XPATH Injection
XPath Injection attacks occur when a web site uses user-supplied information to construct an XPath query for XML data. By sending intentionally malformed information into the web site, an attacker can find out how the XML data is structured, or access data that they may not normally have access to. They may even be able to elevate their privileges on the web site if the XML data is being used for authentication (such as an XML based user file).
Detection
This webapp will take in the username and password, queries username and password in xml file using xpath, and then displays user’s information if the username and password exists. If the webapp is vulnerable to xpath injection, we can bypass the authentication.
Let’s try this valid credential that we have been given. Mike: test123
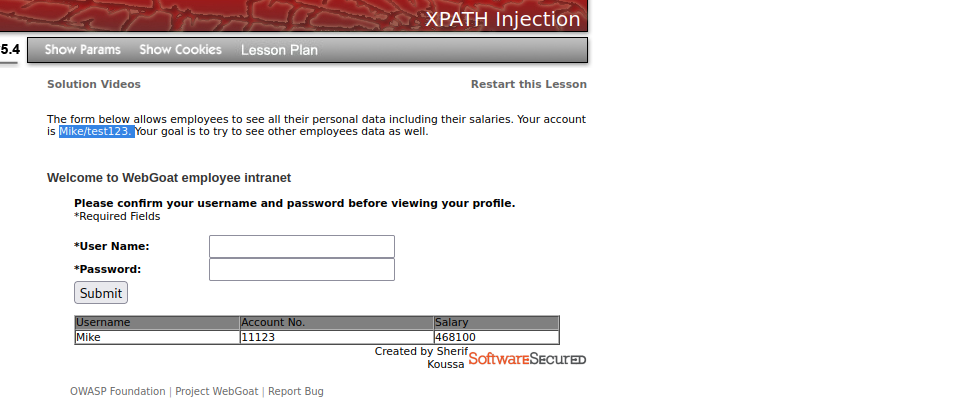
We were able to get user’s detail with the given credential. But our aim is to login without valid credential.
We will now attempt to determine whether or not it’s using xml as it database. Since xpath uses syntax with / > < @ \ .., we will attempt to supply something containing those characters to see if we can get an error or some anomaly.
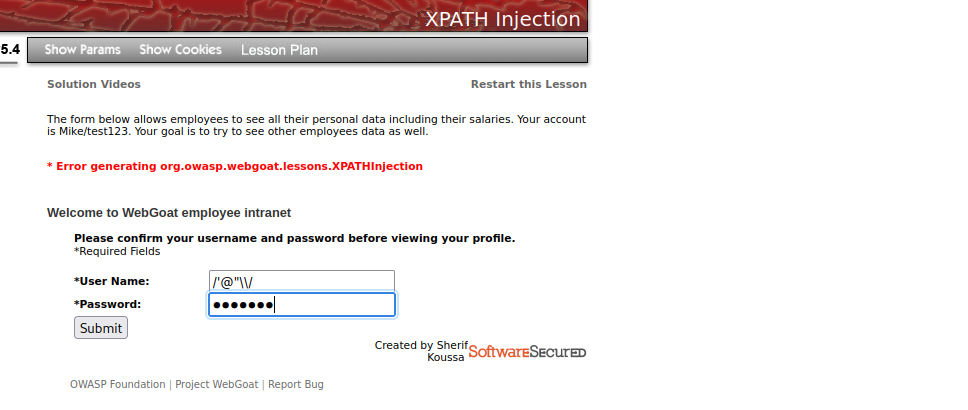
As you can see we got an error, this means our input broke the query, therefore it might be using xpath to process user supplied input.
Exploitation
To bypass the authentication, we will supply ' or '1'='1 in both username and password fields, If it’s successfull, we will be able to retrieve details of others for which we don’t hava permission.

Mitigations
- Use a parameterized XPath interface.
- Escaping All User Supplied Input.
