Sql Injection -> Authentication Bypass
SQL injection is a technique used to exploit user data through web page inputs by injecting SQL commands as statements. If a login form is vulnerable to sql injection, adversaries can bypass the authentication and login to an account for which they do not have permission.
Exploitation
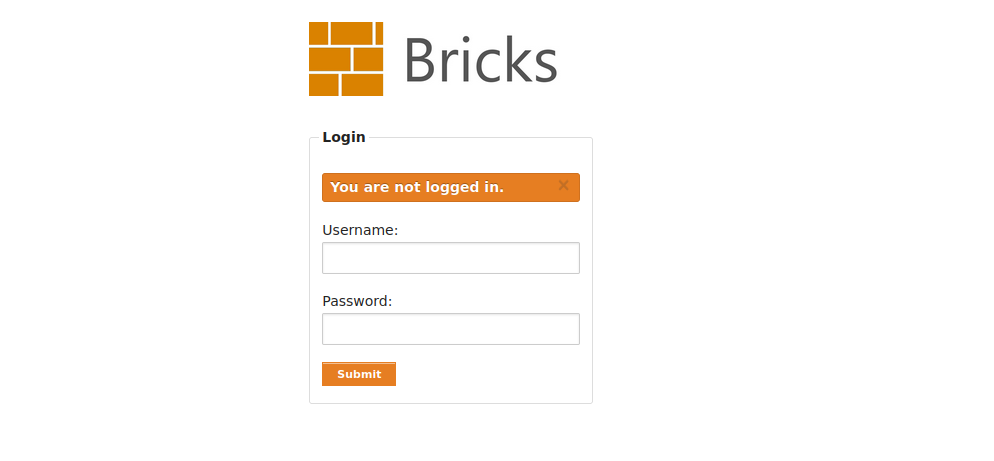
This webapp takes username and password, queries username and password in it database and then gives access to a user if the username and password exists.
Let’s supply wrong credentials first.
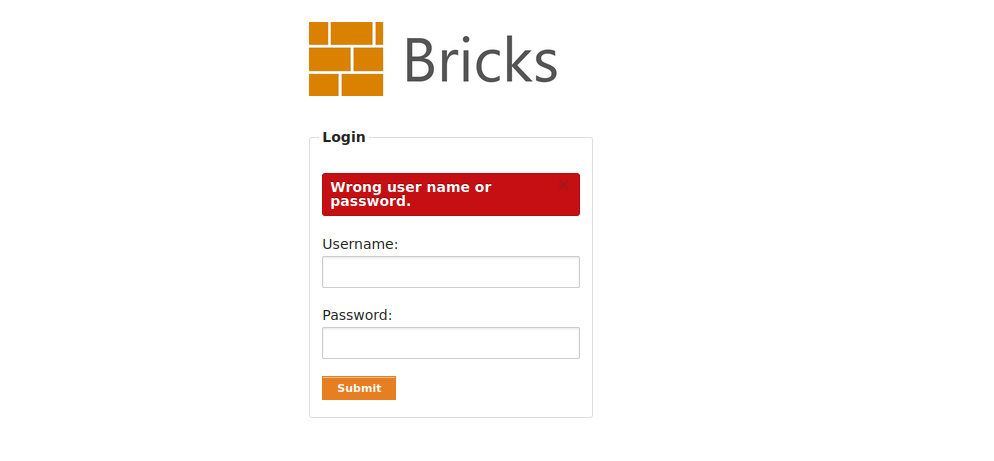
We got this because our credentials were incorrect.
We can predict the query being executed on the backend as something like this:-
SELECT * from [table_name] where username='[input]' and password='[input]'.
By supplying 1' or 1=1;-- -, we will have the backend execute something like SELECT * from [table_name] where username='1' or 1=1;-- -' and password='[input]'. Sql engine will not execute whatever comes after -- because sql engine ignores anything after --, so only SELECT * from [table_name] where username='1' or 1=1; will be executed which will return true, thereby giving us access to the account that first matches the query.
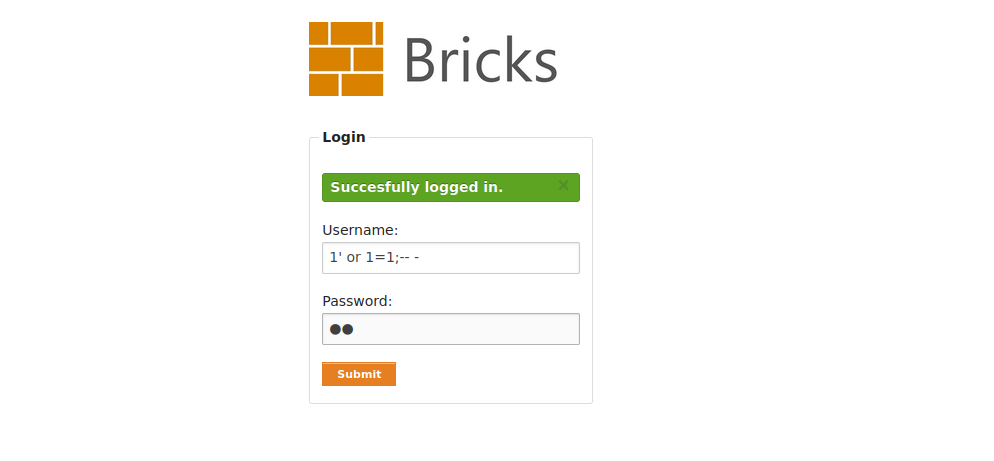
Mitigations
- Use of Prepared Statements (with Parameterized Queries).
- Enforcing Least Privilege
- Escaping All User Supplied Input
