Open Redirection
Open redirection vulnerabilities arise when an application incorporates user-controllable data into the target of a redirection in an unsafe way. An attacker can construct a URL within the application that causes a redirection to an arbitrary external domain. This behavior can be leveraged to facilitate phishing attacks against users of the application.
Detecting Open Redirection
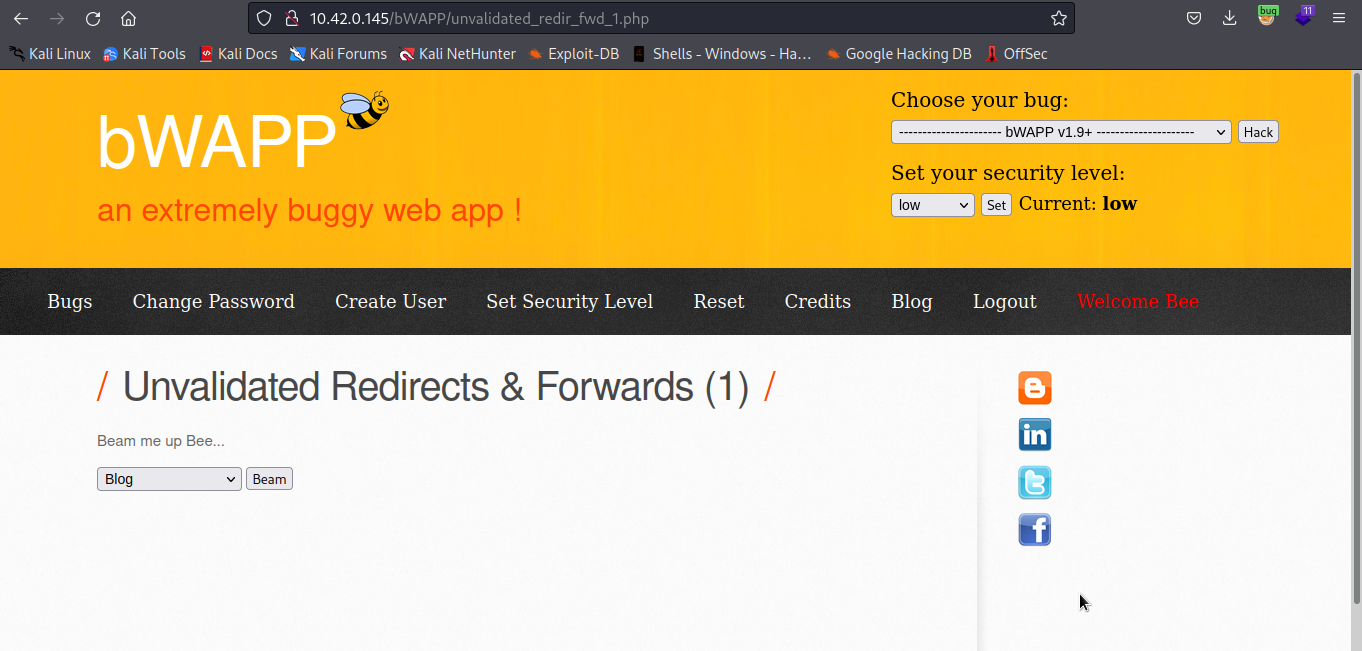
For the purpose of this experiment, we are going to use bWAPP vulnerable web application. If we click on Beam button, we will be redirected to another domain.
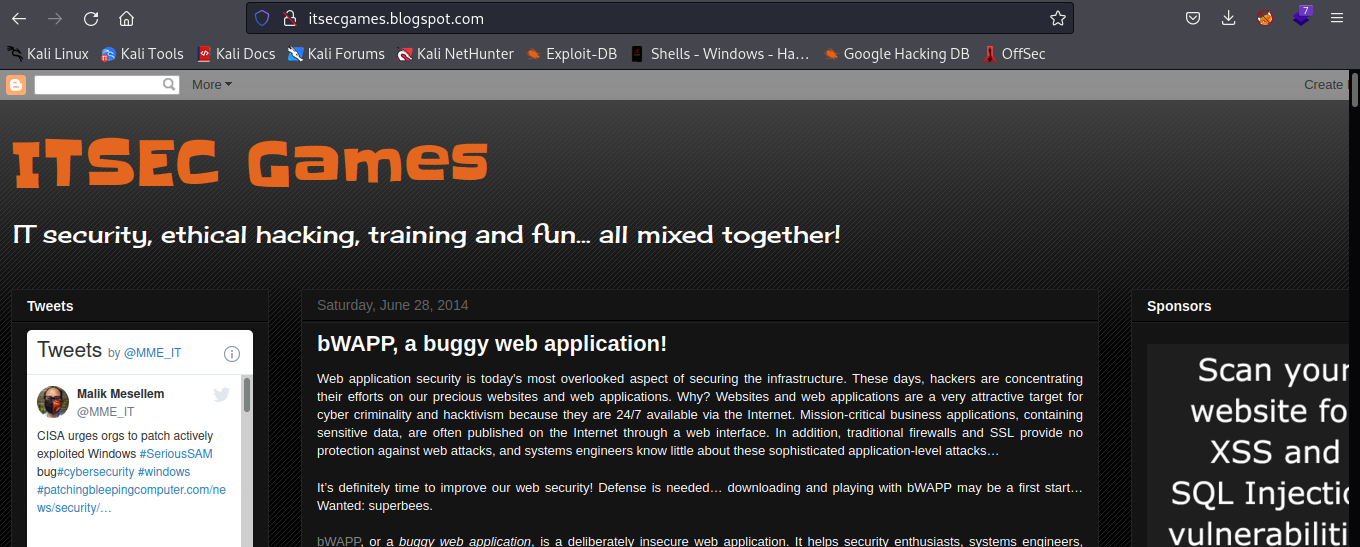
We have been redirected to http://itsecgames.blogspot.com/.
Now we will intercept the request in our burpsuite in order to examine the flow of redirection.
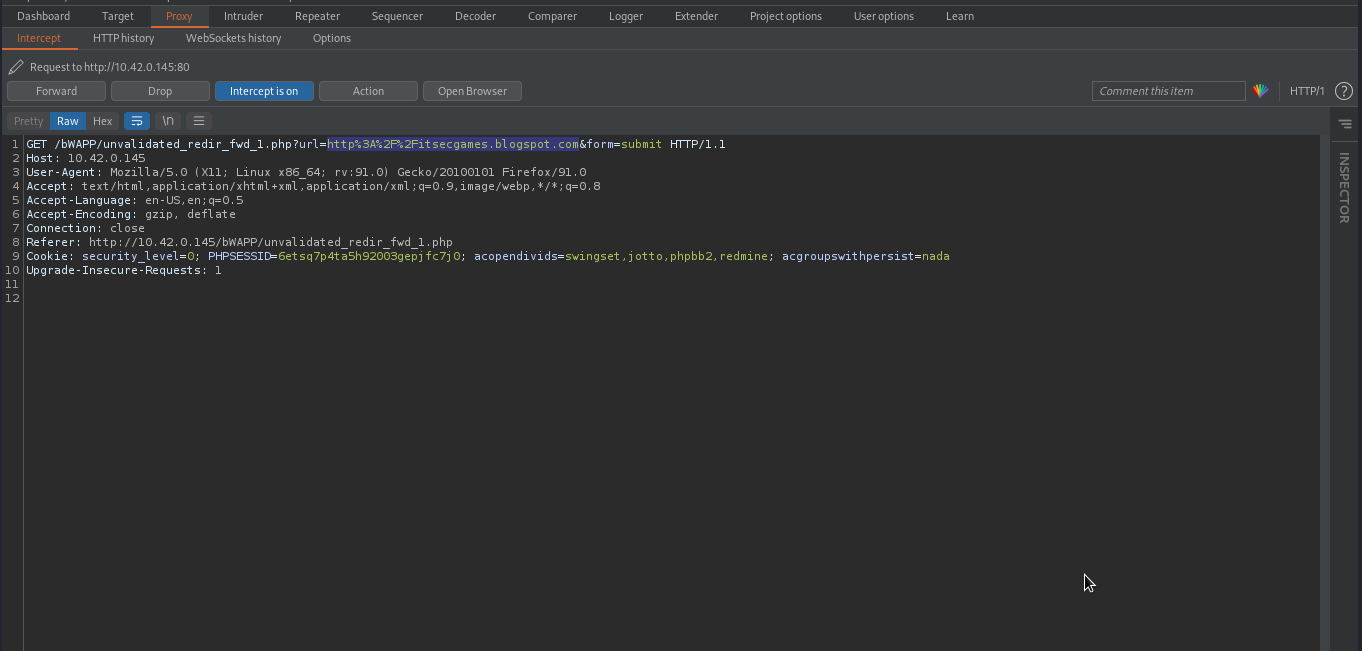
As you can see we have http://itsecgames.blogspot.com/ as the value of url parameter, which means the server is making redirection based on the value of url.
Exploitation
Let’s attempt to replace the value of url parameter with our own domain to see what will happen.
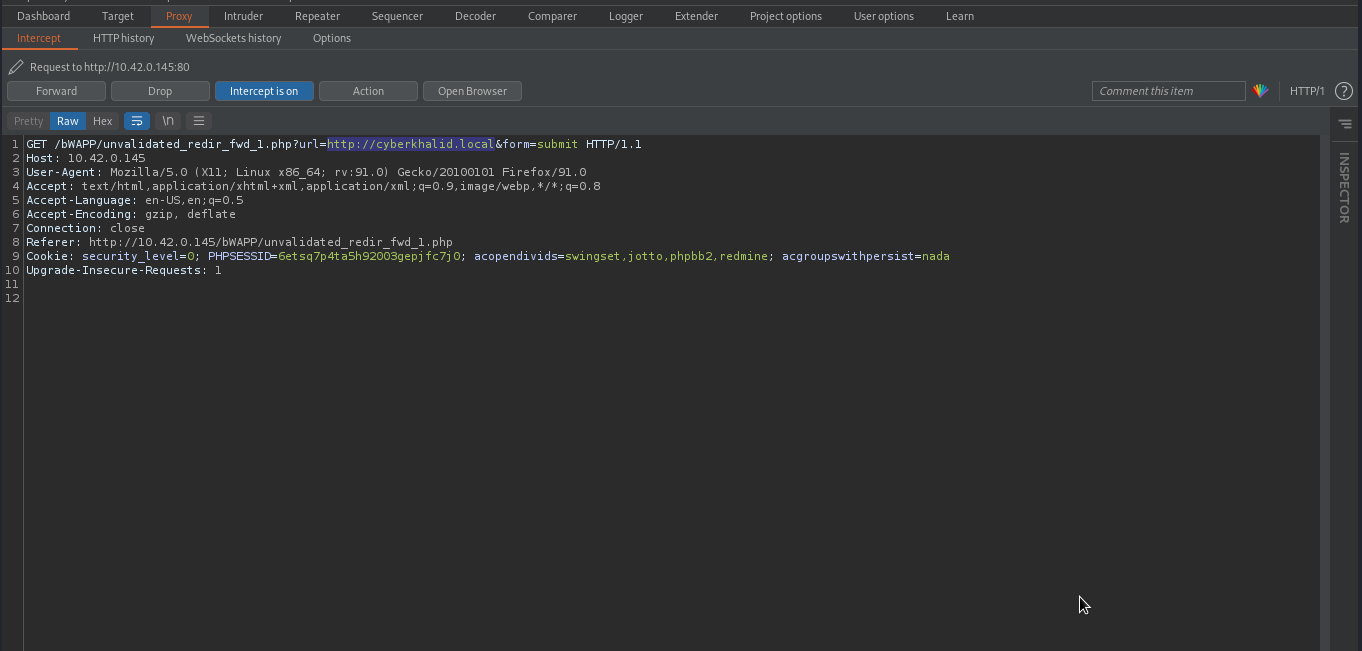
After sending the request to the server, we were redirected to http://cyberkhalid.local.
Mitigations
- Remove the redirection function from the application, and replace links to it with direct links to the relevant target URLs.
- Maintain a server-side list of all URLs that are permitted for redirection. Instead of passing the target URL as a parameter to the redirector, pass an index into this list.
