Kerberos
Kerberos is an authentication protocol that is used to verify the identity of a user or host. It runs on port 88/tcp by default.
Enumeration
Scanning With Nmap
We can use nmap to scan kerberos protocol.
1
2
3
nmap -Pn -sS -sV -p 88 [target_host]
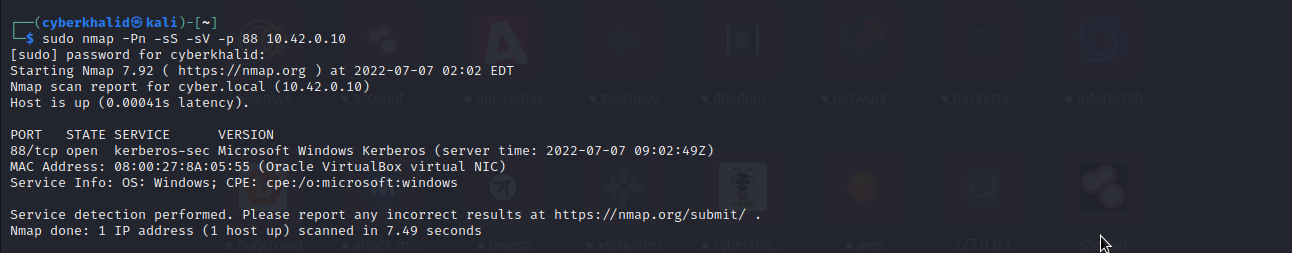
Above image shows kerberos was running on port 88/tcp on our target.
Username Enumeration
We can use kerbrute to enumerate usernames via kerberos protocol.
To enumerate usernames, Kerbrute sends TGT requests with no pre-authentication. If the KDC responds with a PRINCIPAL UNKNOWN error, the username does not exist. However, if the KDC prompts for pre-authentication, we know the username exists and we move on. This does not cause any login failures so it will not lock out any accounts.
1
2
3
kerbrute userenum -d [domain] --dc [dc_ip] [users_file]
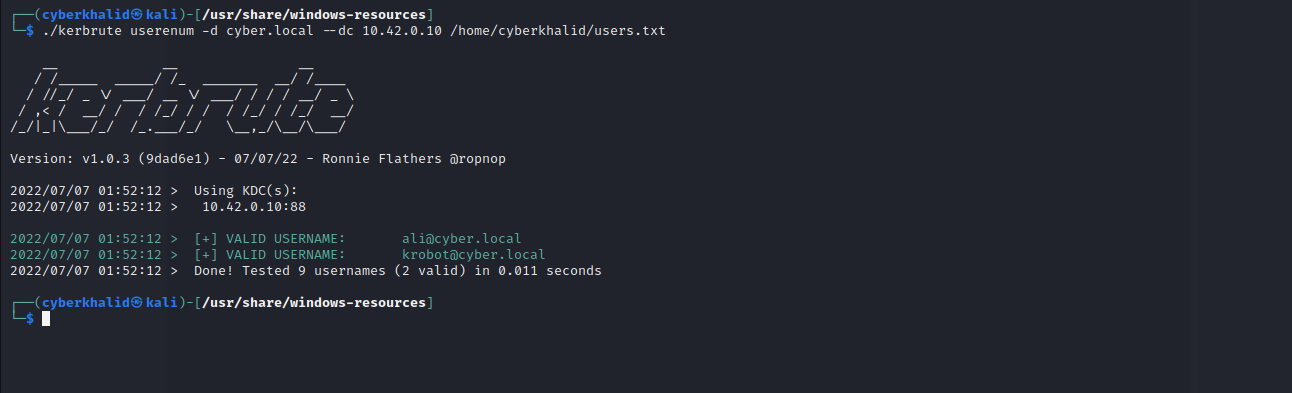
As you can see we were able to get valid usernames.
