Process Discovery
- ID :
T1057 - Tactic :
Discovery - Platforms:
Windows,linux,macos
Process Discovery
Adversaries may attempt to get information about running processes on a system. Information obtained could be used to gain an understanding of common software/applications running on systems within the network. Adversaries may use the information from Process Discovery during automated discovery to shape follow-on behaviors, including whether or not the adversary fully infects the target and/or attempts specific actions.
Exploitations
Windows
Command Prompt
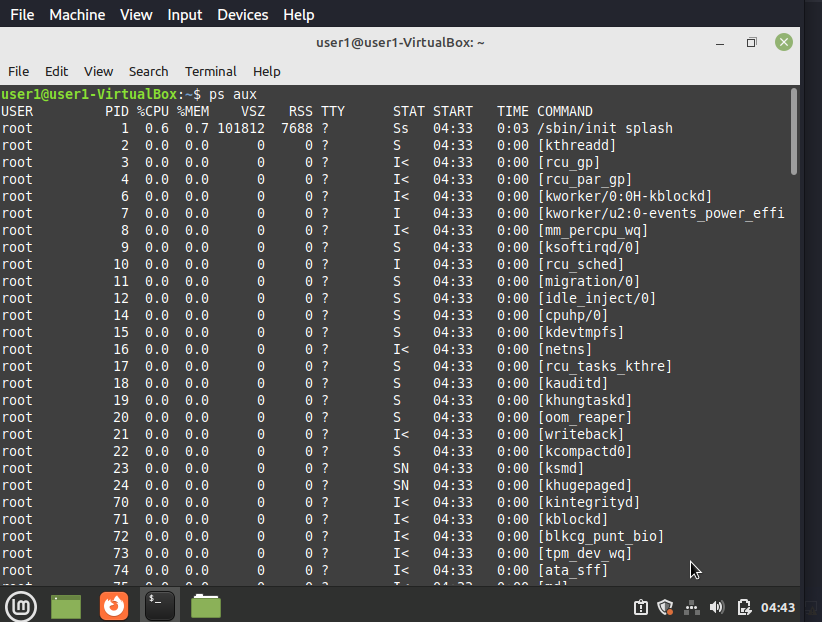
We can get the list of a running processes in windows by executing this command in command prompt.
1
2
3
tasklist
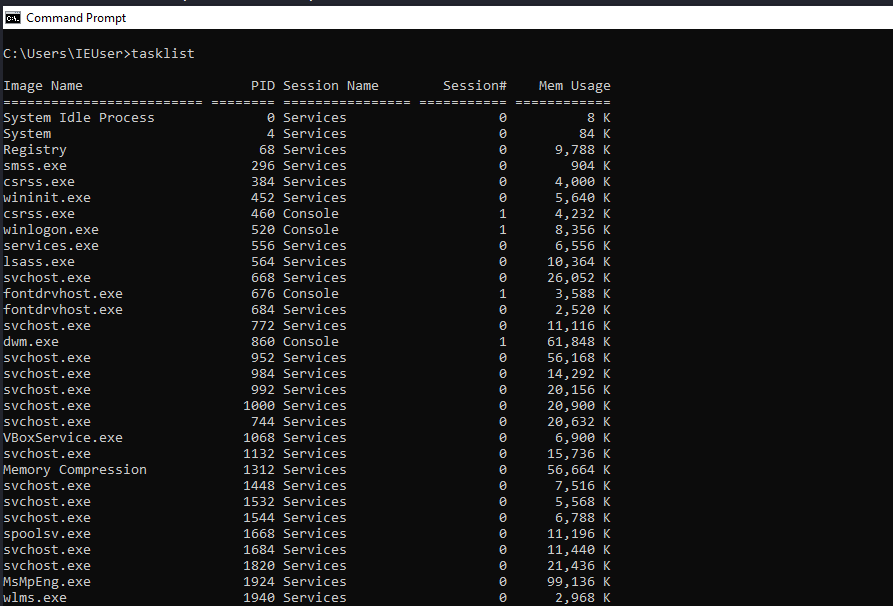
Powershell
We can get the list of a running processes in windows by executing this command in powershell.
1
2
3
get-process
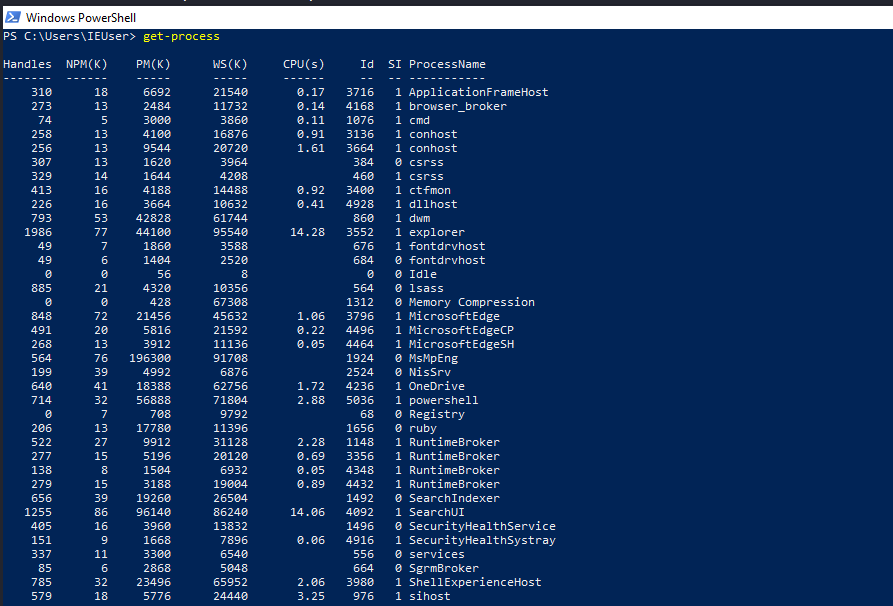
Linux
We can get the list of a running processes in linux by executing the below command.
1
2
3
ps aux