Pivoting: mitre -> TA0008, T1572
Pivoting Is a technique of routing network traffics from one system to another system or networks. Is a technigue that adversary uses to move from one compromised system to another system or to access devices, networks and ports that are not publicly accessible.
Accessing internal port via ssh tunneling 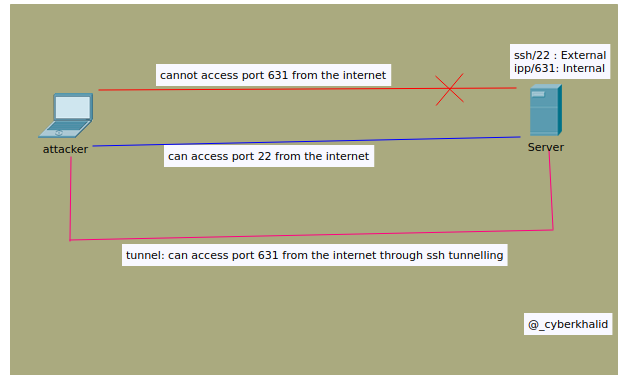
Accessing internal machine via ssh tunneling 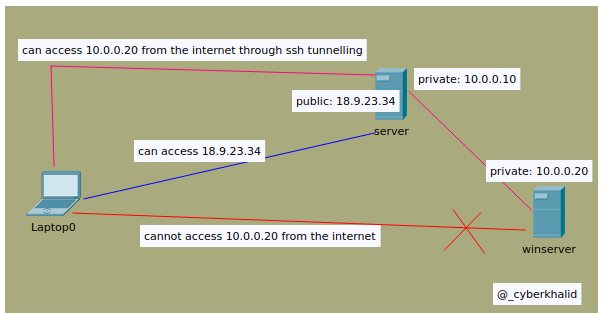
Technigues
- SSH Local Port Forwarding
- Remote Port Forwarding
- Dynamic Port Forwarding
SSH Local Port Forwarding
Is a technigue that allows you to forward a port on the local (ssh client) machine to a port on the remote (ssh server) machine, which is then forwarded to a port on the destination machine.
syntax
ssh -L [local_ip]:[local_port]:[destination_ip]:[destination_port] -N -f [username]@[remote_ip]
Accessing rdp port 3389 using ssh local portforwarding
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(cyberkhalid㉿kali)-[~]
└─$ ssh -L 127.0.0.1:8000:172.172.0.20:3389 -N -f user1@10.42.0.21
user1@10.42.0.21's password:
┌──(cyberkhalid㉿kali)-[~]
└─$ rdesktop 127.0.0.1:8000
Autoselecting keyboard map 'en-us' from locale
Core(warning): Certificate received from server is NOT trusted by this system, an exception has been added by the user to trust this specific certificate.
Failed to initialize NLA, do you have correct Kerberos TGT initialized ?
Core(warning): Certificate received from server is NOT trusted by this system, an exception has been added by the user to trust this specific certificate.
Connection established using SSL.
SSH Remote Port Forwarding
Is a technigue that allows you to forward a port on the remote (ssh server) machine to a port on the local (ssh client) machine, which is then forwarded to a port on the destination machine.
syntax
ssh -R [remote_port]:[destination_ip]:[destination_port] -N -f [username]@[remote_ip]
Accessing http port 50000 using ssh remote portforwarding
1
2
3
4
5
6
7
┌──(cyberkhalid㉿kali)-[~]
└─$ ssh -R 8000:127.0.0.1:50000 -N -f user1@10.42.0.21
user1@10.42.0.21's password:
┌──(cyberkhalid㉿kali)-[~]
└─$
From the ssh server machine
Dynamic Port Forwarding
Is a technigue that allows you to create a socket on the local (ssh client) machine, which acts as a SOCKS proxy server. When a client connects to this port, the connection is forwarded to the remote (ssh server) machine, which is then forwarded to a dynamic port on the destination machine.It Creates a SOCKS proxy server that allows communication across a range of ports.
syntax
ssh -D [local_port] -N -f [username]@[target_ip]
Note: Make sure to modify the proxychains config file.
Accessing rdp port 3389 using ssh dynamic portforwarding
1
2
3
4
5
6
7
8
9
10
11
12
┌──(cyberkhalid㉿kali)-[~]
└─$ ssh -D 1000 -N -f user1@10.42.0.21
user1@10.42.0.21's password:
┌──(cyberkhalid㉿kali)-[~]
└─$ proxychains rdesktop 172.172.0.20
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Autoselecting keyboard map 'en-us' from locale
[proxychains] Strict chain ... 127.0.0.1:1000 ... 172.172.0.20:3389 ... OK