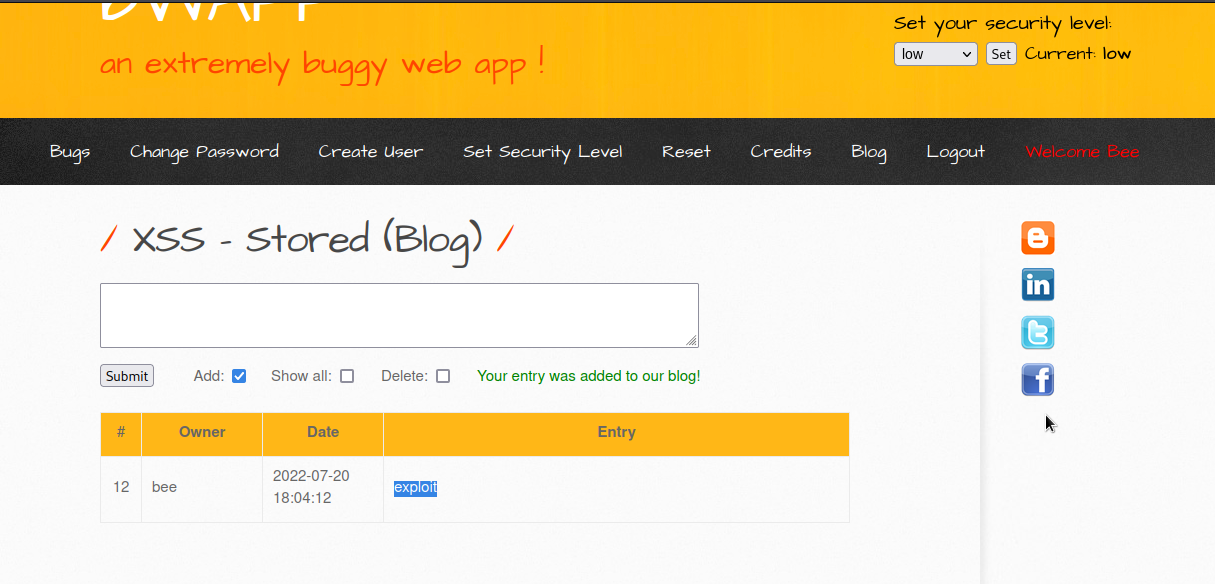
As you can see, our text was added in the entry. Since it was saving and reflecting our input back, it might be vulnerable to stored XSS. We can further inspect the page.
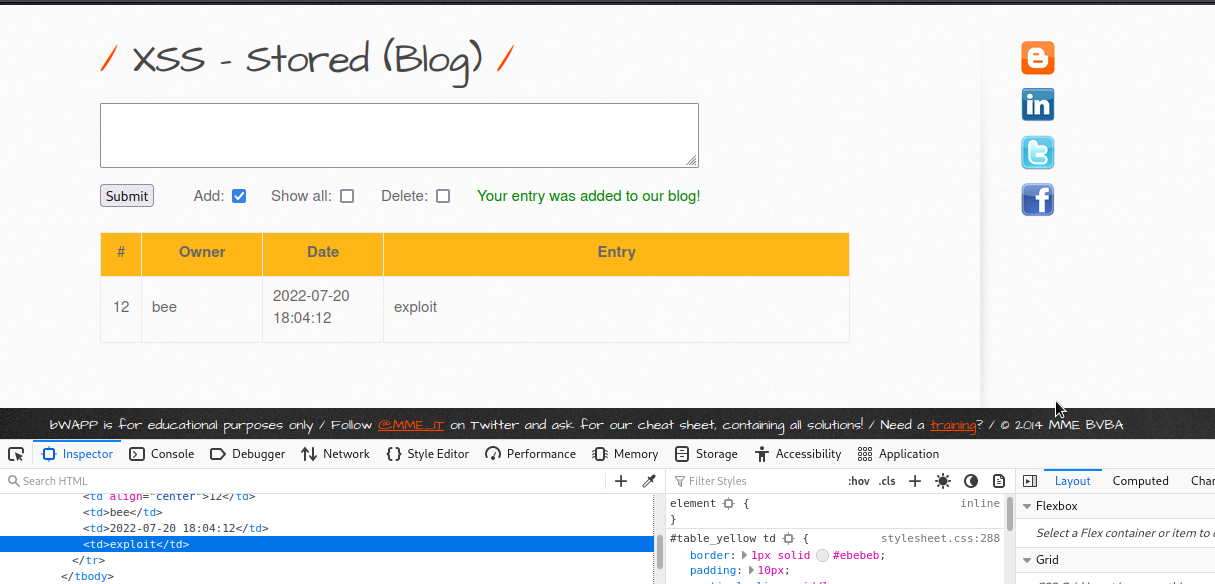
Let’s inject this xss payload <a href=javascript:alert(1)>Click</a> to see if we can get alert box.
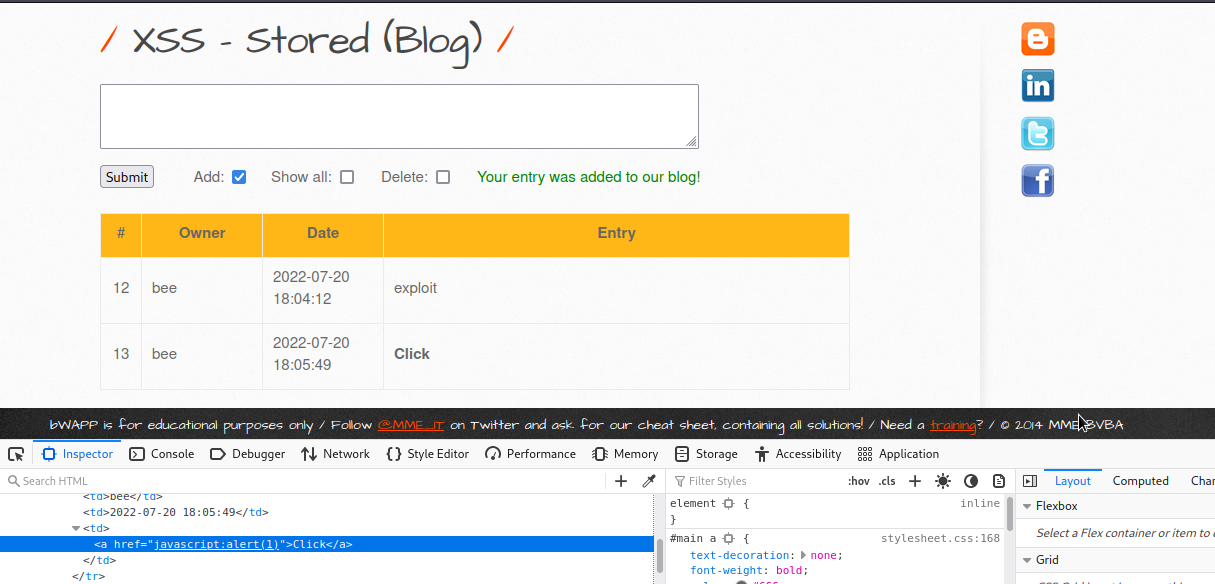
As you can see, the link has appeared in the table. We will click on the link
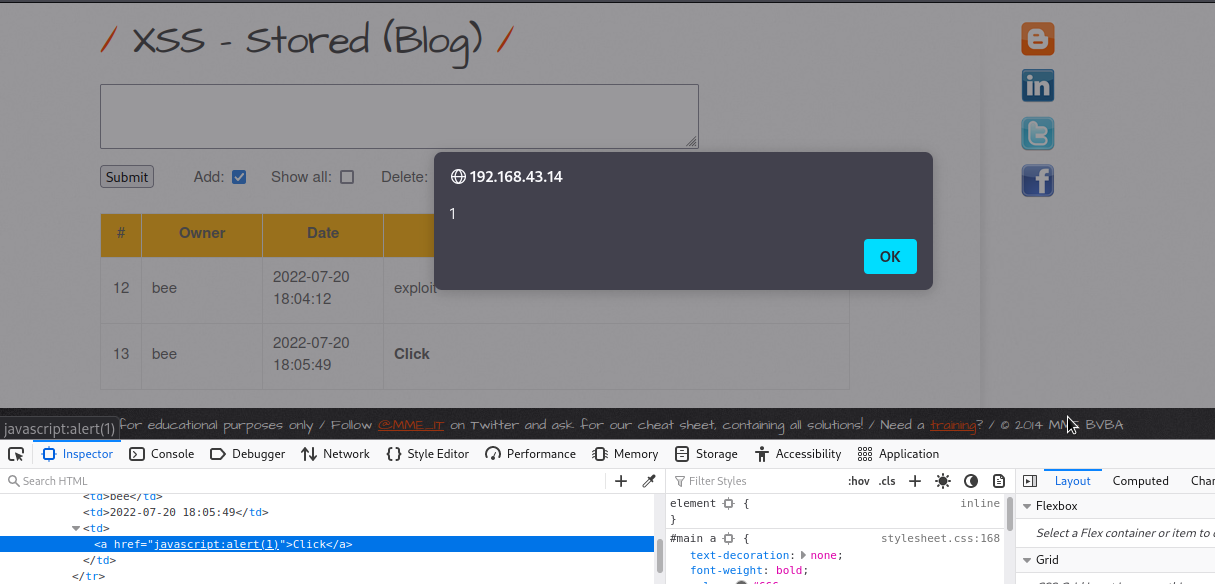
We were able to get alert box.
Mitigations
- Use HTML entity encoding.
- Use Content Security Policy (CSP).
- Set the HttpOnly flag for cookies.
