SNMP
Simple Network Management Protocol (SNMP) is a protocol for network management. It is used to monitor different devices in the network (like routers, switches, printers, IoTs…). It runs on port 161/udp.
Enumeration
Scanning With Nmap
We can use nmap to scan snmp as well as to get the version of snmp running on our target system.
1
nmap -sU -sV -p 161 [target_ip]
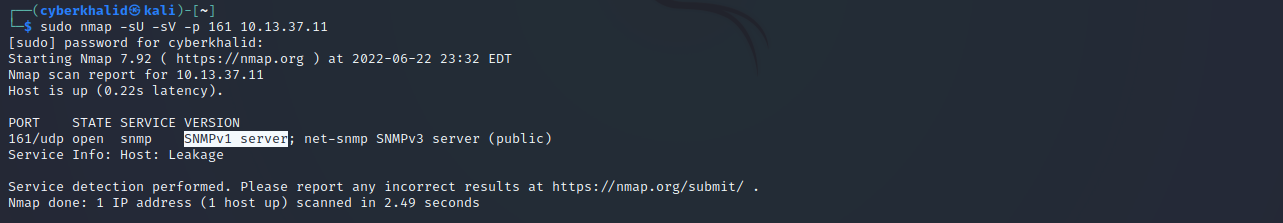
Above image shows snmp is running on port 161/udp on our target. It also reveals the version of snmp running, which was snmpv1
Bruteforcing Community String
SNMP version 1,2 and 2c use community string for authentication. Community String is similar to a user ID or password that is sent along with each SNMP Get-Request to get access to the devices’ information.If the community string is correct, you’re given access to the devices’ statistics and if the string is wrong, the devices simply ignore the request and do not respond to it.
in order to access the information on snmp, you need to know the community string, which can be bruteforced using tools like hydra and nmap.
Nmap
We can use nmap to bruteforce snmp community string.
1
nmap -sU --script snmp-brute.nse -p 161 [target_ip]
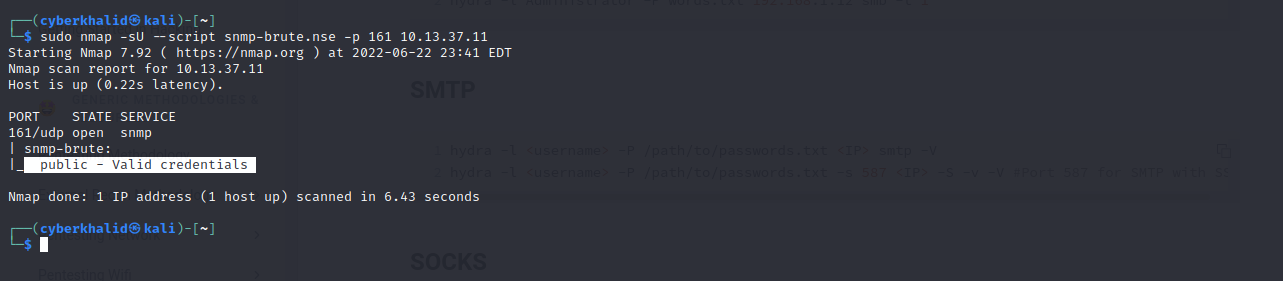
From the above image, we were able to get public as the valid community string of the target snmp.
Hydra
We can also use hydra to bruteforce snmp community string.
1
hydra -P [/path/to/wordlist.txt] -v [target_ip] snmp
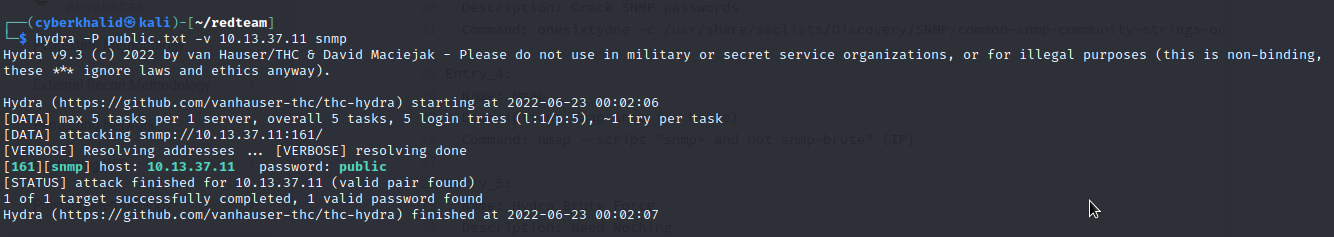
From the above image, we were able to get public as the valid community string of the target snmp.
Exploitation
With the valid community string in hand, we may get lot of information about the host and network devices, we may get ipv4 and ipv6 addresses, usernames, OS version, Services, Processes, Emails, Passwords and much more.
snmpwalk
We can use snmpwalk to get lot of information from snmp.
1
snmpwalk -v [version of snmp] -c [community string] [target_ip]
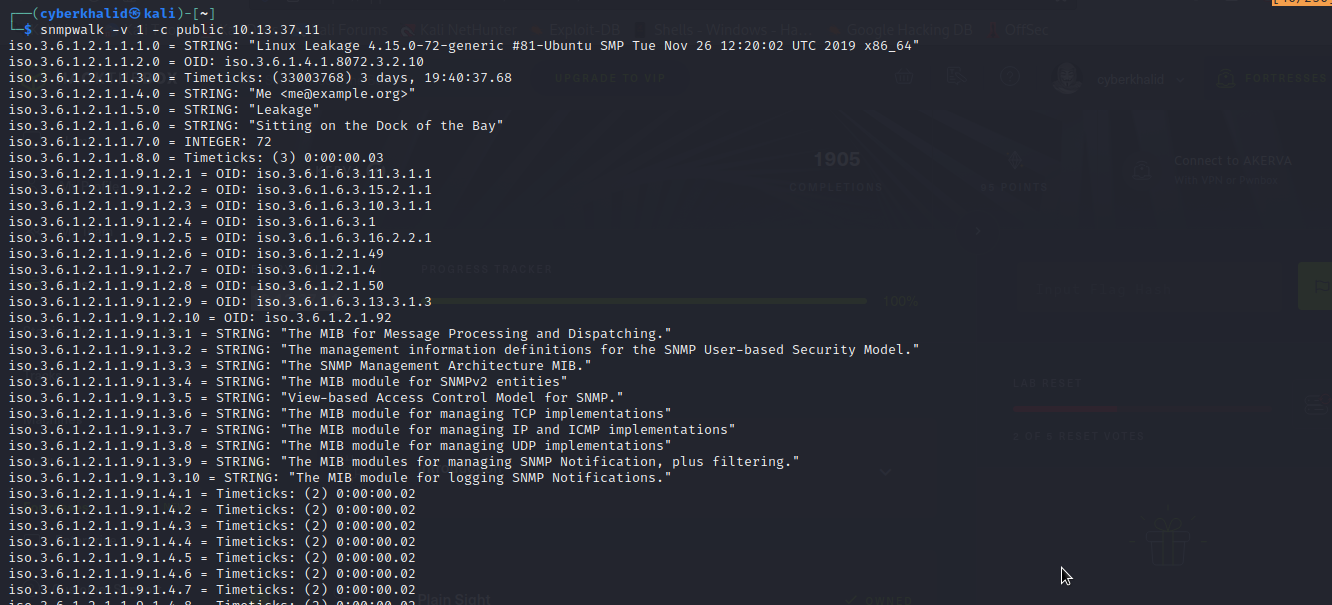
As you can see from the image above, snmpwalk was fetching lot of information from snmp.
Note: As most of the information getting from snmp are huge, we recommend saving it in a file.
Analysis
After saving the outputs in a file, we analysed the file which we were able to get OS version, Email Address, Ethernet In Use, Ip Address, running process and running services.
Os Version and Email Address

Ethernet In Use

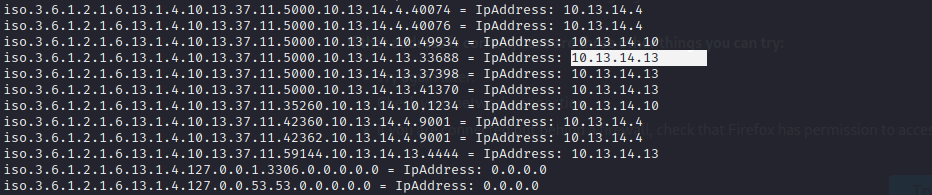
Ipv4 Addresses
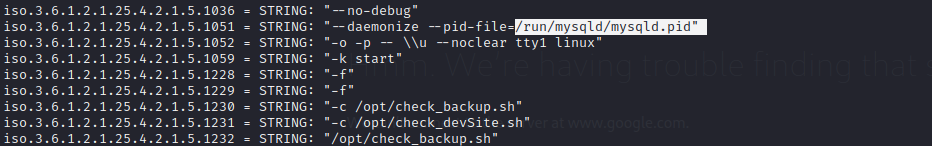
mysql process
Apache running

